From Zero to 100% Akamai with Terraform
 Mike Elissen
Mike Elissen
Changing vendors is never an easy task, especially for your operations team who is managing dozens of configurations on a weekly basis. Infrastructure as Code (IaC) tooling such as the ever-popular Terraform, soon to be in the hands of IBM, can make managing this much, much easier.
I have recently had the pleasure of working with a new Akamai customer as I led their automation project to migrate parts of their tech stack quickly and efficiently over to Akamai.
The customer was very keen to work with Terraform, as it was already being used to manage other technologies in their stack. Akamai offers a Terraform provider as well, currently running at v6.1.0, which allows developers to manage any of the Akamai solutions.
Which Akamai solutions are in scope?
Akamai offers a ton of different solutions. The customer in question wanted to protect and deliver their web applications, API microservices, DNS, and CDN distributions. This led to the following solutions:
| Protecting web apps & APIs | App & API Protector | 50+ hostnames |
| Delivering web apps & APIs | Dynamic Site Accelerator | 50+ hostnames |
| Delivering large content files | Download Delivery | 'Unlimited' hostnames |
| Protecting DNS | Edge DNS | 200 domains/zones |
| HTTPS Certificates | Secure By Default | 50+ certificates |
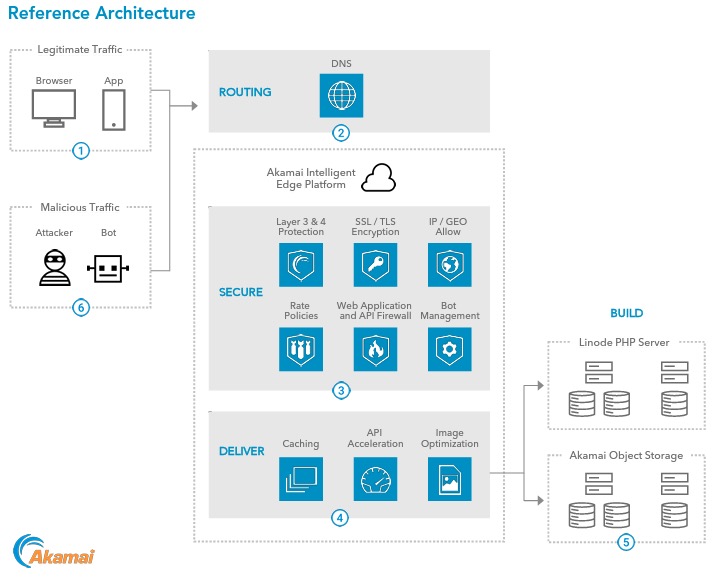
Configuring multiple solutions at once can be a challenge. Especially in the olden days of UIs and ClickOps, you would have to go through the manual process of setting this up individually.
Operational excellence with automation
In a past life at Akamai as a Technical Project Manager, integrating all these solutions simultaneously would be an integration project of roughly 60-75 hours. However, thanks to the ability to reuse Terraform code and create and reuse modules, I was able to lower this down to 24 hours.
Even better, the Terraform templates I created, are available on GitHub, which will cut the time needed to set this up to around 4-6 hours.
You can find the templates right here: https://github.com/akamai/examples-terraform
Everything, Akamai, all at once
The power of Terraform is in its declarative nature where you create all the infrastructure at once. It is tied together by referencing Terraform resources together. Akamai does require a bit of sequencing to make things happen, but our engineering teams have worked to make this all compatible in an integrated fashion.
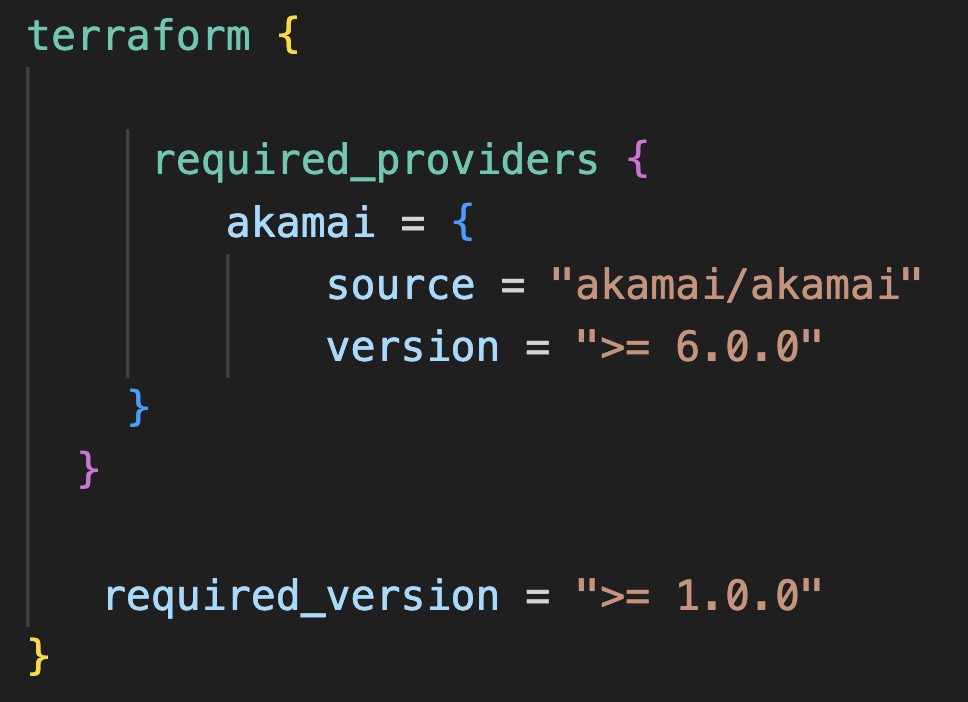
The template I have created does the following:
Prerequisites: Create your Akamai API credentials to authenticate your Terraform requests to Akamai and store them in a .edgerc (Akamai EdgeGrid file).
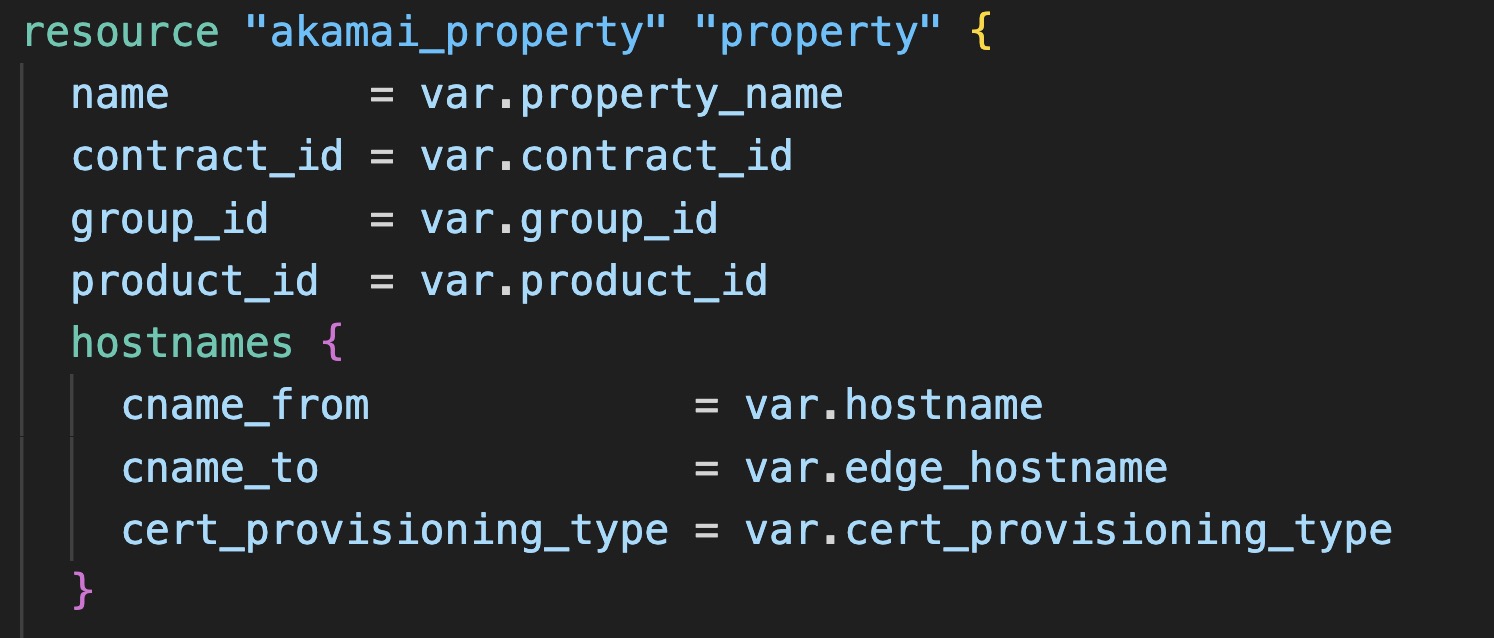
Specify your variables such as DNS zone, hostname you want to protect and delivery (think: blog.securitylevelup.eu), an Akamai EdgeHostname (to CNAME your traffic to Akamai) and your Origin Hostname (where Akamai can retrieve your content, be it static files or dynamic content such as API calls).
Running 'terraform apply' will generate a delivery configuration, security configuration, DNS entries in your DNS zone and an HTTPS certificate, while simultaneously deploying everything to both Akamai's Staging and Production networks, ready for testing.
This entire workflow takes roughly 7 minutes to complete, which is impressive, because, what is also happening is that a DNS entry is created that acts as a Domain Validation check with Let's Encrypt to generate an HTTPS certificate to be deployed securely on Akamai's infrastructure as well.
And within 7 minutes, the web application is fully protected by all the latest and greatest Web Application Firewall protections that Akamai offers, which today, are fully tuned and optimized through the use of AI.
During testing, we were seeing immediate security events coming in from a mini-pen test, showcasing how Akamai is blocking specific web application attacks.
In the hands of the DevOps engineers...
After I created the templates and instructions, I passed on the code bundle to the operations team at the customer who was then able to start migrating their web applications and CDN distributions easily over to Akamai.
Because, the code was templated and reusable, it made the entire process much easier. Each web application or CDN distribution was stored in its own Terraform workflow (read: directory), which could then be managed on-the-fly and isolated from other web applications.
This is perfect for larger organizations that work with different teams, potentially located in various parts of the world or focused on different applications. Akamai's role-based access control is perfectly suited to help support these use cases as well, allowing access to be locked down to specific groups, however you want to set it up.
Furthermore, the customer was also working with Azure DevOps and was able to store each of the Terraform workflows and state files in their pipelines for future use, where they might want to modify specific caching or security rules.
Learnings from this use case
Over the last 5 years, I have worked on roughly 50+ Akamai automation / Terraform workshops and migration projects. While each use case brings something unique to it, the good thing is that Akamai's flexibility allows you to easily fine-tune it to your needs.
Using Terraform Cloud / GitHub / GitLab instead of Azure DevOps - no problem. Managing your DNS elsewhere - easy. Want to template your caching rules even further through Property Manager Includes - possible too. Even the 'still-in-BETA' Terraform CDK is supported to write in different programming languages.
That said, the specific learning for this customer is around 'Unlimited' CDN hostnames.
The customer here wanted the ability to quickly spin up CDN hostnames / distributions quickly for their unique end-user, so a specific UUID had to be converted into a unique CDN hostname, complete with accurate traffic reporting, tracking, and HTTPS certification.Akamai has multiple solutions here allowing you to customize it to your needs. The best approach here is add a wildcard hostname in your delivery configuration such as *.cdn.securitylevelup.eu. All of the hostnames delivered on this subdomain will be properly delivered by Akamai.
Traffic reporting can be easily done by simply filtering on hostname. And then there is also the option to track each hostname with a unique Akamai CP Code.
If you also deploy a *.cdn.securitylevelup.eu HTTPS Certificate and a DNS CNAME record as a one-time action, you don't even need to go through the hassle of individually mapping each hostname and make dozens, if not hundreds of configuration changes.
Try it yourself...
So there you have it, just one of the many Akamai Terraform automation projects I have had the pleasure of working on. The great thing here is that you can easily replicate this yourself.
If you have an active Akamai account with both App & API Protector, Edge DNS and/or Dynamic Site Accelerator running, you should be able to follow along and use these templates to protect and deliver your web applications and/or API microservices.
The templates are compatible with Akamai Terraform Provider v6.0.0 or up and Terraform v.1.7.5 or up.
For more information about the Akamai Terraform Provider, you can find all of our documentation on Akamai TechDocs.
And of course, if you are looking for any guidance on your own Akamai automation project and need help, get in touch! I am happy to help out and ensure you are able to take advantage of all the latest Akamai Developer tooling - and in turn, your web apps and APIs more secure.
Thanks for reading and see you in the next one!
Subscribe to my newsletter
Read articles from Mike Elissen directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mike Elissen
Mike Elissen
In today's world, it is difficult to stay secure with your applications, APIs and data. I can help you. Mike Elissen, Developer Advocate @ Akamai Technologies.