🛡️"Enhanced Security Monitoring: The Ultimate Guide to Wazuh and OpenSearch with Logstash" 🚀
 Khushi Minipara
Khushi MiniparaIn today's digital world, cybersecurity is critical. To combat evolving threats, integrating Wazuh with OpenSearch using Logstash is key. Wazuh excels in threat detection, while OpenSearch offers scalable data analysis. By integrating with Logstash, organisations can streamline security monitoring, from data collection to visualisation. This blog guides you through setting up Wazuh, OpenSearch, and Logstash for enhanced cybersecurity. Let's dive in and empower your security operations!
Throughout this guide, we'll explore step-by-step instructions, best practices, and optimization techniques to ensure a seamless integration process.
Step 1 : Infrastructure Requirements.
For this blog's implementation, we'll be using an Ubuntu virtual machine (VM) as the environment for deploying Wazuh, OpenSearch, and Logstash. Here are the key components of our infrastructure:
Ubuntu VM: Ensure your VM meets the minimum system requirements for running Wazuh, OpenSearch, and Logstash efficiently. This includes sufficient RAM, CPU cores, and disk space.
Wazuh: As an open-source security monitoring platform, Wazuh requires specific ports for communication and data collection. By default, Wazuh uses ports such as 1514 (for syslog data), 55000 (for agent-manager communication), and 9200 (for OpenSearch integration). Please note that if there's a port conflict with OpenSearch, we'll adjust the port settings accordingly.
OpenSearch: Similarly, OpenSearch uses ports for various services such as HTTP (9200), HTTPS (9243), and the OpenSearch Dashboard port (5601). It's crucial to check for port conflicts, especially if Wazuh and OpenSearch are installed on the same VM.
Logstash: Logstash serves as the data processing pipeline between Wazuh and OpenSearch. It typically runs on port 5044 for receiving data from Beats or other sources. Ensure this port is available and not in use by other services
Step 2: Installation and Configuration of Wazuh, OpenSearch and OpenSearch Dashboard .
Wazuh : For deploying Wazuh, a powerful open-source security monitoring platform, we can either use the official documentation available here or with the help of Ansible playbooks that are available on my GitHub Repository. Using these playbooks you can automate the process of installation of wazuh components( User manual for running Ansible Playbook is here ). In this integration I have kept Wazuh and Opensearch on different VM to avoid port conflicts.
Opensearch : In addition to Wazuh, we'll have to install OpenSearch, a scalable and robust search and analytics engine. With OpenSearch, you can efficiently store, search, and analyze large datasets, complementing Wazuh's capabilities for enhanced security monitoring.
a. Download the Debian package for the desired version directly from the OpenSearch Downloads Page . The Debian Package can be downloaded for both x64 and arm64 architectures. The below given link is form x64 architecture.
wget https://artifacts.opensearch.org/releases/bundle/opensearch/2.13.0/opensearch-2.13.0-linux-x64.deb/
b. The command for installing OpenSearch using the provided Debian package and setting the initial admin password:
sudo env OPENSEARCH_INITIAL_ADMIN_PASSWORD=<custom-admin-password> dpkg -i opensearch-2.13.0-linux-x64.deb
Replace <custom-admin-password> with your desired password for the initial admin user during the installation process. This command uses dpkg to install the OpenSearch package from the Debian package file (opensearch-2.13.0-linux-x64.deb) and sets the initial admin password using the OPENSEARCH_INITIAL_ADMIN_PASSWORD environment variable.
c. Run these commands one after the other in your terminal to perform these actions sequentially: enabling OpenSearch to start on boot, starting the OpenSearch service, and checking its status to ensure it's running correctly.
sudo systemctl enable opensearch # Enable OpenSearch to start automatically on boot
sudo systemctl start opensearch # Start the OpenSearch service
sudo systemctl status opensearch # Check the status of the OpenSearch service
d. This command opens the opensearch.yml file located in the /etc/opensearch/ directory using the nano editor with root privileges. You can then make the necessary changes to the OpenSearch configuration using the nano editor interface.
sudo nano /etc/opensearch/opensearch.yml
Add following lines to the OpenSearch.yml file -
network.host: 0.0.0.0
discovery.type: single-node
plugins.security.disabled: false
Save your file and close the editor.
e. Firstly navigate to the OpenSearch configuration directory (/etc/opensearch), remove any existing PEM files, generate a private key for the root certificate (root-ca-key.pem), and then create a self-signed root certificate (root-ca.pem) using OpenSSL with specific subject information (-subj) such as country (C), state (ST), locality (L), organization (O), organizational unit (OU), and common name (CN).
cd /etc/opensearch
sudo rm -f *pem
sudo openssl genrsa -out root-ca-key.pem 2048
sudo openssl req -new -x509 -sha256 -key root-ca-key.pem -subj "/C=CA/ST=ONTARIO/L=TORONTO/O=ORG/OU=UNIT/CN=ROOT" -out root-ca.pem -days 730
Now generate an admin certificate and sign it with the previously created root certificate and private key:
sudo openssl genrsa -out admin-key-temp.pem 2048
sudo openssl pkcs8 -inform PEM -outform PEM -in admin-key-temp.pem -topk8 -nocrypt -v1 PBE-SHA1-3DES -out admin-key.pem
sudo openssl req -new -key admin-key.pem -subj "/C=CA/ST=ONTARIO/L=TORONTO/O=ORG/OU=UNIT/CN=A" -out admin.csr
# Sign the admin certificate with the root certificate and private key you created earlier.
sudo openssl x509 -req -in admin.csr -CA root-ca.pem -CAkey root-ca-key.pem -CAcreateserial -sha256 -out admin.pem -days 730
Then, create the node certificate and after the installation is successful, remove all temporary files that are not required. Later, make sure that the remaining certificates are owned by the OpenSearch user.
sudo openssl genrsa -out node1-key-temp.pem 2048
sudo openssl pkcs8 -inform PEM -outform PEM -in node1-key-temp.pem -topk8 -nocrypt -v1 PBE-SHA1-3DES -out node1-key.pem
# Create the CSR and replace the arguments passed to -subj so they reflect your specific host.
# The CN should match IP Address on which opensearch is installed.
sudo openssl req -new -key node1-key.pem -subj "/C=CA/ST=ONTARIO/L=TORONTO/O=ORG/OU=UNIT/CN=192.168.1.10" -out node1.csr
# Create an extension file that defines a SAN IP for the host. This
# should match the IP of the host.
sudo sh -c 'echo subjectAltName=IP:192.168.1.10 > node1.ext'
sudo openssl x509 -req -in node1.csr -CA root-ca.pem -CAkey root-ca-key.pem -CAcreateserial -sha256 -out node1.pem -days 730 -extfile node1.ext
sudo rm -f *temp.pem *csr *ext #Remove temporary files
sudo chown opensearch:opensearch admin-key.pem admin.pem node1-key.pem node1.pem root-ca-key.pem root-ca.pem #checking ownership
Now run following commands after removing similar commands present in opensearch.yml file located in the /etc/opensearch/ . The following commands will add this script with updated CN(do not forget to replace CN of node-key in following commands).
# Before running this script, make sure to replace the CN in the
# node's distinguished name with a real DNS A record.
echo "plugins.security.ssl.transport.pemcert_filepath: /etc/opensearch/node1.pem" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.ssl.transport.pemkey_filepath: /etc/opensearch/node1-key.pem" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.ssl.transport.pemtrustedcas_filepath: /etc/opensearch/root-ca.pem" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.ssl.http.enabled: true" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.ssl.http.pemcert_filepath: /etc/opensearch/node1.pem" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.ssl.http.pemkey_filepath: /etc/opensearch/node1-key.pem" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.ssl.http.pemtrustedcas_filepath: /etc/opensearch/root-ca.pem" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.allow_default_init_securityindex: true" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.authcz.admin_dn:" | sudo tee -a /etc/opensearch/opensearch.yml
echo " - 'CN=A,OU=UNIT,O=ORG,L=TORONTO,ST=ONTARIO,C=CA'" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.nodes_dn:" | sudo tee -a /etc/opensearch/opensearch.yml
echo " - 'CN=<your_ip_addr>,OU=UNIT,O=ORG,L=TORONTO,ST=ONTARIO,C=CA'" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.audit.type: internal_opensearch" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.enable_snapshot_restore_privilege: true" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.check_snapshot_restore_write_privileges: true" | sudo tee -a /etc/opensearch/opensearch.yml
echo "plugins.security.restapi.roles_enabled: [\"all_access\", \"security_rest_api_access\"]" | sudo tee -a /etc/opensearch/opensearch.yml
f. Restart OpenSearch service.
sudo systemctl restart opensearch
OpenSearch Dashboard : In conjunction with OpenSearch, the installation of OpenSearch Dashboards will be required. OpenSearch Dashboards is an advanced visualization tool that integrates seamlessly with OpenSearch. It enables users to explore, visualize, and analyze their data in real-time.
a. Download the Debian package using the following command -
wget https://artifacts.opensearch.org/releases/bundle/opensearch-dashboards/2.13.0/opensearch-dashboards-2.13.0-linux-x64.deb
b. After the Debian package is downloaded, install the debian package.
sudo dpkg -i opensearch-dashboards-2.13.0-linux-x64.deb
c. Reload systemd's configuration files to recognize any changes in service files, ensuring that the system manager is up-to-date, and then enable and start OpenSearch Dashboards service.
sudo systemctl daemon-reload
sudo systemctl enable opensearch-dashboards
sudo systemctl start opensearch-dashboards
sudo systemctl status opensearch-dashboards
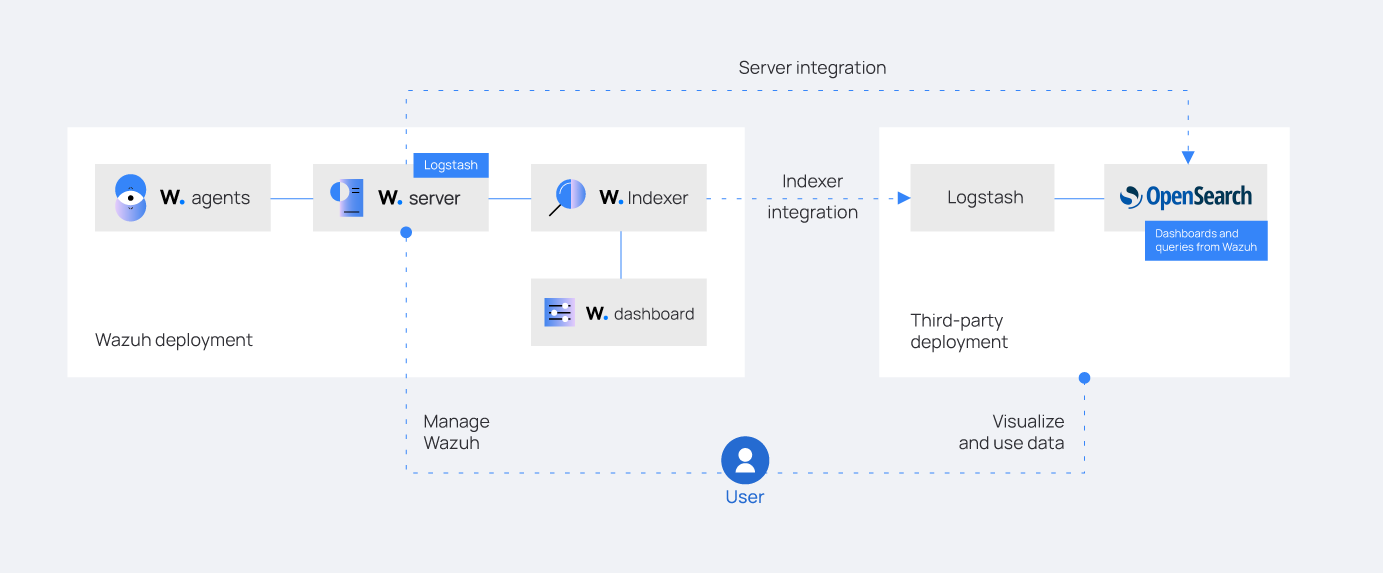
Step 3: Integration of Wazuh and OpenSearch using Logstash.
Logstash serves a crucial role in integrating Wazuh and OpenSearch by facilitating data ingestion, transformation, and forwarding. It acts as a data pipeline that collects security logs from Wazuh, processes them, and sends them to OpenSearch for storage and analysis. Logstash's installation involves adding the Elastic repository, updating package lists, and then installing Logstash, enabling seamless data flow between Wazuh and OpenSearch for enhanced security monitoring and threat detection.
a. Logstash Installation :
Firstly we will use below command to fetch the GPG key used to sign the Elastic package repositories and then the other command to pipe the output to the gpg command, which processes the GPG key and converts it from ASCII armor to binary format (using --dearmor). The resulting file is saved to /usr/share/keyrings/elastic-keyring.gpg, which can be used to verify the packages.
wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | sudo gpg --dearmor -o /usr/share/keyrings/elastic-keyring.gpg
The below command installs the apt-transport-https package, which allows the apt package manager to retrieve packages over the secure HTTPS protocol, ensuring the integrity and security of the packages being downloaded.
sudo apt-get install apt-transport-https
Now, we will have to add a new source list file for the Elastic 8.x packages. It saves the repository definition to /etc/apt/sources.list.d/elastic-8.x.list
echo "deb [signed-by=/usr/share/keyrings/elastic-keyring.gpg] https://artifacts.elastic.co/packages/8.x/apt stable main" | sudo tee -a /etc/apt/sources.list.d/elastic-8.x.list
The below command ensures that the system's package lists are up to date and then proceeds to install Logstash, enabling data processing and integration capabilities for various data sources, including Wazuh and OpenSearch.
sudo apt-get update && sudo apt-get install logstash
b. Install the logstash-input-opensearch (reading data from OpenSearch)and logstash-output-opensearch (writing data to OpenSearch)plugins using the following command:
sudo /usr/share/logstash/bin/logstash-plugin install logstash-input-opensearch logstash-output-opensearch
c. The below commands create two directories (wazuh-indexer-certs and opensearch-certs) under /etc/logstash/ to store the necessary root certificates securely and then copies the root-ca.pem certificate file from the Wazuh indexer's certificate directory (/etc/wazuh-indexer/certs/) to the newly created wazuh-indexer-certs directory in Logstash (/etc/logstash/) (my Wazuh is installed in some other VM so i copied my root certificate file at/home/khushi )and similarly copy certificate file from the OpenSearch certificate directory (/etc/opensearch/) to the newly created opensearch-certs directory in Logstash (/etc/logstash/).
mkdir /etc/logstash/wazuh-indexer-certs
mkdir /etc/logstash/opensearch-certs
cp /home/khushi/root-ca.pem /etc/logstash/wazuh-indexer-certs
cp /etc/opensearch/root-ca.pem /etc/logstash/opensearch-certs
d. The below two commands are used to grant the Logstash user read permissions (755) for the copied Wazuh Indexer and OpenSearch root certificates. This ensures that Logstash can access and use these certificates securely for communication with the respective services.
sudo chmod -R 755 /etc/logstash/wazuh-indexer-certs/root-ca.pem
sudo chmod -R 755 /etc/logstash/opensearch-certs/root-ca.pem
e. The command first create directory and then fetches the specified JSON template file from the Wazuh repository and saves it as wazuh.json in the specified directory (/etc/logstash/templates/). This template is used for configuring index initialization in OpenSearch via Logstash.
mkdir /etc/logstash/templates
curl -o /etc/logstash/templates/wazuh.json https://packages.wazuh.com/integrations/opensearch/4.x-2.x/dashboards/wz-os-4.x-2.x-template.json
f. The below commands disable history recording temporarily, set a Logstash Keystore password in the system configuration file, and then enable history recording. Additionally, they adjust file permissions and start the Logstash service, ensuring secure password storage and service functionality.
set +o history
echo 'LOGSTASH_KEYSTORE_PASS="<MY_KEYSTORE_PASSWORD>"'| sudo tee /etc/sysconfig/logstash
export LOGSTASH_KEYSTORE_PASS=<MY_KEYSTORE_PASSWORD>
set -o history
sudo chown root /etc/sysconfig/logstash
sudo chmod 600 /etc/sysconfig/logstash
sudo systemctl start logstash
Replace "<MY_KEYSTORE_PASSWORD>" with the password you want to store for your Keystore.
g. Now we will have to securely store the credentials of the Wazuh indexer and OpenSearch in the Logstash keystore. Firstly, we will create a Logstash Keystore in the specified path :
sudo -E /usr/share/logstash/bin/logstash-keystore --path.settings /etc/logstash create
After entering the below commands, you will be prompted to enter your credentials of OpenSearch and Wazuh indexer in the Logstash Keystore. The credentials will not be visible as you enter them so enter them very carefully.
sudo -E /usr/share/logstash/bin/logstash-keystore --path.settings /etc/logstash add OPENSEARCH_USERNAME
sudo -E /usr/share/logstash/bin/logstash-keystore --path.settings /etc/logstash add OPENSEARCH_PASSWORD
sudo -E /usr/share/logstash/bin/logstash-keystore --path.settings /etc/logstash add WAZUH_INDEXER_USERNAME
sudo -E /usr/share/logstash/bin/logstash-keystore --path.settings /etc/logstash add WAZUH_INDEXER_PASSWORD
h. This command creates a new configuration file named wazuh-opensearch.conf in the /etc/logstash/conf.d/ directory. It's a blank file that will be used to define Logstash parameters.
sudo touch /etc/logstash/conf.d/wazuh-opensearch.conf
Now open the wazuh-opensearch.conf file in the nano text editor using below command :
sudo nano /etc/logstash/conf.d/wazuh-opensearch.conf
Once the editor opens try to add following configuration and modify it with your <WAZUH_INDEXER_ADDRESS> and <OPENSEARCH_ADDRESS>. If you have set some other path to the certificate file, then make sure to replace that too.
input {
opensearch {
hosts => ["<WAZUH_INDEXER_ADDRESS>:9200"]
user => "${WAZUH_INDEXER_USERNAME}"
password => "${WAZUH_INDEXER_PASSWORD}"
index => "wazuh-alerts-4.x-*"
ssl => true
ca_file => "/etc/logstash/wazuh-indexer-certs/root-ca.pem"
query => '{
"query": {
"range": {
"@timestamp": {
"gt": "now-1m"
}
}
}
}'
schedule => "* * * * *"
}
}
output {
opensearch {
hosts => ["<OPENSEARCH_ADDRESS>"]
auth_type => {
type => 'basic'
user => '${OPENSEARCH_USERNAME}'
password => '${OPENSEARCH_PASSWORD}'
}
index => "wazuh-alerts-4.x-%{+YYYY.MM.dd}"
cacert => "/etc/logstash/opensearch-certs/root-ca.pem"
ssl => true
template => "/etc/logstash/templates/wazuh.json"
template_name => "wazuh"
template_overwrite => true
legacy_template => false
}
}
Step 4: Running Logstash .
After configuring Logstash for Wazuh-OpenSearch integration, stop Logstash temporarily and then test your configuration by running Logstash from the CLI with your configuration file wazuh-opensearch.conf using below commands:
sudo systemctl stop logstash
sudo -E /usr/share/logstash/bin/logstash -f /etc/logstash/conf.d/wazuh-opensearch.conf --path.settings /etc/logstash/
Once confirmed, cancel the command and start Logstash as a service for better reliability. Enable Logstash and start the Logstash as a service using the below 2 commands. This setup ensures Logstash runs consistently and independently of the terminal's lifecycle, improving system stability and automation.
sudo systemctl enable logstash
sudo systemctl start logstash
Step 5: Verify the Integration.
Now in order to verify the integration, we will have to create the index pattern name for Wazuh alerts in OpenSearch Dashboards. The steps are as follows:
a. Go to Management in OpenSearch Dashboards by selecting the ☰ icon and then choosing Management > Dashboards Management.
b. In the Management section, click on Index Patterns and then click on Create index pattern.
c. Enter wazuh-alerts-* as the index pattern name in the provided field.
d. Choose timestamp as the primary time field. This field will be used with the global time filter for time-based data visualization.
e. Click on Create index pattern to finalize and create the index pattern for Wazuh alerts.
f. To view and explore the data, navigate to the menu and select Discover under OpenSearch Dashboards. This will allow you to analyze and visualize the Wazuh alerts using the created index pattern.
By seamlessly transferring Wazuh alerts to OpenSearch, organizations can gain real-time visibility and actionable insights into security events. This integration would streamline incident detection and response, enhance data visualization capabilities, and strengthen overall security operations, leading to improved threat detection and mitigation strategies.
Subscribe to my newsletter
Read articles from Khushi Minipara directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
