What is AWS Shield and How is it Different from Cloudflare DDoS Protection?
 SK
SK
Before we start, a quick glossary of terms...
Application Layer [1]
An application layer is an abstraction layer that specifies the shared communication protocols and interface methods used by hosts in a communications network. An application layer abstraction is specified in both the Internet Protocol Suite (TCP/IP) and the OSI model.
In the OSI model, the definition of the application layer is narrower in scope. The OSI model defines the application layer as only the interface responsible for communicating with host-based and user-facing applications.
Attack Surface [2]
The attack surface of a software environment is the sum of the different points (for "attack vectors") where an unauthorized user (the "attacker") can try to enter data to, extract data, control a device or critical software in an environment. Keeping the attack surface as small as possible is a basic security measure.
Cloud Security [3]
Cloud computing security or, more simply, cloud security, refers to a broad set of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, services, and the associated infrastructure of cloud computing. It is a sub-domain of computer security, network security, and, more broadly, information security.
Content Delivery Network [4]
A content delivery network or content distribution network (CDN) is a geographically distributed network of proxy servers and their data centers. The goal is to provide high availability and performance by distributing the service spatially relative to end users.
DDoS attack [5]
In computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a network.
In a distributed denial-of-service attack (DDoS attack), the incoming traffic flooding the victim originates from many different sources.
OSI Model [6]
The Open Systems Interconnection (OSI) model is a reference model from the International Organization for Standardization (ISO) that "provides a common basis for the coordination of standards development for the purpose of systems interconnection." In the OSI reference model, the communications between systems are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application.
Web Application Firewall [7]
A web application firewall (WAF) is a specific form of application firewall that filters, monitors, and blocks HTTP traffic to and from a web service. By inspecting HTTP traffic, it can prevent attacks exploiting a web application's known vulnerabilities, such as SQL injection, cross-site scripting (XSS), file inclusion, and improper system configuration.
So How Do You Protect Your Stuff on the ‘nets Anyways?
You have infrastructure, applications, and data out the in the big Cloud in the sky. How do you keep all these safe and secure?
With Cloud Security of course.
Cloud Security is a broad set of measures and controls utilized to protect your computing stuff in the cloud. Cloud Security is important because threats exist. Threats such as data loss, unauthorised access, damage to computer systems and networks, etc. To make things worse, the attacks and breaches to those computer systems and networks used to carry out those threats can come from all directions and in different forms. It’s a wild, wild west out there. Luckily, most cloud providers do implement some form of best security practices.
Other than that, we will be having a look at a particular insidious form of attack called a DDoS attack for our discussion.
Why DDoS Attacks are Such a Big Headache?
A DDoS (Distributed Denial-of-Service) is a malicious attack that is designed to bring your resources to their knees and make them crash such that they are unable to serve your real users, thus the “denial of service” part. This is done by flooding your resources - whether server, service, or network - with lots of Internet traffic coming from compromised or controlled sources across the Internet all at once.
Being hit by a DDoS is bad because your systems or service could be down for hours even days. You could lose revenue. You might suffer reputational damage. Your cloud computing bill might balloon.
The discussion on DDoS attacks would not be complete if we didn’t go deeper into how Internet systems are interconnected.
This is where the Open Systems Interconnection (OSI) model comes in. The OSI model is a reference model on how the Internet works basically. The OSI model also enables different systems to communicate using standard protocols. It breaks down network communication into 7 abstraction layers : physical, data link, network, transport, session, presentation, and application.
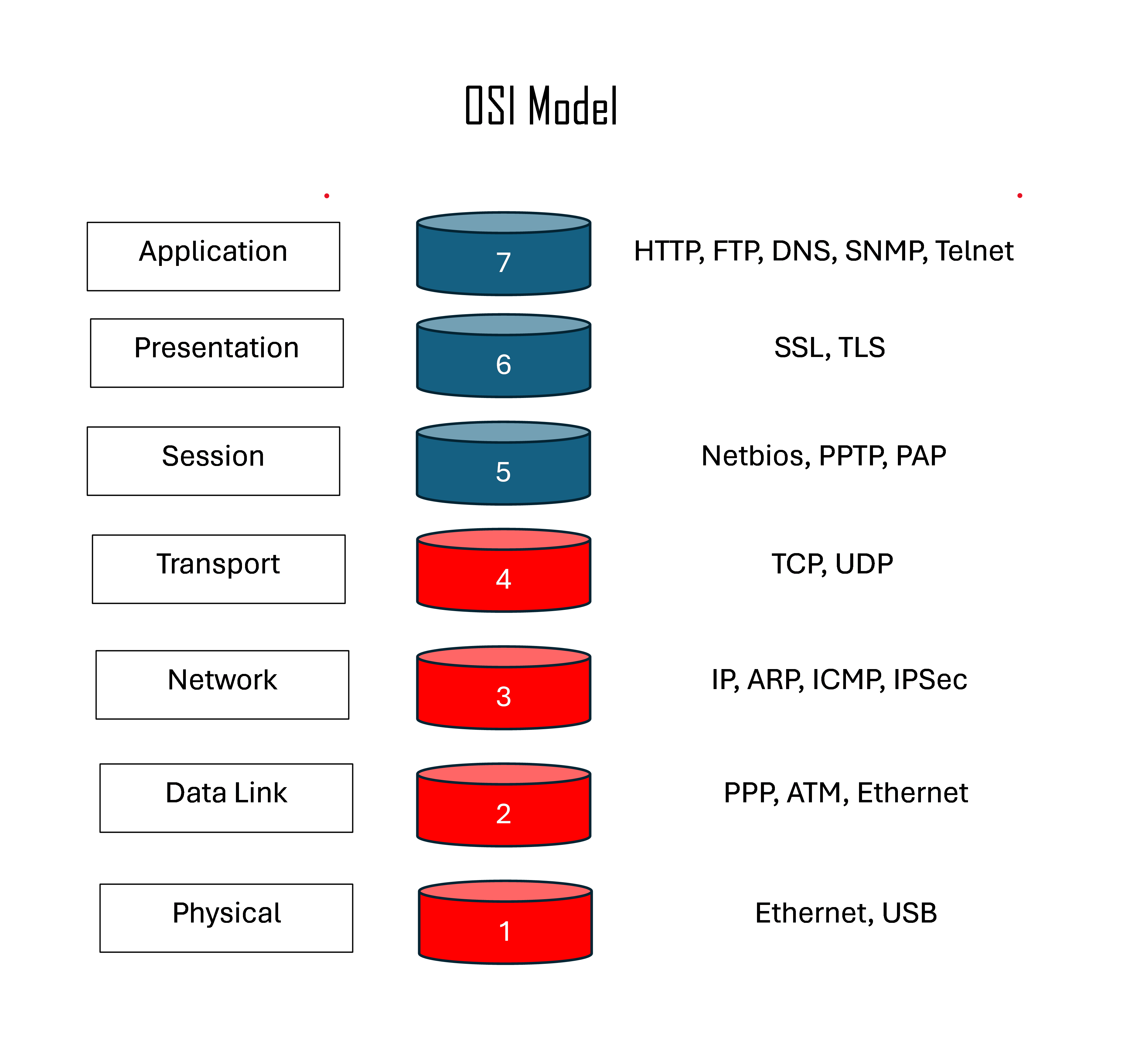
DDoS attacks are classified according to which layer of the OSI layer they are targeting. They are common in layer 3 (network), layer 4 (transport), layer 6 (presentation), and layer 7 (application).
To protect against DDoS attacks or at least to mitigate against them, it is recommended to reduce the “surface area” against which an unauthorized person can attack, for starters.
One very useful prevention strategy is to use a WAF (Web Application Firewall). Web application firewalls are used to filter HTTP traffic to and from your web service. Web Application Firewalls mostly analyse the GET and POST part of HTTP requests. GET requests retrieve data from the server, and POST requests send data to the server.
CDN (Content Delivery Networks) are also a good place to go to counteract against DDoS attacks. CDNs consists of servers that are distributed across different geographical areas that cache content and deliver it closer to users’ locations. CDNs can speed up the loading of a data-heavy web page, for example, by bringing content closer and faster to where the user is requesting a resource.
The beauty of CDNs, in the case of DDoS attacks, is that they can distribute load across their network of servers, reducing the impact on the original server.
Luckily, depending on your cloud provider, the mitigation options discussed above will be available in the form of services to protect your stuff on the internets.
AWS and Cloudflare: Two Leading Cloud Providers
AWS (Amazon Web Services) is a cloud computing provider that delivers IT resources on-demand across the Internet using a pay-as-go pricing model. AWS has been around since the early 2000s. And is one of the most popular cloud service providers according to market share. Cloudflare, the company, on the other hand, offers a wide range of products and solutions for clients to improve the security and performance of their websites and services.
Both AWS and Cloudflare offer services to protect and mitigate against DDoS attacks. They both offer WAFs and CDNs, for example.
But what we are interested in the most is their offerings specifically designed against DDoS attacks.
Introducing AWS Shield and Cloudflare DDoS Protection
AWS Shield is a service to protect your resources against DDoS attacks. AWS Shield comes in two flavours: AWS Shield Standard (a free service already activated for all customers of AWS) and AWS Shield Advanced (an optional premium service where you get protection against more sophisticated DDoS attacks)
Cloudflare DDoS Protection on the other hand, gives unmetered, and unlimited DDoS protection at layers 3, 4, and 7 to all its customers on all its services and all plans (there are free and paid plans).
AWS Shield is a managed serviced (meaning AWS fully takes care of managing and monitoring the underlying infrastructure) which provides always-on detection against DDoS attacks. AWS Shield is tightly integrated with other AWS services.
Cloudflare DDoS Protection needs to be configured separately and integrated with your existing infrastructure. It detects and mitigates against DDoS attacks automatically.
It should be mentioned that these services (AWS Shield and Cloudflare DDoS Protection) may and should be supplemented with other security services such as WAFs and CDNs for extra protection.
So, what do you think?
AWS Shield or Cloudflare DDoS Protection?
References:
1. Wikipedia, https://en.wikipedia.org/wiki/Application_layer [Last accessed 30/04/2024]
2. Wikipedia, https://en.wikipedia.org/wiki/Attack_surface [Last accessed 01/05/2024]
3. Wikipedia, https://en.wikipedia.org/wiki/Cloud_computing_security [Last accessed 30/04/2024]
4. Wikipedia, https://en.wikipedia.org/wiki/Content_delivery_network [Last accessed 01/05/2024]
5. Wikipedia, https://en.wikipedia.org/wiki/Denial-of-service_attack [Last accessed 30/04/2024]
6. Wikipedia, https://en.wikipedia.org/wiki/OSI_model [Last accessed 01/05/2024]
7. Wikipedia, https://en.wikipedia.org/wiki/Web_application_firewall [Last accessed 01/05/2024]
Subscribe to my newsletter
Read articles from SK directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

SK
SK
I am aspiring to be a well-rounded full stack developer and data engineer. I am currently enrolled for BSc Mathematics and Computer Science. I have recently added AWS Certified Cloud Practitioner to my arsenal.