Part 3 : The public key infrastructure and certificate management
 Sai Keerthan Kasula
Sai Keerthan KasulaTable of contents

With respect to my previous articles, I explained how encryption and decryption are performed, including the elements used for the hybrid encryption.
As we know, we use two keys for asymmetric encryption: a public key and a private key. The term "public" refers to the fact that the key is made available to all the parties involved in the communication process.
What happens if the key is tampered with? How can we ensure that the public key being shared with you is authentic and comes from the actual sender? What if certificates are compromised and the sender is unaware and uses them for communication?
Let's explore solutions to these concerns with relevant examples and address the risks of insecure communication.
Let's imagine ram and arjun are the two parties involved in the communication process:
Arjun wants to send a message to ram by encrypting the message using the ram's public key.
Ram gonna share his public key to arjun, but arjun is not sure about the key that it is not genuine.
Now, how do arjun ensure that the key received from ram is genuine and can be used for communication?.
This is where public key infrastructure comes in.
Public Key Infrastructure
Definition: The Public key infrastructure (PKI) is the set of hardware, software, policies, processes, and procedures required to create, manage, distribute, use, store, and revoke digital certificates and public-keys.
PKIs help establish the identity of people, devices, and services – enabling controlled access to systems and resources, protection of data, and accountability in transactions.
The Certificate Authority (CA)
A certificate authority is a company or organization that acts to validate the identities of entities (such as websites, email addresses, companies, or individual persons) and bind them to cryptographic keys through the issuance of electronic documents known as**digital certificates.**
So, Continuing with our example, public key infrastructure ensures that Arjun receives a well-trusted and authentic public certificate from Ram. Here, the certificate authority binds Ram’s identity to a public certificate, acting as a provider of Ram's identity.
After Arjun receives the certificate, he validates Ram's identity with the help of the certificate authority.
For example, let's examine the certificate issued to Google.
Below, you can see that Google is identified by the common name (CN) - *.google.com, and the certificate is issued by GTS CA 1C3.
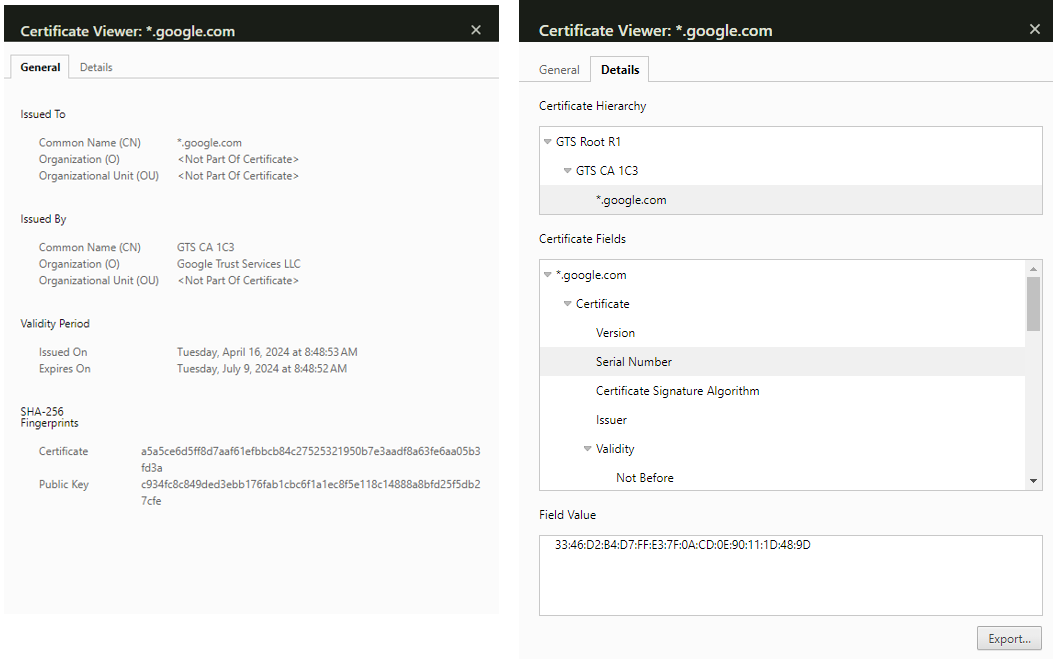
Each certificate is identified by a unique serial number and includes a date and time specifying when it should be used and when it expires.
How to check whether certificate can be used for the communication, is revoked by the CA?
This is where we actually need a list of certificate serial numbers that are not supposed to be used for any kind of communication or to perform cryptographic operations. The term for that list is called as "Certificate Revocation List (CRL)."
Note: You must be wondering that if CA validates a person, company or an organization who validates the certificate authorities then, In india, we have Controller of Certifying Authorities (CCA) to license and regulate the working of certifying Authorities which is controlled by ministry of electronics and information technology.
So here is the hierarichy:
Organization certificate > issued by CA > CA is identified by CCA. This hierarchy is called as "Certificate Chain of Trust".
In continuation, after checking the CRL list whether it contains the received ram's certificate serial number, arjun actually validates the ram identity using the certificate chain of trust and accepts the ram's certificate to proceed for the communcation.
Conclusion
In this article we have learnt how public keys are exchanged and validated to perform secure communication.
In my next article, let us explore about process of SSL HandShake and let us actually create our own public and private keys using the openSSL commands.
Follow me for more such content !
Regards,
Sai Keerthan Kasula, Jr. Software Developer.
Subscribe to my newsletter
Read articles from Sai Keerthan Kasula directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sai Keerthan Kasula
Sai Keerthan Kasula
Embracing this journey, eager to confront new challenges daily and strive towards becoming the best version of myself.