The Importance of HTTPS for API Security
 Venkatakumar Chembati
Venkatakumar Chembati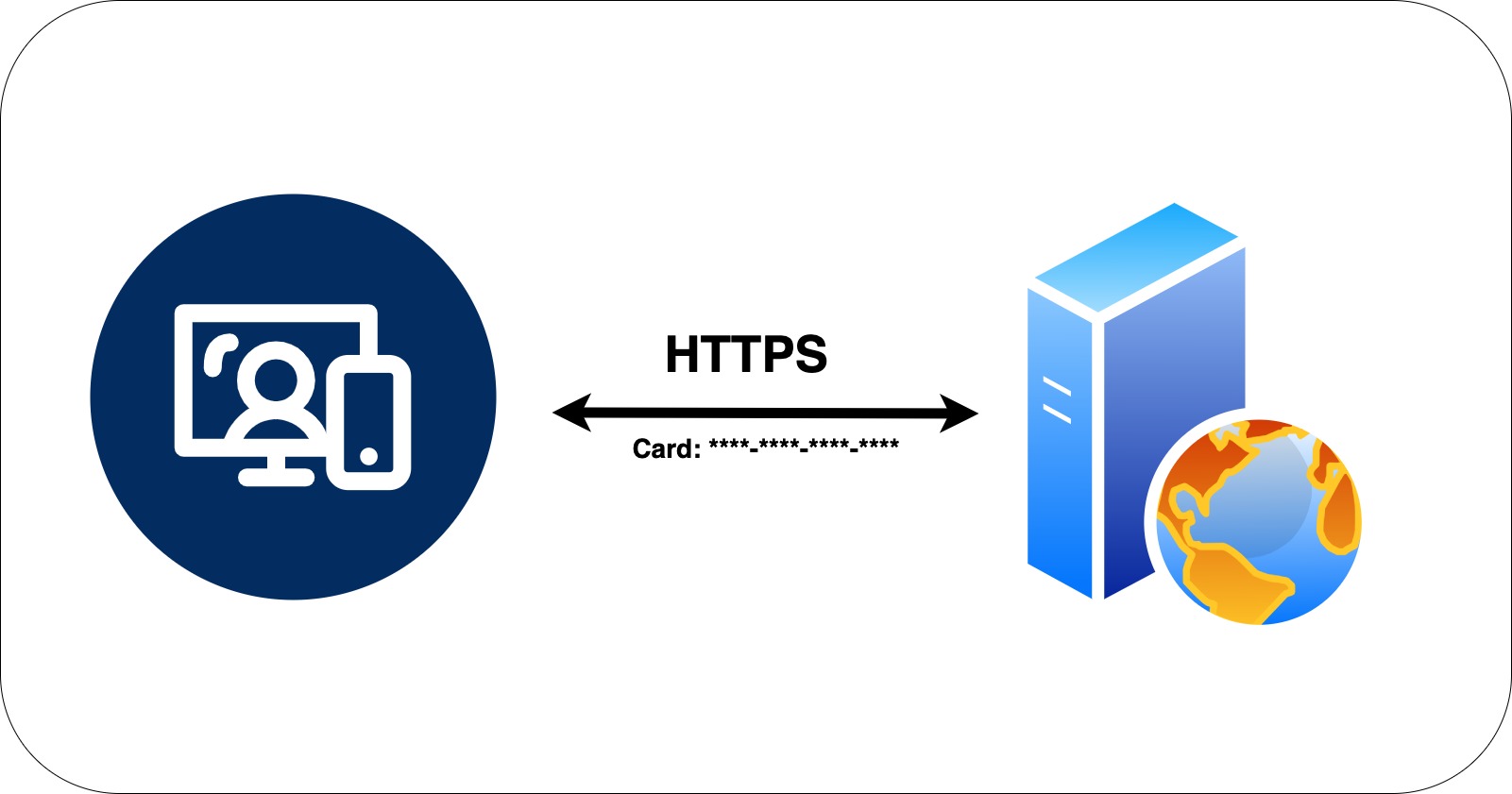
What is so crucial about HTTPs in today's digital landscape that most websites mandate its use? In this article, we delve into the differences between HTTP and HTTPs. To understand better about this concept, let's explore the fundamentals of TLS/SSL and encryption.
We all understand that APIs are significant for business and for their smooth functioning. But, How can we ensure that data being sent in the request and received from response are secure between client and server. It is important to secure the data transmission, otherwise, attackers can intercept the requests which can lead to data disclosure.
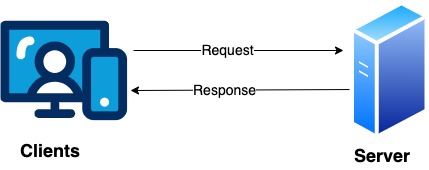
When a client request is being sent to the server, we should be certain about the following things.
How can a client make sure that it is communicating with the intended server?
Is the data received from the receiver or sender reliable? How can we ensure on the data integrity?
How can we make sure the data is not read by attackers during the transmission?
So, we need to utilize a framework or a model that secures the data which prevents attacks during transmission.
HTTP
HTTP is an application-level protocol used for communication between the client and the server. With HTTP, the data exchanged between the client and the server is in plain text and not secure.
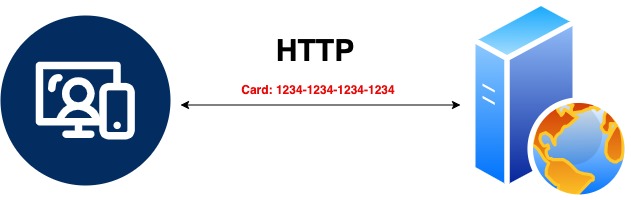
For instance, when making an online purchase and the website requests payment to finalize the order, using HTTPS ensures that the entered card information is secure and cannot be read by anyone on the internet.
HTTPS
HTTPs is an extension for HTTP and the data exchanged between the client and the server is encrypted.

Https achieves the secure transmission using Transport Layer Security (TLS).
Transport Layer Security (TLS)
Transport Layer Security(TLS) is a cryptographic protocol that permits the secure transmission of data between client and the server.
When TLS is used, the server is able to authenticate with the client using a digital certificate. Digital certificates are public certificates in the form of files used by clients to verify the server identity and authenticates themselves. This TLS authentication process ensures secure data transmission, thus prevents attacks during data transmission.
TLS uses both Asymmetric and symmetric encryption. Asymmetric encryption is used to establish a secure session between client and the server, and symmetric encryption is used to exchange the data with in that session.
Let's see how TLS handshake happens using the below diagram.
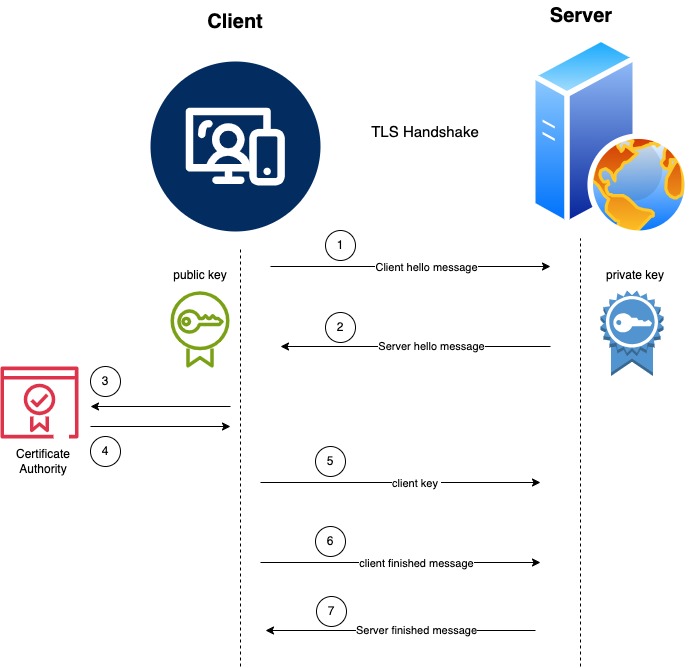
Client sends hello message to the server along with TLS/SSL version, client random and the cryptographic algorithm it supports.
Server responds back with server's random, session, cryptographic algorithm it received from the client and the digital certificate. The digital signature is produced using a private key at the server side. The server also sends the public key to the client during this process.
Client verifies the digital certificate with certificate authority and validate the authenticity of the server.
If the certificate is not valid, then the client fails the authenticity of the server. This can happen when an invalid certificate or expired certificate is received from the server. This way, the server authenticates with the client. Until this step, TLS established a secure session using asymmetric key.
Now client generates another string called premaster secret, which is then encrypted using client's public key and sends over to the server. The server then decrypts this premaster secret with it's private key. Now, both client and the server can generate the same symmetric key using client random, server random and premaster secret. This symmetric is used for exchanging the data in the secure session.
The client sends the finished message indicating the client end of handshake is completed. This is the first message that is encrypted using the symmetric key.
The server then responds back with it's own finished message indicating the server end of handshake. This message is the first message that is encrypted using the symmetric key from server side. After this, each message is encrypted using the same symmetric key from both parties.
As we can see TLS uses both asymmetric and symmetric encryption. Asymmetric encryption is slow and symmetric encryption has no built-in mechanism for secure exchange of the key. So TLS uses asymmetric encryption for establishing secure session and helps to share the symmetric key which is then used for encrypting the data.
In conclusion, understanding the differences between HTTP and HTTPs is crucial in today's digital landscape. While HTTP transmits data in plain text, HTTPs encrypts the data exchanged between the client and the server using Transport Layer Security (TLS).
Implementing HTTPs ensures secure data transmission, preventing attacks during communication. By utilizing TLS, which combines asymmetric and symmetric encryption, websites can authenticate servers, establish secure sessions, and encrypt data for safe transmission. It is evident that adopting HTTPs is essential for maintaining data integrity and security in online interactions.
Subscribe to my newsletter
Read articles from Venkatakumar Chembati directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Venkatakumar Chembati
Venkatakumar Chembati
Solutions Architect | Product Design & Development | Cloud-Native Microservices | Distributed Applications (Back-End)