CI/CD for Netflix Application
 sumit Jeswani
sumit Jeswani
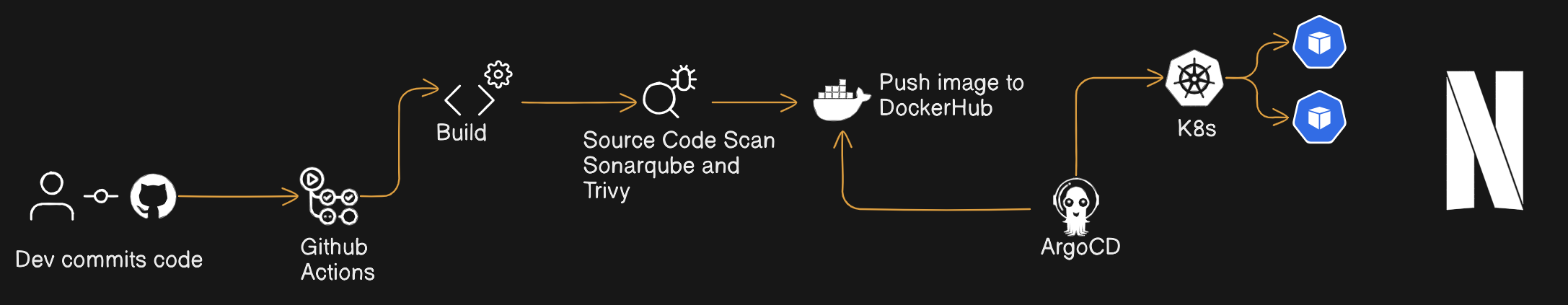
This project outlines the Continuous Integration and Continuous Deployment (CI/CD) pipeline set up for a Netflix clone application deployed on a local Kubernetes cluster. The pipeline automates the process of building, testing, and deploying application updates, ensuring efficiency and reliability in the development and deployment lifecycle.
Tools Used:
GitHub: Code versioning platform used for hosting the application's source code.
GitHub Actions: CI/CD workflow automation tool integrated with GitHub for building, testing, and deploying applications.
SonarQube: Static code analysis tool utilized for scanning the source code to identify and fix code quality issues.
Trivy: Vulnerability scanner for containers, for scanning both the source code and Docker images for security vulnerabilities.
Docker Hub: Image registry service for storing Docker images built during the CI/CD process.
Kubernetes: Container orchestration platform, for deploying, scaling, and managing containerized applications.
Argo CD: GitOps continuous delivery tool, for deploying applications on Kubernetes clusters from Git repositories.
CI/CD Workflow:
Developer Pushes Code Update:
- Whenever a developer pushes code changes to the GitHub repository, it triggers the CI/CD pipeline.
GitHub Actions Workflow:
The GitHub Actions workflow is triggered, initiating the automated CI/CD process.
Source code is scanned using SonarQube and Trivy to identify code quality issues and security vulnerabilities.
Upon successful code analysis, the Docker image is built and pushed to Docker Hub.
Image Scanning:
- Trivy scans the Docker image for security vulnerabilities, ensuring that only secure images are deployed.
Update Kubernetes Deployment:
The CI/CD pipeline updates the image tag in the GitHub Kubernetes deployment file with the newly built Docker image.
This ensures that the Kubernetes deployment always uses the latest version of the application image.
Argo CD Deployment:
The updated Kubernetes deployment file triggers Argo CD, initiating the deployment process.
Argo CD synchronizes the desired state defined in the Git repository with the actual state of the Kubernetes cluster.
The application is deployed or updated on the local Kubernetes cluster based on the changes in the Git repository.
The CI/CD pipeline outlined above streamlines the development and deployment of the Netflix clone application on a local Kubernetes cluster. By leveraging automation and various tools, the pipeline enhances efficiency, reliability, and security throughout the software development lifecycle.
name: CI
on: [workflow_dispatch, push] # Manually run workflow and trigger on push
# A workflow run is made up of one or more jobs that can run sequentially or in parallel
jobs:
# Job-1 Build
build:
name: Build
runs-on: ubuntu-latest
steps:
- name: Checkout repo
uses: actions/checkout@v4
- name: Set up Node
uses: actions/setup-node@v3
with:
node-version: 18
- name: Install dependencies
run: npm install
- name: Build project
run: npm run build
# Job-2 Source Code Scan
Code_Scan:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
with:
# Disabling shallow clones is recommended for improving the relevancy of reporting
fetch-depth: 0
- name: SonarQube Scan
uses: kitabisa/sonarqube-action@v1.2.0
with:
host: ${{ secrets.SONAR_HOST_URL }}
login: ${{ secrets.SONAR_TOKEN }}
- name: Trivy filesystem Scan
run: |
#install trivy
sudo apt-get install wget apt-transport-https gnupg lsb-release -y
wget -qO - https://aquasecurity.github.io/trivy-repo/deb/public.key | gpg --dearmor | sudo tee /usr/share/keyrings/trivy.gpg > /dev/null
echo "deb [signed-by=/usr/share/keyrings/trivy.gpg] https://aquasecurity.github.io/trivy-repo/deb $(lsb_release -sc) main" | sudo tee -a /etc/apt/sources.list.d/trivy.list
sudo apt-get update
sudo apt-get install trivy -y
#command to scan files
trivy fs .
# Job-3 Push Docker image to Docker Hub and update image tag in deplyment.yml file
Push_Image:
runs-on: ubuntu-latest
steps:
- name: Set up QEMU
uses: docker/setup-qemu-action@v3
- name: Set up Docker Buildx
uses: docker/setup-buildx-action@v3
- name: Login to Docker Hub
uses: docker/login-action@v3
with:
username: ${{ secrets.DOCKERHUB_USERNAME }}
password: ${{ secrets.DOCKERHUB_TOKEN }}
- name: Build and push
uses: docker/build-push-action@v5
with:
push: true
tags: sumitjeswani/netflix:${{ github.sha }}
build-args: |
TMDB_V3_API_KEY=${{ secrets.TMDB_API_KEY }}
- name: Run Trivy vulnerability scanner
uses: aquasecurity/trivy-action@master
with:
image-ref: "docker.io/sumitjeswani/netflix:${{ github.sha }}"
format: 'table'
exit-code: '1'
ignore-unfixed: true
vuln-type: 'os,library'
severity: 'CRITICAL,HIGH'
- name: Trivi Image Scan
if: false # This another way to scan using trivy
run: |
#install trivy
sudo apt-get install wget apt-transport-https gnupg lsb-release -y
wget -qO - https://aquasecurity.github.io/trivy-repo/deb/public.key | gpg --dearmor | sudo tee /usr/share/keyrings/trivy.gpg > /dev/null
echo "deb [signed-by=/usr/share/keyrings/trivy.gpg] https://aquasecurity.github.io/trivy-repo/deb $(lsb_release -sc) main" | sudo tee -a /etc/apt/sources.list.d/trivy.list
sudo apt-get update
sudo apt-get install trivy -y
#command to scan files
trivy image docker.io/sumitjeswani/netflix:${{ github.sha }}
- name: Checkout repo
uses: actions/checkout@v3
- name: Update image in deployment.yaml
working-directory: ./Kubernetes
run: |
sed -i 's|sumitjeswani/netflix:.*|sumitjeswani/netflix:'${{ github.sha }}'|' deployment.yml
git config --global user.name 'Sumit Jeswani'
git config --global user.email 'jeswanisumit1999@gmail.com'
git add deployment.yml
git commit -m "Update deployment.yml"
git push
Github repo link - https://github.com/jeswanisumit1999/Netflix-clone/
Subscribe to my newsletter
Read articles from sumit Jeswani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
