Amazon API Gateway - Part2
 Utkarsh Rastogi
Utkarsh Rastogi
Amazon Cloud Concepts Learning --> Day16
API Gateway Caching
By setting up an Amazon API Gateway cache and indicating its gigabyte capacity, you may add caching to API requests.
The endpoint's response can be cached thanks to caching.
Caching can decrease the number of times a request is sent to the backend and increase the API's response time.
For a predetermined period (known as the time to live, or TTL), API Gateway caches replies.
300 seconds is the standard TTL (min 0, max 3600).
Caches are defined per Stage.
Only GET methods have caching enabled by default.
Caches are encrypted.
The cache has a capacity of 0.5 GB to 237 GB.
For methods, cache settings can be overridden.
If necessary, you can instantly invalidate or flush the whole cache.
Clients can use the header Cache-Control: max-age=0 to invalidate the cache
API Gateway Throttling
The ability to throttle the number of requests per second (RPS) that your API may get from a single client or from all clients is known as API gateway throttling.
Throttling ensures dependable performance and availability by preventing your backend services from being overloaded by an unexpected spike in requests.
API Gateway throttling-related settings are applied in the following order:
Per-client or per-method throttling limits that you set for an API stage in a usage plan
Per-method throttling limits that you set for an API stage
Account-level throttling per region
AWS Regional throttling
Security recommended practices in Amazon API Gateway
You should consider the many security aspects that API Gateway offers when creating and implementing your own security rules. The following best practices do not constitute a comprehensive security solution; rather, they are only broad recommendations. Consider these best practices as useful suggestions rather than rules, as they may not be suitable or adequate for your situation.
Use least privilege access
Least privilege access may be implemented using IAM rules for the creation, reading, updating, and deletion of API Gateway APIs.
Put logging in place
To record API requests, use CloudWatch Logs or Amazon Data Firehose.
Set up alerts for Amazon CloudWatch
You observe a single measure over a predetermined period by using CloudWatch alerts.
Turn on CloudTrail on AWS
A record of the activities performed by a user, role, or AWS service in API Gateway is provided by CloudTrail.
Turn on AWS Config
Configuring your API Gateway resources according to AWS Config guidelines is the best option.
Make use of the AWS Security Hub
Utilizing AWS Security Hub, keep an eye on how you are utilizing API Gateway in relation to security best practices.
API Gateway Lambda Authorizers
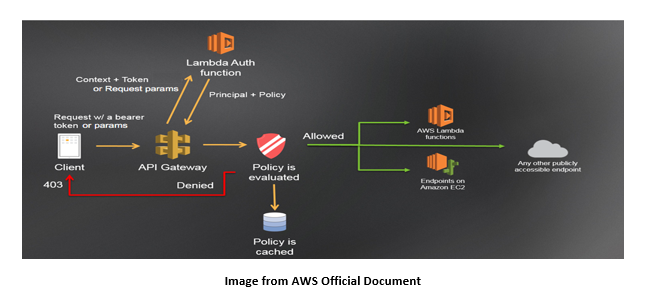
Control access to your API by utilizing a Lambda authorizer, which was originally called a custom authorizer.
Your Lambda authorizer is called by API Gateway when a customer requests a method on your API. The caller's identity is received as input by the Lambda authorizer, which outputs an IAM policy.
To put in place a unique authorization mechanism, use a Lambda authorizer. Your system can employ a bearer token authentication technique like OAuth or SAML, or it can use request parameters to ascertain the caller's identity.
There are two types of lambda authorizer
Request parameter-based lambda authorizer (REQUEST authorizer)
A REQUEST authorizer receives the caller's identity in a combination of headers, query string parameters, stageVariables, and $context variables.
Token based lambda authorizer (TOKEN authorizer)
A TOKEN authorizer receives the caller's identity in a bearer token, such as a JSON Web Token (JWT) or an OAuth token.
Limitations
Below mentioned tables includes some basic limitations
| Name | Default | Adjustable |
| Regional APIs per region | 600 | No |
| Edge-optimized APIs per region | 120 | No |
| Stages per API | 10 | Yes |
| Authorizers per API | 10 | Yes |
Additional Resources
https://aws.amazon.com/api-gateway/faqs/
"Thank you for reading! If you found this blog helpful, don't forget to subscribe and follow for more insightful content. Your support keeps me motivated to bring you valuable insights. Stay updated and never miss out on our latest posts. Feel free to leave comments or suggestions for future topics. Happy learning!"
https://awslearner.hashnode.dev/amazon-web-services-via-category
Subscribe to my newsletter
Read articles from Utkarsh Rastogi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Utkarsh Rastogi
Utkarsh Rastogi
👨💻 AWS Cloud Engineer | Around 6 years of Corporate Experience | Driving Innovation in Cloud Solutions 🔧 Day-to-Day Tasks: Specialize in creating AWS infrastructure for Migration Projects. Leveraging services such as S3, SNS, SQS, IAM, Lambda, System Manager, Kinesis, OpenSearch, Cognito, Storage Gateway, Cloud Watch, API Gateway, AWS Event Scheduler, Secret Manager, ECS, Application Load Balancer, VPC among others. Additionally, I excel in crafting Splunk Dashboards and implementing alerting mechanisms for Cloud Watch logs to monitor failures. My approach involves constructing AWS infrastructure using the Serverless framework and Cloud Formation templates, while automating tasks through Boto3 (Python Scripting) Lambdas. 🎯 Passion: I am deeply passionate about continuously learning new technologies and eagerly anticipate the transformative impact of cloud computing on the tech landscape. 📧 Connect: Feel free to reach out to me at awslearningoals@gmail.com. Let's connect and explore potential collaborations! https://www.linkedin.com/in/rastogiutkarsh/