Securing Your AWS VPC with an Automated Quarantine Solution
 Foluso Ogunsakin
Foluso Ogunsakin
In the age of the Cloud, setting up computing infrastructure has become relatively easy. This can also mean the data and resources in the cloud are not properly protected from malicious actors and activities if the right controls, monitoring and configurations are not applied.
If you're navigating the vast expanse of AWS (Amazon Web Services) or any other public cloud service provider, you're probably aware of the constant dance with security threats. Whether it's blocking the sneaky manoeuvres of cyber attackers or adding layers of defence to fortify the security of your environment against potential breaches, the battle of cloud security and its threats landscape is ever-evolving.
In this blog post, I built a simple quarantine solution to show how you can respond to active threats within your AWS VPC by automatically locking down your infrastructure to stop the advances and activities of a malicious actor.
Solution Overview
I used various automation tools and event-based services to create and deploy all the resources and services for the quarantine solution. The following AWS services and programming tools were used:
Amazon EC2: This service allows you to create a virtual machine instance in AWS.
Amazon VPC: This is a logical section of the cloud provided to the customer. Think of it as your own space or data centre in the cloud where you can launch your resources.
Amazon GuardDuty: An intelligent threat detection service that monitors your resources for malicious activities from numerous sources or actors and provides detailed findings and actionable events for visibility and remediation.
Amazon EventBridge: It is a serverless event bus that helps you receive, filter, transform, route, and deliver events from your applications or infrastructure. It can help to build scalable event-driven applications using events generated from AWS services and other sources.
AWS Lambda: An event-driven serverless computing service where you can execute your code without the need to manage servers. It supports various programming languages like Python.
AWS CloudFormation: It's a service that allows you to use Infrastructure as Code to create and manage immutable infrastructures in AWS.
Python +Boto3: Python is a versatile high-level programming language. Boto3 is an AWS Python SDK useful for making API calls to your AWS environment for various actions.
GitHub + Actions: a version control system with a feature to enable you to build an automated pipeline for deployment and management of your cloud infrastructure. The code for this solution is hosted on GitHub and deployed with GitHub Actions.
The AWS resources are created using a CloudFormation template and deployed with GitHub Actions which packages the application and deploys the stack to the configured AWS account.
This solution simulates a poorly configured public-facing workload in an EC2 instance that has been compromised by curl ing some known malicious domains labelled for Bitcoin and then triggering the lockdown of the VPC.
Solution Architecture
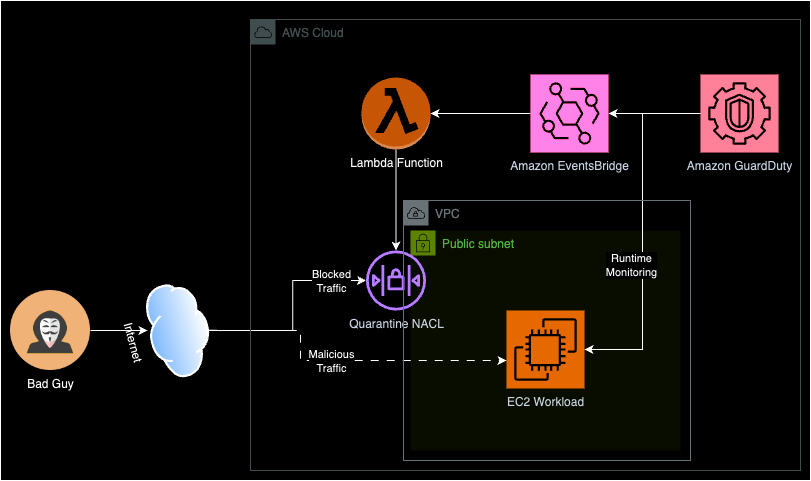
This architecture focuses on the activities and events within the AWS account. The security event is generated by simply passing a bash script to the EC2 via user data. The script contains multiple DNS commands for Bitcoin domains which are executed at the launch of the EC2 instance.
The Amazon GuardDuty picks up malicious activity in the EC2 instance and registers it in its Findings database. Amazon EventBridge is configured to listen for GuardDuty Findings events in EC2 instances, so when GuardDuty detects malicious activities in the instance, that event is picked up by EventBridge which then invokes the Quarantine Lambda Function that locks down the EC2 public subnet with a Network Access Control List.
Once the resources have been deployed to the AWS environment, you can immediately access the sample webpage deployed in the instance to confirm the before and after quarantine effect by browsing the public IP of the instance.
It can take up to ~15 minutes until the quarantine effect kicks in, afterwards, you will be able to see and browse the malicious activities in your GuardDuty Findings console.
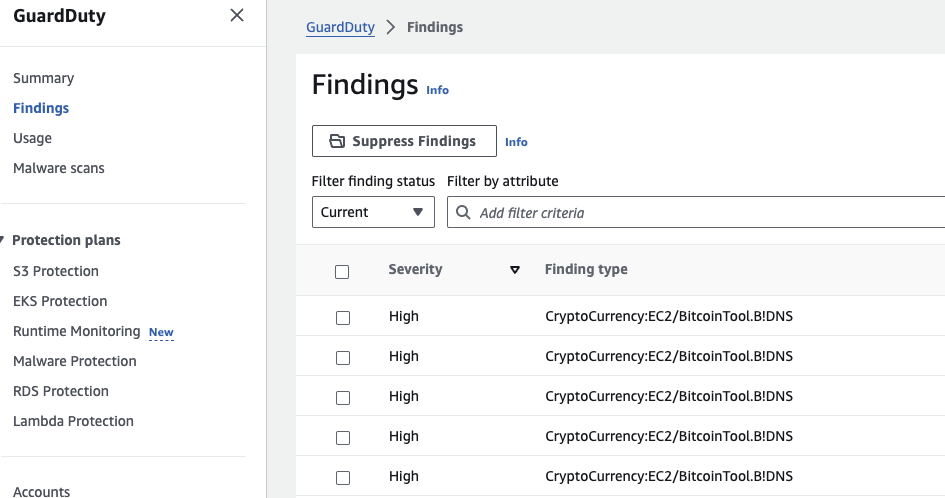
Because there are multiple DNS commands in the bash script that would trigger multiple quarantine actions, the AWS Lambda Function is created to be idempotent - it first checks if the quarantine NACL is already enforced before attempting deployment. If the quarantine NACL doesn't exist, it creates and associates the NACL with the EC2's public subnet. Newly created NACLs have a rule to deny all incoming and outgoing traffic which satisfies the requirement hence there's no need to add any deny rules.
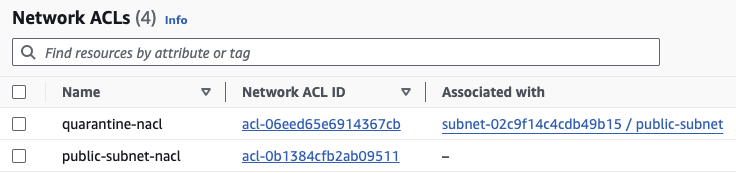
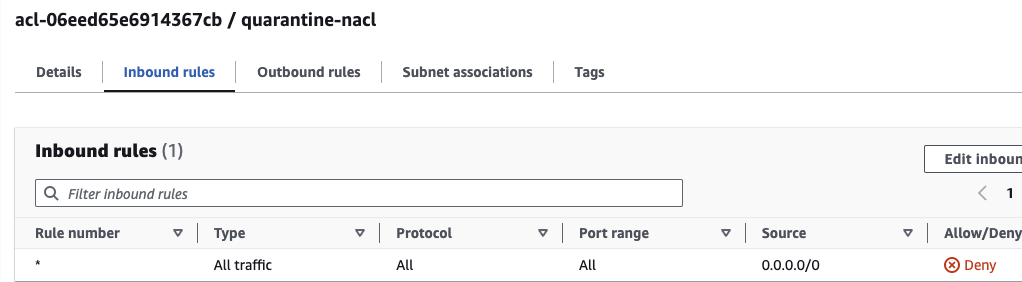
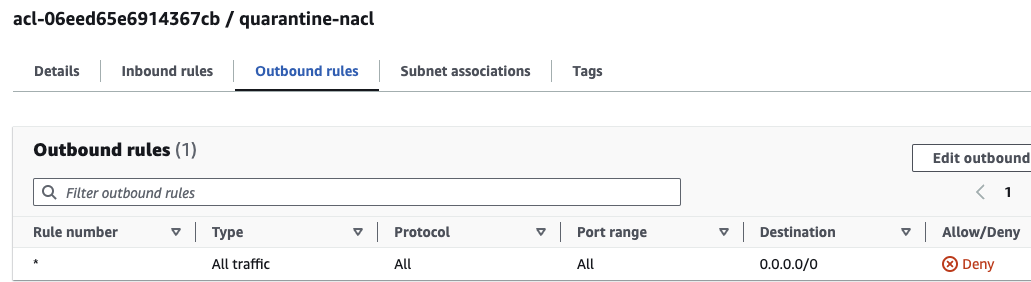
Immediately the quarantine Network ACL is created, all traffic to the public subnet and instance is stopped and you or the 'Bad Guy' in this scenario will not be able to access the instance from anywhere, through any protocol anymore.
Solution Deployment
This solution can be deployed to your AWS environment by making a copy of the repository, updating the GitHub Actions file, and pushing the changes to your environment.
Deployment Prerequisites
Create an IAM Identity with permissions for the GitHub Actions pipeline and configure the IAM credentials (Access key & Secret access key) in GitHub Actions secrets in the Settings -> Security -> Secrets and variables -> Actions tab of the repository.
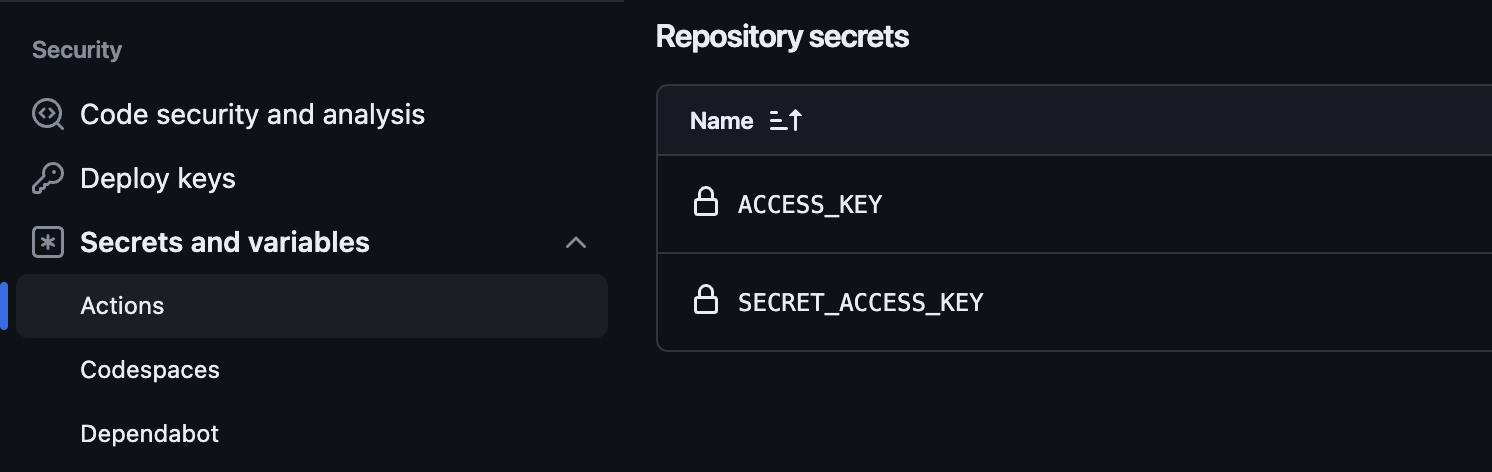
Add a valid
Ec2ImageIdvalue to the stack parameters in the GitHub Actions file:deploy.yml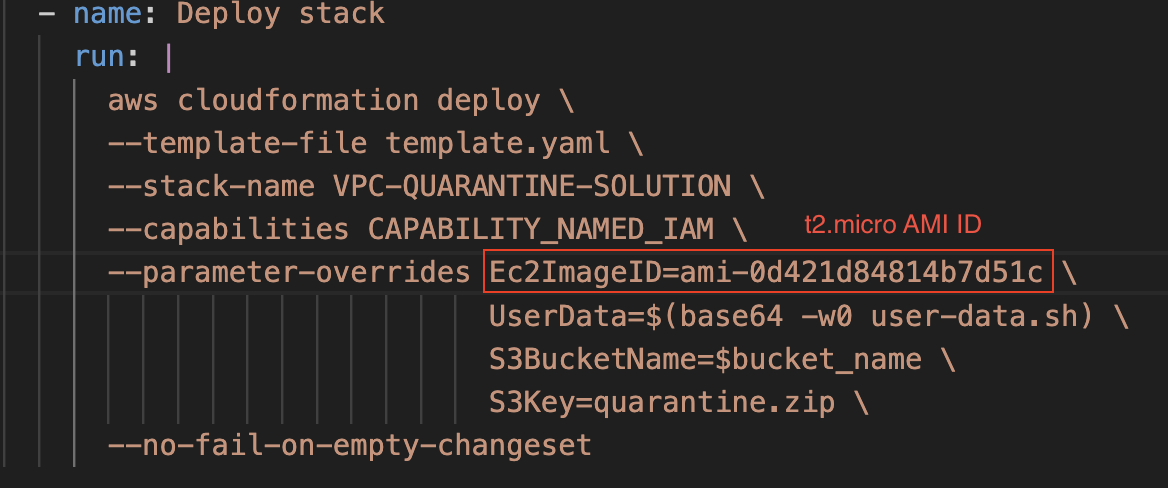
Implementation Steps
Copy or clone the repository.
Complete all the Deployment Prerequisites from above.
Push your changes to your repository.
Confirm access to the webpage in the public EC2 instance.
- Grab the instance public IP from the CloudFormation Stack Outputs or EC2 console.
After ~15 minutes, attempt to access the website again.
Check the VPC public subnet to confirm quarantine NACL is in effect.
You will be blocked from accessing the website.
Cleanup Steps
Check out the Readme section of the repo for detailed cleanup steps.
Delete the Quarantine NACL.
Delete the CloudFormation stack.
Delete the S3 bucket.
Conclusion
In some cases, this quarantine solution might not be the best solution for your workloads or environments but the essence of this solution is to show you how you can build intelligent auto-remediation capabilities into your infrastructure to respond to security events promptly because in some other cases, it might be the difference between losing or protecting your assets.
Amazon GuardDuty is not limited to EC2 instance monitoring, it also supports other workloads and resources in your AWS accounts like your Databases, Containers, Amazon S3, and AWS Lambda.
With AWS Lambda, you can build a variety of functionalities to respond to GuardDuty Findings like forwarding the event to an Amazon SNS endpoint for sending Emails, Texts or Push messages to the responsible team or individual. You can also use Lambda to send alerts or notifications to an Instant Messaging application like Slack or even terminate the compromised resources in scenarios where they are stateless or ephemeral.
Subscribe to my newsletter
Read articles from Foluso Ogunsakin directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Foluso Ogunsakin
Foluso Ogunsakin
Servant for IT Infrastructure and Cloud Computing.