CIS Benchmarking for Redhat/CentOS/RockyLinux/Ubuntu and Amazon Linux with OpenSCAP
 Arun Mohan
Arun Mohan
OpenSCAP
The oscap command-line utility, provided by the openscap-scanner package, performs configuration and vulnerability scans, and generates reports and guidance based on these scans.
SCAP Security Guide (SSG)
This predefined collection of security policies for Linux systems is provided in the scap-security-guide package. The guide provides a catalog of hardening advice that is linked to various government requirements to help define and customize security policies according to the organization's needs. This guide is not just documentation; rather, this guide provides rules and scripts that are used by the oscap command.
Script Check Engine (SCE)
The openscap-engine-sce package provides the SCE extension that enables you to write security content by using Bash, Python, or Ruby.
SCAP Workbench
This graphical utility performs scans on a single local or a remote system, and generates security reports based on these scans. The utility can also be used to customize compliance policies.
The SCAP Security Guide
The SCAP Security Guide is a collection of security policies for Linux systems, in the form of SCAP documents. The guide consists of rules with detailed descriptions and proven remediation scripts and Ansible Playbooks. The SCAP Security Guide can be used with OpenSCAP tools to automate the auditing of a Linux system.
SCAP Security Guide transforms the security guidelines that are recommended by different authorities into a machine-readable format that can be used by OpenSCAP to audit your system. The guide builds multiple security baselines from the high-quality SCAP content. If your system must comply with one of the provided baselines, then you can select the appropriate profile from the SCAP Security Guide. However, most real world deployments require adjustments to the profile based on the organization's security requirements.
For ease of use, all the available security policies are broken into profiles. A profile can be defined as a grouping of security settings that correlate to a known policy.
Procedure for CIS Level1 Benchmarking for Red hat & Rocky Linux
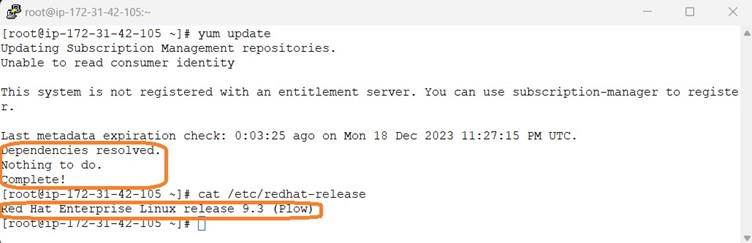
Make sure that all packages are update-to-date and check the OS release
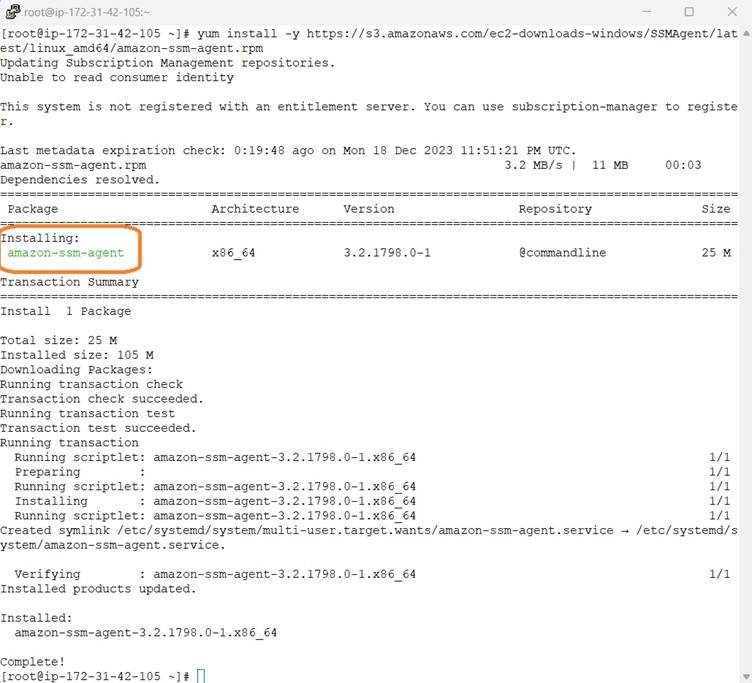
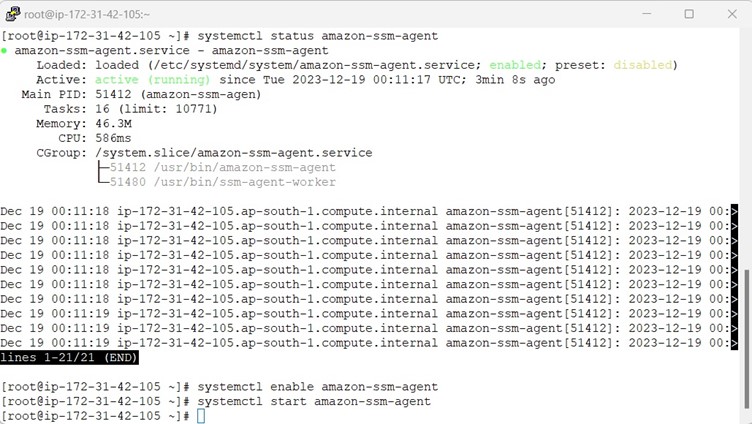
To access RHEL via AWS Session Manager we need to install ssm-agent whereas other operating systems are shipped along with ssm-agent installed.
Please refer the below document for AWS SSM Agent Installation
https://docs.aws.amazon.com/systems-manager/latest/userguide/agent-install-rhel-8-9.html
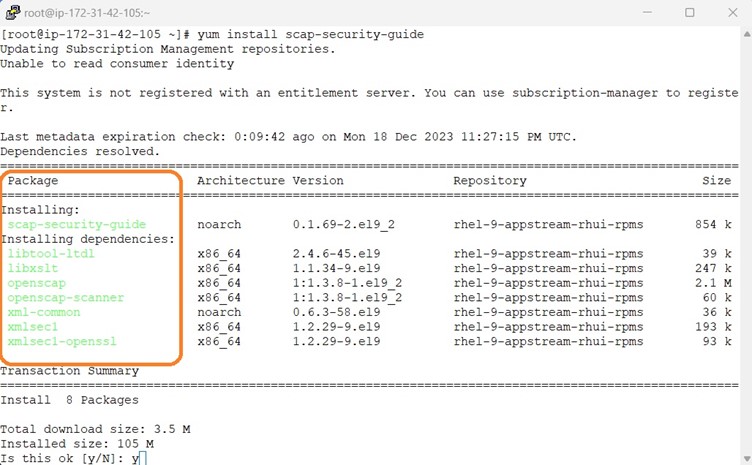
Use the yum install scap-security-guide command to install the SCAP Security Guide. This command automatically installs the openscap-scanner package as a dependency. The openscap-scanner package contains the OpenSCAP command-line tool called oscap.
The SCAP source data stream supports document generation, information interchange, automation of compliance testing, compliance scoring, and situational tailoring. The data stream file contains the SCAP profiles with all the rules that are required to run an evaluation or a scan.
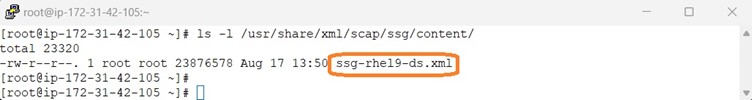
To review all the security rules that are associated with a profile, you can consult the data stream file. However, you can also use the oscap command to generate a user-friendly HTML version of the security guide for a specific profile.
To use the oscap command to generate the HTML security guide for a specific profile, you must provide the profile's unique id attribute. You can use the oscap info command to parse the data stream file and to display the profiles, along with their id attributes.
The following example uses the oscap info command to inspect the security content:
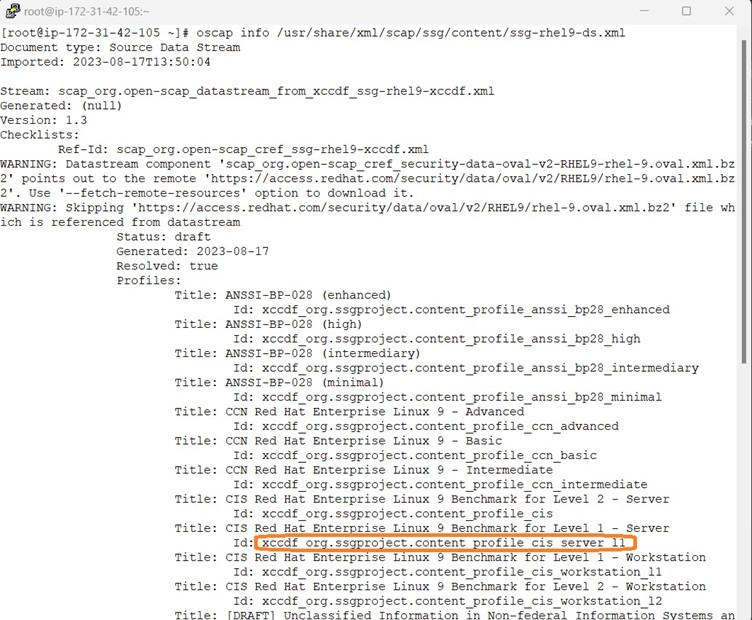
Scanning a System for Compliance
To scan a system, install the openscap-scanner and scap-security-guide packages on that system, and select the XCCDF data stream file and the profile that you intend to use.
Run the oscap xccdf eval command to scan the system. Provide the data stream file as an argument, and the identifier of the profile to use with the --profile option.
The following example shows how to use the oscap xccdf eval command to scan the local system.
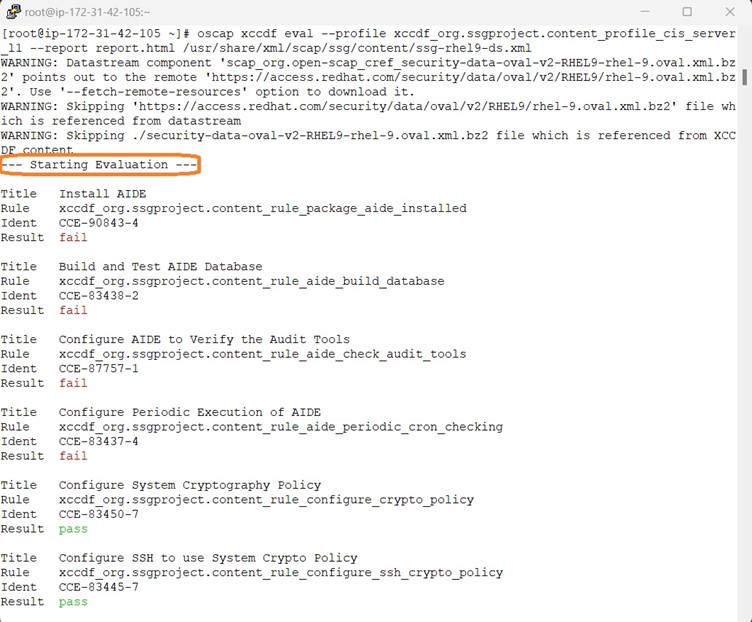
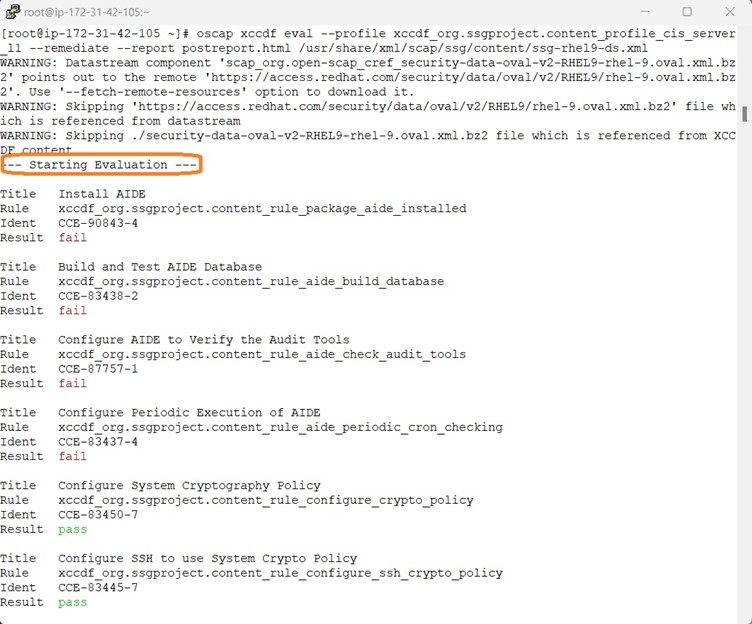
Scanning & Remediation a System for Compliance
Below screenshot shows the Remediation along with Scanning
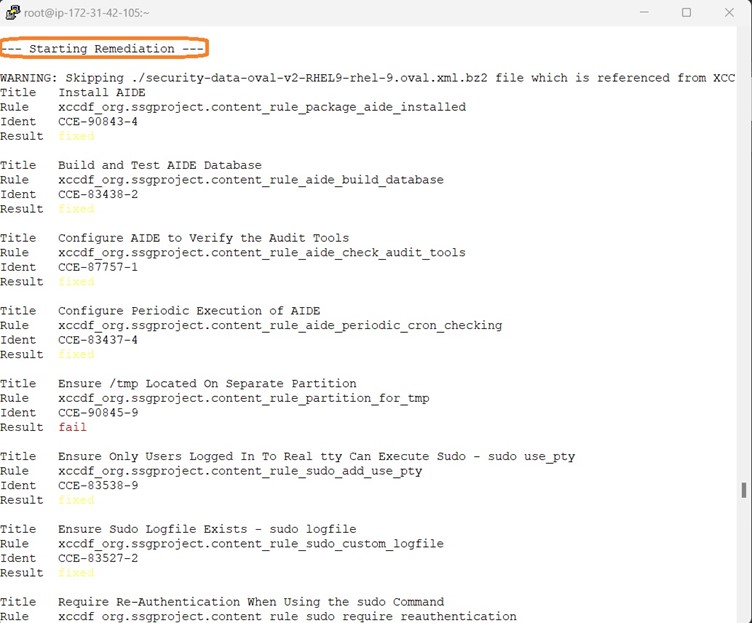
Post remediation, it is time to review the generated report via command line browser. Here we are using lynx as command line browser.
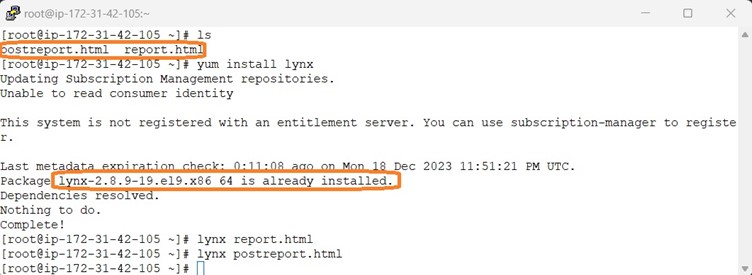
Once all the remediation is done , we have to do the sanity checks whether everything works properly and remove the OpenSCAP along with its dependencies , lynx command line browser and the generates HTML report.
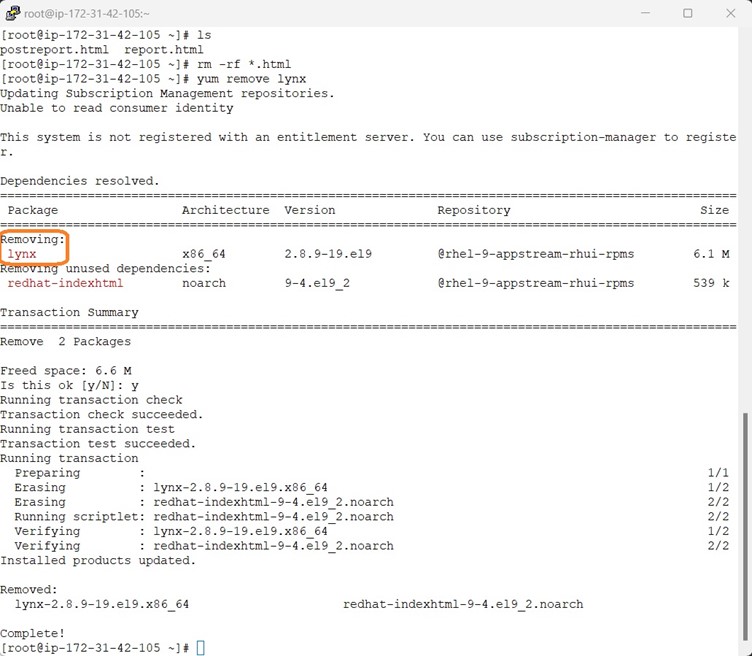
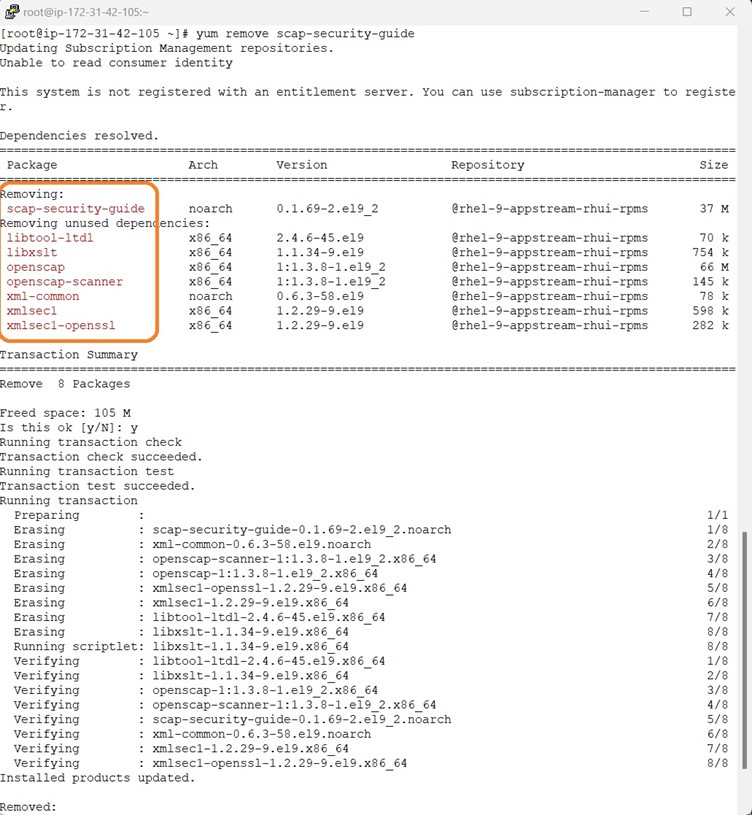
It is time to reboot and handover the server to Cloud team to create a Golden Image from the Hardened RHEL9 Server.
The procedure remains same for RHEL & Rocky Linux.
Procedure for CIS Level1 Benchmarking for Ubuntu 22.04
Make sure that all packages are update-to-date and check the OS release
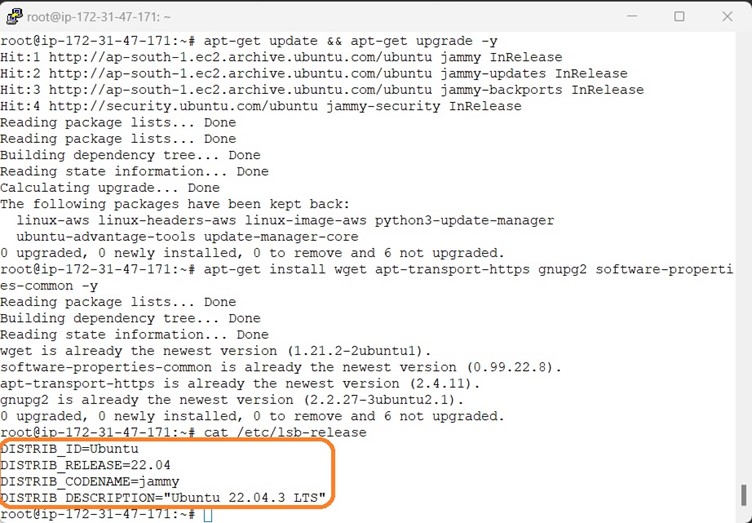
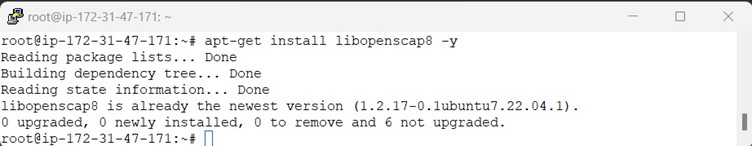
Install the latest version of the OpenSCAP using the following command
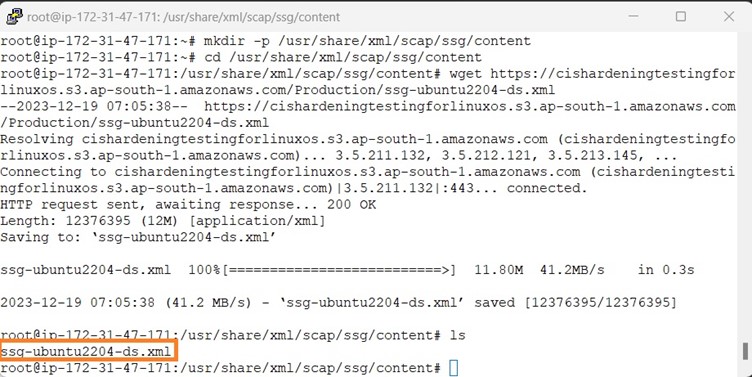
SCAP content for Ubuntu 22.04 is not getting installed so we have uploaded the ssg-ubuntu2204-ds.xml file in the S3 bucket this xml file is generated from the Compliance as code Git hub repo.
Follow the steps provided in the below screenshot to download the SCAP content for Ubuntu 22.04
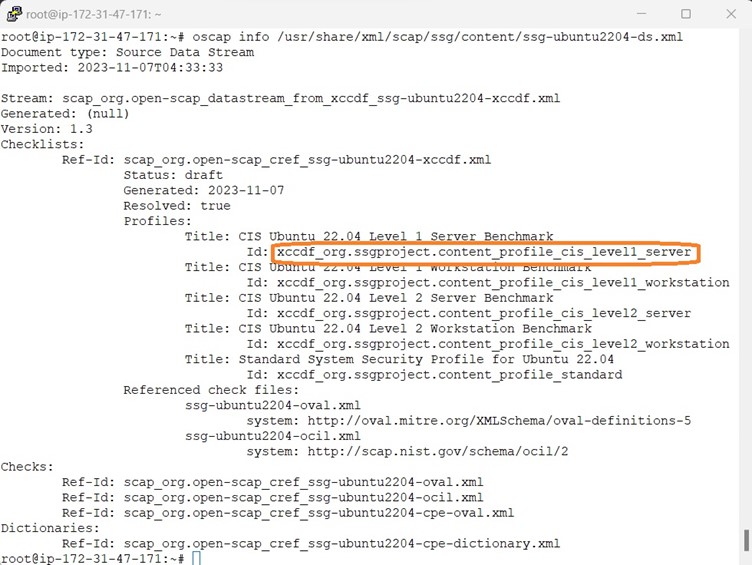
use the oscap info command to parse the data stream file and to display the profiles, along with their id attributes.
The following example uses the oscap info command to inspect the security content:
Scanning a System for Compliance
Run the oscap xccdf eval command to scan the system. Provide the data stream file as an argument, and the identifier of the profile to use with the --profile option.
The following example shows how to use the oscap xccdf eval command to scan the local system.
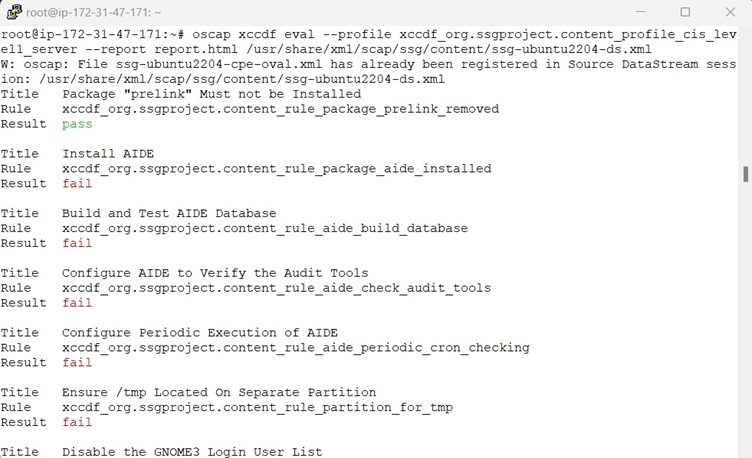
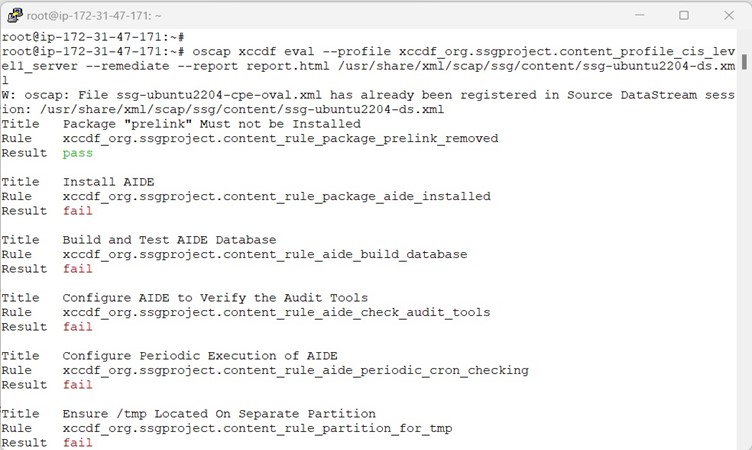
Scanning & Remediation a System for Compliance
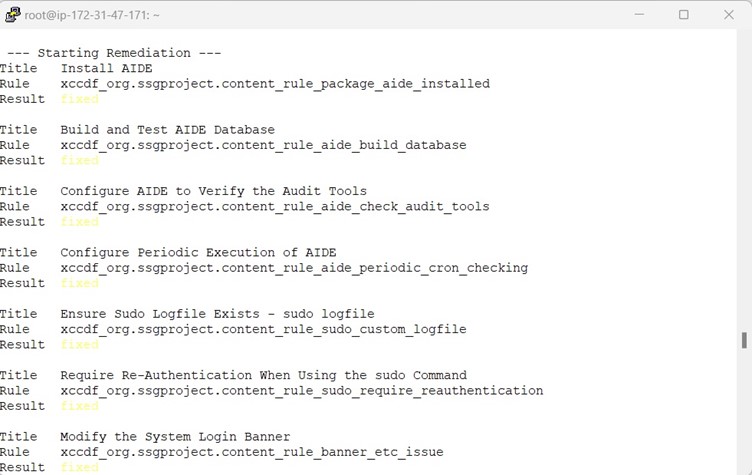
Below screenshot shows the Remediation along with Scanning
Post remediation, it is time to review the generated report via command line browser. Here we are using lynx as command line browser.
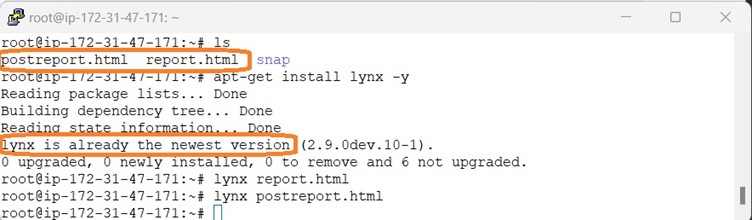
Once all the remediation is done, we have to do the sanity checks whether everything works properly and remove the OpenSCAP along with its dependencies, lynx command line browser and the generates HTML report.
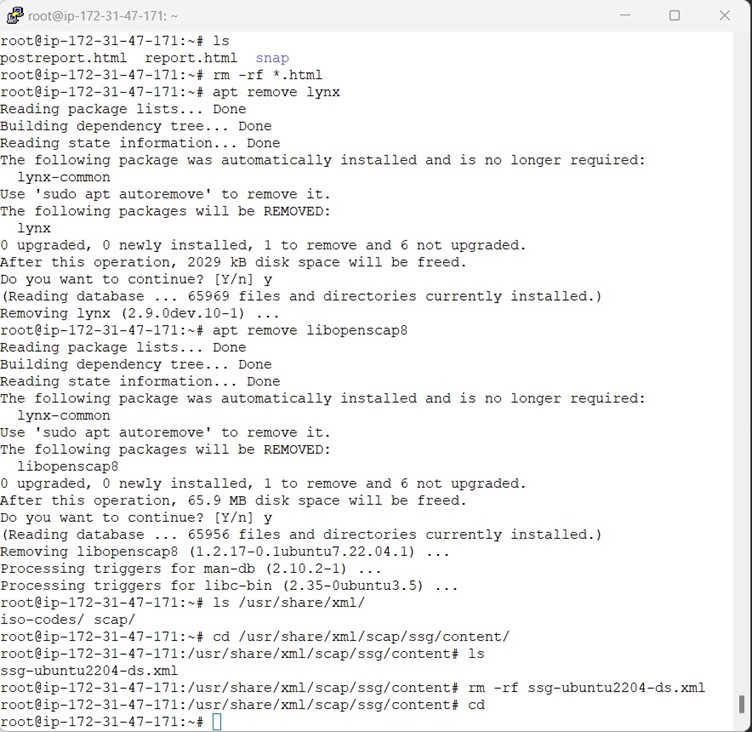
It is time to reboot and handover the server to Cloud team to create a Golden Image from the Hardened Ubuntu Server 22.04.
Procedure for CIS Level1 Benchmarking for AmazonLinux2, ECS Optimized AmazonLinux2, EKS Optimized AmazonLinux2
AmazonLinux2 is based on the RHEL7, so the SCAP content remains same for RHEL7 & AmazonLinux2.
But as amazon doesn’t maintain the SCAP content in their repo for CIS Level1 benchmarking we have to do some hack to achieve this
Make sure that all packages are update-to-date and check the OS release
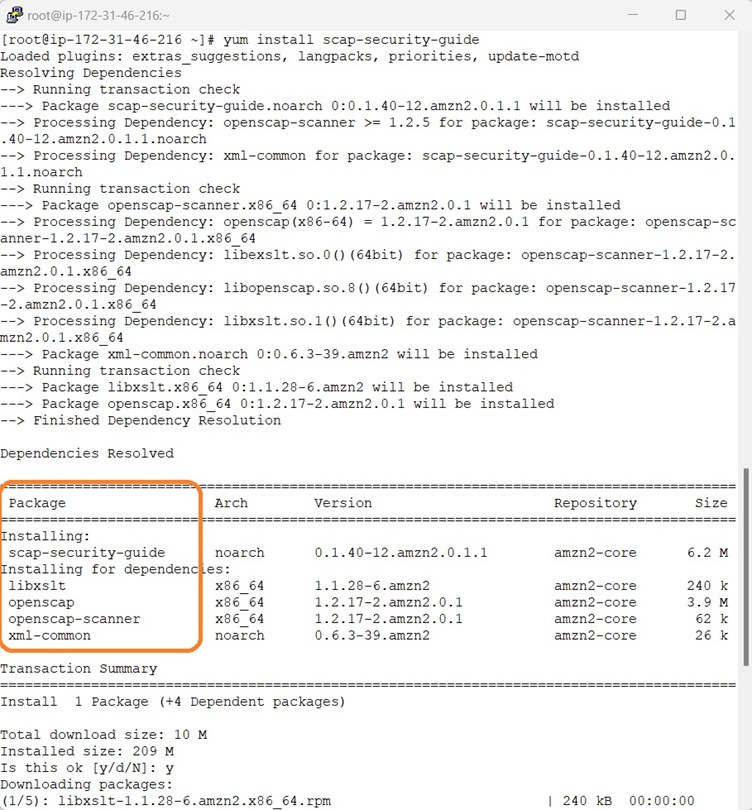
Use the yum install scap-security-guide command to install the SCAP Security Guide. This command automatically installs the openscap-scanner package as a dependency. The openscap-scanner package contains the OpenSCAP command-line tool called oscap.
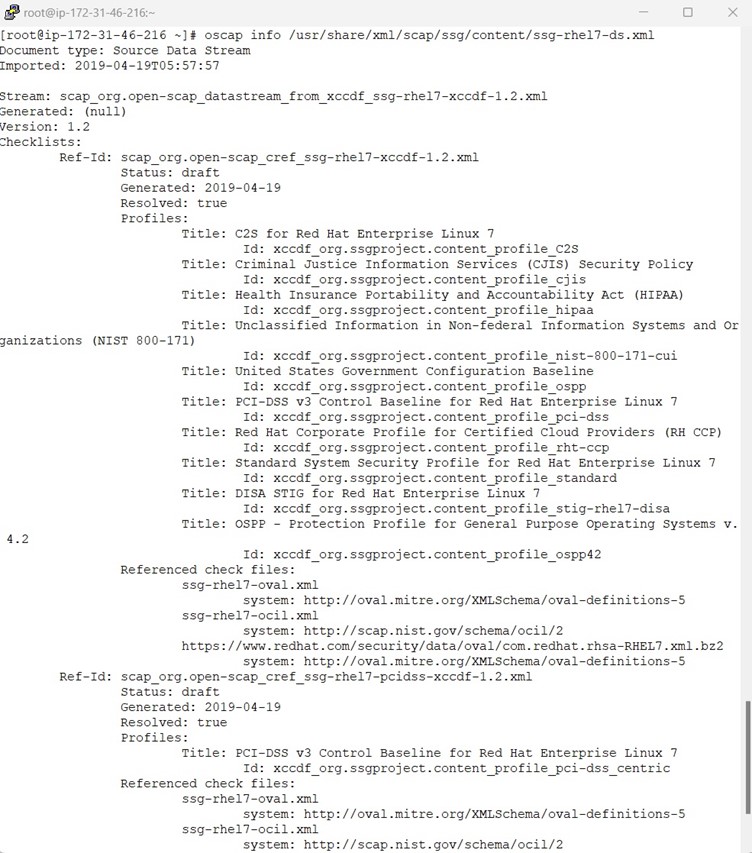
The following example uses the oscap info command to inspect the security content:
As Amazon doesn’t maintain SCAP content/profile for CIS benchmark oscap info is not showing the CIS Level1 profile.
So Its time to do the hack so that SCAP content for RHEL7 will work for AmazonLinux2 , follow the procedure mentioned in the Screenshot.
Let’s investigate the rhel text in the openscap config files , here we need to be familiar with CPE names .
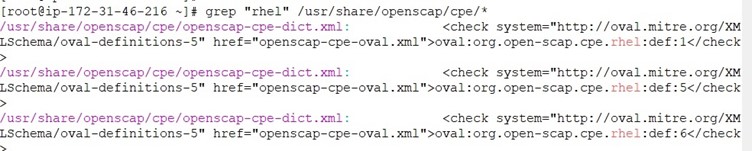
Below screenshot shows how to modify the RHEL7 SCAP content for AmazonLinux2
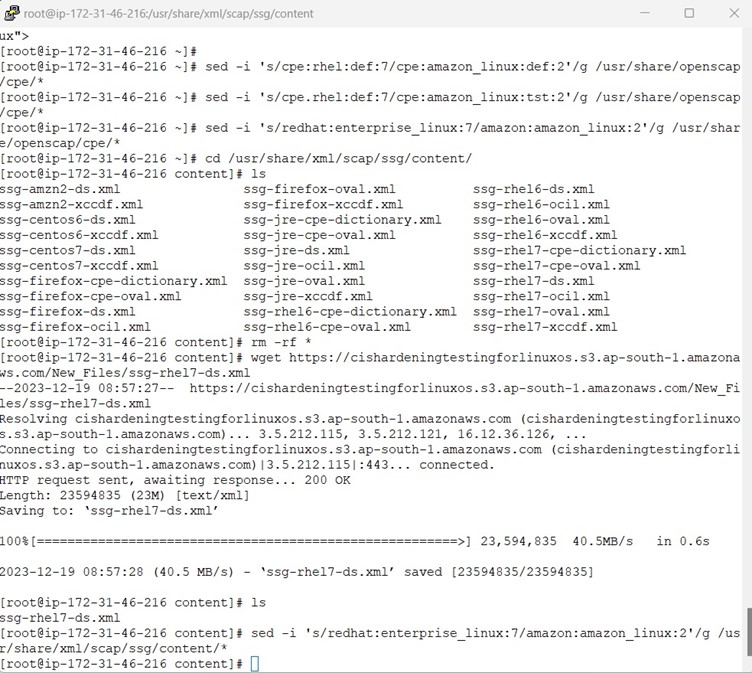
By now we are good with setup, lets fetch the available profiles and this time it should list the CIS Level 1 profile.
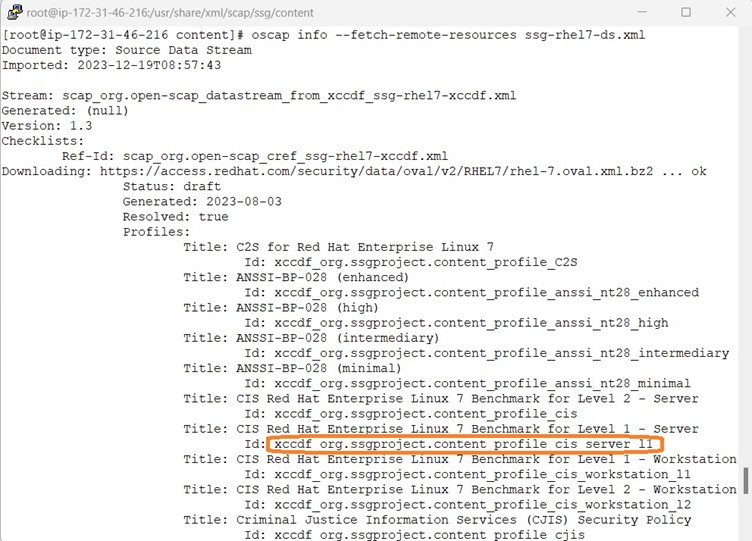
The Scan and Remediation Procedure list below is same as RHEL 9 & Ubuntu
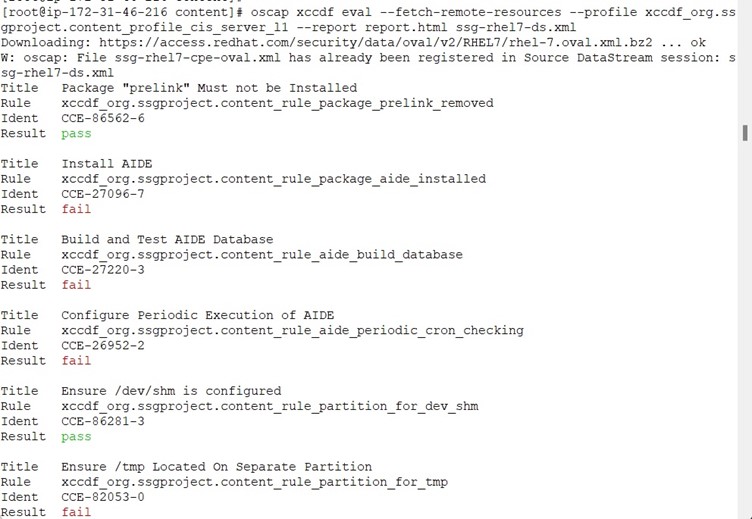
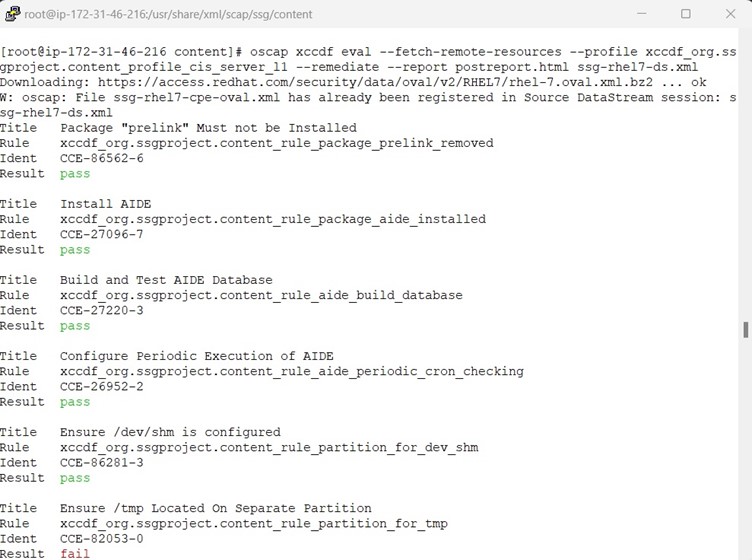
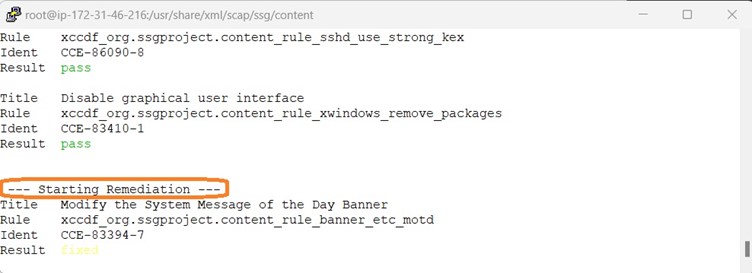
Post remediation, it is time to review the generated report via command line browser. Here we are using lynx as command line browser.
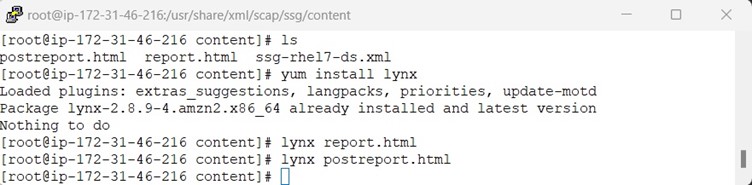
Once all the remediation is done, we have to do the sanity checks whether everything works properly and remove the OpenSCAP along with its dependencies, lynx command line browser and the generates HTML report.
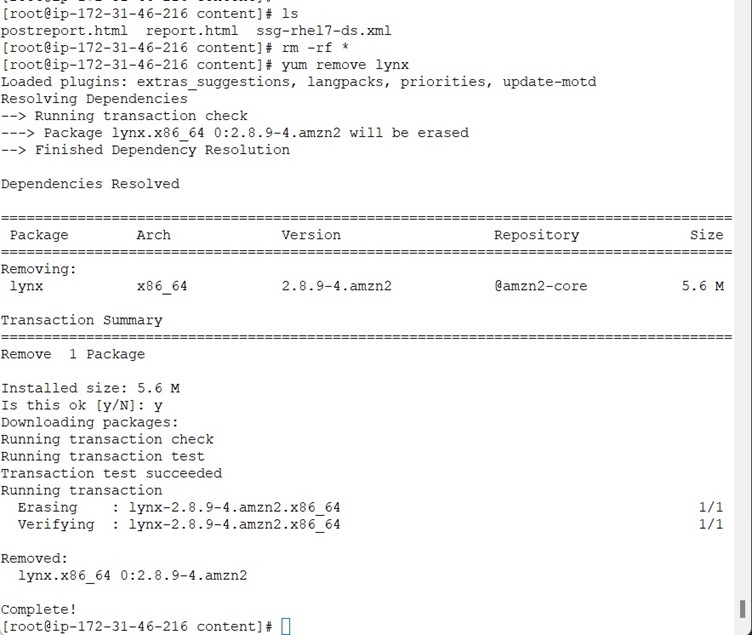
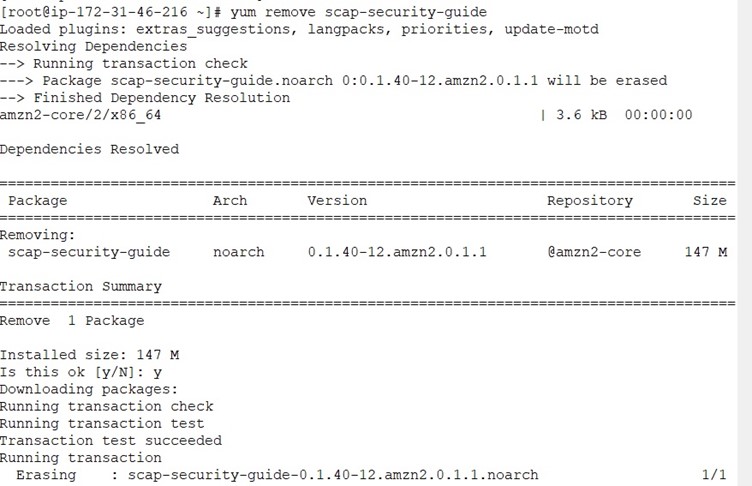
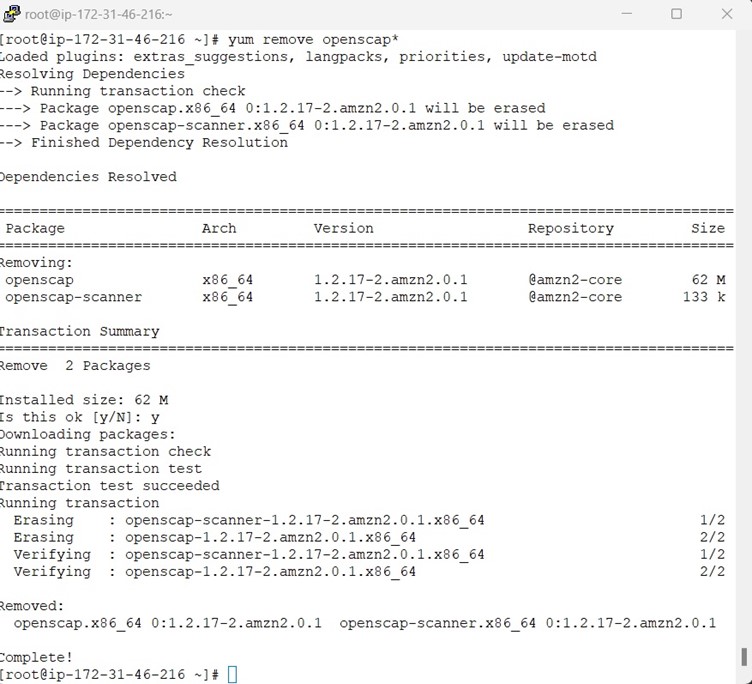
It is time to reboot and handover the server to Cloud team to create a Golden Image from the Hardened AmazonLinux2 Server.
The procedure remains same for ECS & EKS Optimized AmazonLinux2.
Subscribe to my newsletter
Read articles from Arun Mohan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
