Let's setup VPC and understand all VPC concepts like VPC Peering, Transit Gateway.
 Shraddha Suryawanshi
Shraddha Suryawanshi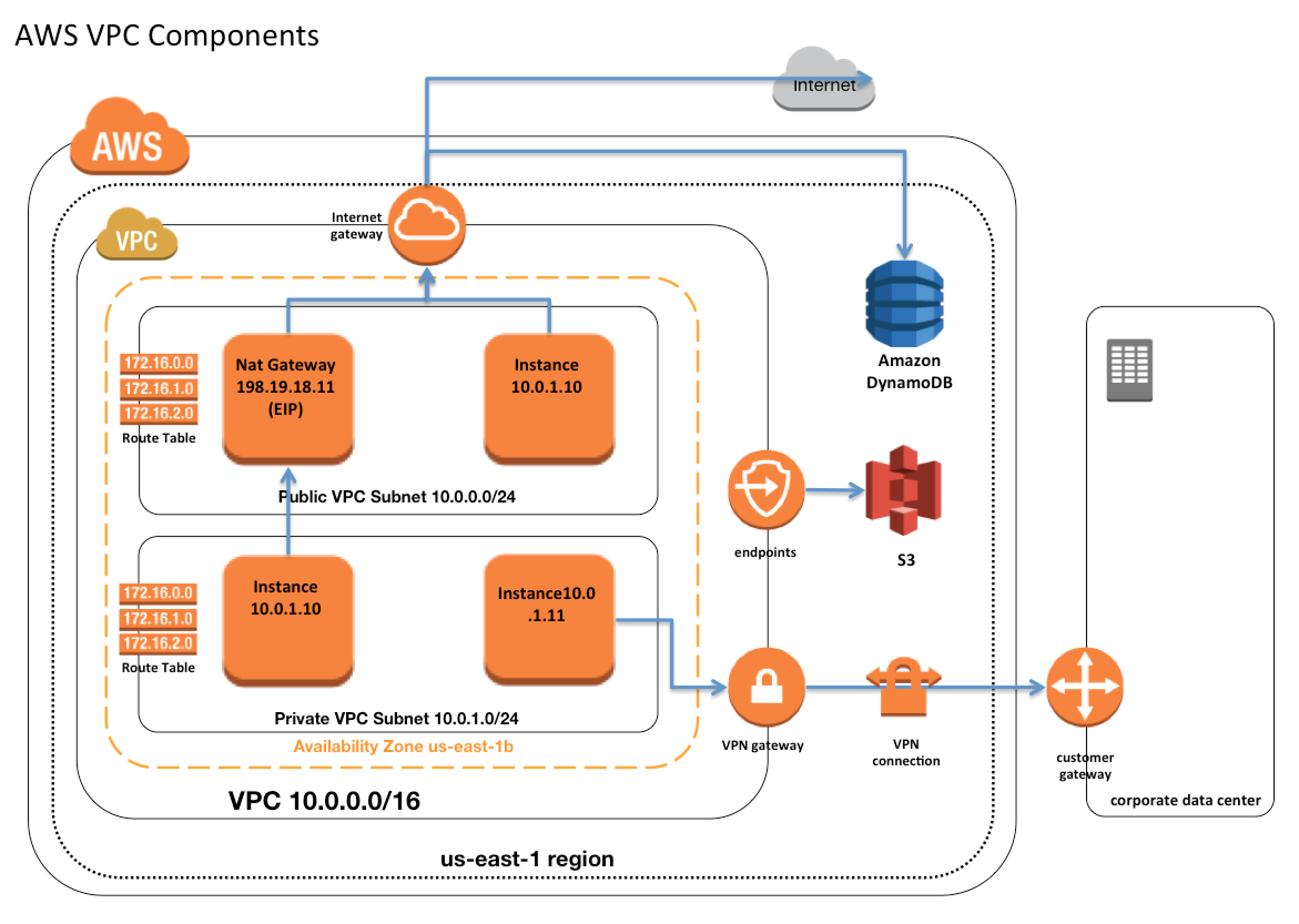
Amazon Virtual Private Cloud (Amazon VPC)
It is a logically isolated virtual network where you can launch your AWS resources.
It is a virtual networking environment where you can decide the range of your IP addresses for your VPC., add subnets, add gateways, and associate security groups.
Later with the help of route tables we can attach various gateways to the subnet for accessing external network, traffic or internet. For example for configure route table to attach internet gateway to public subnet.
Route Table:
A route table contains a set of rules, called routes, that determine where network traffic from your subnet or gateway is directed. Subnets A subnet is a range of IP addresses in your VPC. A subnet must reside in a single Availability Zone. After you add subnets, you can deploy AWS resources in your VPC..
Internet gateway:
It is a horizontally scaled, redundant, and highly available VPC component that allows communication between your VPC and the internet. An internet gateway enables resources in your public subnets (such as EC2 instances) to connect to the internet if the resource has a public IPv4 address or an IPv6 address.
NAT gateway:
You can use a NAT gateway so that instances in a private subnet can connect to services outside your VPC but external services cannot initiate a connection with those instances.
Public – (Default) Instances in private subnets can connect to the internet through a public NAT gateway, but cannot receive unsolicited inbound connections from the internet. You create a public NAT gateway in a public subnet and must associate an elastic IP address with the NAT gateway at creation. You route traffic from the NAT gateway to the internet gateway for the VPC.
Private – Instances in private subnets can connect to other VPCs or your on-premises network through a private NAT gateway. You can route traffic from the NAT gateway through a transit gateway or a virtual private gateway.
Sure, let's break it down step by step:
VPC Creation:
Go to the AWS Management Console and navigate to the VPC dashboard.
Click on "Create VPC" and specify the CIDR block (e.g., 10.0.0.0/16) for your VPC.
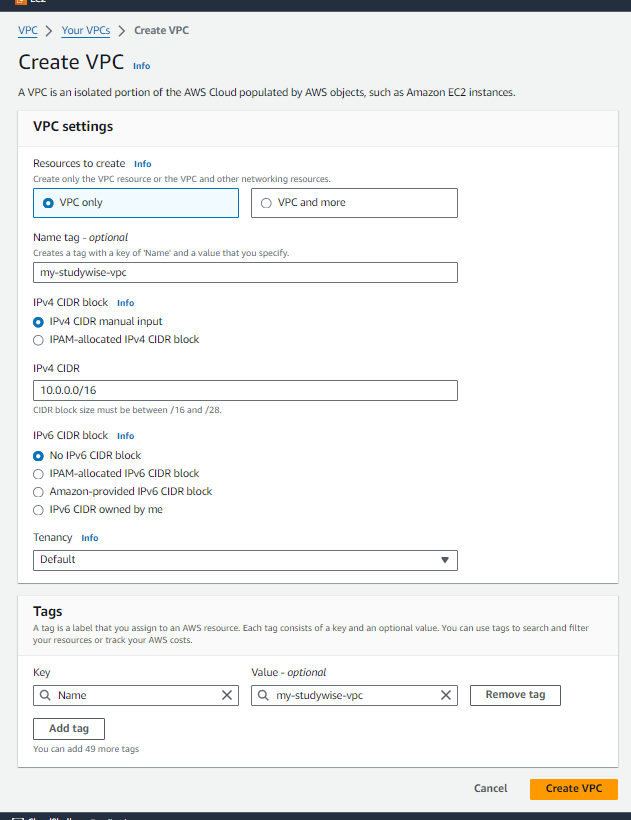
Click on 'Create VPC'
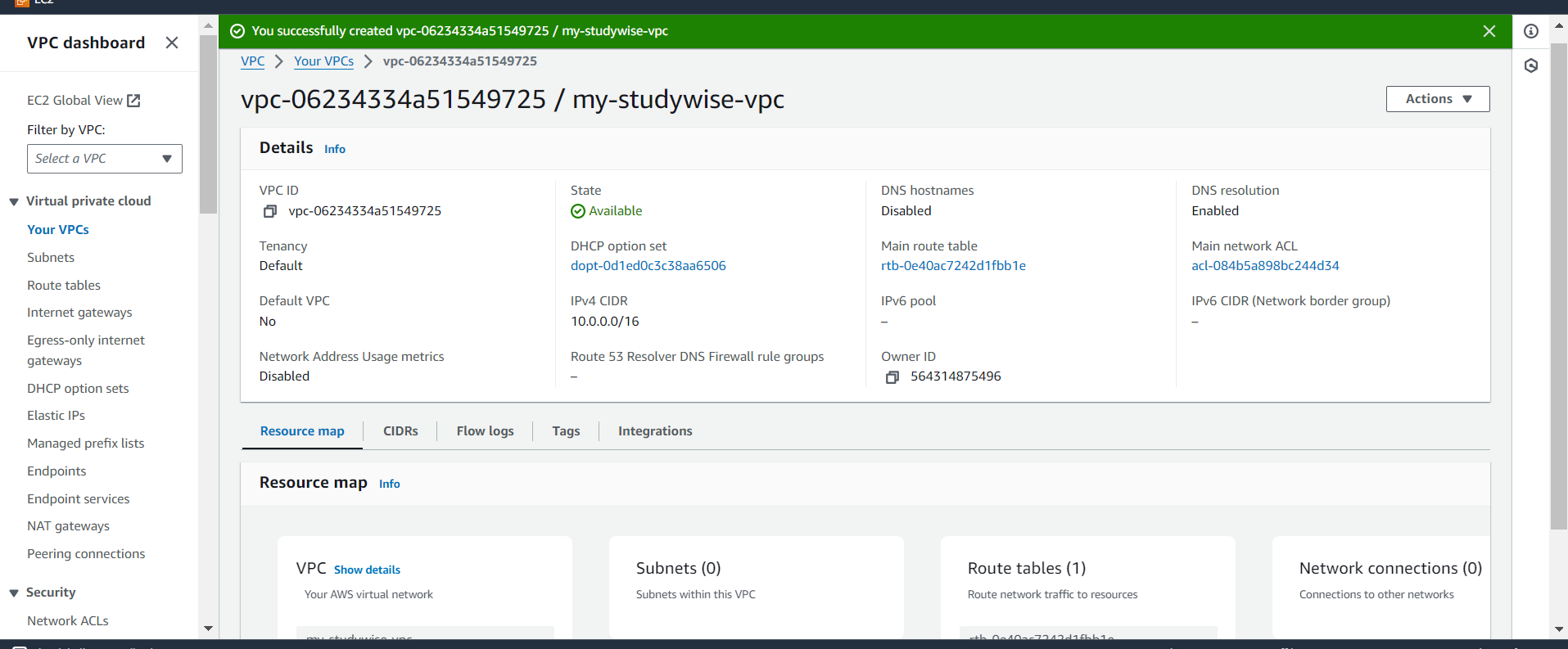
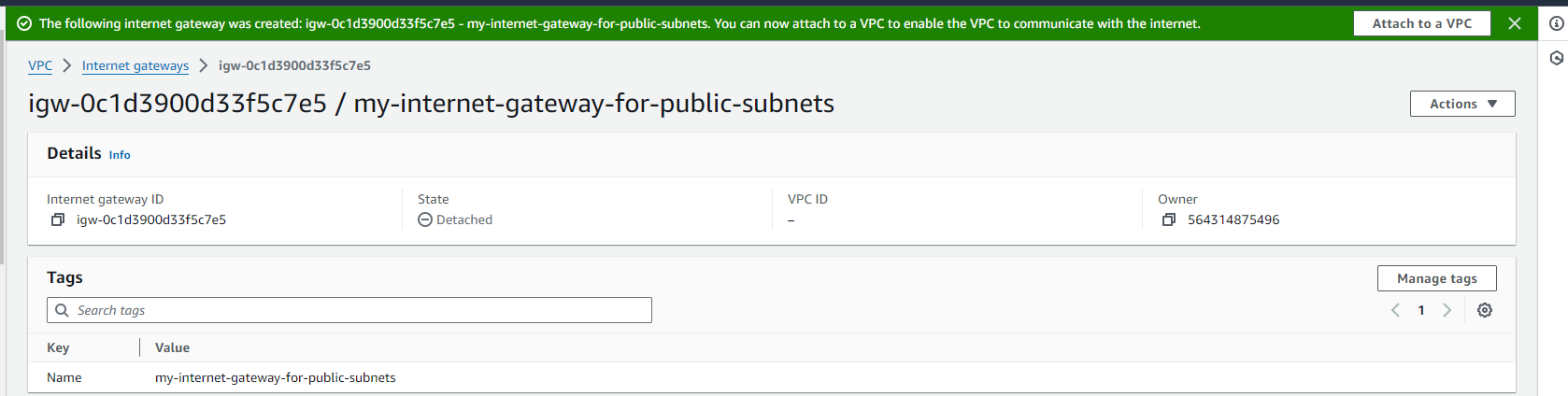
Your VPC has been created successfully.
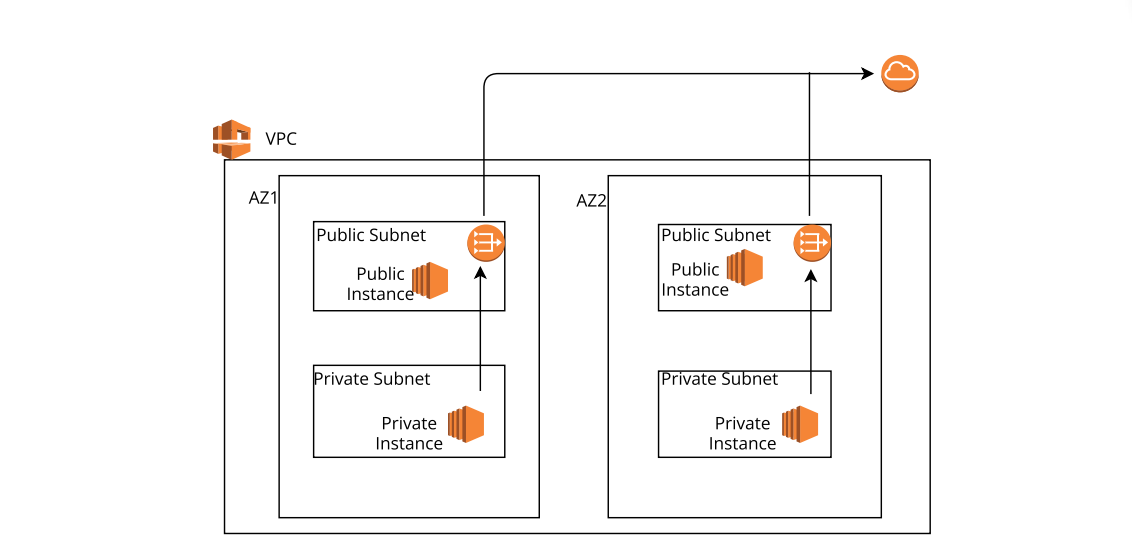
Subnet Creation: Here I am creating a VPC with 4 Subnets (2 Public, 2 Private) in Mumbai region for high availability and demonstrating connectivity through the 4 subnets.
Click on "Create Subnet" and select the VPC created.
Public Subnets: Go to the VPC dashboard and select "Subnets." Choose an availability zone (AZ) in Mumbai region and specify the CIDR block (e.g., 10.0.1.0/24) for the subnet.
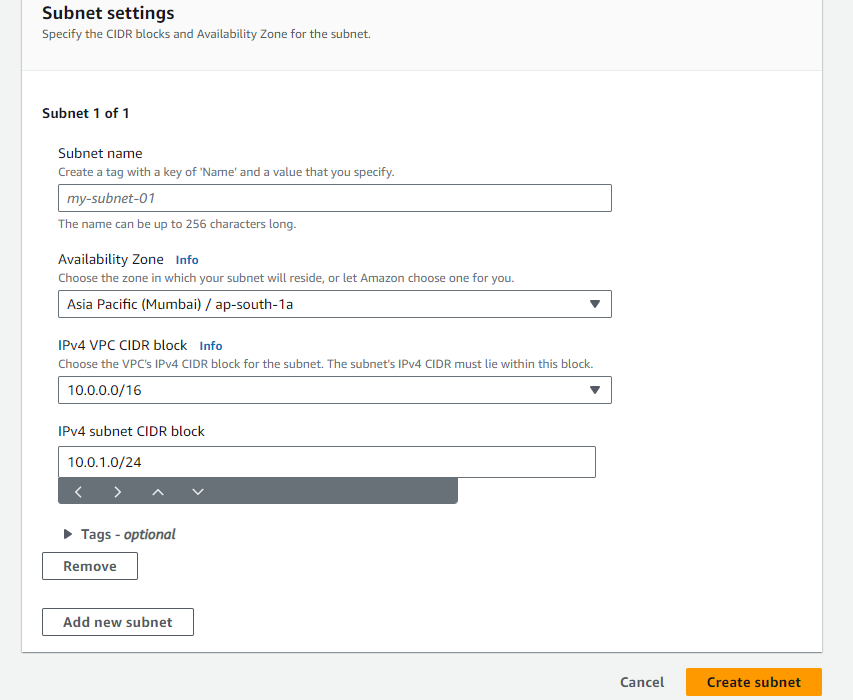
Repeat the process to create another public subnet in a different AZ (e.g., 10.0.2.0/24).
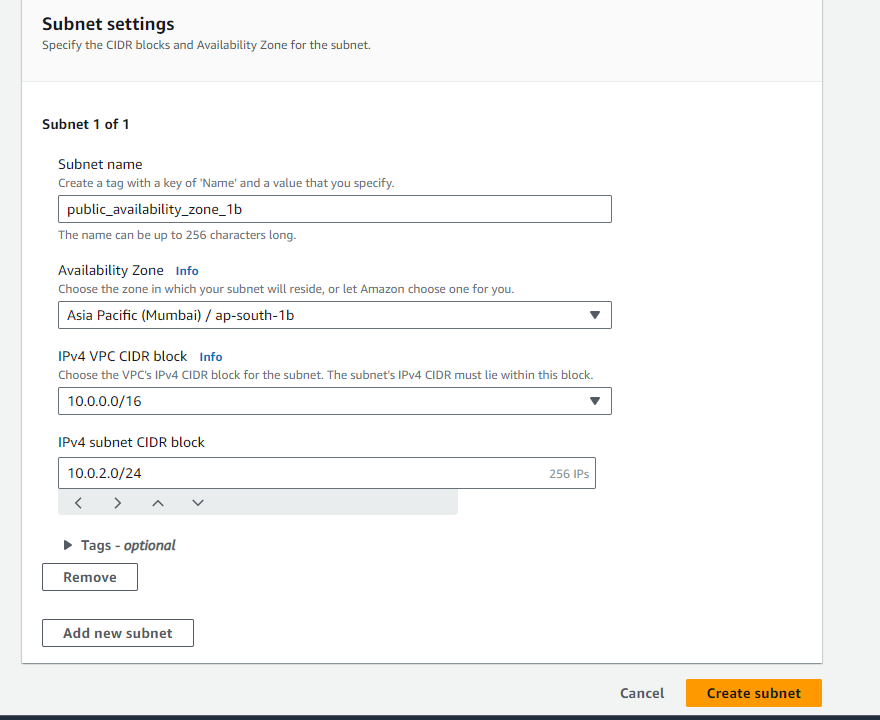
Private Subnets: Follow the same steps as above, but specify different CIDR blocks (e.g., 10.0.3.0/24 and 10.0.4.0/24) for the private subnets.
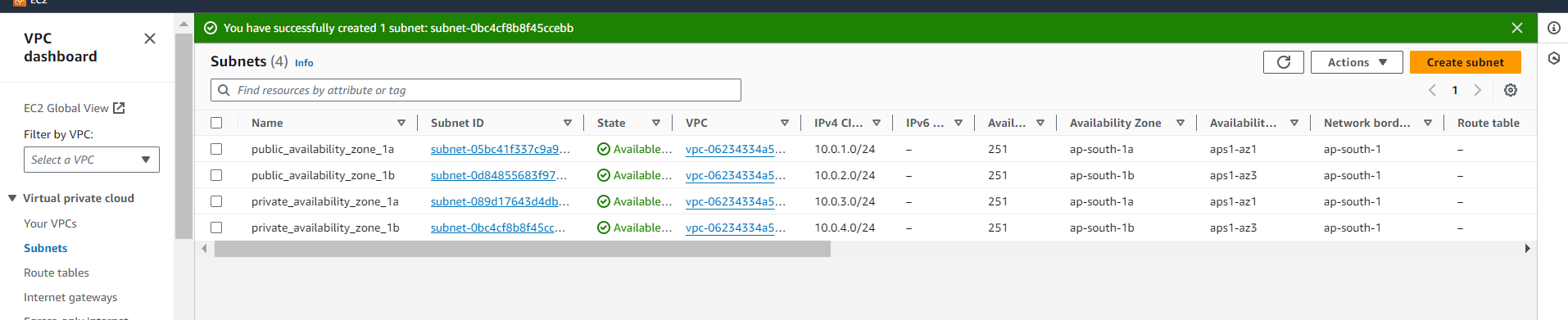
public_availability_zone_1a - 10.0.1.0/24
public_availability_zone_1b - 10.0.2.0/24
private_availability_zone_1a - 10.0.3.0/24
private_availability_zone_1b - 10.0.4.0/24
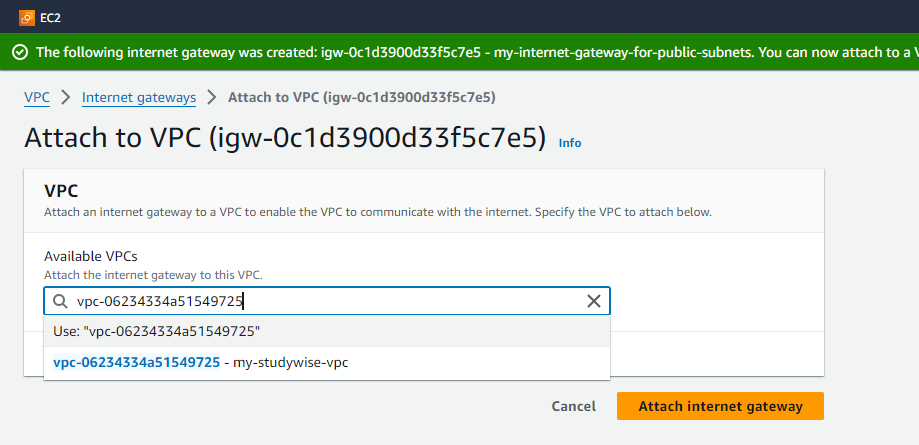
Attach Internet Gateway (IGW) to Public Subnets: Go to the VPC dashboard and select "Internet Gateways."
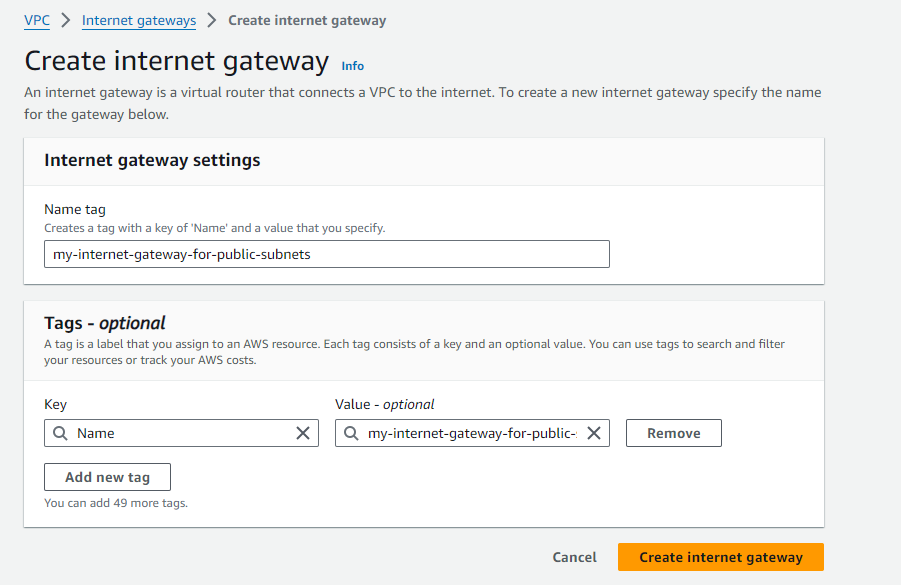
Click on "Create Internet Gateway" and attach it to your VPC.
Select each public subnet, navigate to the "Route Table" tab, and add a route for 0.0.0.0/0 pointing to the internet gateway. Let's create a new Route table for our custom VPC and not disturb the main route tables of the custom VPC
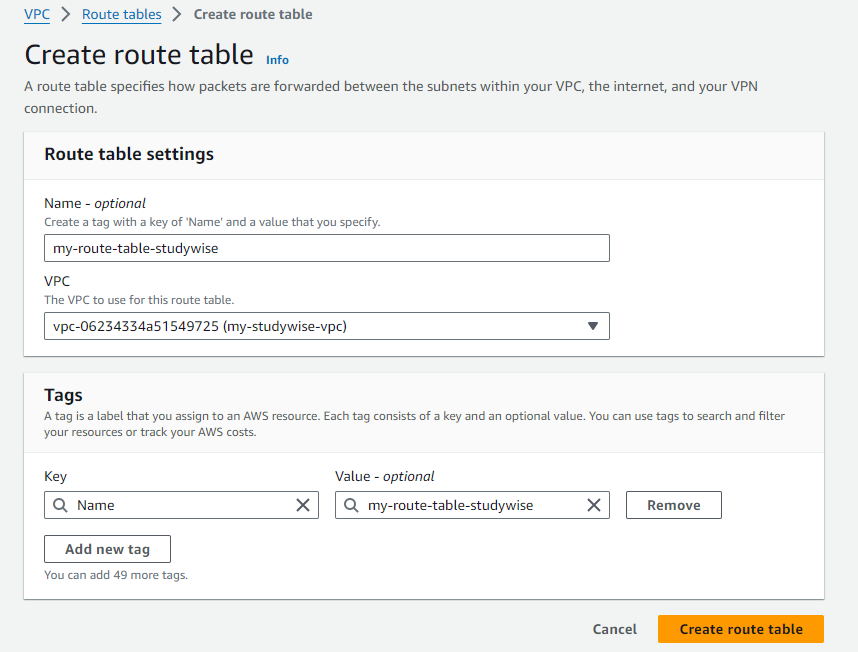
Click on 'Create route table'. Give a name and select your VPC
Click on 'Edit subnet associations'.
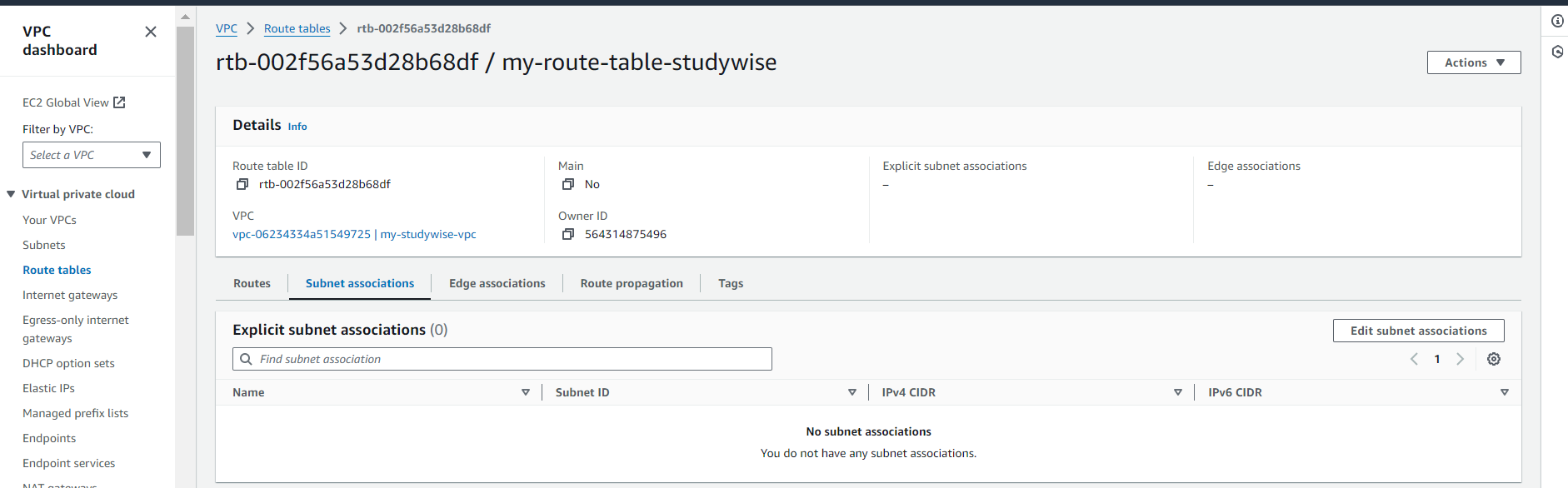
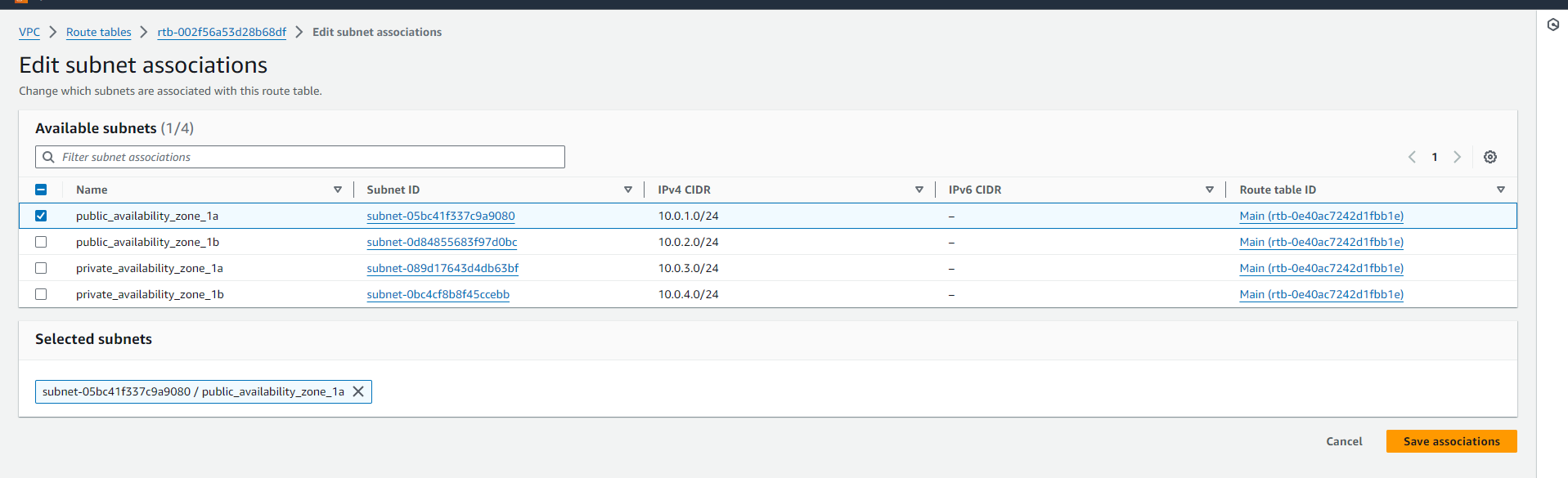
Select the required subnets and click on 'Save associations'. Now our subnet association has been successfully done.
Now click on 'Routes' option from the menu. -> Click on 'Edit routes'.
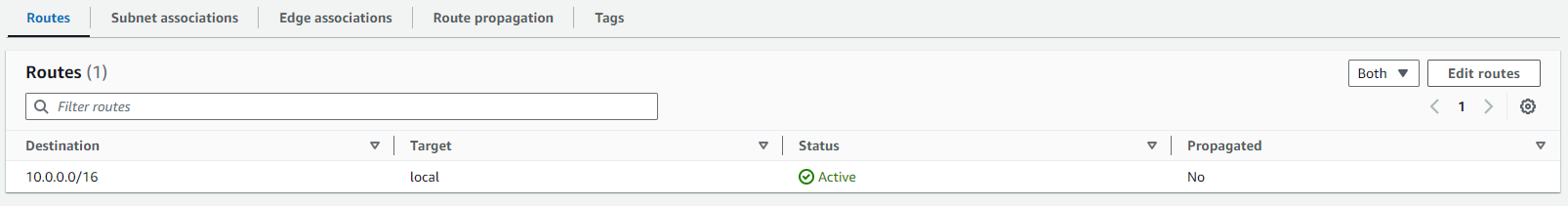
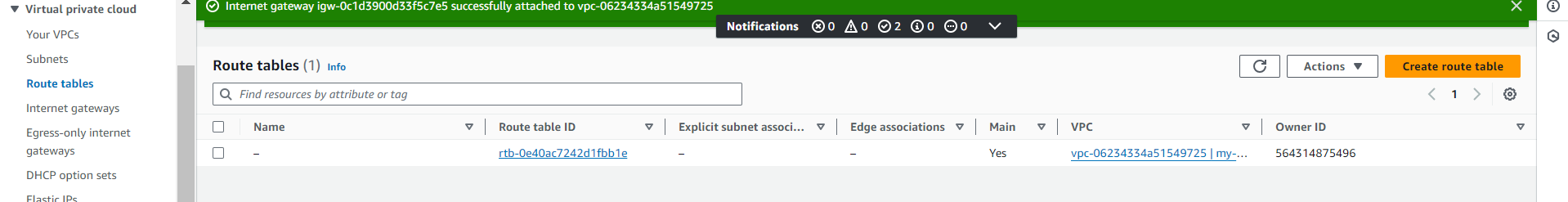
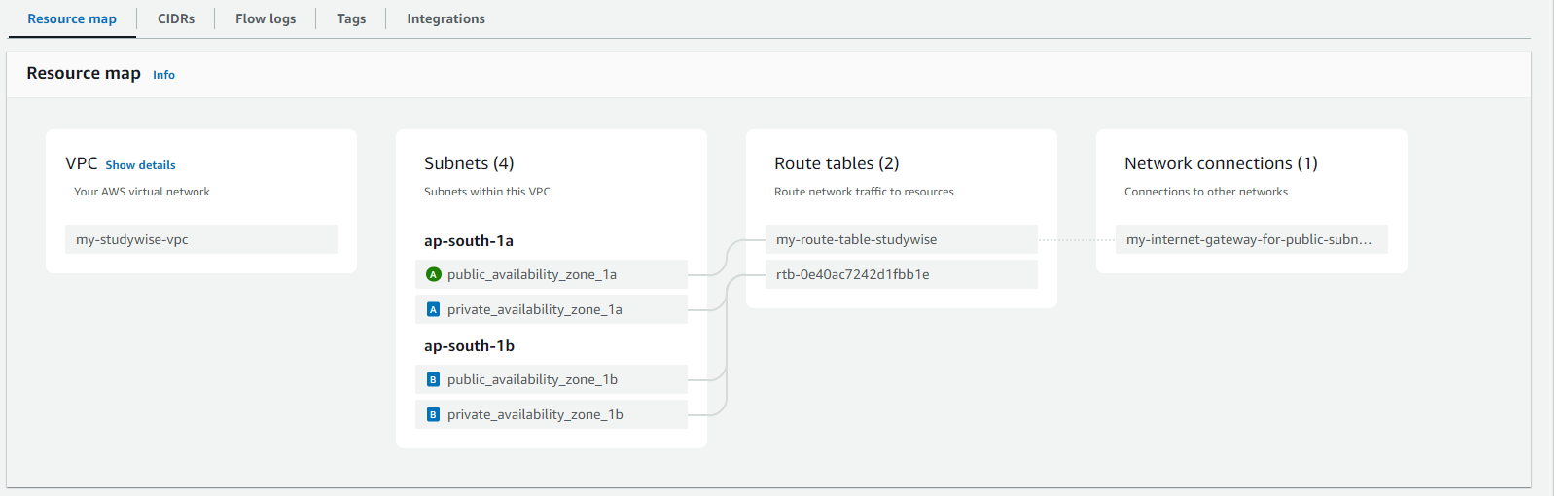
Before doing this you can check the resource map of your VPC, you can see the internet gateway is attached to VPC but is not attached to subnets.
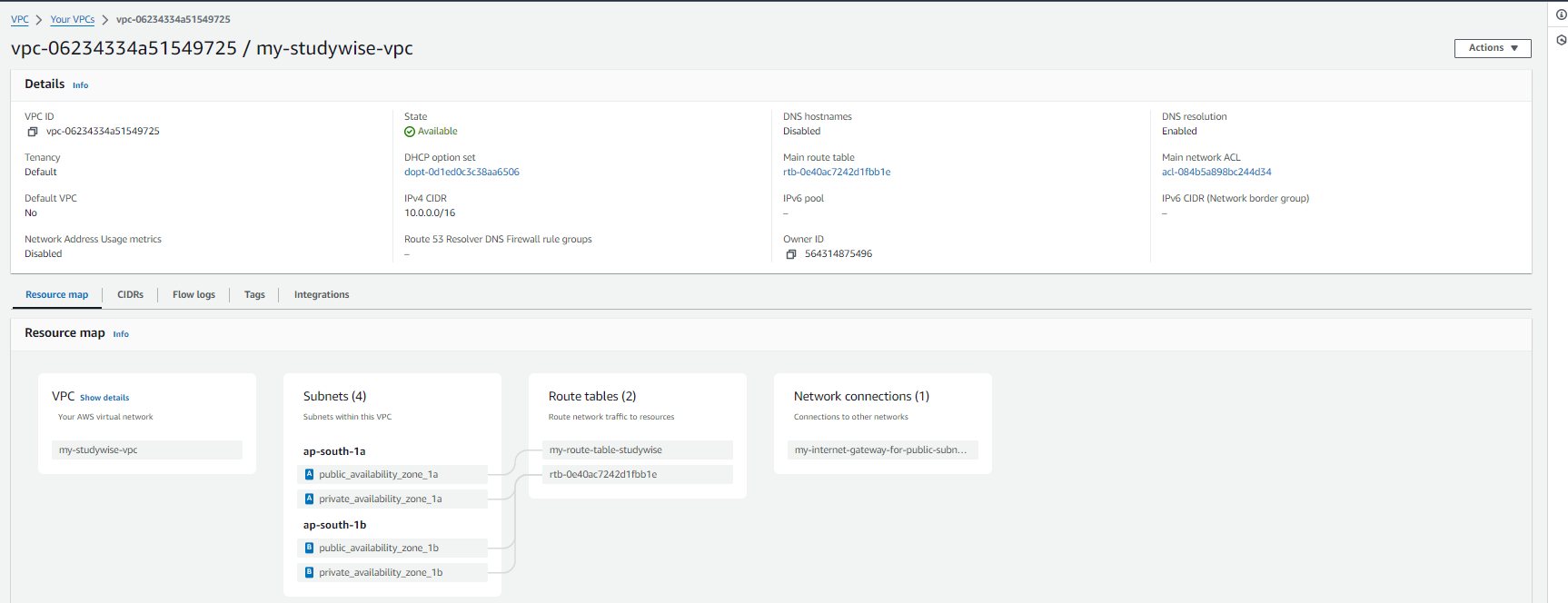
Click on 'Add route' and give the destination which is the internet in our case it is generally taken as 0.0.0.0/0 and select the target as Internet gateway, it will show your Internet gateway ID.
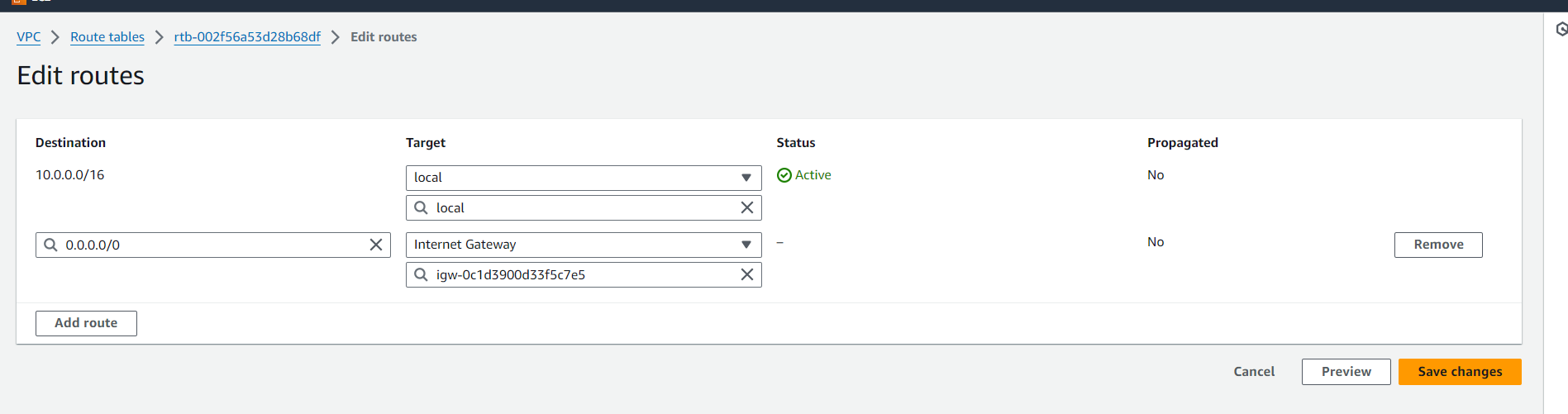
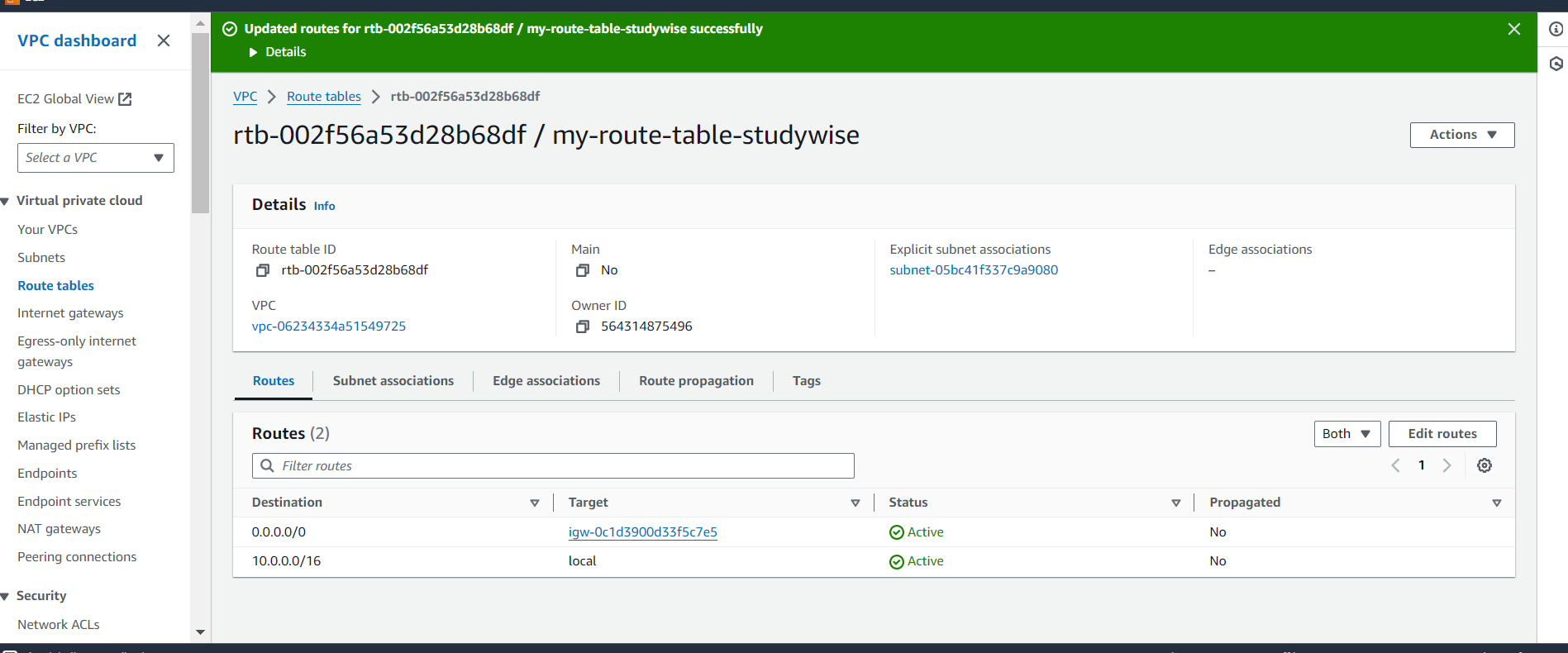
Now you can see resource map, internet gateway is attached to the subnet association i.e public_availability_zone_1a
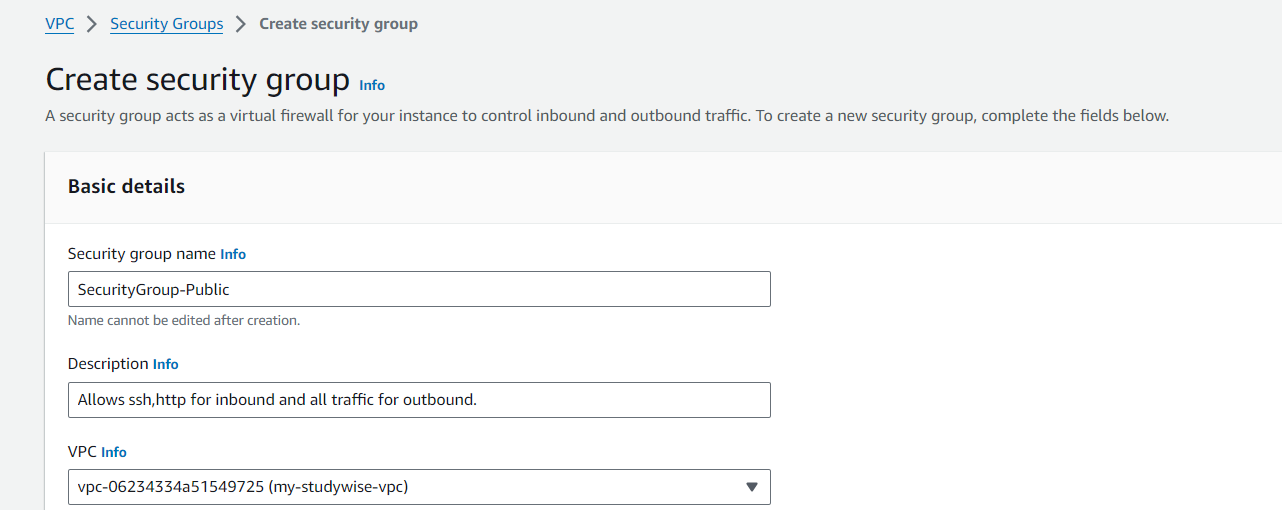
Create a Security Group for public and private subnets:
Here I am configuring the subnets for demonstrating the traffic allowed and blocked by Security Groups.
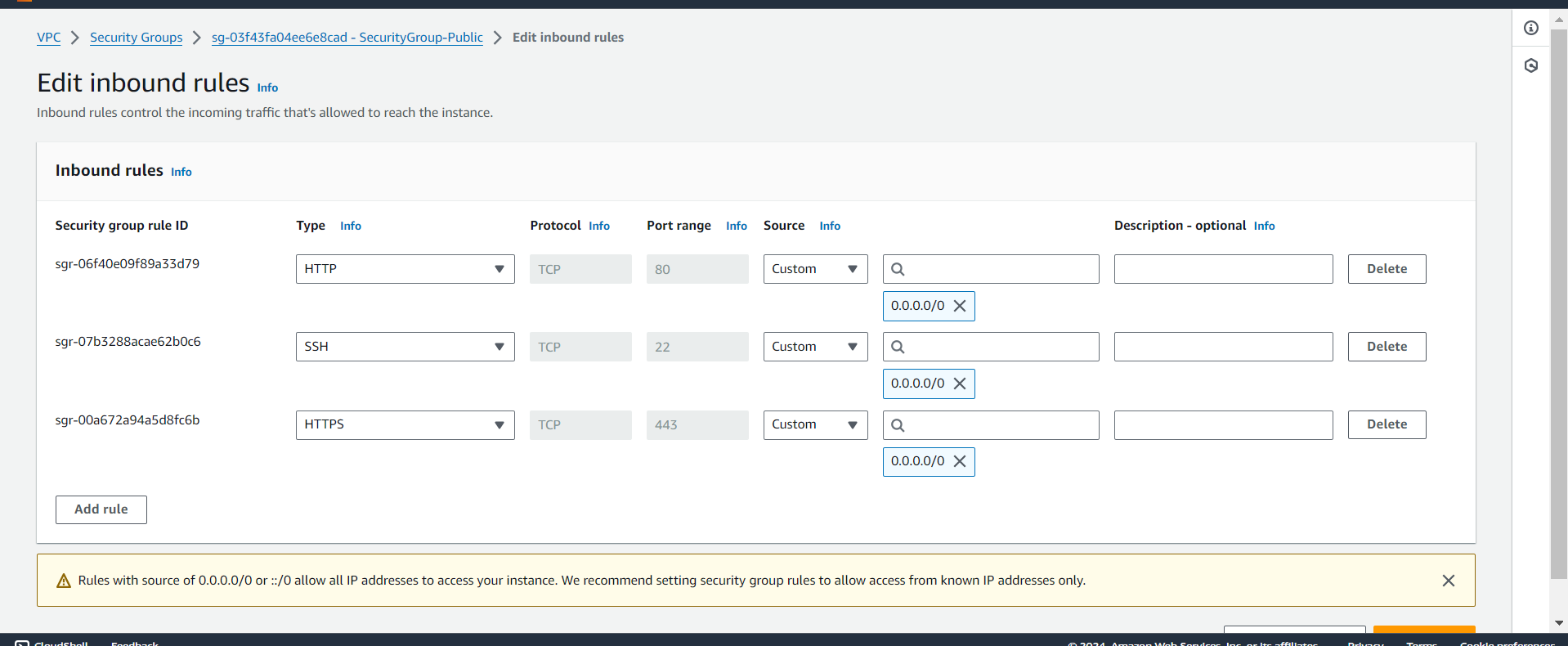
Public Security Group-
Inbound : HTTP(80), HTTPS(443), SSH(22)
Outbound : All traffic
Private Security Group-
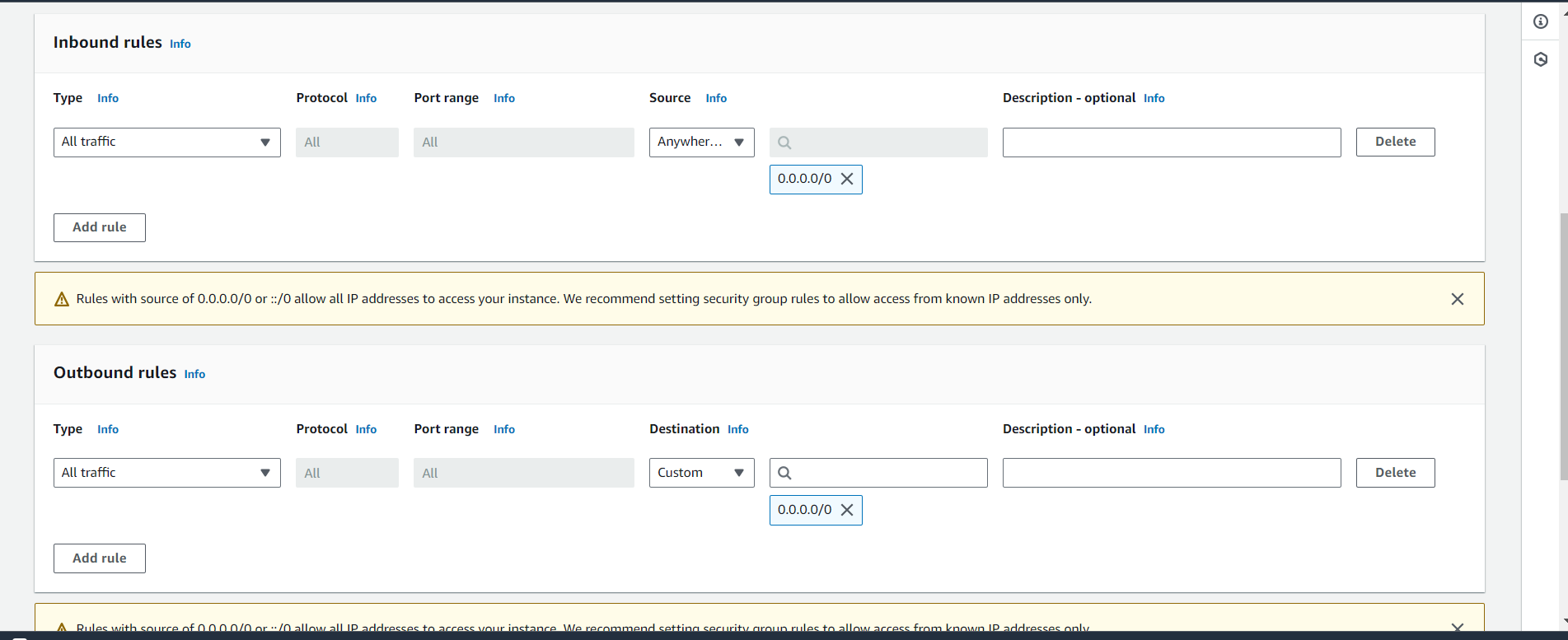
Inbound : All traffic
Outbound : All traffic
Similarly create a security group for private.
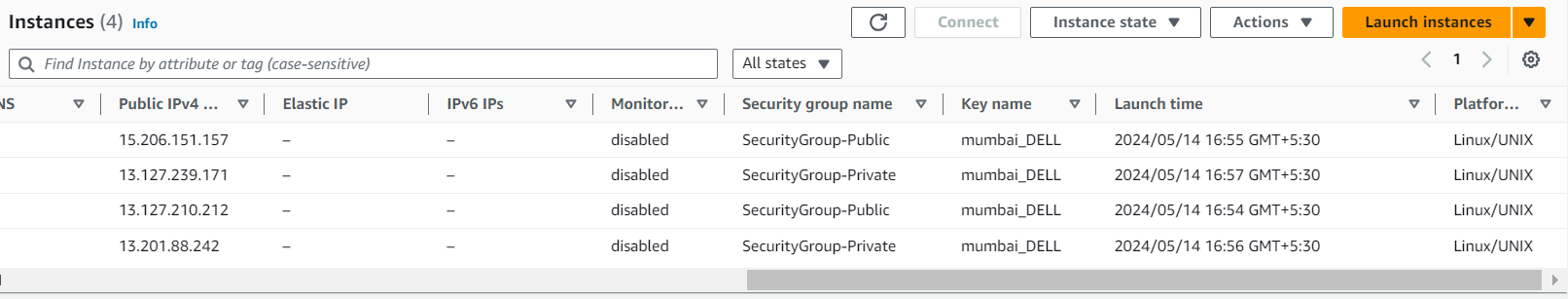
Launch EC2 Instances:
Now that your VPC is set up, you can start launching resources like EC2 instances or databases within the defined subnets.
Define proper name for your instance and select AMI of your choice.
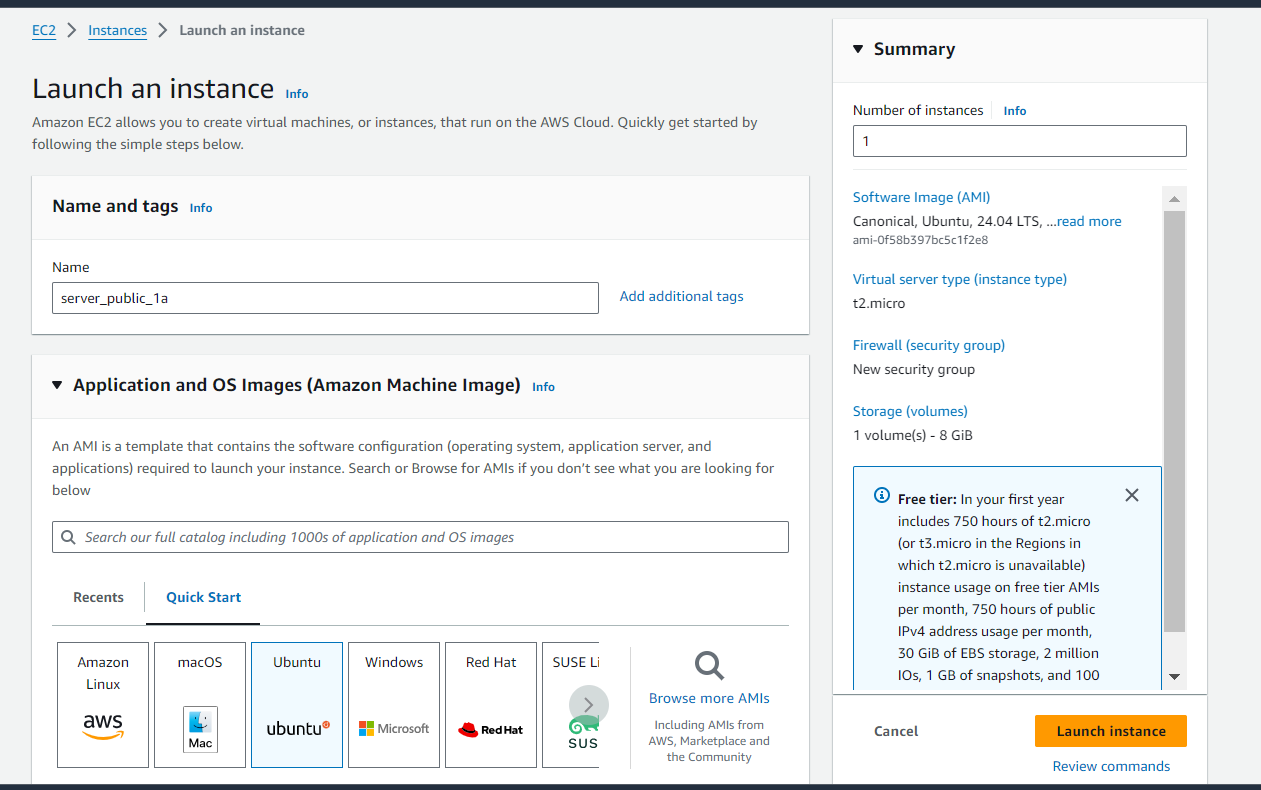
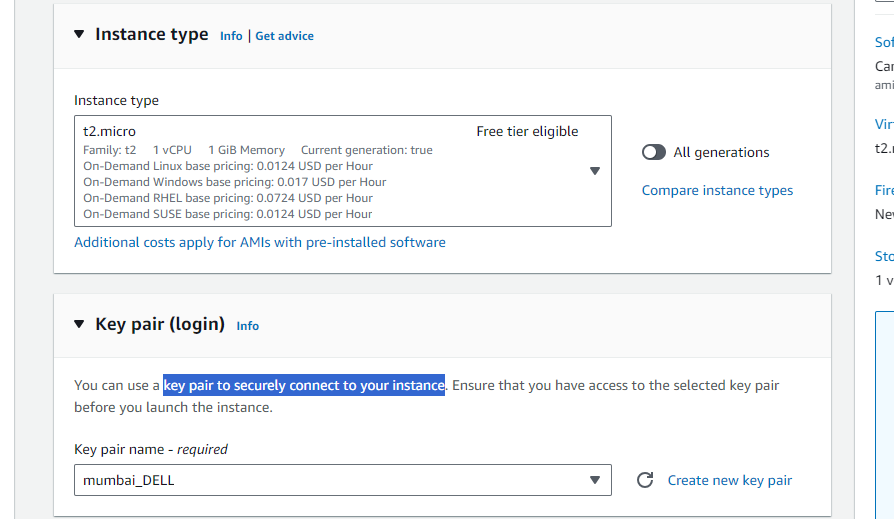
You can choose t2.micro as your instance type and select key pair to securely connect to your instance.
Click on 'Edit' in Network settings and select our custom VPC and custom subnets. Enable Auto-assign public IP.
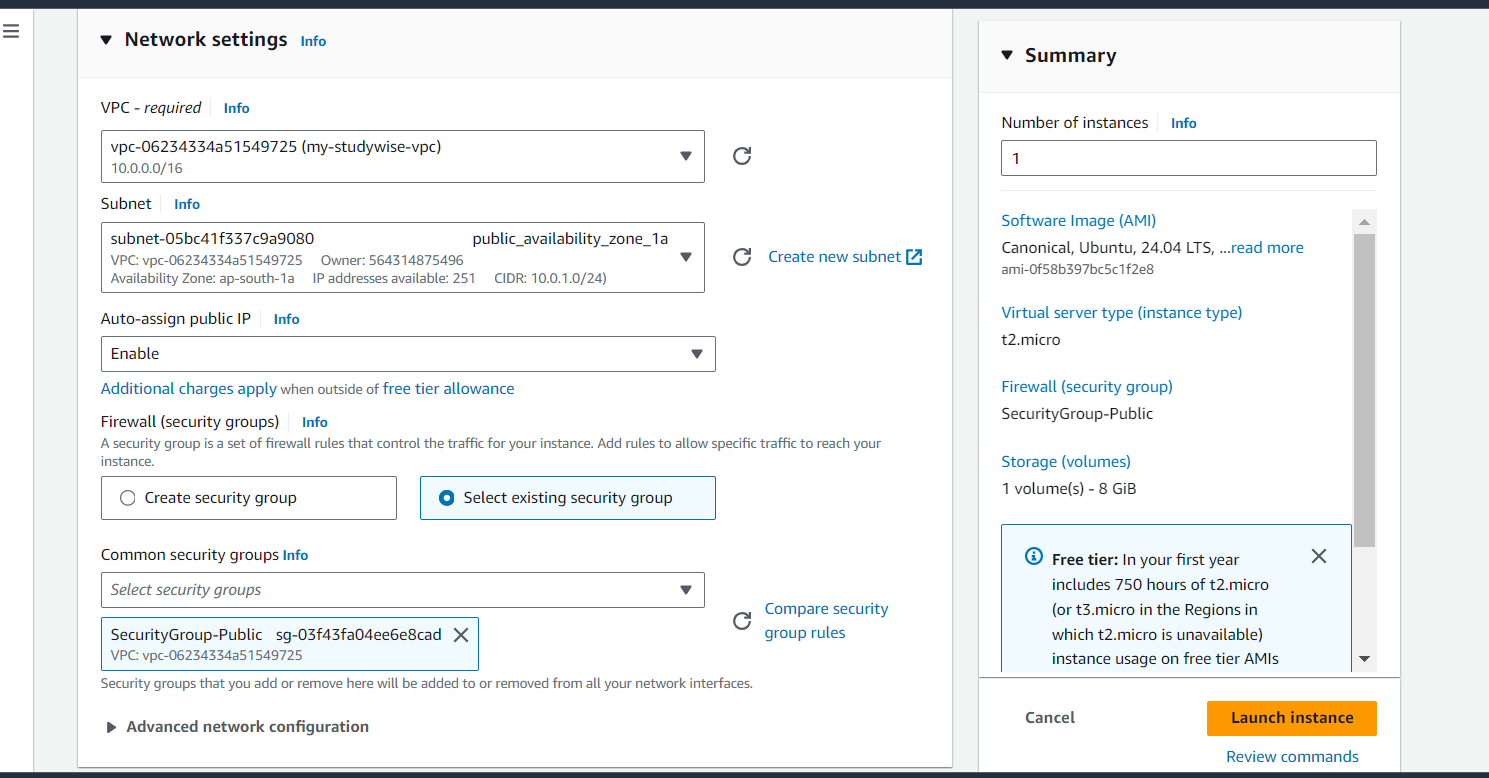
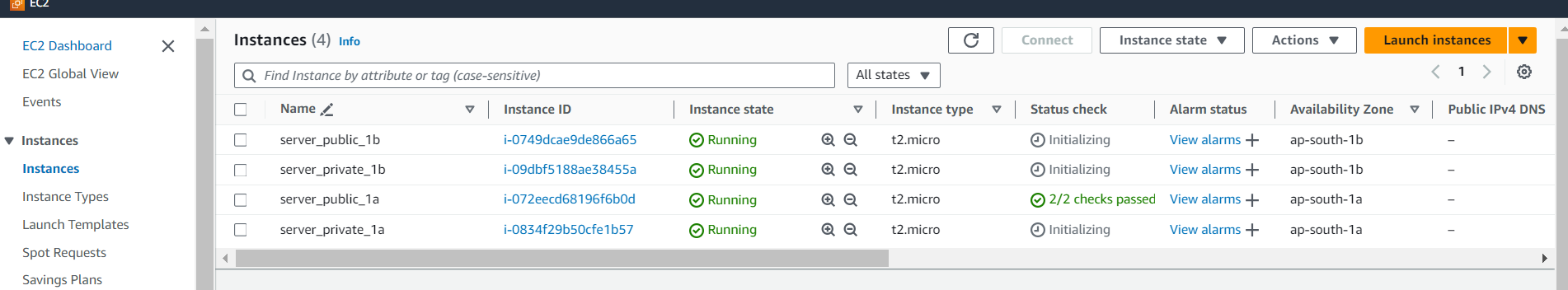
Similarly launch an instance in each of the public and private subnets.
Assign appropriate security groups to each instance.
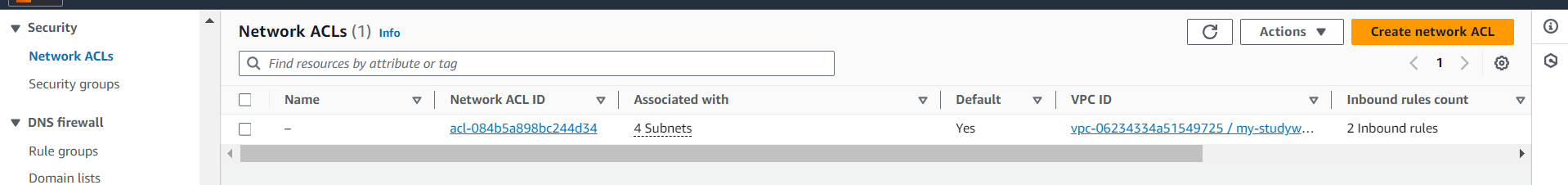
Configure Network Access Control Lists (NACLs)
Create a Network ACL on selecting your VPC.
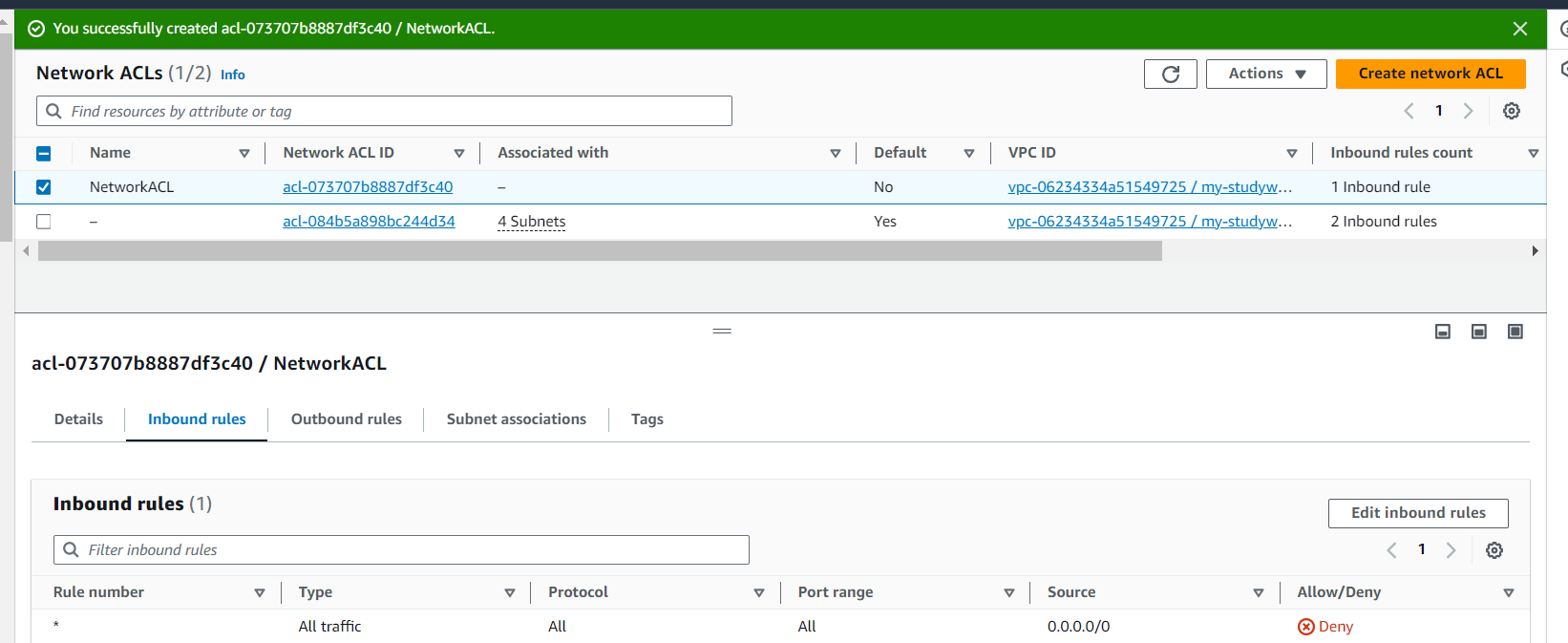
Click Edit Inbound rules:
Allow HTTP (80) , SSH (22)
Deny HTTPS(443)
Click Edit Outbound Rules:
All traffic
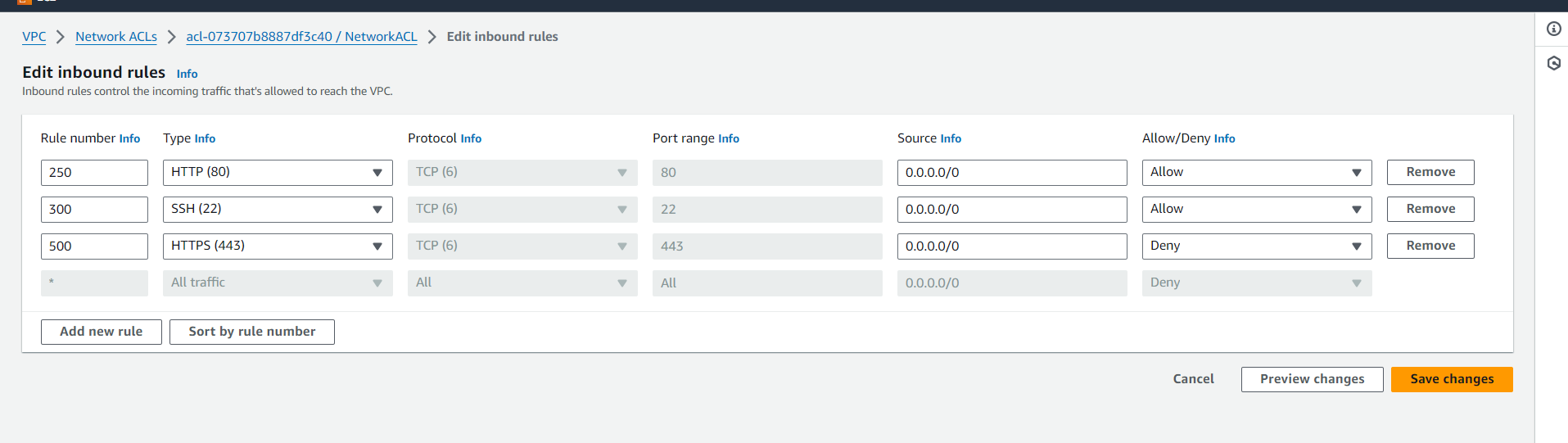
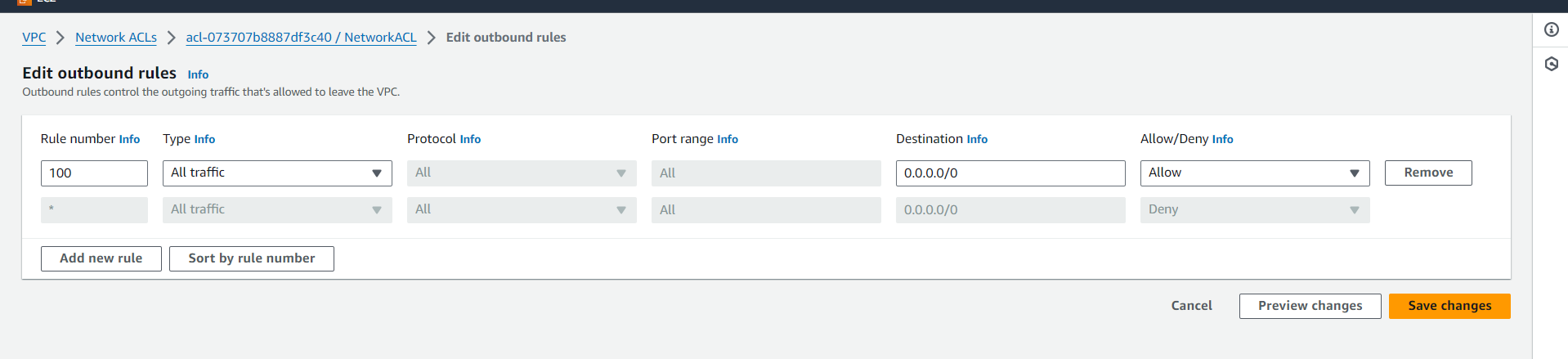
On doing this setup it is clear that public subnet is attached to Internet Gateway hence instances In that subnet can access internet.
Whereas the instances in private subnet cannot access internet.
Connect (server_public_1a) instance using EC2 Instance Connect
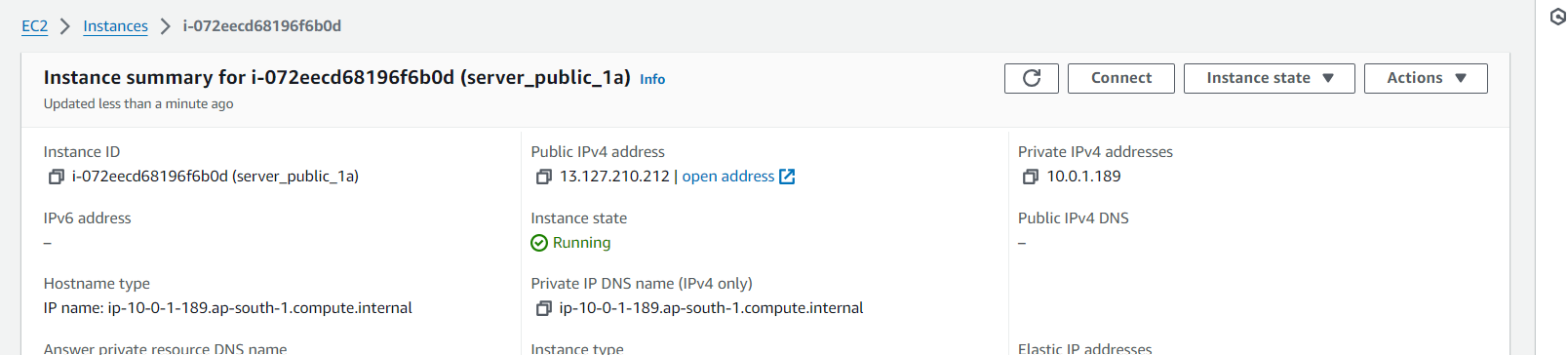
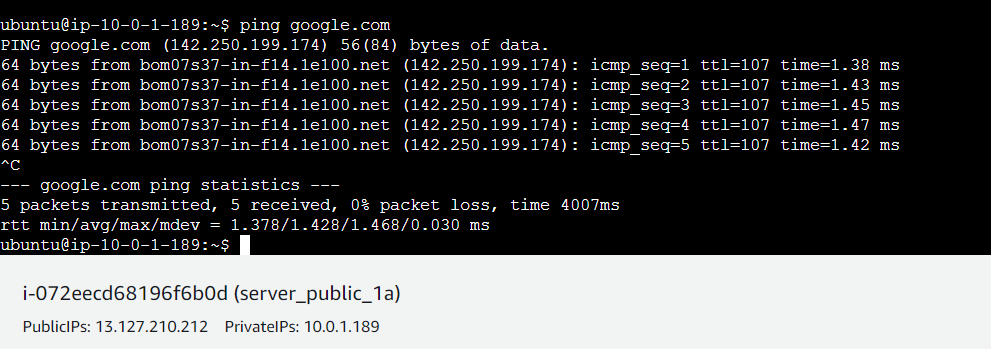
Hence Proved.
When you try to connect (server_private_1a) instance using EC2 Instance Connect, you will receive a errors like:
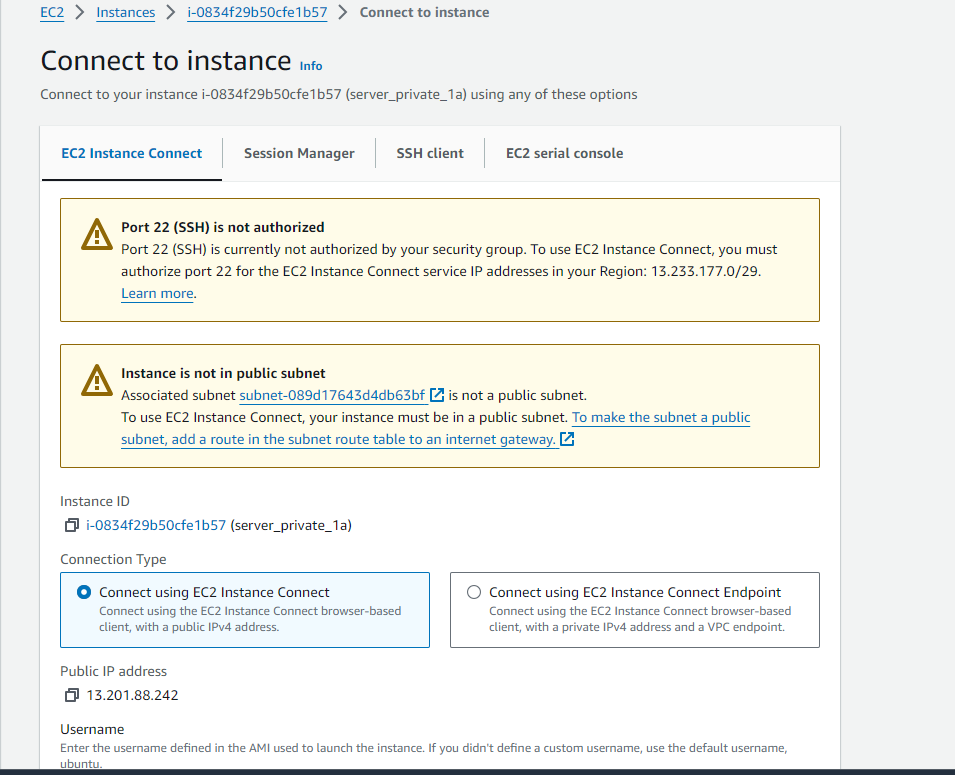
To troubleshoot Port 22 (SSH) is not authorized.
Edit Inbound rules, authorize port 22 for the EC2 Instance Connect service IP addresses in your Region
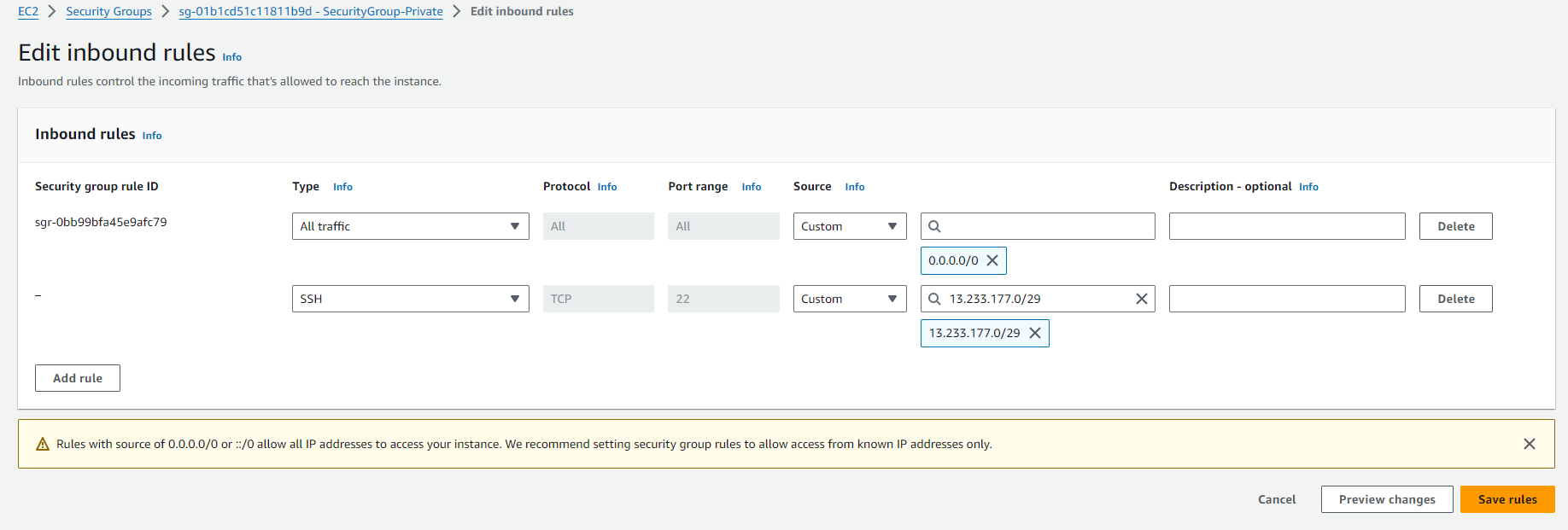
To troubleshoot Instance is not in public subnet
Associated subnet subnet-089d17643d4db63bfis not a public subnet.
To make the subnet a public subnet, add a route in the subnet route table to an internet gateway Follow below steps.
Create and Attach NAT Gateway:
Go to the VPC dashboard and select "NAT Gateways."
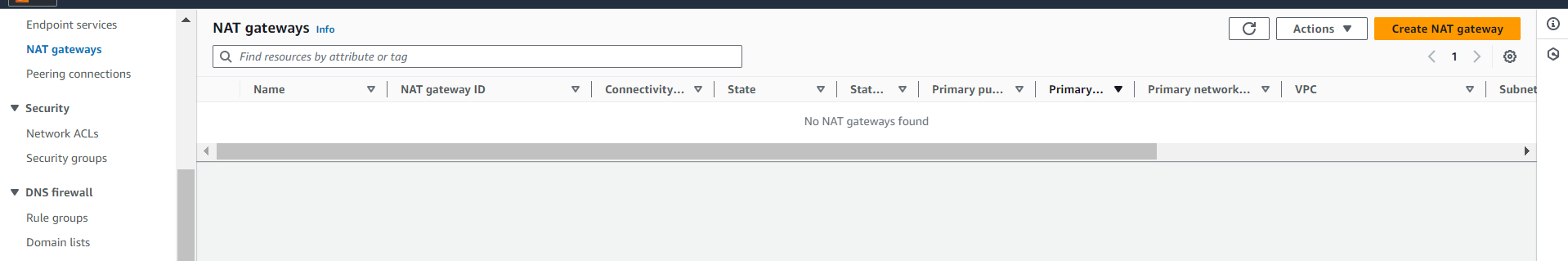
Click on "Create NAT Gateway" and select the public subnet. Ensure the Elastic IP is allocated.
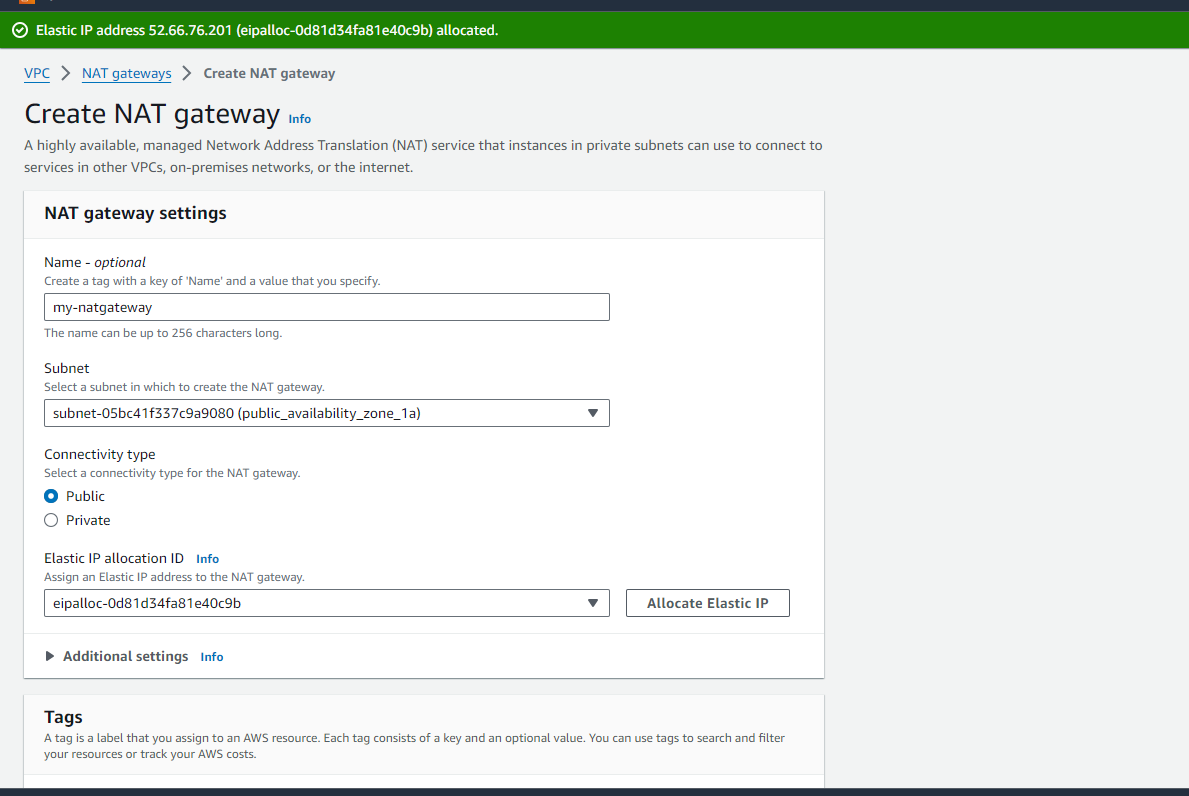
Now select your Route Table you just created and Click on 'Edit subnet associations'.
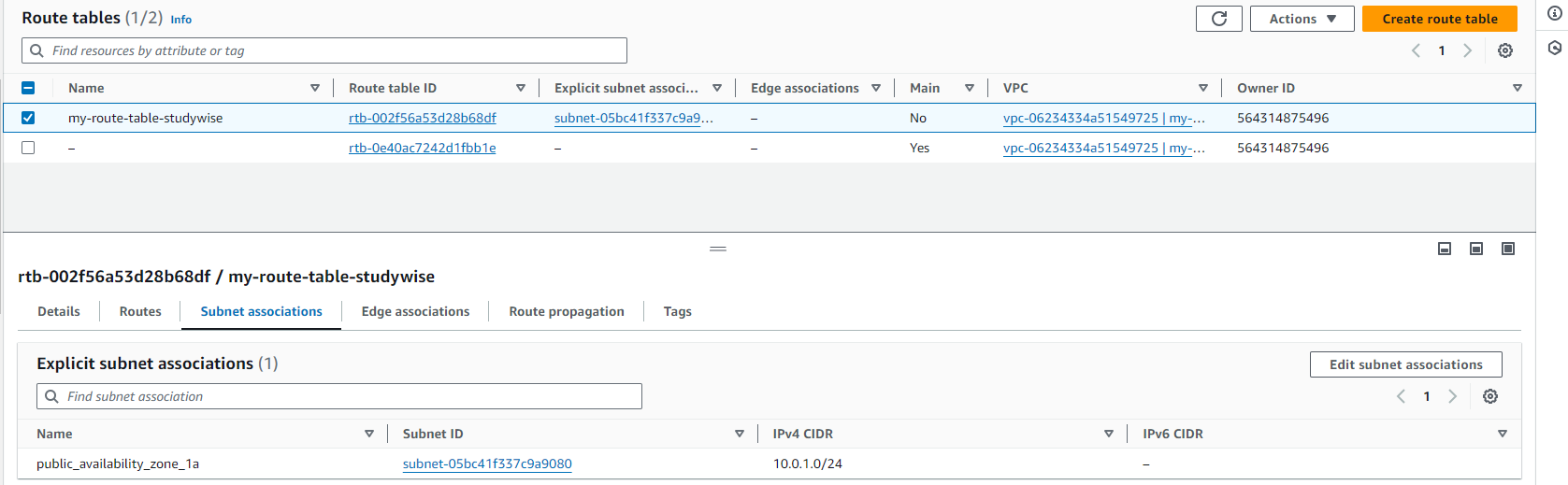
Add your subnet (private_availability_zone_1a) where you want the internet access and click on save associations
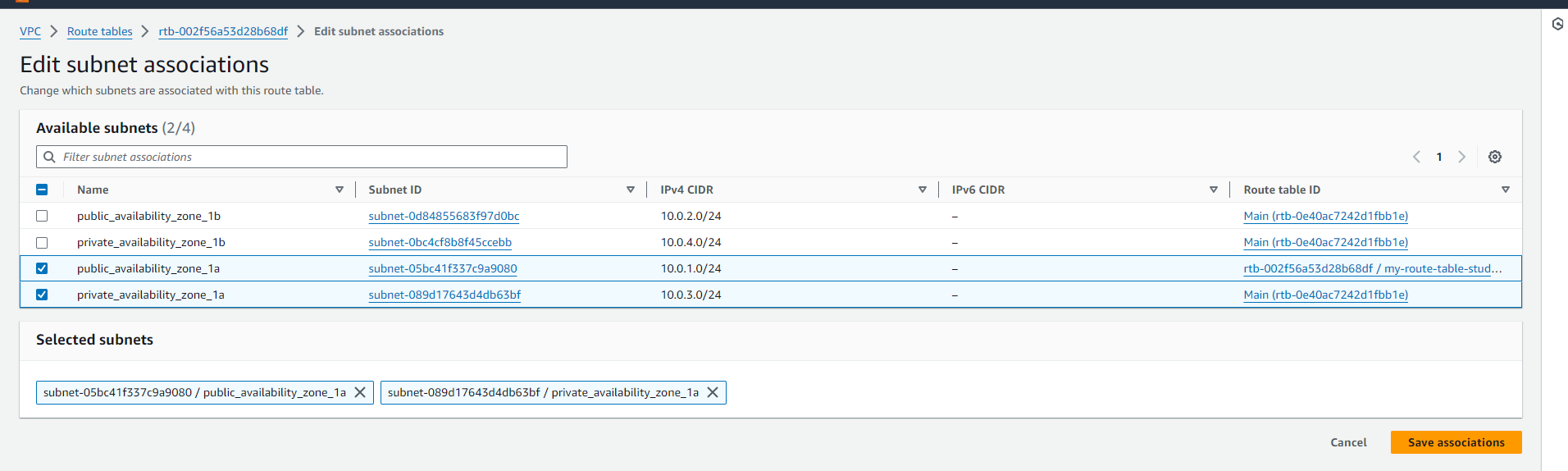
If you check resource map of your VPC you'll see that NAT Gateway is visible but is not associated with subnet.
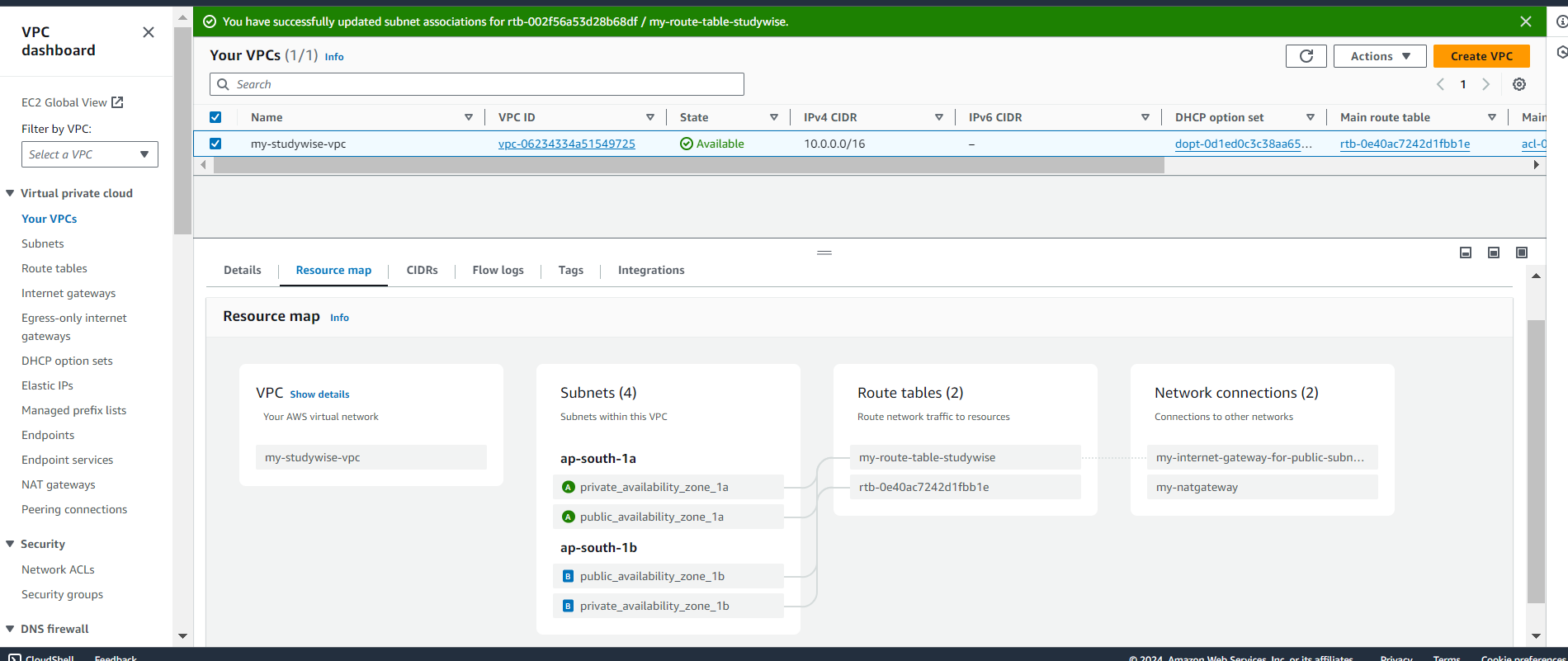
Update the private subnet's route table to include a route for 0.0.0.0/8 pointing to the NAT Gateway. In Actions tab select Edit Routes.
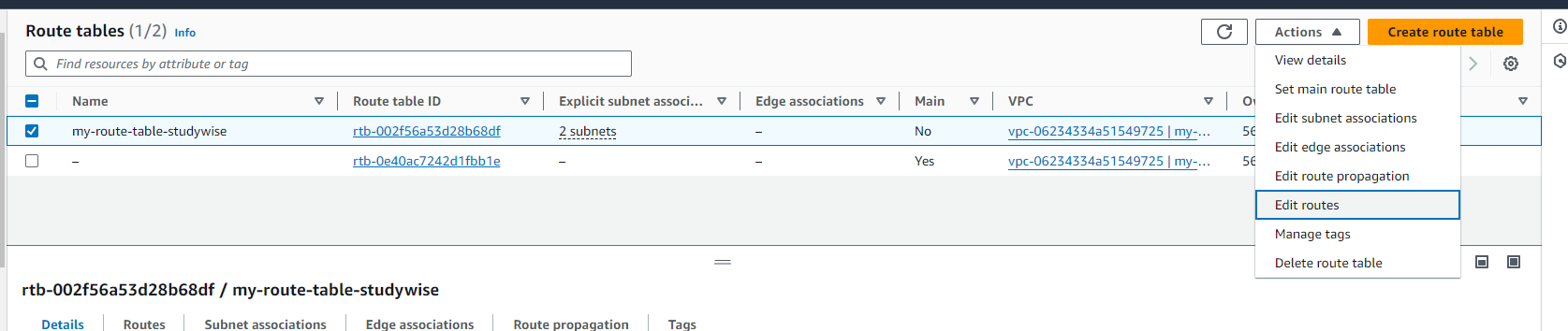
Add the required configuration. And click on Save Changes.
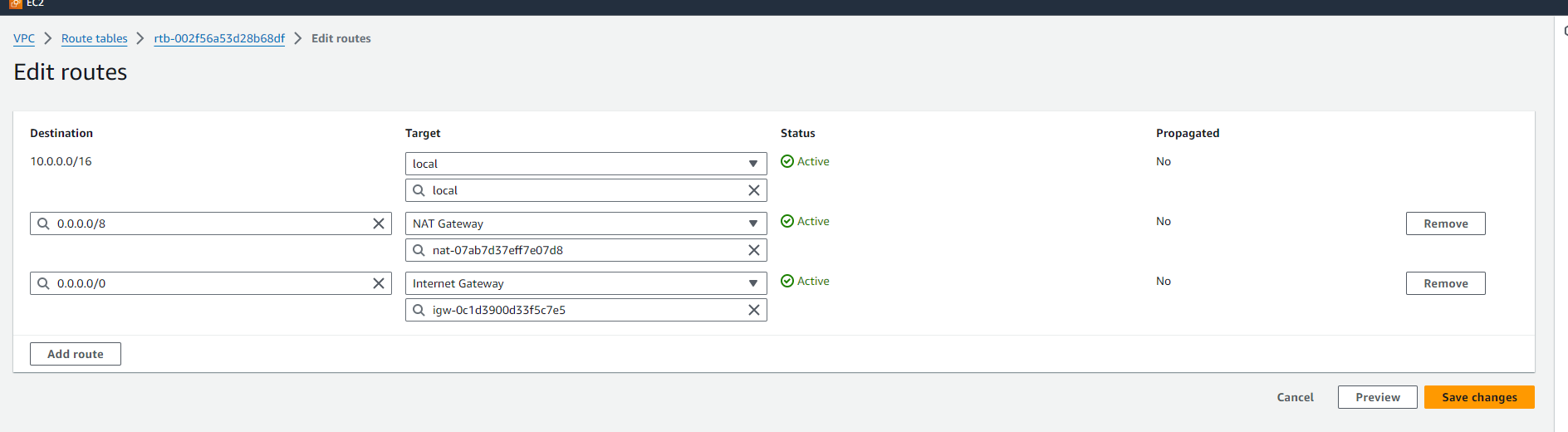
Now you will be able to connect your instance using EC2 Instance Connect. You can test the internet connectivity using telnet or ping.
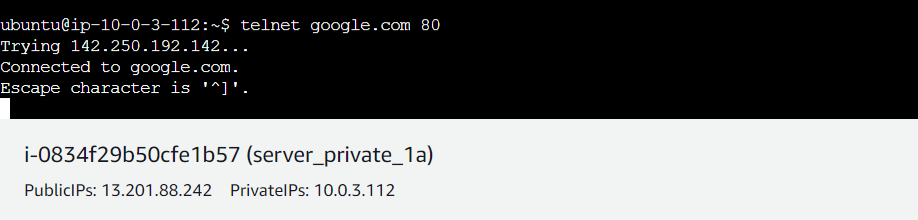
Test Connectivity:
Testing Outbound Connection:
Test Connectivity using cURL or wget: Once logged into the server, you can test connectivity to external resources using curl or wget commands. cURL is primarily used for transferring data whereas wget is used for downloading files using various network protocols like HTTP, HTTPS, FTP.
For example, to test connectivity to a web server over HTTP (port 80), you can use:
curl http://google.comorwgethttp://google.com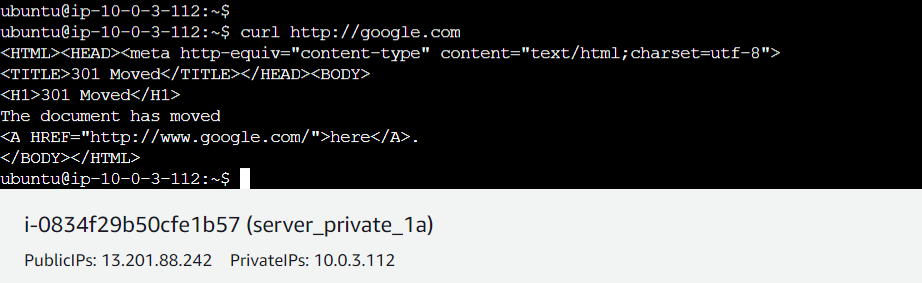
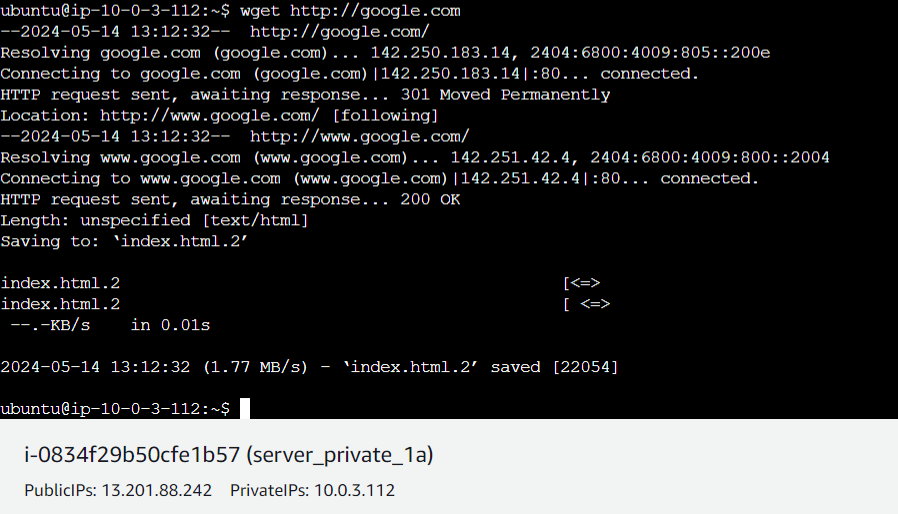
If you are getting an HTML page/code you can connect to the resource. Similarly test for https.
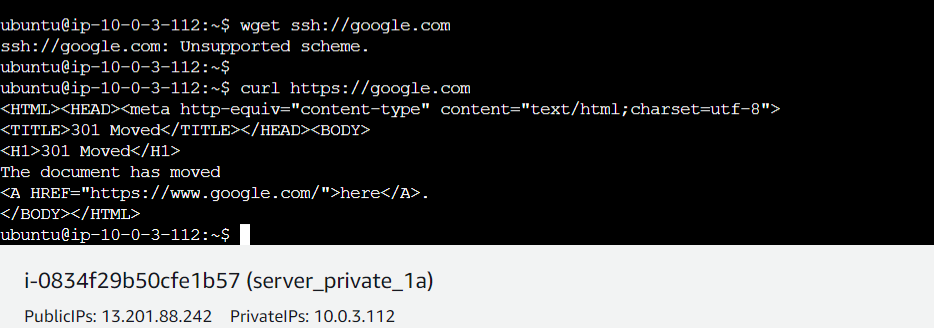
Now check for SSH. You can test SSH connectivity using
ssh username@destination_ip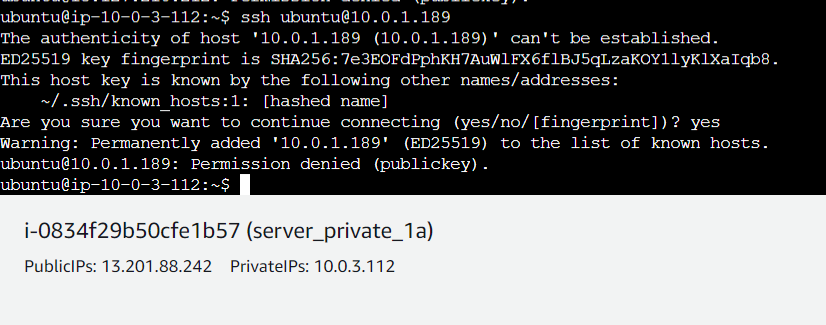
You will see that you are able to access SSH connection.
Testing Inbound Connection:
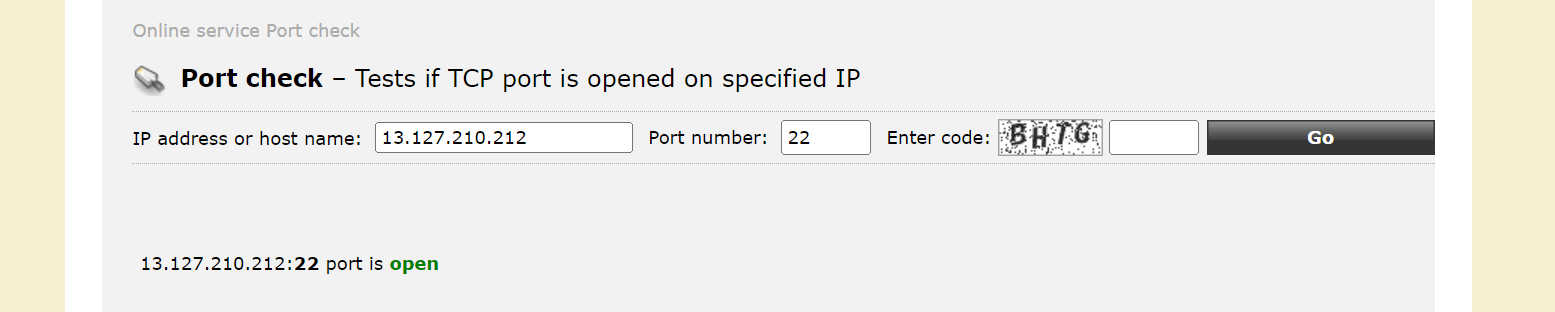
To test inbound traffic connectivity to your server, you can use online port scanning tools. Here I am using https://portchecker.co/canyouseeme or https://ping.eu/port-chk/
Testing with SSH port 22
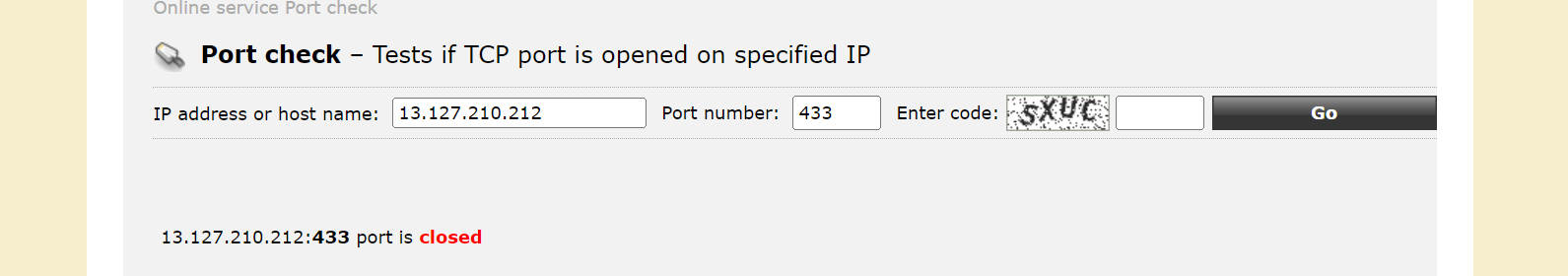
Testing with HTTPS port 433
To understand this you can watch my youtube video :
Test Inter-Availability Zone subnet Connectivity:
Ping or telnet from an EC2 instance in one private subnet to an EC2 instance in the other private subnet. In the route table attach the remaining subnet associations.
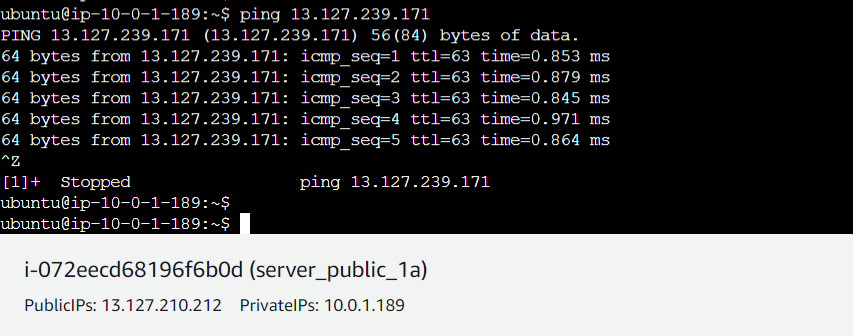
This should provide a comprehensive setup and demonstration of VPC configuration along with inter and intra-subnet connectivity in AWS Mumbai region.
Set up VPC peering in AWS, along with testing connectivity and creating an RDS instance connected to the peered VPC:
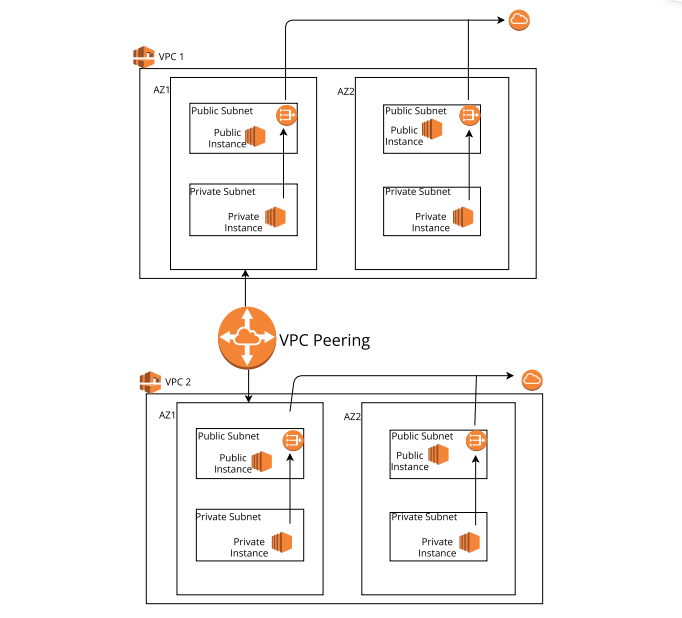
Navigate to VPC Dashboard and select VPC and more in any region of your choice.
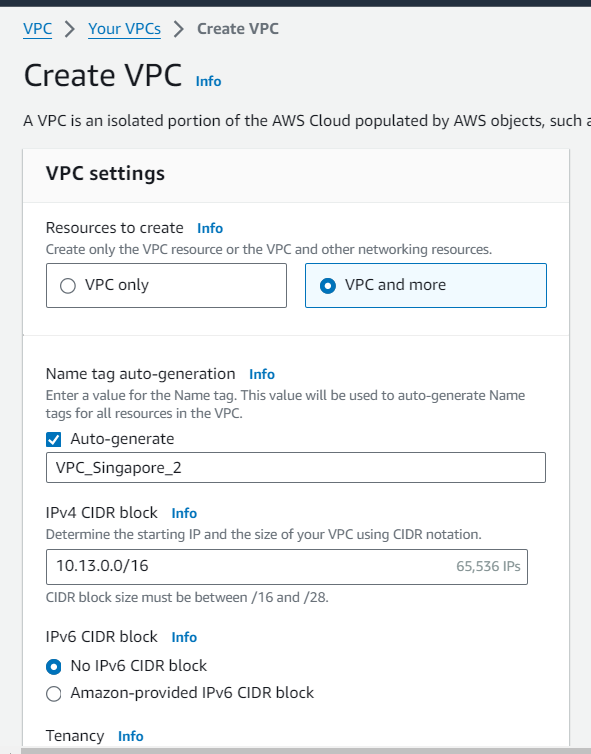
Keep the number of public and private subnets as 2. Select NAT Gateway in 1 AZ and VPC endpoint for S3 gateway.
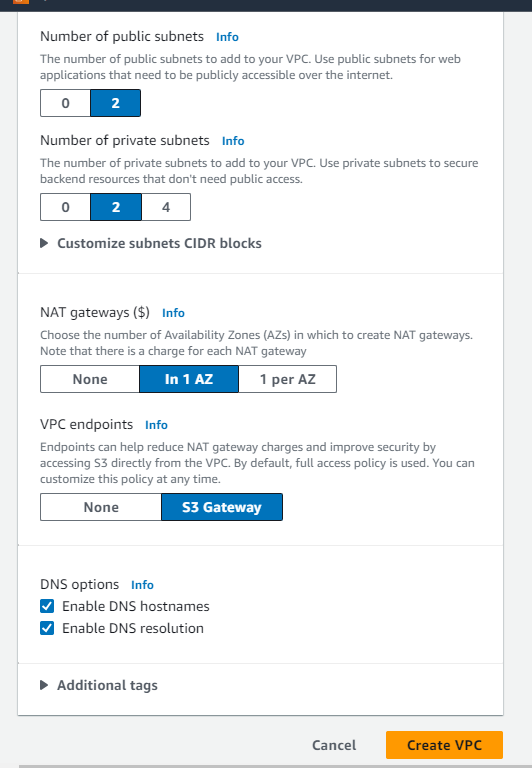
You can see the details of VPC being created:
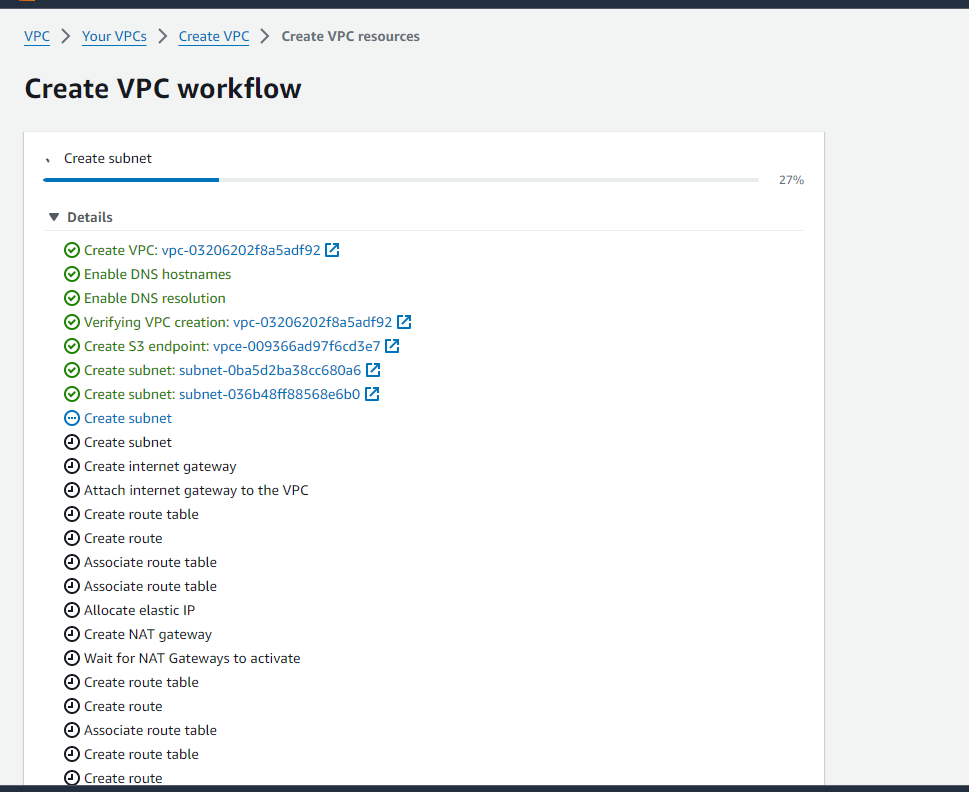
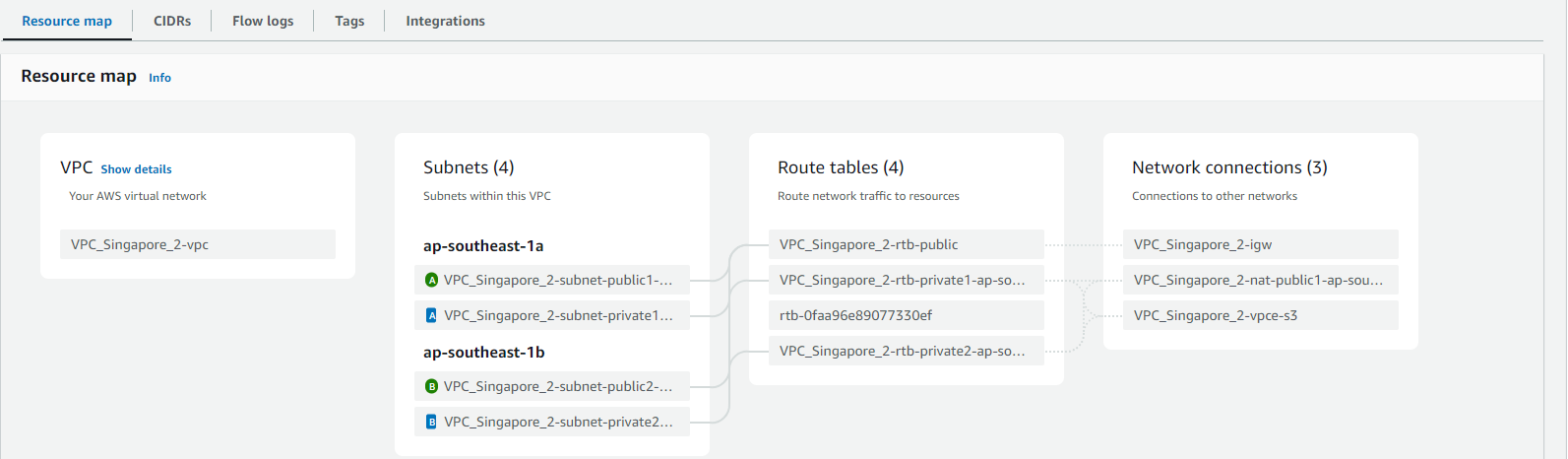
See Resource Map for better understanding.
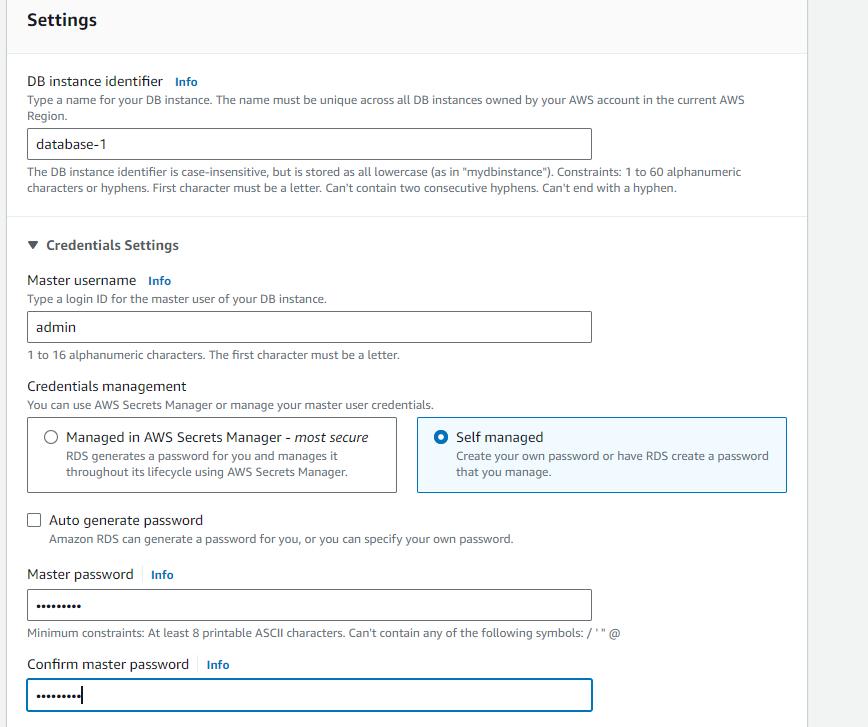
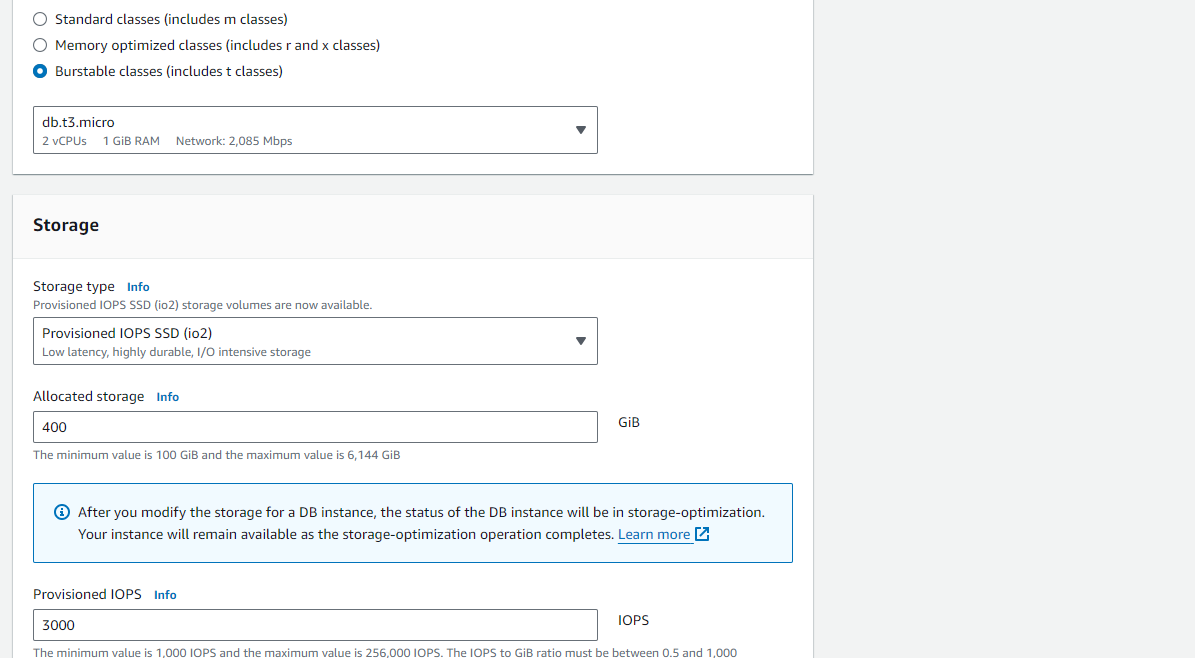
Create RDS Instance:
Navigate to the RDS service in the AWS Management Console.
Click on "Create database" and follow the wizard to create an RDS instance.
Choose the appropriate DB engine, instance specifications, template and other settings.
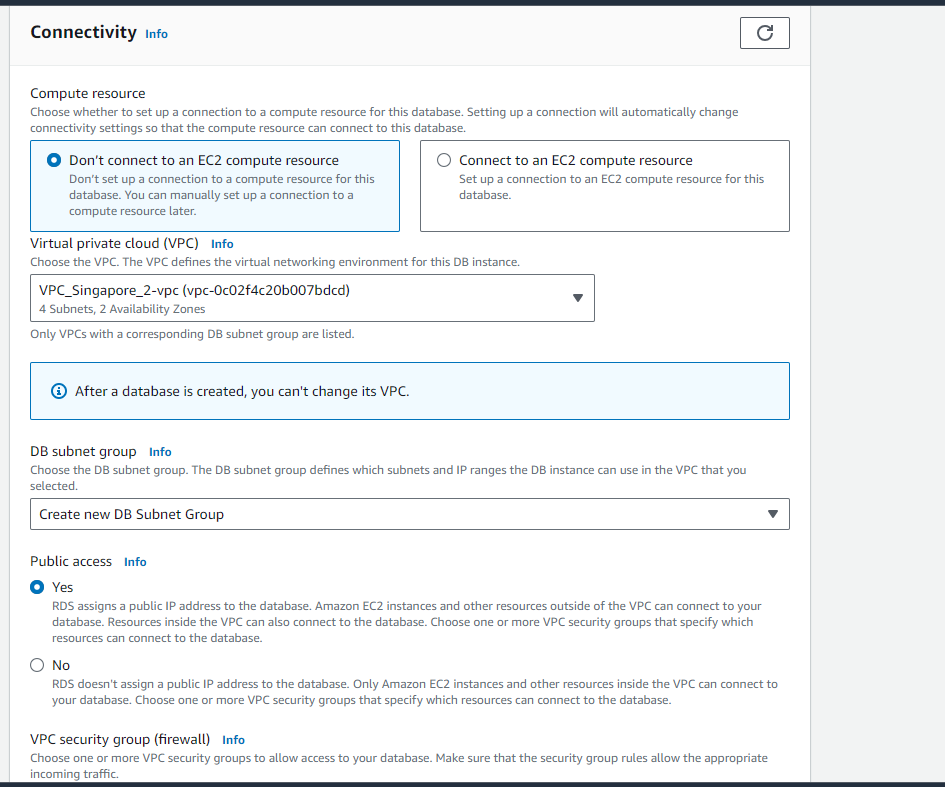
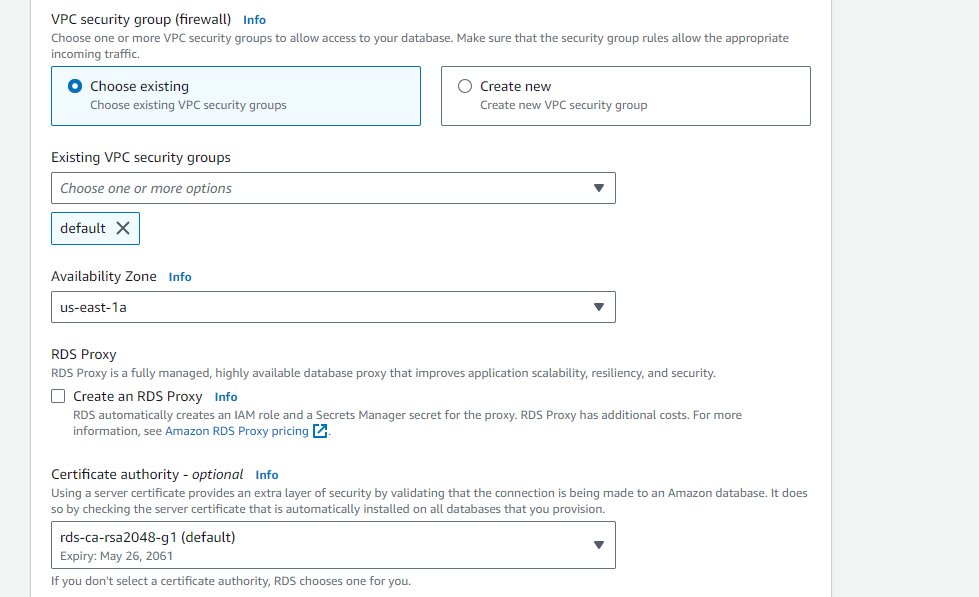
In the "Connectivity" section, select the VPC and subnets where you want to deploy the RDS instance.
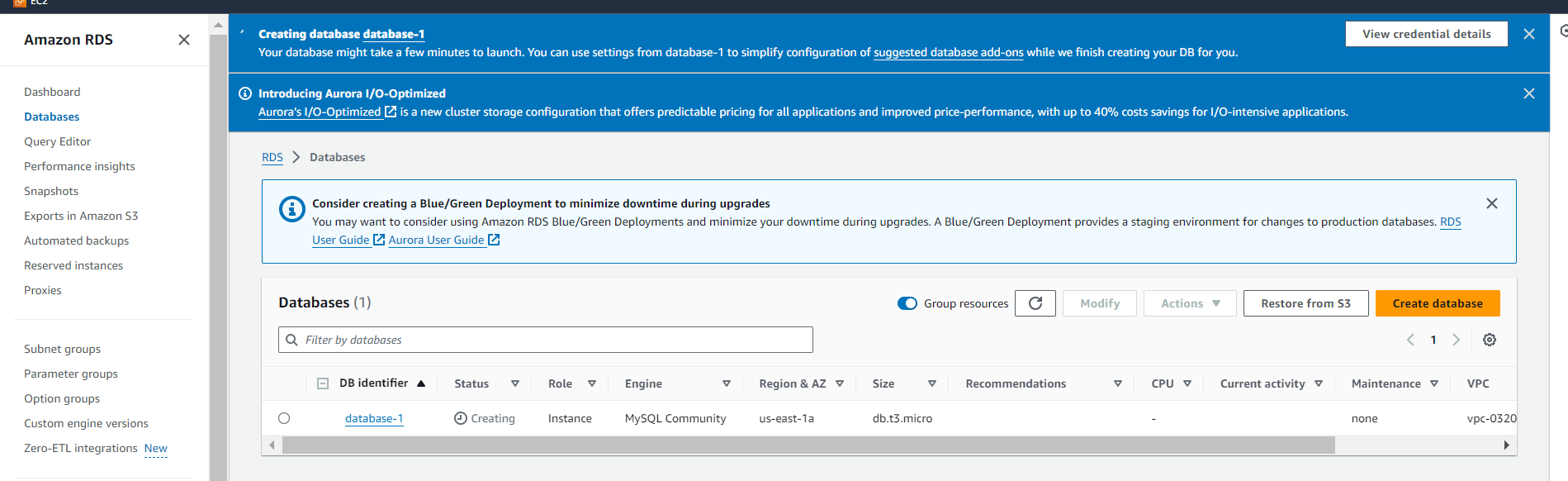
Complete the wizard and create the RDS instance.
Create VPC Peering Connection:
Click on "Peering Connections" in the left sidebar.
Click on "Create Peering Connection" and follow the wizard. Select the VPC you want to peer with from the dropdown list. Optionally, provide a name tag for the peering connection.
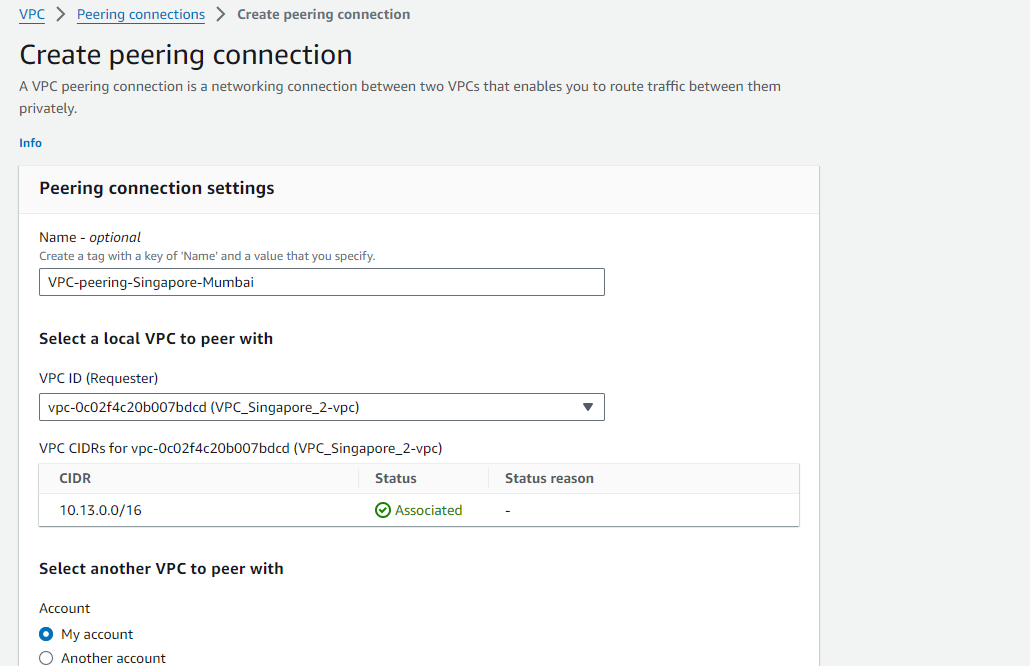
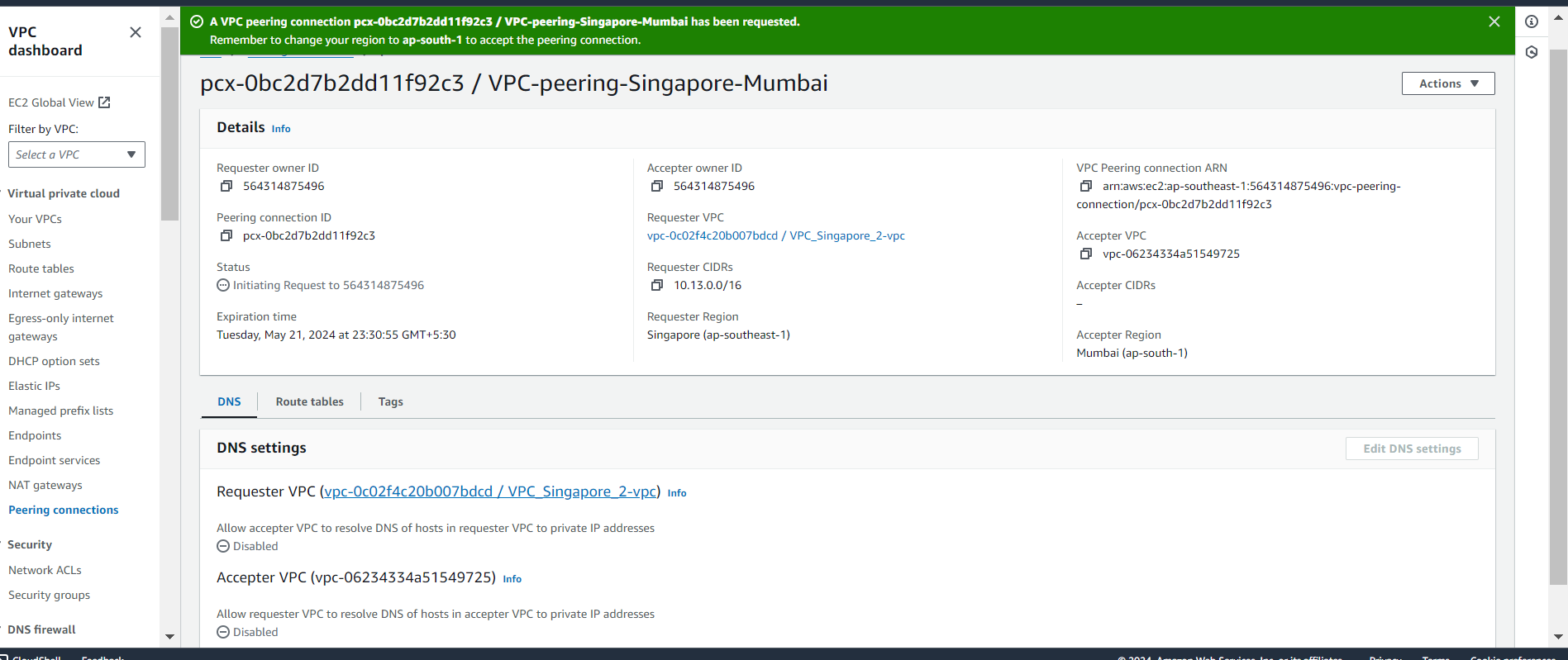
Select proper VPC ID. Click on "Create Peering Connection".
Accept Peering Connection:
After creating the peering connection, select it from the list.
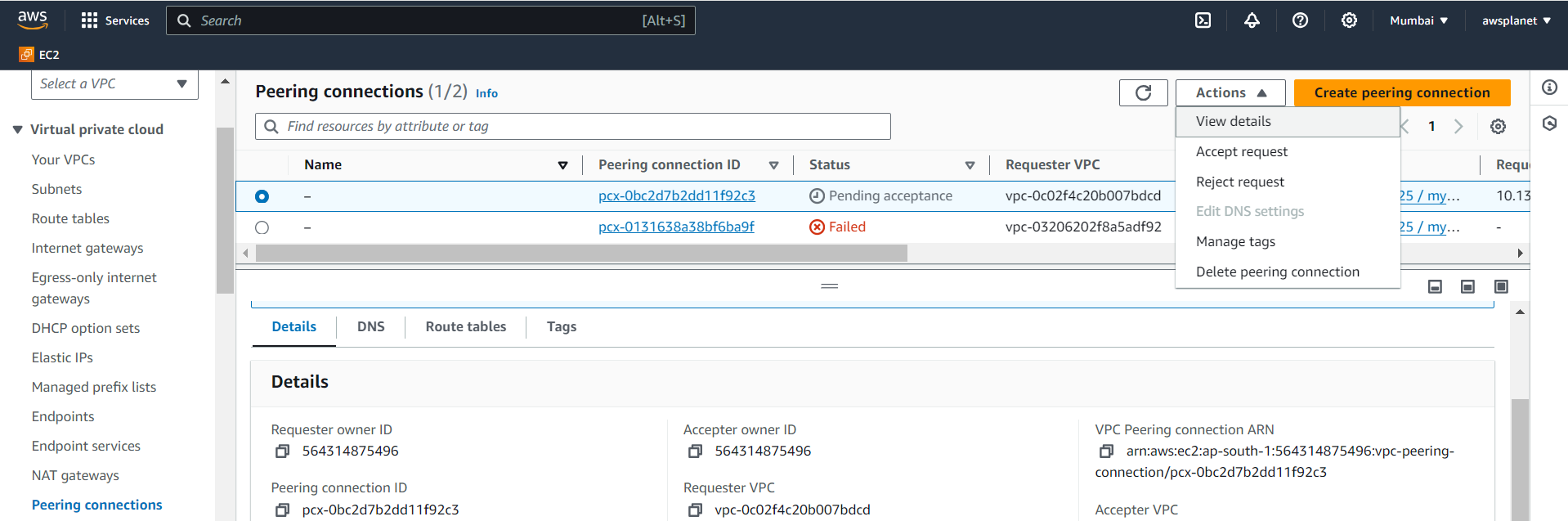
Click on "Actions" and then "Accept Request".
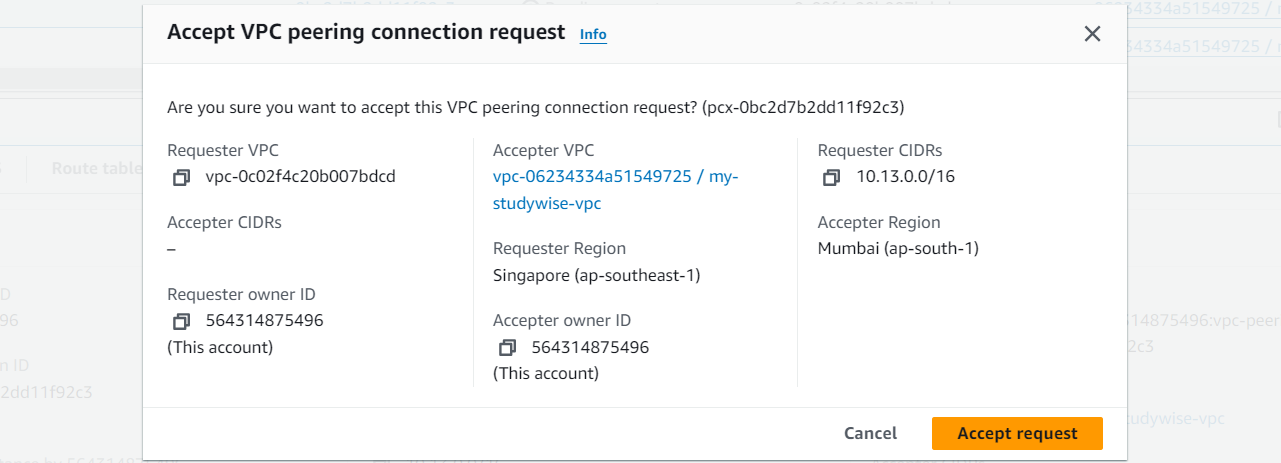
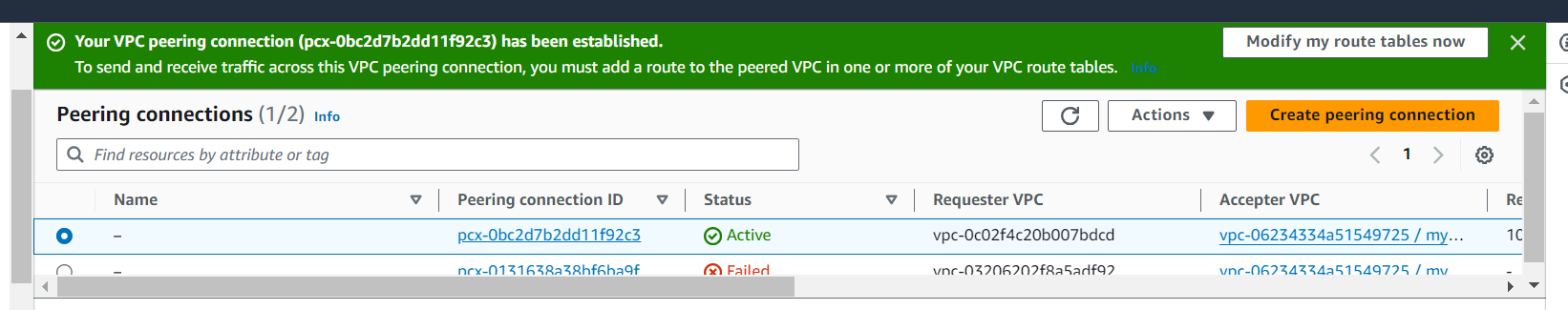
Confirm the settings and click on "Yes, Accept". Update Route Tables:
Go to the route tables associated with the subnets in each VPC. Add a route for the CIDR block of the peered VPC pointing to the peering connection.
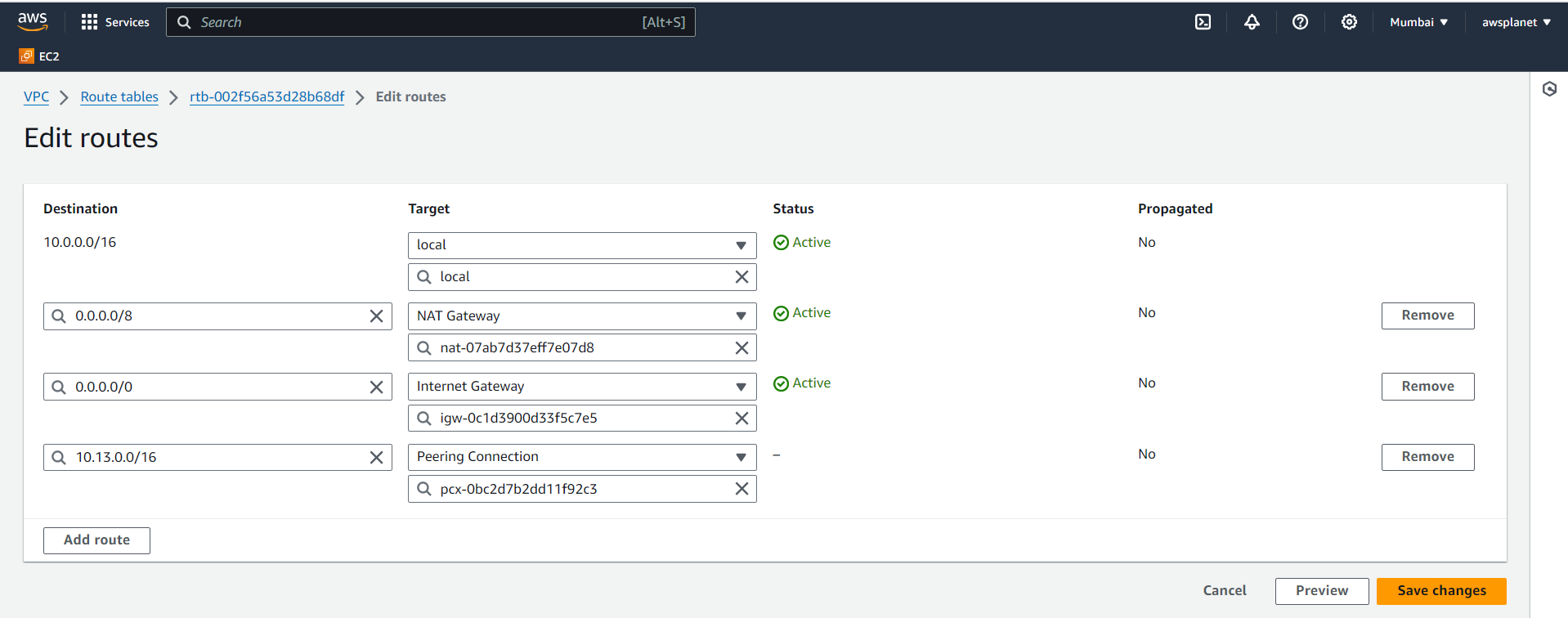
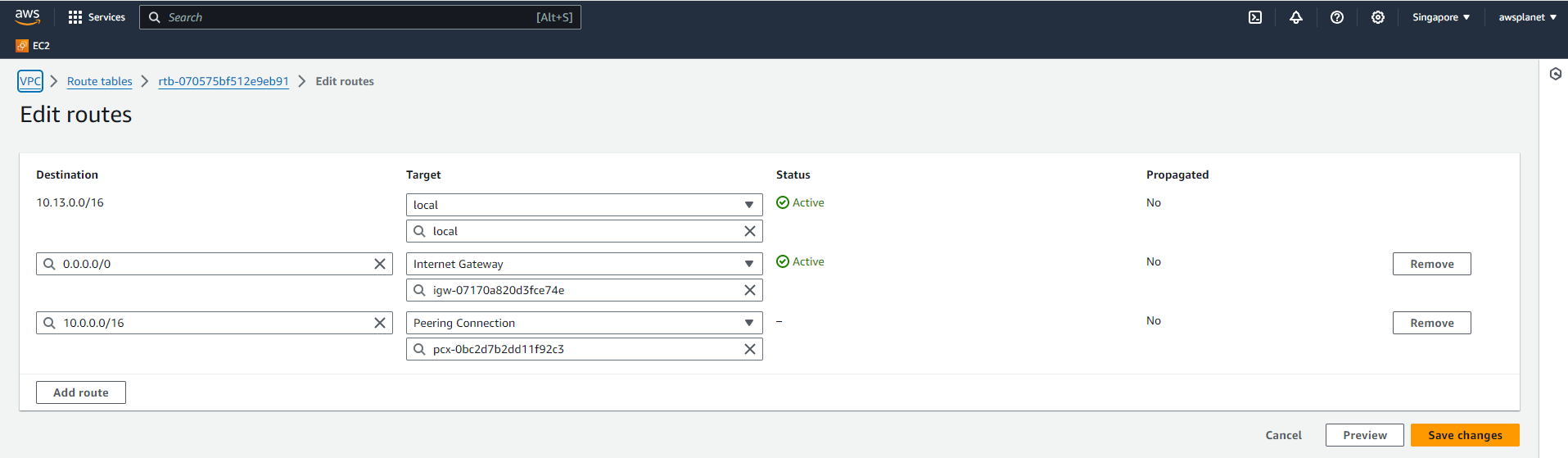
Repeat this step for both VPCs involved in the peering.
Testing Connectivity: Ping Test:
Use the ping command from an instance in one VPC to an instance in the peered VPC. Syntax:
ping <private_ip_of_instance_in_peered_VPC>Example:
ping 10.0.4.16Here I am able to ping both my instances in private subnet in Mumbai region from Singapore region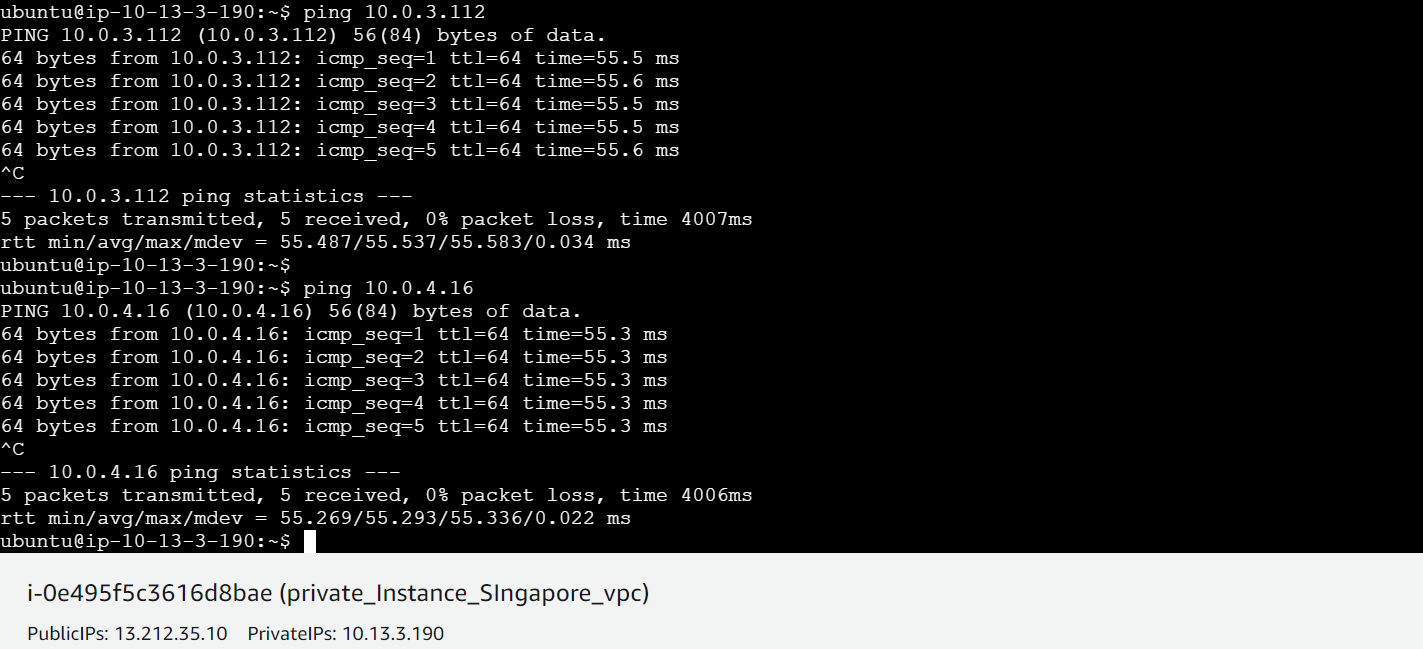
If the VPC peering is set up correctly, you should receive ICMP echo replies indicating successful connectivity.
SSH Test:
If SSH (port 22) is allowed between the instances, you can SSH from an instance in one VPC to an instance in the peered VPC.
Syntax:
ssh @<private_ip_of_instance_in_peered_VPC>Example: ssh ec2-user@10.1.0.10
If connectivity is successful, you should be able to log in to the instance in the peered VPC.
Thankyou for your time.
Subscribe to my newsletter
Read articles from Shraddha Suryawanshi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
