Understanding Server-Side Request Forgery (SSRF)
 Cloud Tuned
Cloud Tuned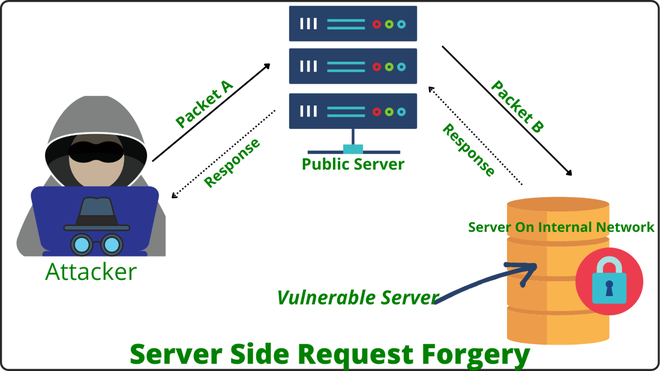
Understanding Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) is a security vulnerability that occurs when an attacker is able to send unauthorized requests from a vulnerable server. This type of attack can lead to data leaks, server exploitation, and even full system compromise. In this article, we'll delve into SSRF, explore how it works, and discuss strategies for mitigating this threat.
How SSRF Works
Exploitable Endpoint: The attacker identifies a vulnerable endpoint within the target server, typically one that accepts user-supplied URLs or performs external requests.
Malicious Input: The attacker submits a specially crafted request containing a URL that points to a sensitive internal resource or a restricted external server.
Server-Side Execution: The server processes the attacker's request, retrieves the specified URL, and returns the response to the attacker.
Exploitation: Depending on the server's configuration and permissions, the attacker may be able to exploit SSRF to access internal systems, bypass security controls, or perform unauthorized actions on external servers.
Mitigating SSRF Attacks
Input Validation: Implement strict input validation and sanitization mechanisms to prevent attackers from injecting malicious URLs or payloads into requests.
Whitelisting: Maintain a whitelist of allowed URLs or domains that the server is permitted to access. Restrict requests to only those URLs that are explicitly approved.
Network Segmentation: Use network segmentation techniques to isolate sensitive internal resources from external-facing servers. Limit the server's ability to make outbound connections to trusted domains only.
Access Controls: Implement access controls and permissions to restrict the server's ability to access sensitive resources or perform certain actions. Use least privilege principles to minimize the potential impact of SSRF attacks.
Conclusion
Server-Side Request Forgery (SSRF) is a critical security vulnerability that can have serious consequences for web applications and servers. By understanding how SSRF attacks work and implementing proper security measures, developers and administrators can protect their systems from exploitation and unauthorized access. Techniques such as input validation, whitelisting, network segmentation, and access controls can help mitigate the risk of SSRF attacks and ensure the integrity and security of server-side applications.
Are you interested in learning more about web application security, server hardening, or best practices for secure development? Share your thoughts in the comments below and subscribe to our blog newsletter for updates on similar topics
Subscribe to my newsletter
Read articles from Cloud Tuned directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
