Understanding Insecure Direct Object References (IDOR)
 Cloud Tuned
Cloud Tuned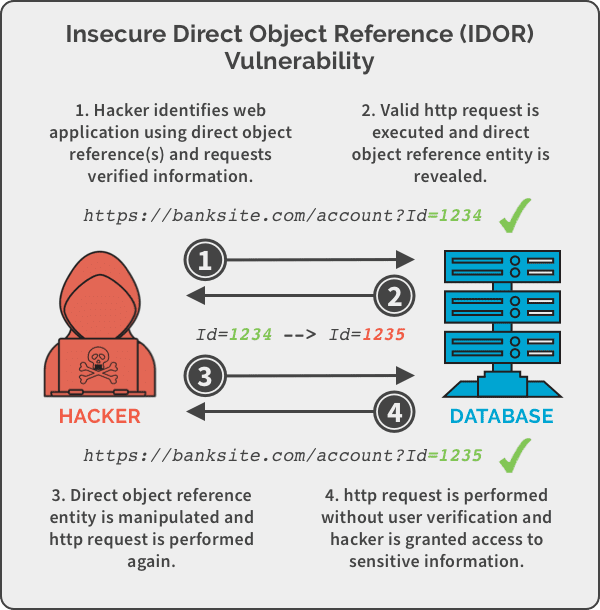
Understanding Insecure Direct Object References (IDOR)
Insecure Direct Object References (IDOR) is a common security vulnerability that occurs when an application exposes sensitive data or functionality by directly referencing internal objects or resources without proper authorization checks. This vulnerability can lead to unauthorized access to sensitive information, data manipulation, and other security breaches. In this article, we'll explore IDOR, understand how it works, and discuss strategies for preventing and mitigating this threat.
How IDOR Works
Direct Object References: The application uses direct references, such as database keys or filenames, to access and manipulate internal objects or resources.
Lack of Authorization Checks: The application fails to enforce proper authorization checks to verify whether the user has permission to access or modify the referenced object.
Exploitation: An attacker identifies a vulnerable endpoint or parameter that accepts user input or object references. By manipulating the input or parameters, the attacker can bypass authorization checks and access or modify sensitive data or resources.
Unauthorized Access: The attacker gains unauthorized access to sensitive information or resources, such as user data, financial records, or administrative functions, leading to potential data breaches or system compromise.
Preventing and Mitigating IDOR
Authorization Checks: Implement robust authorization checks throughout the application to ensure that users are only allowed to access or modify objects and resources that they are authorized to access.
Indirect Object References: Instead of using direct object references, use indirect references or unique identifiers that are not predictable or directly linked to internal objects. This makes it harder for attackers to guess or manipulate object references.
Access Controls: Enforce strict access controls and permissions to restrict users' access to sensitive data and functionality based on their roles and privileges. Use role-based access control (RBAC) or attribute-based access control (ABAC) to granularly control access to resources.
Input Validation: Implement thorough input validation and sanitization mechanisms to prevent attackers from injecting malicious input or manipulating object references through parameters, URLs, or forms.
Conclusion
Insecure Direct Object References (IDOR) is a serious security vulnerability that can have significant consequences for web applications and systems. By understanding how IDOR works and implementing proper security measures, developers can protect their applications from unauthorized access and data breaches. Techniques such as robust authorization checks, indirect object references, access controls, and input validation can help mitigate the risk of IDOR attacks and ensure the integrity and security of applications.
Are you interested in learning more about web application security, vulnerability mitigation, or best practices for secure development? Share your thoughts in the comments below and subscribe to our blog newsletter for updates on similar topics.
Subscribe to my newsletter
Read articles from Cloud Tuned directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
