Discover Proton Mail registration date with one weird trick…
 ValdikSS
ValdikSS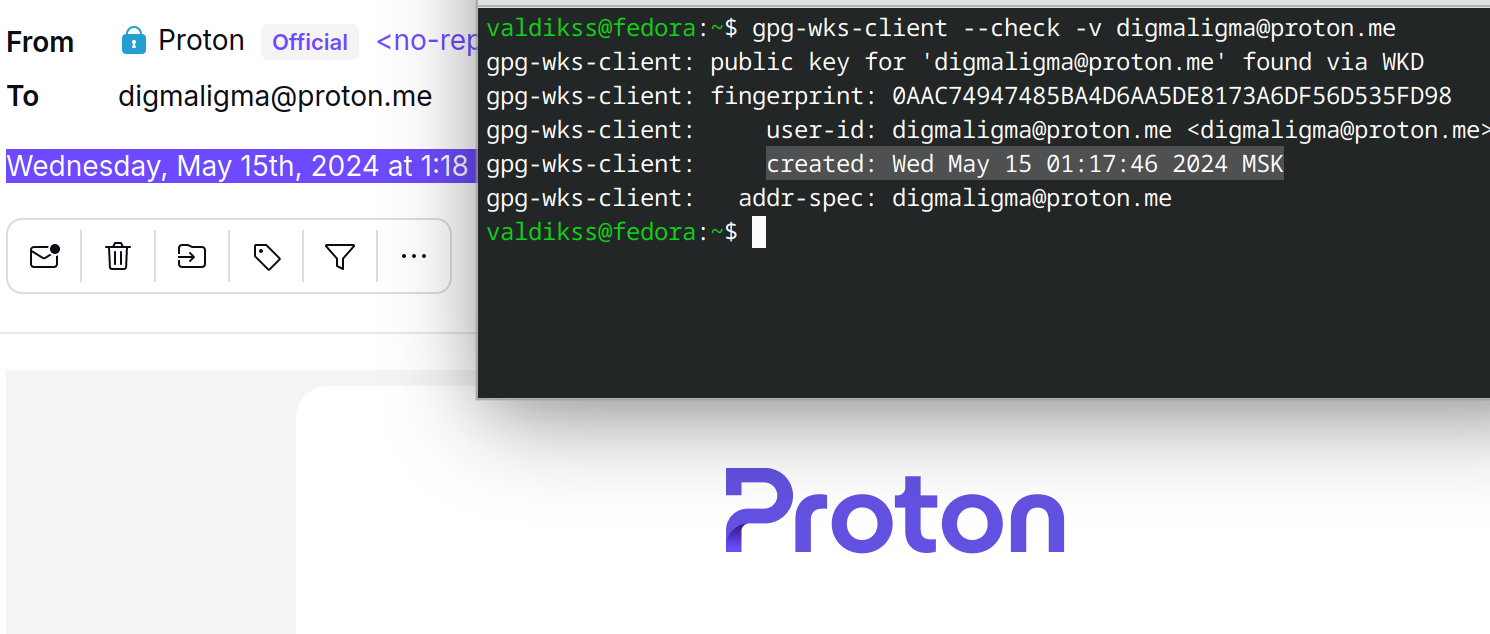
TL;DR: Proton Mail generates PGP key and publishes it upon account creation using Web Key Directory (WKD) standard. The key contains account creation timestamp, with second precision, which reflects the account creation date.
Proton, a privacy-oriented Swiss company providing different online services, is most known as an email provider. Proton Mail, created in 2014, was one of the first services to introduce end-to-end encryption for the messages sent between parties inside their service, and later provided support for Pretty Good Privacy (PGP), allowing it to be used for external emails en masse as well, without any convoluted configuration.
The service does all the setup for you:
The PGP key is generated automatically when the account is created, so others could encrypt messages for you
Your key is published with Web Key Discovery (WKD) standard, so others could discover your key automatically before writing to you
The keys of correspondents are automatically looked up upon adding them as To: or CC: when sending a new message
And all of this works nicely!
WKD
The Web Key Discovery (WKD) protocol is fairly simple: it allows to find the public PGP key by downloading it from your email domain name under a well-known HTTPS path /.well-known/openpgpkey/hu/, using z-base-32-encoded SHA1 hash of your email address before @ symbol as a filename.
It allows the email clients to discover the keys without using keyservers, and the contents are authenticated using HTTPS encryption and validated with a domain-bounded TLS certificate.
However, there's one minor detail: the PGP key created on account creation includes precise timestamp of its generation date, which could be used to get more information about your account than you'd wanted to disclose, even if you never used encrypted messaging.
Get the key
You need a fairly recent GnuPG client or gpg-wks-client utility from GnuPG package:
$ gpg-wks-client --check -v digmaligma@proton.me
gpg-wks-client: public key for 'digmaligma@proton.me' found via WKD
gpg-wks-client: fingerprint: 0AAC74947485BA4D6AA5DE8173A6DF56D535FD98
gpg-wks-client: user-id: digmaligma@proton.me <digmaligma@proton.me>
gpg-wks-client: created: Wed May 15 01:17:46 2024 MSK
gpg-wks-client: addr-spec: digmaligma@proton.me
gpg-wks-client: created: Wed May 15 01:17:46 2024 MSK
If you don't have gpg-wks-client, regular gnupg could be used instead. However, it automatically imports the key into your gnupg's keystore, which may be undesirable.
$ gpg --locate-external-keys digmaligma@proton.me
gpg: key 73A6DF56D535FD98: "digmaligma@proton.me <digmaligma@proton.me>" not changed
gpg: Total number processed: 1
gpg: unchanged: 1
pub ed25519 2024-05-14 [SC]
0AAC74947485BA4D6AA5DE8173A6DF56D535FD98
uid [ unknown] digmaligma@proton.me <digmaligma@proton.me>
sub cv25519 2024-05-14 [E]
The PGP key contain time in UTC, GnuPG uses your local time zone configured in the OS to display the information from it.
Solutions
The situation with PGP metadata is not unique to Proton, the same applies for your own generated keys in any email client or manually. However, before WKD the keys weren't available as freely in public, oftentimes the parties shared their keys in a form of file attachment in the first messages of the email conversation, and not all of them were uploaded to the keyservers.
Proton Mail does not allow to completely remove the encryption key, nor does it allow to control whether it's being published over WKD.
However, you can generate your own key and import it to Proton.
To hide the timestamp, we could use a fake date like 1 January 2020 00:00:00 to generate our key:
Set your local date and time to the desired value before running gpg
OR
use libfaketime to spoof it. Make sure to terminate gpg-agent first!
$ faketime -f '2020-01-01 00:00:0' gpg --full-generate-key
[…]
Please select what kind of key you want:
(1) RSA and RSA
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(9) ECC (sign and encrypt) *default*
(10) ECC (sign only)
(14) Existing key from card
Your selection? 9
Please select which elliptic curve you want:
(1) Curve 25519 *default*
(4) NIST P-384
(6) Brainpool P-256
Your selection? 1
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 0
Key does not expire at all
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: Digma
Email address: digmaligma@proton.me
Comment:
You selected this USER-ID:
"Digma <digmaligma@proton.me>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
[…]
public and secret key created and signed.
pub ed25519 2019-12-31 [SC]
F7D02E55CE5C0FE51973AC9D84760D5E63B24E54
uid Digma <digmaligma@proton.me>
sub cv25519 2019-12-31 [E]
# Export private key into file
$ gpg --armor --export-secret-keys Digma > key.asc
Now navigate to Settings → All settings → Encryption and keys → Email encryption keys, select "Import key" from the drop-down menu, and import your file.
Make sure to tag it as primary key, as only a single key is published over WKD.
$ gpg-wks-client --check -v digmaligma@proton.me
gpg-wks-client: public key for 'digmaligma@proton.me' found via WKD
gpg-wks-client: fingerprint: F7D02E55CE5C0FE51973AC9D84760D5E63B24E54
gpg-wks-client: user-id: Digma <digmaligma@proton.me>
gpg-wks-client: created: Wed Jan 1 00:00:00 2020 MSK
gpg-wks-client: addr-spec: digmaligma@proton.me
Please not to forget taking zone into consideration: the time is faked for your local time zone! MSK time zone (UTC+3) is used in this example, which means that the key metadata has '31 Dec 2019 21:00:00 UTC'.
Conclusion
This simple trick could be used to reckon more information from the Proton Mail account, which could be used as a bot or puppet accounts detection metric, along with other possibilities, such as government-wide traffic correlation of first access to Proton services to match it with PGP creation date.
Proton Mail does not allow to enumerate the accounts using WKD lookups though, generating random keys for non-existent addresses.
Up until very recently there was a convenient web service to lookup and show keys information, however it's been withdrawn due to lack of time for maintenance.
Like the method? Go ahead and replenish your collection of notes of OSINT :)
👉 Like to publish an article at https://iq.thc.org? Contact us at root@proton.thc.org.
Subscribe to my newsletter
Read articles from ValdikSS directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
