Building a Secure CI/CD Pipeline on Oracle Cloud with DevSecOps Tools
 Merlin Saha
Merlin SahaTable of contents
- Introduction
- Technologies Used:
- Step 1: Provision Infrastructure using Terraform
- Step 2: Configure Jenkins(Agent and Master) on OCI, automically with Ansible Playbook and Bash Script
- Step 3: Integrate OWASP Dependency-Check
- Step 4: Integrate Trivy for Container Image Scanning
- Step 5: Integrate SonarQube for Code Quality Analysis
- Step 6: Configure the CI/CD Pipeline
- Step 6: Deployment Choice 1, Oracle Cloud Virtual Machines
- Step 7: Deployment Choice 2, Kubernetes on Oracle Cloud Virtual Machines
- Step 8: Source code
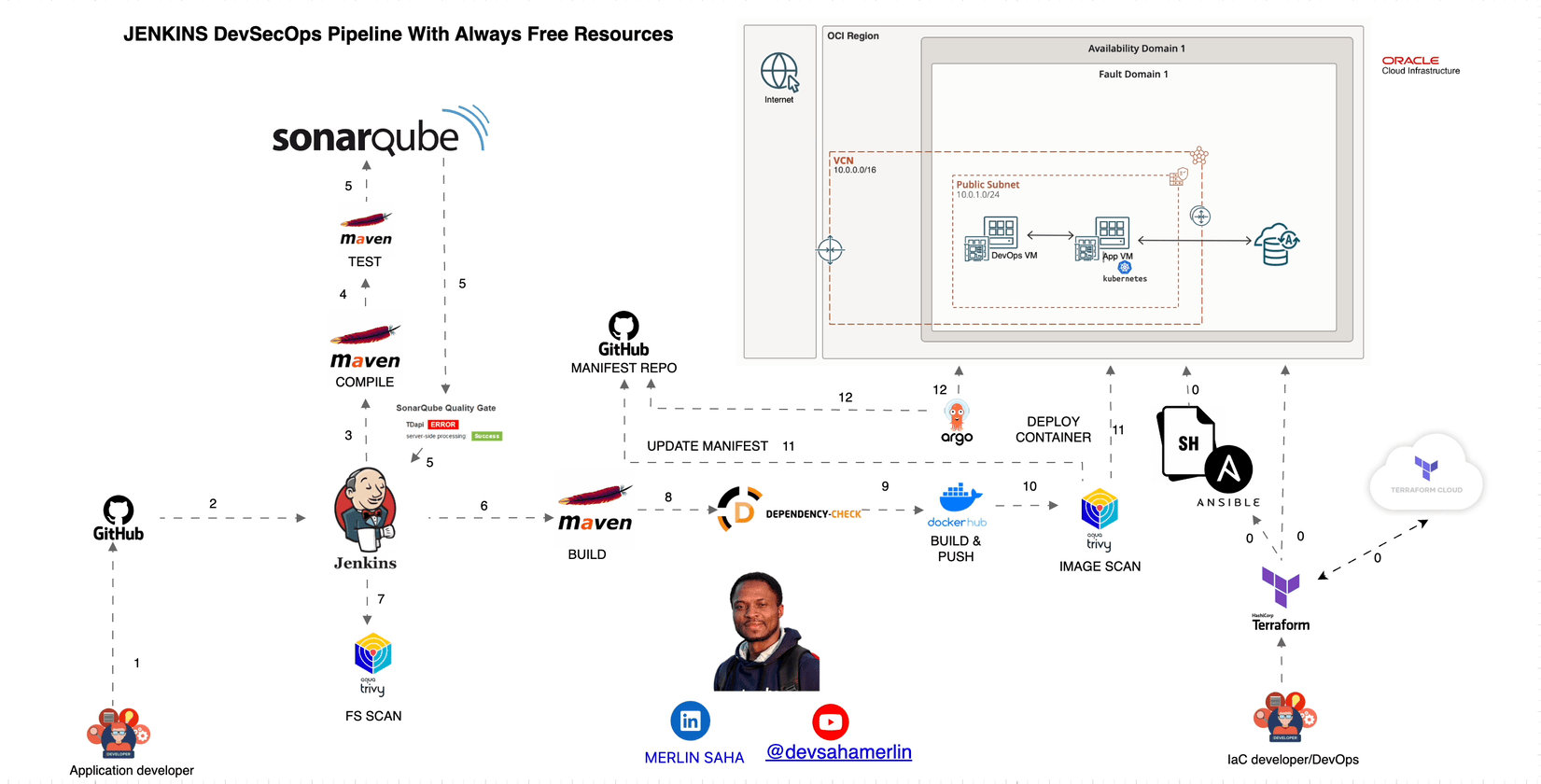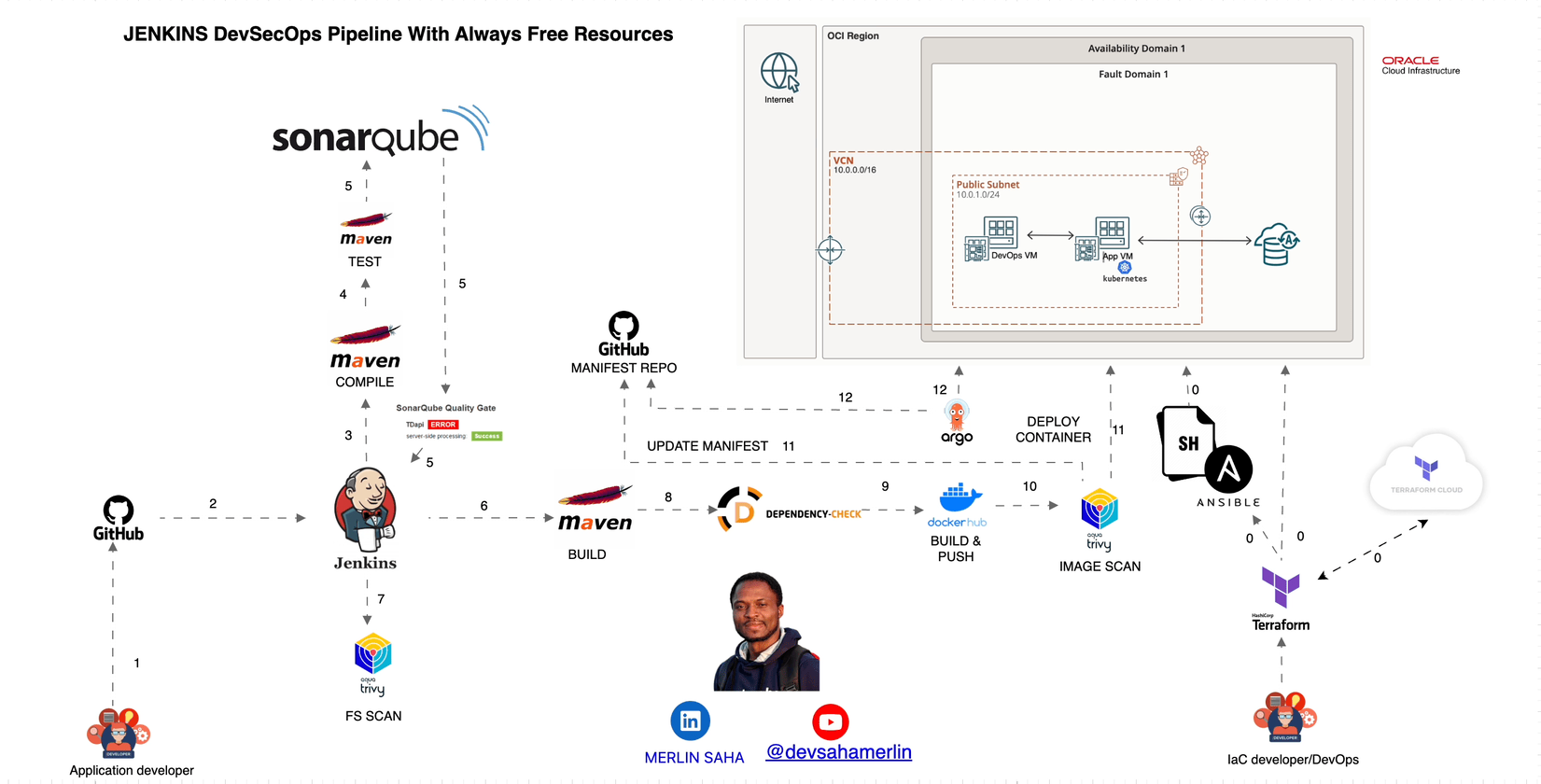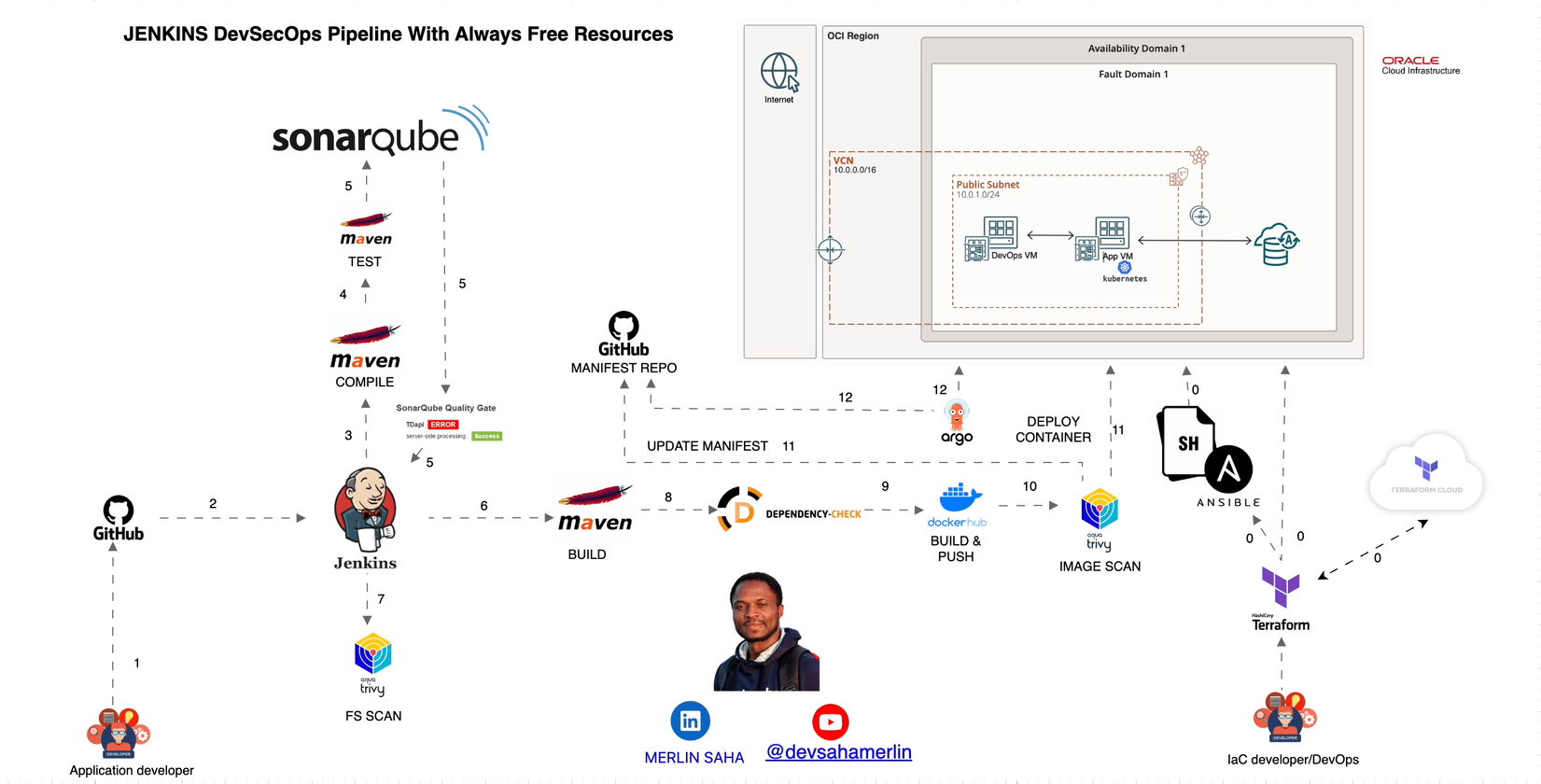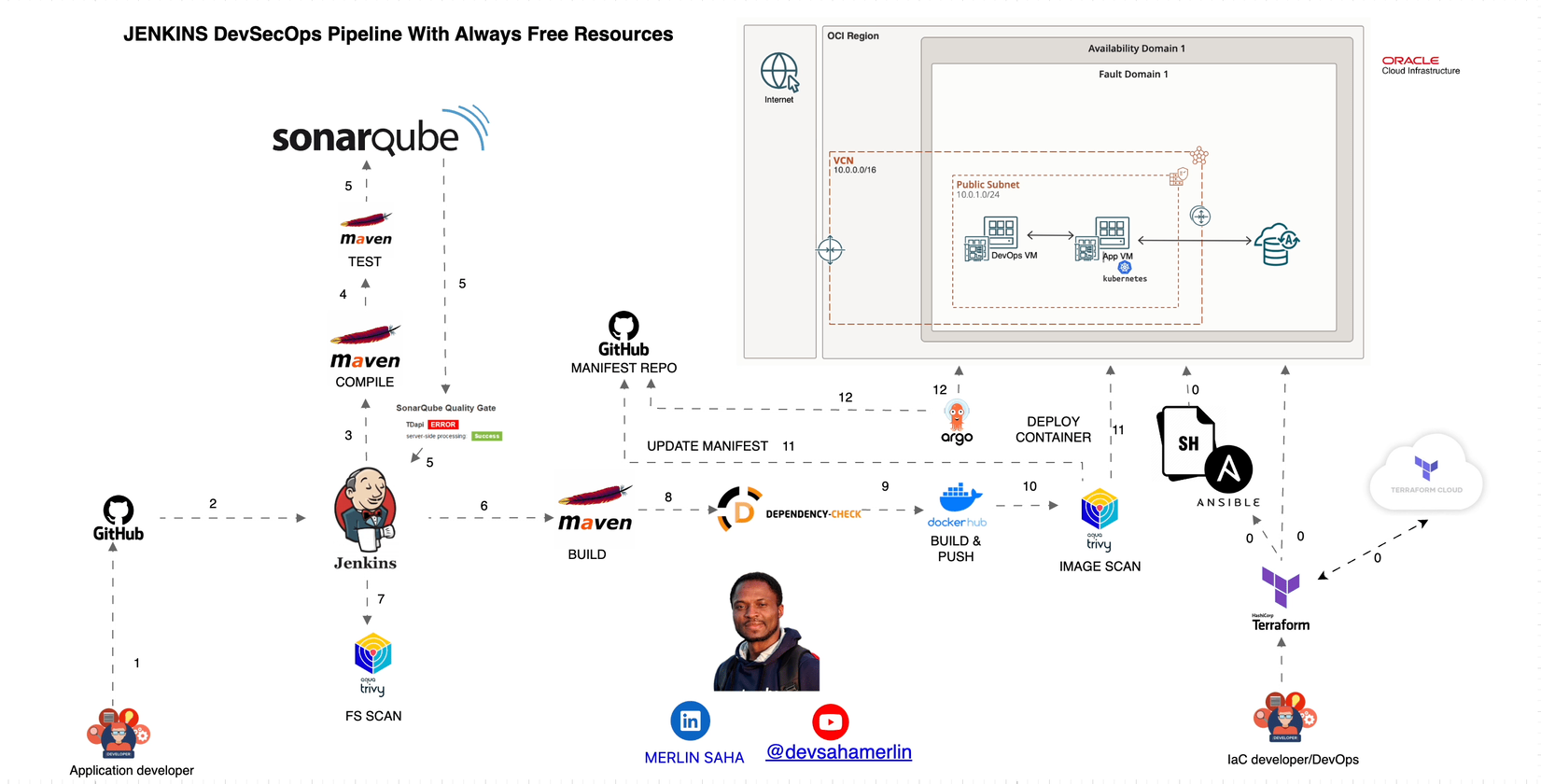
Automated Secure CI/CD Pipeline for Oracle Cloud Infrastructure with DevSecOps Practices (Jenkins, OWASP Dependency Check, Trivy, SonarQube, VCN, Compartment, Security Group, Maven, GitHub, Docker, Docker Hub, ArgoCD, Kubernetes) Using Terraform, Ansible, and Bash Scripts
Introduction
We'll walk through the tools to set up an automated secure CI/CD pipeline for Oracle Cloud Infrastructure (OCI) using popular DevSecOps tools and techniques. We'll explore two deployment choices: one on Oracle Cloud Virtual Machines and the other on Kubernetes installed on Oracle Cloud Virtual Machines. Additionally, we'll leverage Terraform, Ansible and Bash scripts to automate the provisioning and configuration of the required infrastructure and tools and Argo CD for Deployment.
Technologies Used:
Jenkins: An open-source automation server that facilitates Continuous Integration and Continuous Deployment (CI/CD) processes.
OWASP Dependency-Check: A utility that identifies project dependencies and checks for known, publicly disclosed vulnerabilities.
Trivy: A simple and comprehensive vulnerability scanner for containers and other artifacts, suitable for CI/CD pipelines.
SonarQube: A platform for continuous code quality analysis, providing insights into code quality, security vulnerabilities, and technical debt.
Oracle Autonomous Database: A fully managed, preconfigured database environment that is designed to provide high performance, high availability, and automated patching and upgrades.
Virtual Cloud Network (VCN): OCI's software-defined networking service that provides connectivity between resources in the cloud.
Compartment: A logical container in OCI for isolating and controlling access to resources.
Security Group: A virtual firewall that controls inbound and outbound traffic at the instance level in OCI.
Maven: A build automation tool used primarily for Java projects, managing dependencies and building and packaging applications.
GitHub: A web-based version control and collaboration platform for software development.
Docker: An open-source platform for building, shipping, and running applications in containers.
Docker Hub: A cloud-based registry service for storing, distributing, and managing Docker container images.
ArgoCD: A declarative continuous delivery tool for Kubernetes applications.
Kubernetes: An open-source container orchestration system for automating deployment, scaling, and management of containerized applications.
Terraform: An infrastructure-as-code (IaC) tool that allows you to provision and manage cloud resources using a declarative configuration language.
Ansible: An open-source IT automation tool that automates software provisioning, configuration management, and application deployment.
Bash Scripts: Shell scripts written in the Bash scripting language for automating various tasks.
Check PoC video here in French
Step 1: Provision Infrastructure using Terraform
Use Terraform to provision the required infrastructure resources in OCI, including:
Virtual Cloud Network (VCN)
Subnets
Compute instances (for Jenkins, SonarQube, etc.)
Oracle Autonomous Database instance
Security groups
Compartments
Etc.
Step 2: Configure Jenkins(Agent and Master) on OCI, automically with Ansible Playbook and Bash Script
Install Java and Jenkins on the designated Compute instance.
Intall Kubernetes
Install Trivy on the Jenkins Compute instance.
Install Docker
Configure Jenkins Master and Ajent.
Deploy ArgoCD
Step 3: Integrate OWASP Dependency-Check
Install OWASP Dependency-Check on the Jenkins Compute instance.
Create a Jenkins pipeline job and add a stage to run OWASP Dependency-Check.
Configure OWASP Dependency-Check to scan your application's dependencies for known vulnerabilities.
Step 4: Integrate Trivy for Container Image Scanning
Add a stage in your Jenkins pipeline to scan the built container image using Trivy.
Configure Trivy to scan for vulnerabilities in the container image and its dependencies.
Step 5: Integrate SonarQube for Code Quality Analysis
Use Terraform to provision a SonarQube server on OCI.
Add a stage in your Jenkins pipeline to run SonarQube analysis on your code.
Configure SonarQube to analyze your code for bugs, code smells, and security vulnerabilities.
Step 6: Configure the CI/CD Pipeline
Define the stages in your Jenkins pipeline:
Checkout code from GitHub
Build the application using Maven
Run OWASP Dependency-Check
Build and scan the container image with Trivy
Run SonarQube analysis
Include a stage for building and pushing the container image to Docker Hub.
Add a stage in the pipeline to trigger ArgoCD deployment after successful pipeline execution.
Etc.
Configure Jenkins to trigger the pipeline automatically on code commits or manually as needed.
Step 6: Deployment Choice 1, Oracle Cloud Virtual Machines
- Deploy the application on Oracle Cloud Virtual Machines
Step 7: Deployment Choice 2, Kubernetes on Oracle Cloud Virtual Machines
- Configure ArgoCD to automatically deploy your application to the Kubernetes cluster based on the pipeline output.
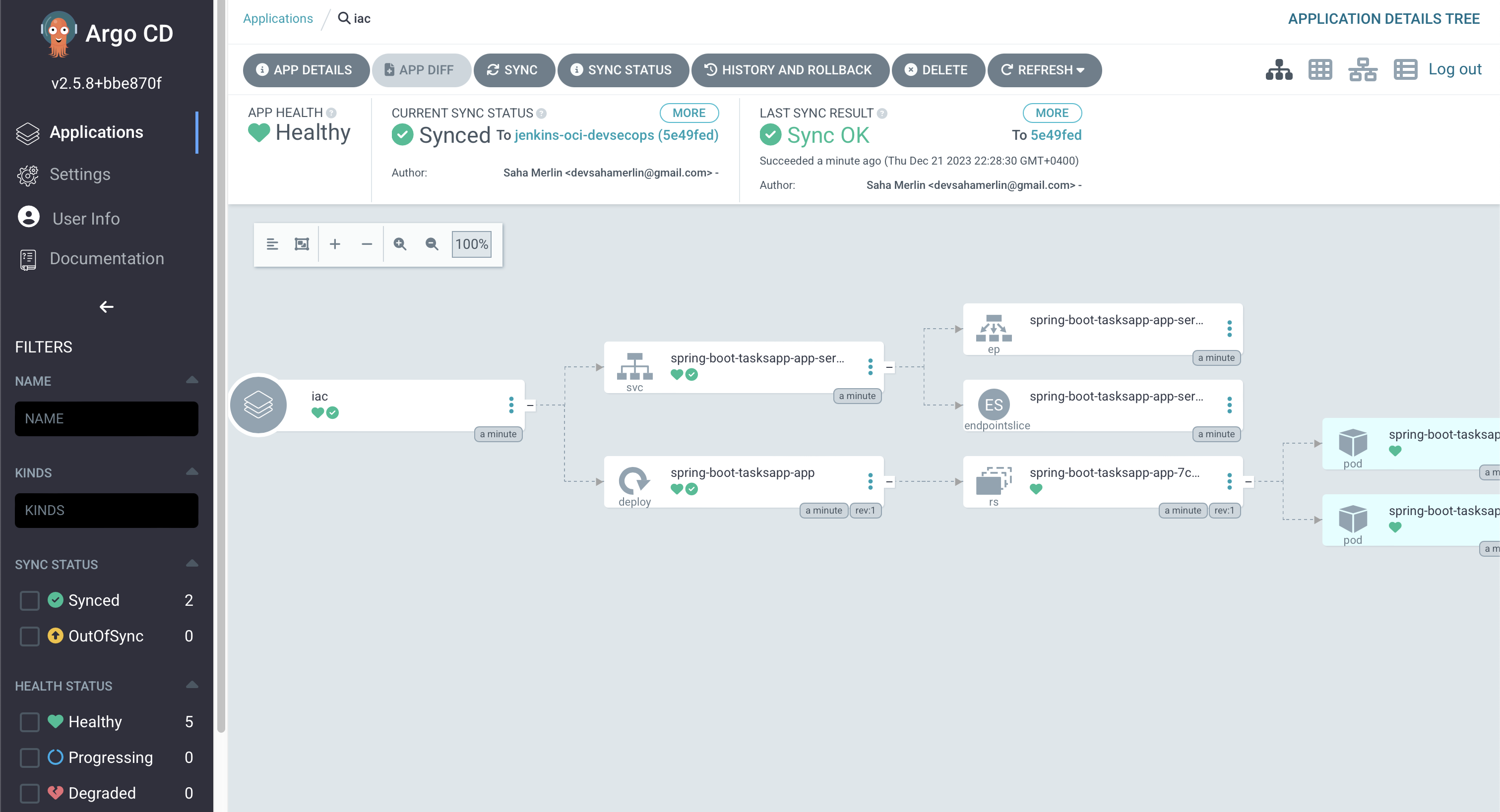
Contratulations to have read till here !
Step 8: Source code
Source code here with a README file: https://github.com/devsahamerlin/iac-spring-boot-atp-jenkins-oci-devsecops
Video Link here in French: https://www.youtube.com/watch?v=mvBNh6scVHk
By following steps in video you will leveraging tools like Terraform, Ansible, and Bash scripts, to automate the provisioning and configuration of an end-to-end secure CI/CD pipeline for Oracle Cloud Infrastructure. This pipeline incorporates DevSecOps practices using popular tools like Jenkins, OWASP Dependency Check, Trivy, and SonarQube, ensuring that security is addressed throughout the entire software development lifecycle.
The deployment choices provided cater to different scenarios: the first choice deploys the application on Oracle Cloud Virtual Machines, while the second choice leverages Kubernetes for container orchestration and deployment on Oracle Cloud Virtual Machines. In both choices, all required resources, including Oracle Autonomous Database, are provisioned using the provided Terraform code.
Subscribe to my newsletter
Read articles from Merlin Saha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Merlin Saha
Merlin Saha
Specialising in Cloud Architecture and Application Modernisation, Saha Merlin is a Cloud Solutions Architect and DevSecOps Specialist who helps organizations build scalable, secure, and sustainable infrastructure. With six years of specialized experience in highly regulated industries—split equally between insurance and finance—he brings deep understanding of compliance requirements and industry-specific challenges to his technical implementations. His expertise spans various deployment models including Container-as-a-Service (CaaS), Infrastructure-as-a-Service (IaaS), and serverless platforms that drive business outcomes through technical excellence. He strategically implements open source technologies, particularly when SaaS solutions fall short or when greater control and autonomy are essential to meeting business requirements. Saha integrates DevSecOps practices, Green IT principles to minimize environmental impact, and Generative AI to accelerate innovation. With a solid foundation in Software Engineering and nine years of diverse industry experience, he designs cloud-native solutions that align with both industry standards and emerging technological trends.