Frida & Objection setup
 Prasnjit Kumar sharma
Prasnjit Kumar sharma
To install Frida and Objection we need to run the command in Super user mode.
$pip3 install frida-tool
$pip3 install objection
if anything went wrong please update the package and upgrade it in superuser mode.
To run the Frida server After starting emulator
$ adb shell "/data/local/tmp/frida-server &"
When we run the above mentioned
Run the Rootbeer application. This application detect the device is rooted or not and we are going to bypass the root detection of this application. Here we will be using objection tool
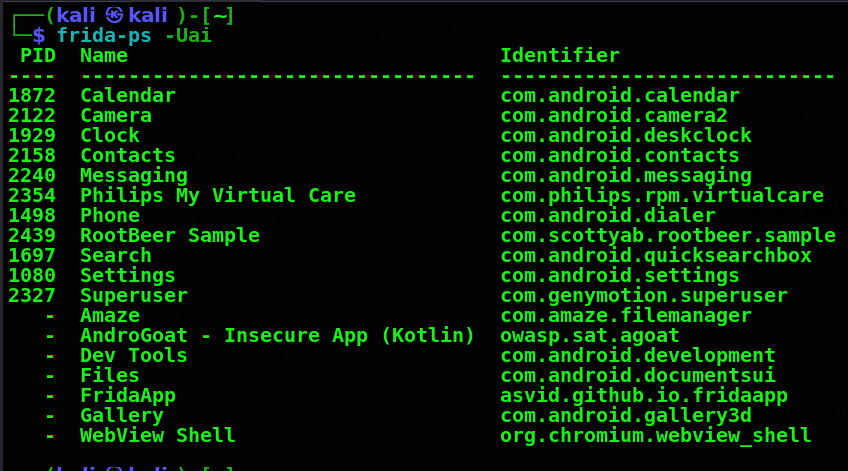
To check the services running in frida
frida-ps -Uai
To run the application dyanamically use Objetion and command below
$objection --gadget asvid.github.io.fridaapp explore
Lets check all the class method for main activity
#android hooking list class_methods com.scottyab.rootbeer.sample.MainActivity
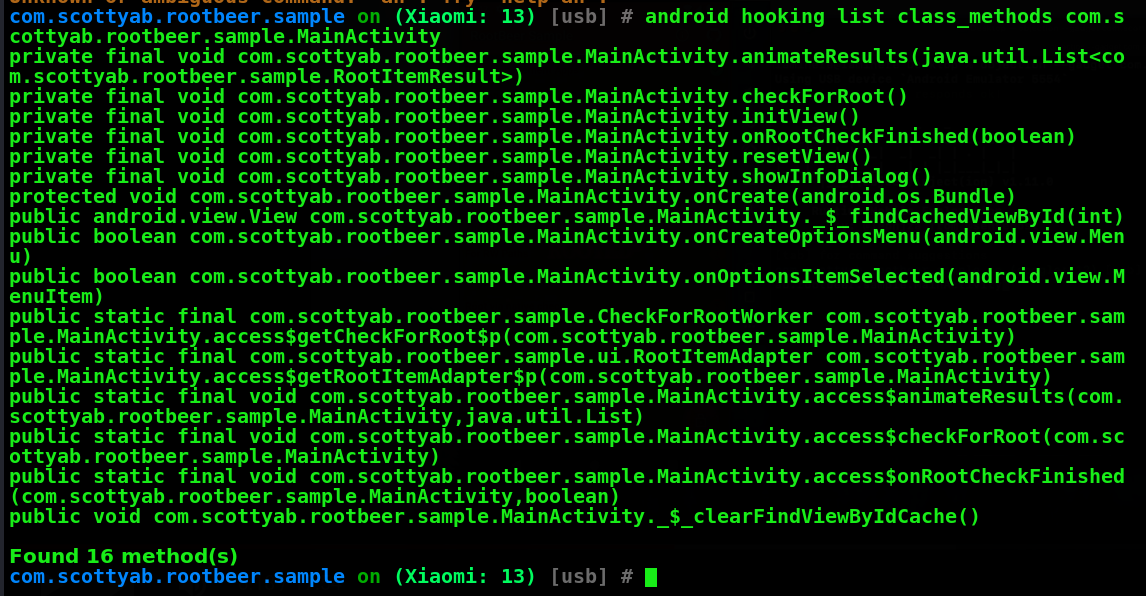
we can see we have 16 method in main class.
#android hooking watch class_method "com.scottyab.rootbeer.RootBeer.checkForBinar y" --dump-return
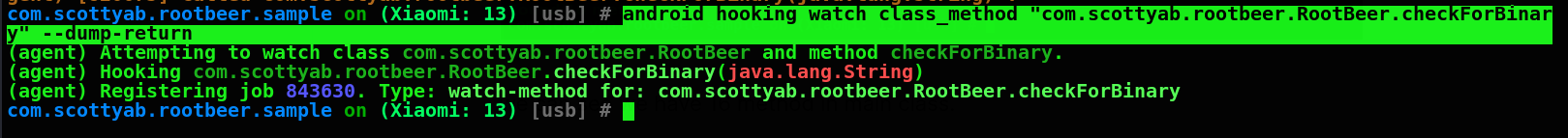
Refresh Rootbeer application and check for
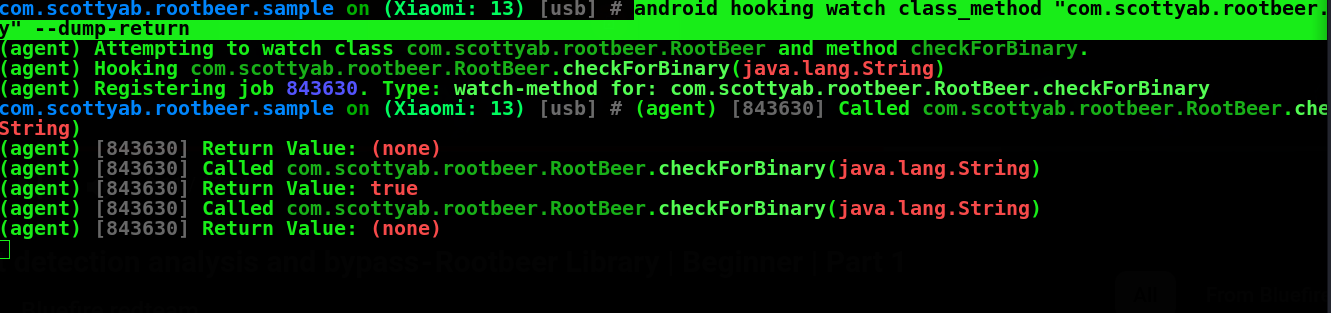
Now we need to set the value of checkForBinary value to False so that when application is checking for root it will return to False and we will be bypassing the root
#android hooking set retu rn_value "com.scottyab.rootbeer.RootBeer.checkForBinary" false
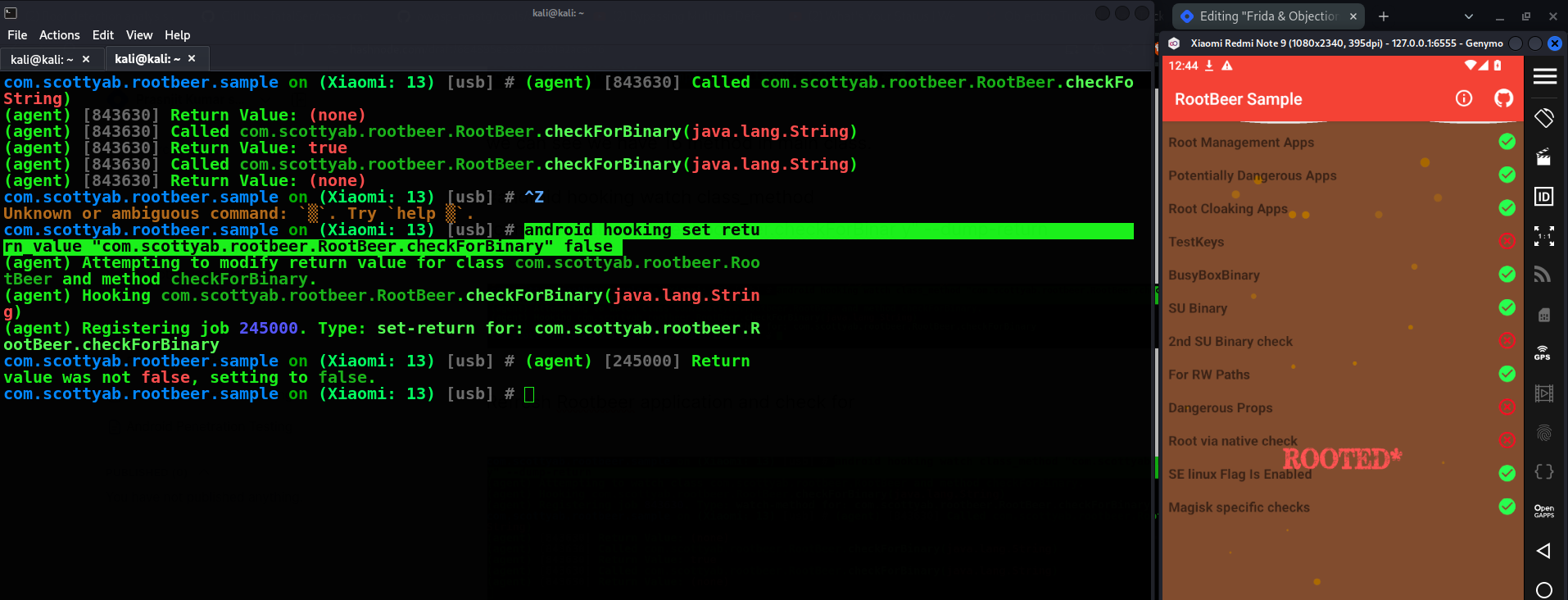
In the POC we can see Value of su binary is set to be false and we have sucessfully bypass root detection.
For SSL pining Bypass we just need to run
#android sslpinning disable
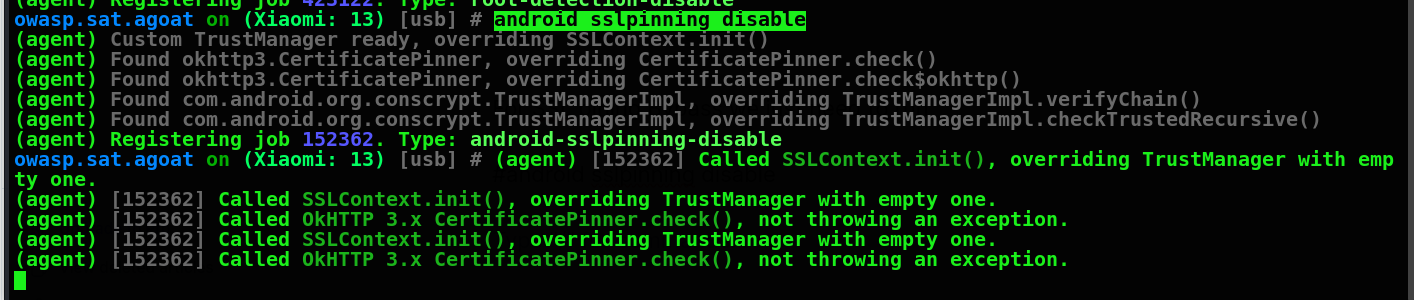
Easy method of bypassing root detection
Go to the given URL and copy the line of code
https://codeshare.frida.re/@dzonerzy/fridantiroot/
Create a text file and copy then code form the URL and Paste in the txt file and save it.
Open the Terminal and run the given command.
$frida -l New\ Empty\ File -f owasp.sat.agoat -U
Note:- Frida is tool
-l, -f, -U is option selected
New\ Empty\ File is file where we save the scripts
owasp.sat.agoat : is binary of our application
Subscribe to my newsletter
Read articles from Prasnjit Kumar sharma directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Prasnjit Kumar sharma
Prasnjit Kumar sharma
I am Prasnjit Kumar Sharma from Madhubani Bihar. I have completed my B. Tech IT from Sri Ramakrishna engineering college and I have done specialization on Threat handling and risk analysis. Currently, i am working with the L&T Technology on the connected security framework project, and recently I have completed my CISSP(Certified Information System Security Professional) certification from simplilearn. Along with this, now I am a candidate of (ISC)2.