Proxy & It's Types
 Dhaval Bavda
Dhaval BavdaProxy
It is a server or a computer hardware that is placed in between the client and the application which acts a intermediary source for the communication.
It servers various functions and come in different types. It is configured to perform specific tasks.
Two Types of Proxy :-
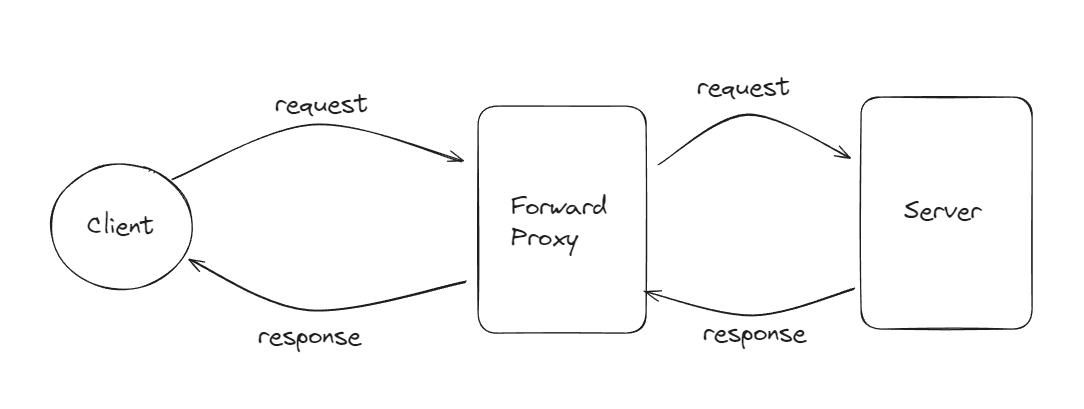
Forward Proxy
It is a proxy server that is used on the client side. When a client sends a request, it first goes through this proxy server. The proxy server then forwards the request to the actual server. Once the actual server processes the request and sends back a response, the proxy server receives this response and passes it back to the client. This method of communication ensures that the client's identity remains hidden from the actual server because the actual server only interacts with the proxy server.
This adds a layer of privacy and security for the client, as the actual server cannot directly see or track the client's information. Additionally, forward proxies can be used to bypass geo-restrictions, filter content, and cache data to improve performance. By using a forward proxy, clients can access resources without directly exposing their IP addresses to the servers they are communicating with.
Advantages:
Enhanced Privacy: A forward proxy hides the user's IP address, making it harder for websites and online services to track the client's online activities.
Anonymity: By masking the IP address, users can browse the internet more anonymously, protecting their identity and personal information.
Access Control: It can be used to prevent access to certain online websites from the internet.
Access to Restricted Content: Users can access content that is restricted in their geographical region by routing their connection through a proxy server located in a different region.
Bandwidth Savings: Caches frequently accessed web content, leading to faster load times and reduced bandwidth usage.
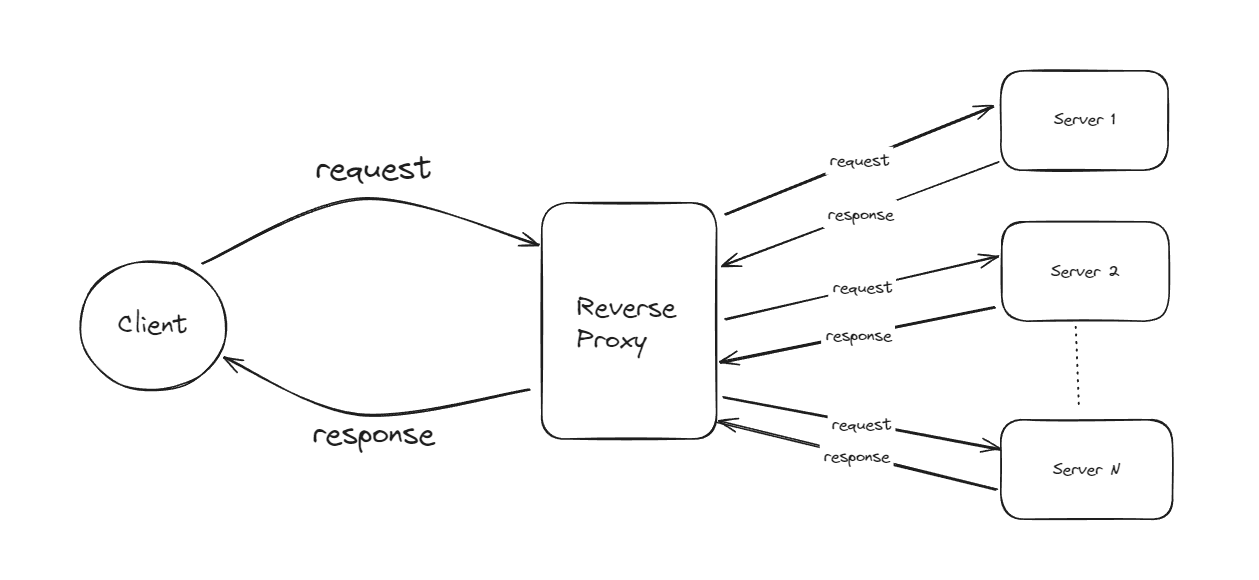
Reverse Proxy
A reverse proxy is a server-side proxy that acts as an intermediary between the client and the actual server. When a client sends a request, the reverse proxy receives it first. The reverse proxy then forwards this request to the actual server. Once the actual server processes the request and generates a response, it sends this response back to the reverse proxy. The reverse proxy then delivers the response to the client.
This process ensures that the client never directly interacts with the actual server. Instead, all communication goes through the reverse proxy, which keeps the server's identity hidden from the client. This setup not only enhances security by masking the server's details but also provides additional benefits such as load balancing, improved performance through caching, and the ability to handle SSL termination. By using a reverse proxy, organizations can better manage traffic, protect their servers from direct exposure, and ensure a more secure and efficient communication flow between clients and servers.
Advantages:
Enhanced Security: By hiding the IP addresses of the backend servers, a reverse proxy makes it harder for attackers to target specific servers directly.
Load Balancing: A reverse proxy can spread incoming traffic across multiple servers, making sure no single server gets overloaded. This boosts the overall performance and reliability of the service.
High Availability: By distributing traffic and checking server health, reverse proxies can ensure high availability. If one server fails, the proxy can send traffic to other working servers.
SSL Termination: Handles SSL encryption and decryption, offloading this resource-intensive process from backend servers.
Content Caching: Reverse proxies can store frequently accessed content, reducing the load on backend servers and speeding up response times for users. This is especially useful for static content like images, CSS files, and JavaScript.
Logging: Reverse proxies can provide a centralized point for logging and monitoring all incoming and outgoing traffic.
Scalability: Reverse proxies can help in scaling applications by easily adding or removing backend servers without affecting the client experience.
Conclusion
Proxies are super handy tools in networking and cybersecurity. They play key roles in boosting privacy, security, performance, and access control. Knowing the different types of proxies and what they do can help users and organizations use them effectively to meet their specific needs.
Subscribe to my newsletter
Read articles from Dhaval Bavda directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
