Chaos Engineering: A Comparative Review and Analysis of Tools
 Rakesh Vardan
Rakesh Vardan
Introduction:
Chaos Engineering has emerged as a critical discipline in the world of software development, helping teams build more resilient and robust systems. Several tools have been developed to facilitate chaos engineering practices. This article provides a comparative analysis of some of the most popular chaos engineering tools available today.
1. Chaos Monkey:
Chaos Monkey is a resiliency tool developed and used by Netflix. It follows the principles of Chaos Engineering by randomly terminating instances in production to ensure that engineers implement their services to be resilient to instance failures.
Chaos Monkey is designed to work on the Amazon Web Services (AWS) platform. It operates by randomly selecting a target from a specified group and terminating it. This random termination simulates potential real-world issues and allows developers to proactively identify and fix weaknesses in their systems. Chaos Monkey is fully integrated with Spinnaker, the continuous delivery platform that Netflix uses. It should work with any backend that Spinnaker supports (AWS, Google Compute Engine, Azure, Kubernetes, Cloud Foundry). It has been tested with AWS, GCE, and Kubernetes.
The primary advantage of Chaos Monkey is its maturity and wide adoption. Being one of the first tools in the field of Chaos Engineering, it has been thoroughly tested and refined. It's backed by Netflix, which gives it a strong support base.
However, Chaos Monkey's scope is primarily limited to AWS. While it can be a powerful tool for teams operating in an AWS environment, those using other platforms may find its functionality limited. Additionally, compared to some other Chaos Engineering tools, it may not offer as wide a range of chaos experiments.
2. Gremlin:
Gremlin is a Chaos Engineering platform developed by Gremlin Inc. It provides a fully hosted service that allows engineers to safely, securely, and easily simulate chaos to test how their systems handle failure scenarios.
Gremlin offers a wide range of attack vectors, including resource attacks (like CPU, memory, disk, and IO), state attacks (like shutdown and time travel), and network attacks (like latency, packet loss, and DNS). This makes it a comprehensive tool for a variety of chaos experiments.
One of the key advantages of Gremlin is its user-friendly interface, which makes it easy to design and run chaos experiments. It also provides strong support and detailed documentation, making it accessible for both beginners and experienced practitioners of Chaos Engineering.
However, Gremlin is not open-source, and its pricing can be a barrier for small teams or individual users. It's also a more complex tool, which may be more than some users need for simple chaos experiments.
3. Chaos Toolkit:
Chaos Toolkit is an open-source Chaos Engineering tool developed by ChaosIQ (now Reliably). It's designed to be a simple, easy-to-use, and extendable tool for running chaos experiments.
One of the key features of the Chaos Toolkit is its extendability. It provides a simple core that you can extend with plugins to support a wide range of platforms and technologies. This makes it a versatile tool that can be adapted to many different environments.
Chaos Toolkit also emphasizes simplicity and ease of use. It uses a declarative JSON or YAML format for defining chaos experiments, making it easy to understand and control what your experiments will do.
However, the Chaos Toolkit is less mature compared to some other Chaos Engineering tools, and it has a limited set of built-in attacks. It's also a more low-level tool, which means it may require more setup and configuration compared to a fully hosted service like Gremlin.
4. Litmus:
Litmus is an open-source Chaos Engineering tool developed by MayaData and the open-source community. It's a Kubernetes-native tool, meaning it's designed specifically to run chaos experiments in Kubernetes environments.
One of the key features of Litmus is its extensive chaos experiment library. It provides a wide range of pre-defined chaos experiments that you can use to test your Kubernetes applications, including pod failures, node failures, network latency, and more.
Litmus also emphasizes observability and SRE principles. It provides detailed metrics and logs for your chaos experiments, making it easy to understand the impact of the chaos and identify any issues.
However, because Litmus is Kubernetes-native, it's limited to Kubernetes environments. If you're not using Kubernetes, you may find its functionality limited.
5. PowerfulSeal:
PowerfulSeal is an open-source Chaos Engineering tool developed by Bloomberg. It's designed to inject failure into your Kubernetes clusters, helping you detect problems as early as possible.
One of the key features of PowerfulSeal is its robustness. It provides a wide range of chaos experiments, including killing pods, draining nodes, and introducing network latency. It also supports both automated and interactive modes, giving you flexibility in how you run your chaos experiments.
PowerfulSeal also emphasizes observability (with Prometheus or Datadog). It provides detailed logs and metrics for your chaos experiments, making it easy to understand the impact of the chaos and identify any issues.
However, PowerfulSeal is less user-friendly compared to some other Chaos Engineering tools. It requires more setup and configuration, and its command-line interface may be intimidating for beginners. It's also limited to Kubernetes environments.
6. Chaos Mesh:
Chaos Mesh is an open-source Chaos Engineering platform developed by PingCAP. It's designed to orchestrate chaos experiments in Kubernetes environments.
One of the key features of Chaos Mesh is its comprehensive range of fault types. It supports a wide variety of chaos experiments, including pod failures, network failures, I/O failures, and even JVM application failures. This makes it a versatile tool for testing the resilience of your Kubernetes applications.
Chaos Mesh also emphasizes ease of use. It provides a user-friendly dashboard for managing and monitoring your chaos experiments, making it accessible for both beginners and experienced practitioners of Chaos Engineering.
However, like Litmus and PowerfulSeal, Chaos Mesh is Kubernetes-native and is therefore limited to Kubernetes environments.
7. Pumba:
Pumba is a chaos testing and network emulation tool for Docker, developed by Alexei Ledenev. It's designed to introduce chaos and network latency to Docker containers to test their resilience and discover faults.
One of the key features of Pumba is its simplicity and lightweight nature. It operates directly on running Docker containers, making it easy to integrate into any Docker-based environment. It supports a variety of chaos experiments, including stopping, killing, and removing Docker containers, as well as introducing network latency, packet loss, and rate control.
However, Pumba is less mature compared to some other Chaos Engineering tools, and its scope is primarily limited to Docker environments. It's also a more low-level tool, which means it may require more setup and configuration compared to a fully hosted service.
8. ToxiProxy:
ToxiProxy is a framework for testing network conditions, developed by Shopify. It's designed to simulate different network conditions and failures, allowing you to test how your application handles them.
One of the key features of ToxiProxy is its focus on network conditions. It supports a variety of network failures, including latency, timeouts, and packet loss. This makes it a valuable tool for testing the resilience of your application to network issues.
ToxiProxy operates as a TCP proxy, introducing the specified network conditions between your application and any services it communicates with over the network. This makes it a versatile tool that can be used with any application that communicates over TCP.
However, ToxiProxy's scope is primarily limited to network conditions. If you need to test other types of failures, such as resource exhaustion or system failures, you may need to use it in conjunction with other Chaos Engineering tools.
Below are the high-level decision diagram & comparative table for all the discussed tools for implementing Chaos Engineering.
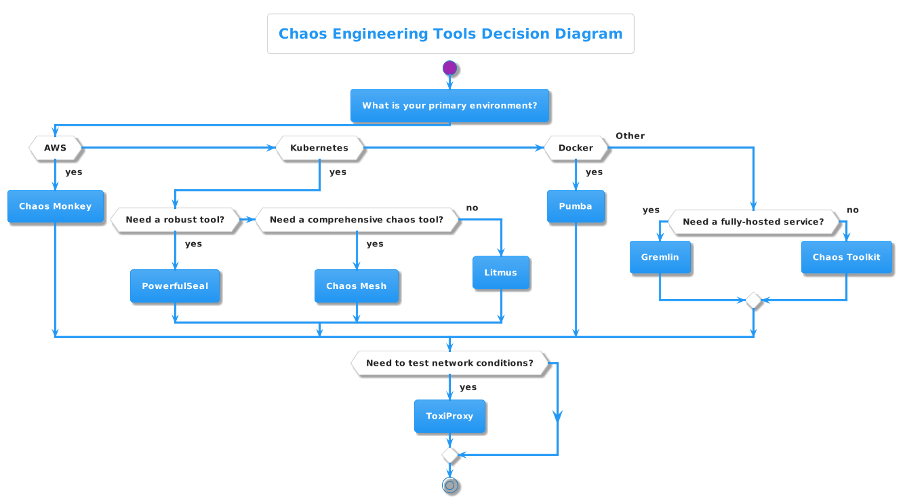
| Tool | Developed By | Key Features | Limitations | Idea For |
| Chaos Monkey | Netflix | Mature, wide adoption, integrated with Spinnaker, AWS-focused | Limited to AWS, less range of chaos experiments | AWS environments |
| Gremlin | Gremlin Inc. | User-friendly interface, a wide range of attack vectors, strong support and detailed documentation | Not open-source, pricing can be a barrier for small teams | Both beginners and experienced practitioners |
| Chaos Toolkit | ChaosIQ (now Reliably) | Open-source, extendable with plugins, simple core, easy to use | Less mature, limited set of built-in attacks, requires more setup and configuration | Users who need a simple, extendable tool |
| Litmus | MayaData and the open-source community | Kubernetes-native, extensive chaos experiment library, strong observability | Limited to Kubernetes environments | Kubernetes environments |
| PowerfulSeal | Bloomberg | Robust, wide range of chaos experiments, supports automated and interactive modes | Less user-friendly, requires more setup and configuration, limited to Kubernetes environments | Kubernetes environments |
| Chaos Mesh | PingCAP | Kubernetes-native, comprehensive range of fault types, user-friendly dashboard | Limited to Kubernetes environments | Kubernetes environments |
| Pumba | Alexei Ledenev | Simple, lightweight, operates directly on Docker containers | Less mature, limited to Docker environments | Docker environments |
| ToxiProxy | Shopify | Focus on network conditions, operates as a TCP proxy | Primarily limited to network conditions | Applications that communicate over TCP |
Conclusion:
Each of these tools has its strengths and weaknesses, and the best one for your team depends on your specific needs and environment. By understanding the capabilities of each tool, you can make an informed decision and embrace chaos to build more resilient systems.
Originally published at Wearecommunity-india-devtestsecops-community
Subscribe to my newsletter
Read articles from Rakesh Vardan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rakesh Vardan
Rakesh Vardan
I am a Software Development Engineer in Test (SDET) specializing in CI/CD processes, with a strong background in UI and API test automation. My expertise lies in designing robust testing frameworks that integrate seamlessly with CI/CD workflows, guaranteeing software quality and reliability.