Road to the RHCSA: Week 5
 Darnell W.
Darnell W.
Closing in on 2 weeks before my RHCSA preliminary exam, I am seeking to gain further traction in gaining a high understanding of the basics of Linux administration.
Last week, I focused on performing service management by understanding service units, managing service states with systemctl , perform package management by installing, updating, and removing software packages using package managers like yum and dnf , perform cron jobs to schedule system tasks, and network management.
This week, I will go further into NIC configuration, continue with network management with a focus on firewalls, performing root password recovery, finding files on a system, look into how SELinux works and its security benefits, and learn about storage management with LVM.
Monday: Network and Interface (NIC) Configuration
Today, my area of focus was mastering network and interface configuration. Proper network configuration is essential for ensuring connectivity, managing network services, and optimizing performance in a Linux environment. Key aspects of network management include setting up and configuring network interfaces, understanding IP addressing, and managing routing. Familiarity with configuration files such as /etc/sysconfig/network-scripts/ifcfg-* for Red Hat-based systems is vital, as these files define network parameters for each interface.
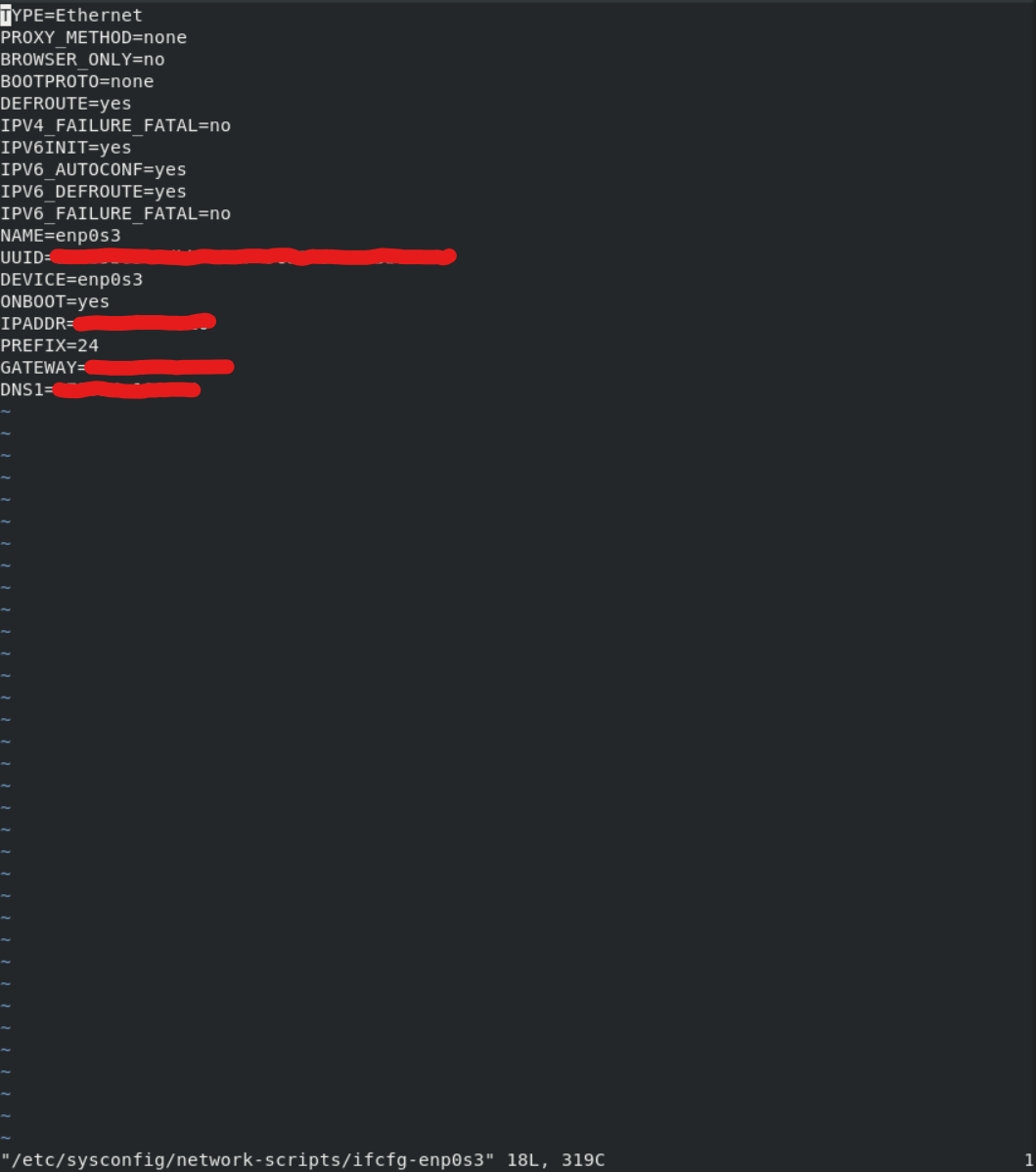
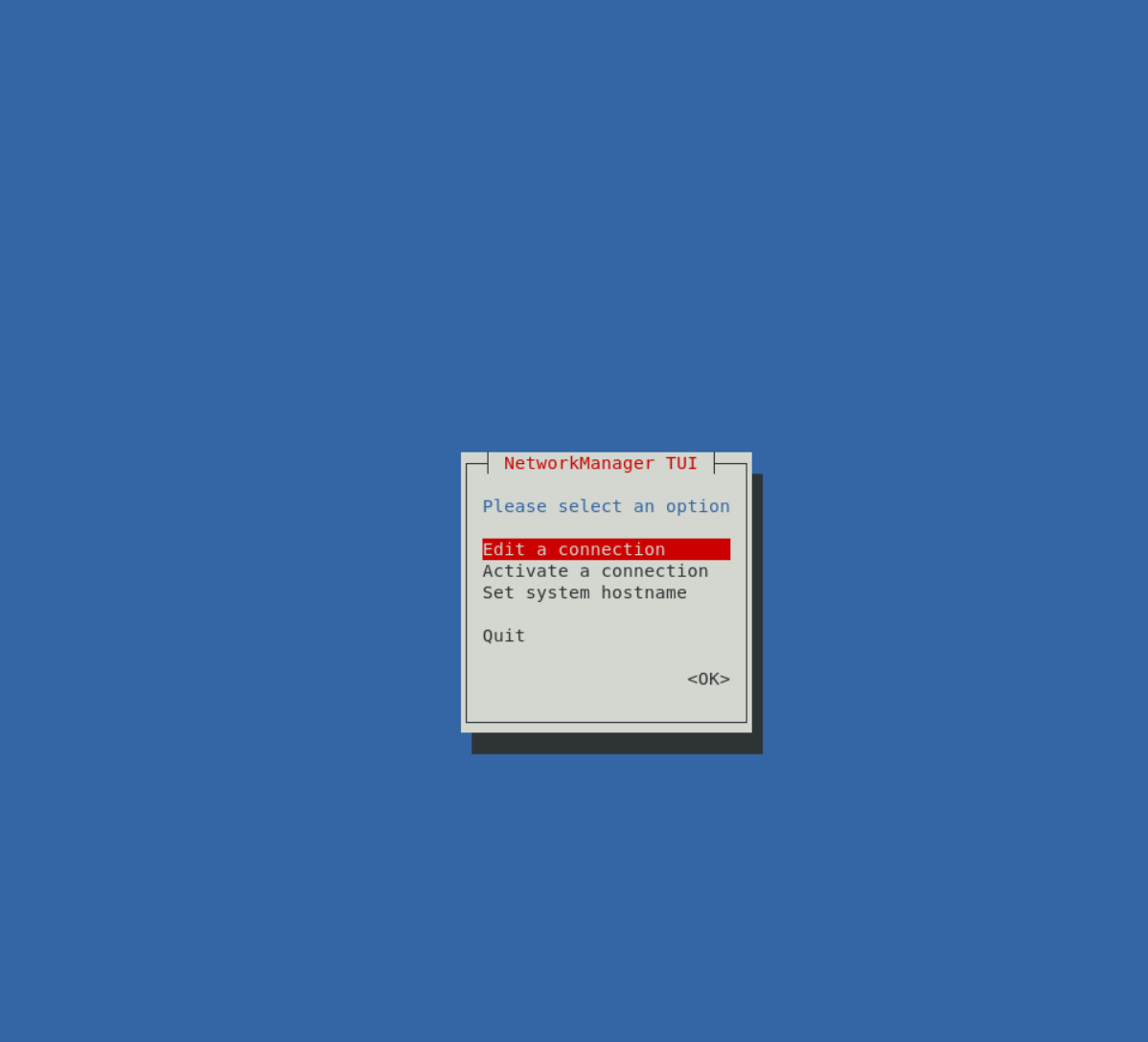
Using commands like nmcli and nmtui to manage NetworkManager, as well as traditional tools like ip and ifconfig, allows me to efficiently configure and troubleshoot network settings. For the exam, I will more than likely lean on nmtui due to the user interface.
In addition to basic interface configuration, understanding advanced topics like bonding, bridging, and VLANs is also essential. Bonding allows for the aggregation of multiple network interfaces to increase throughput and provide redundancy. Bridging enables the creation of virtual networks within a single host, which is particularly useful for virtualization scenarios. Configuring VLANs helps in segmenting network traffic for better management and security. Mastery of these concepts and tools not only prepares me for the RHCSA exam but also equips me with practical skills to manage and optimize network configurations in real-world Linux environments. Ensuring robust and efficient network setups is key to maintaining seamless connectivity and performance across the infrastructure.
Tuesday: Firewalls
Today, I gained understanding of how firewall management is proving to be a crucial part of my study journey. Firewalls are essential for securing Linux systems by controlling the flow of network traffic and protecting against unauthorized access and potential threats. The primary tool for firewall management in Red Hat Linux is firewalld, which provides a dynamic interface to configure network filtering rules.
Learning to use firewalld involves understanding its zone-based structure, where each zone defines a set of rules that govern the inbound and outbound traffic for network interfaces. By mastering commands like firewall-cmd to add, modify, and remove rules, I can have confidence that my systems are both secure and compliant with organizational policies.
In addition to firewalld, gaining proficiency with iptables, the underlying packet filtering framework, is equally important. iptables provides more granular control over packet filtering, allowing for detailed rule creation that defines how packets are processed through the system.
Understanding how to configure tables, chains, and rules in iptables helps in creating robust firewall policies tailored to specific security needs. Combining the use of firewalld for high-level management and iptables for detailed configurations equips me with comprehensive skills to effectively manage and secure network traffic. This dual approach not only prepares me for the RHCSA exam but also enhances my ability to implement and maintain strong security measures in real-world Linux environments, ensuring the safety and integrity of network communications.
Wednesday: Root Password Recovery and Finding Files
To recover the root password on a Linux system, you'll need to boot into single-user mode or use a rescue environment.
First, reboot the system and access the GRUB menu.
Once there, select the kernel you wish to boot and press 'e' to edit the boot parameters.
Locate the line that starts with "linux" or "linux16" and append init=/bin/bash at the end of the line.
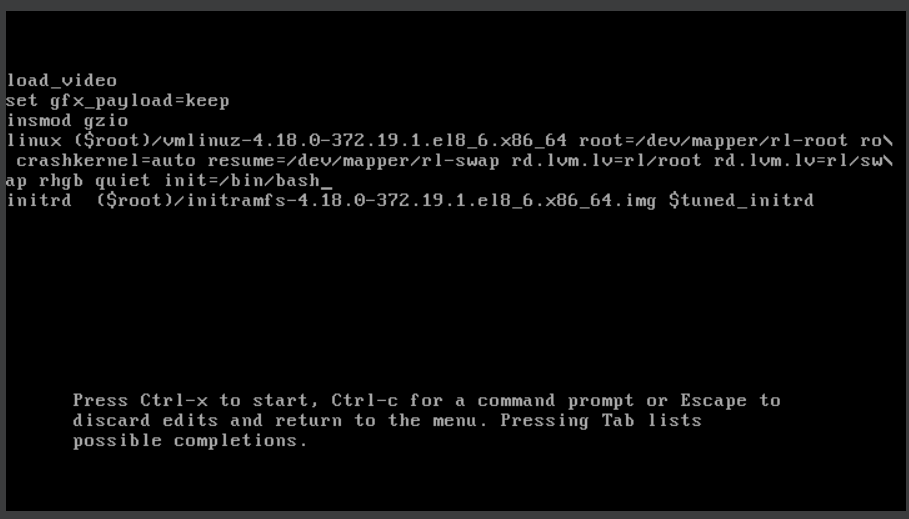
This change will boot the system directly into a bash shell with root privileges. After the system boots, remount the root filesystem in read/write mode using mount -o remount,rw /.
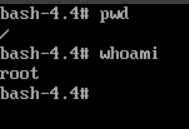
Then, use the passwd command to set a new root password.
Finally, reboot the system by typing exec /sbin/init or reboot.
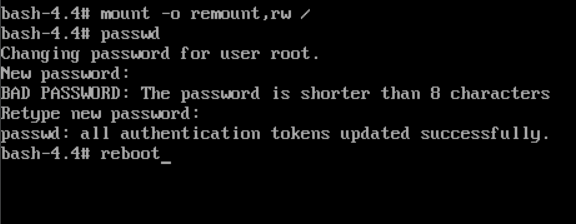
This process will reset the root password, allowing you to regain full administrative access to the system. Always ensure you have proper authorization to perform this operation, as unauthorized root access can lead to significant security risks.
Finding files in a Linux system can be efficiently managed using various command-line tools. The find command is one of the most powerful and versatile utilities for searching files and directories based on numerous criteria such as name, size, modification date, and permissions.
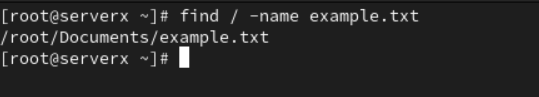
For example, to find a file named "example.txt" starting from the root directory, you can use the command find / -name example.txt.
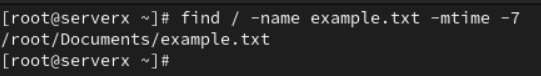
To search for files modified in the last seven days, you can use find /path/to/directory -mtime -7.
Another useful tool is locate, which relies on a prebuilt database to quickly find files by name. The database is periodically updated by the updatedb command, making locate much faster than find for simple name-based searches. For instance, locate example.txt will swiftly return all occurrences of "example.txt" across the system. Additionally, the grep command can be combined with find to search for specific text within files, enhancing the granularity of your searches.
Mastery of these tools ensures efficient file management and retrieval, an essential skill for both RHCSA exam candidates and everyday Linux administration.
Thursday: SELinux & Linux Security
Security-Enhanced Linux (SELinux) is a crucial framework for maintaining high-security standards in Linux environments, offering robust access control mechanisms that go beyond traditional discretionary access controls.
SELinux implements mandatory access control (MAC) policies, which restrict users' and processes' abilities to access files and system resources based on defined security policies.
For RHCSA exam candidates, mastering SELinux is essential, as it provides the foundational knowledge required to configure, manage, and troubleshoot security policies effectively. Understanding SELinux involves learning how to set and enforce policies, manage SELinux modes, and interpret security context labels, which collectively ensure a secure and compliant system environment.
Learning SELinux equips administrators with the skills to mitigate potential security threats and enforce strict access controls. By mastering SELinux tools such as semanage, setsebool, and restorecon, RHCSA candidates can effectively manage SELinux policies and ensure system security. Additionally, understanding SELinux log messages and employing troubleshooting techniques enables administrators to identify and resolve security policy violations efficiently. Overall, proficiency in SELinux not only prepares candidates for the RHCSA exam but also empowers them to implement and maintain robust security measures, safeguarding Linux systems against unauthorized access and potential exploits.
Friday: Logical Volume Management (LVM)
Logical Volume Management (LVM) has been a vital part of my studies. LVM provides a flexible and efficient way to manage disk space in Linux environments, allowing administrators to create, resize, and move logical volumes without the need for extensive downtime. Understanding LVM involves learning to create and manage volume groups (VGs), physical volumes (PVs), and logical volumes (LVs). These components form the backbone of LVM, enabling dynamic allocation and management of storage space across multiple physical disks. Key commands such as pvcreate, vgcreate, and lvcreate are essential for setting up and maintaining LVM structures, providing a robust framework for scalable and resilient storage management.
Mastering LVM also includes advanced tasks like resizing logical volumes with lvextend and lvreduce, taking snapshots for backups, and migrating data between physical volumes. These capabilities allow for seamless storage management and optimization, which are crucial in enterprise environments where data availability and flexibility are paramount. Additionally, understanding LVM’s integration with file systems, such as extending a logical volume and resizing the file system in one seamless operation, enhances my ability to maintain and troubleshoot storage configurations effectively. Gaining proficiency in LVM not only prepares me for the RHCSA exam but also equips me with the practical skills needed to manage complex storage solutions in real-world scenarios, ensuring that I can efficiently support the dynamic storage needs of any Linux-based infrastructure.
Subscribe to my newsletter
Read articles from Darnell W. directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
