From Zero to Cipher: An Introductory Guide to Cryptography
 Manan Shah
Manan Shah
Understanding the Cryptography
Cryptography is a method used to secure communication by changing plain text into a coded format called ciphertext. It uses different algorithms and protocols to keep data private, ensure its accuracy, verify identities, and prevent denial of actions. In simple terms, cryptography uses codes to protect information so only the intended recipients can read it, stopping unauthorized access. The word "cryptography" comes from Greek words meaning "hidden writing." It uses math techniques and rules called algorithms to change messages in ways that are hard to decode.
In simpler terms, cryptography is like creating secret codes that only the right people can understand, keeping our information safe and secure from unauthorized access.
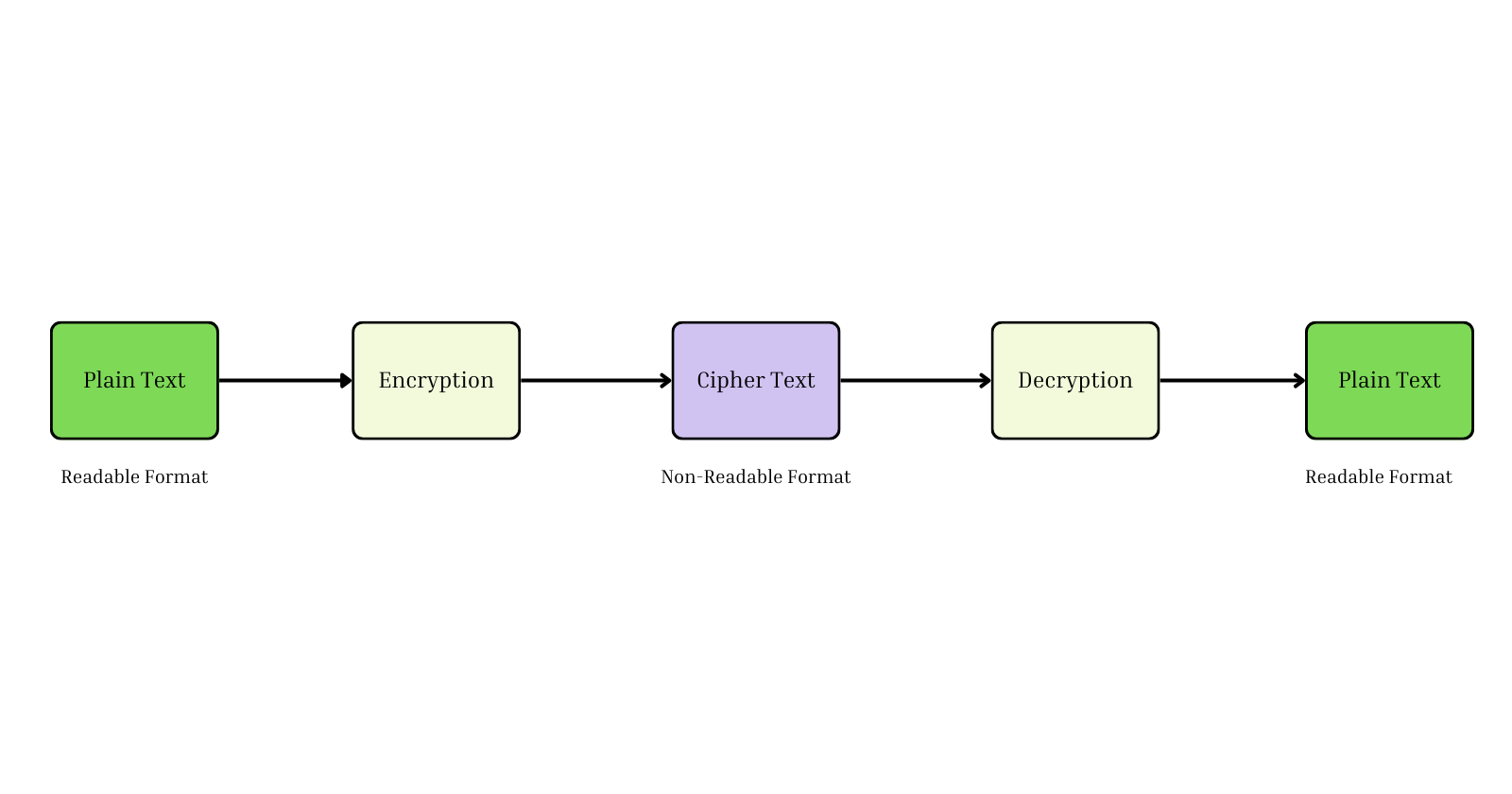
Key Terms in Cryptography
Plain Text-
Plain text is the original, readable form of a message or data before any encryption is applied. It is easy for humans and computers to understand but is unprotected and can be accessed by unauthorized people if not encrypted.
Encryption-
Encryption is the process of changing plain text into an unreadable format called ciphertext using an algorithm and a key. The goal of encryption is to protect data by making it unreadable to unauthorized people and ensuring data privacy during transmission or storage.
Cipher Text-
Ciphertext is the scrambled, unreadable result of encrypting plain text. It looks like a random mix of characters and can't be understood without the right decryption key, stopping unauthorized people from accessing the original information.
Decryption-
Decryption is the reverse process of encryption, converting ciphertext back into its original plain text using an algorithm and a key. This process allows authorized parties to access and understand the encrypted data.
Types of Cryptography
There are two main types of Cryptography.
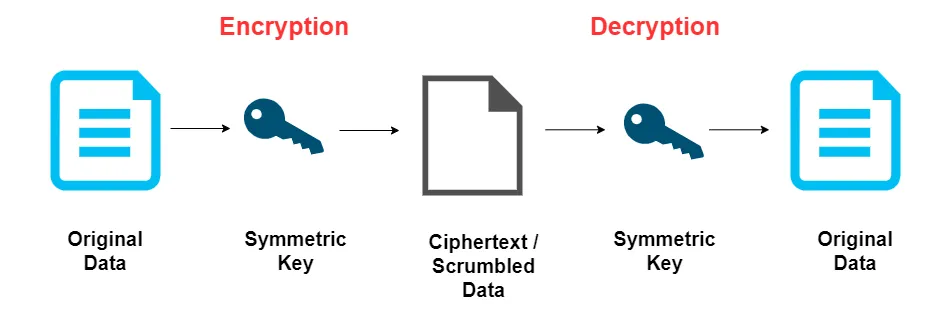
Symmetric Cryptography-
Symmetric cryptography, also known as secret-key cryptography, uses the same key for both encryption and decryption. This method is simple and efficient, making it great for quickly securing large amounts of data. Common algorithms used include AES and 3DES. The main challenge is safely sharing and managing the key between users. Despite this, symmetric cryptography is widely used for data encryption, secure communications, and network security, providing strong protection for sensitive information.
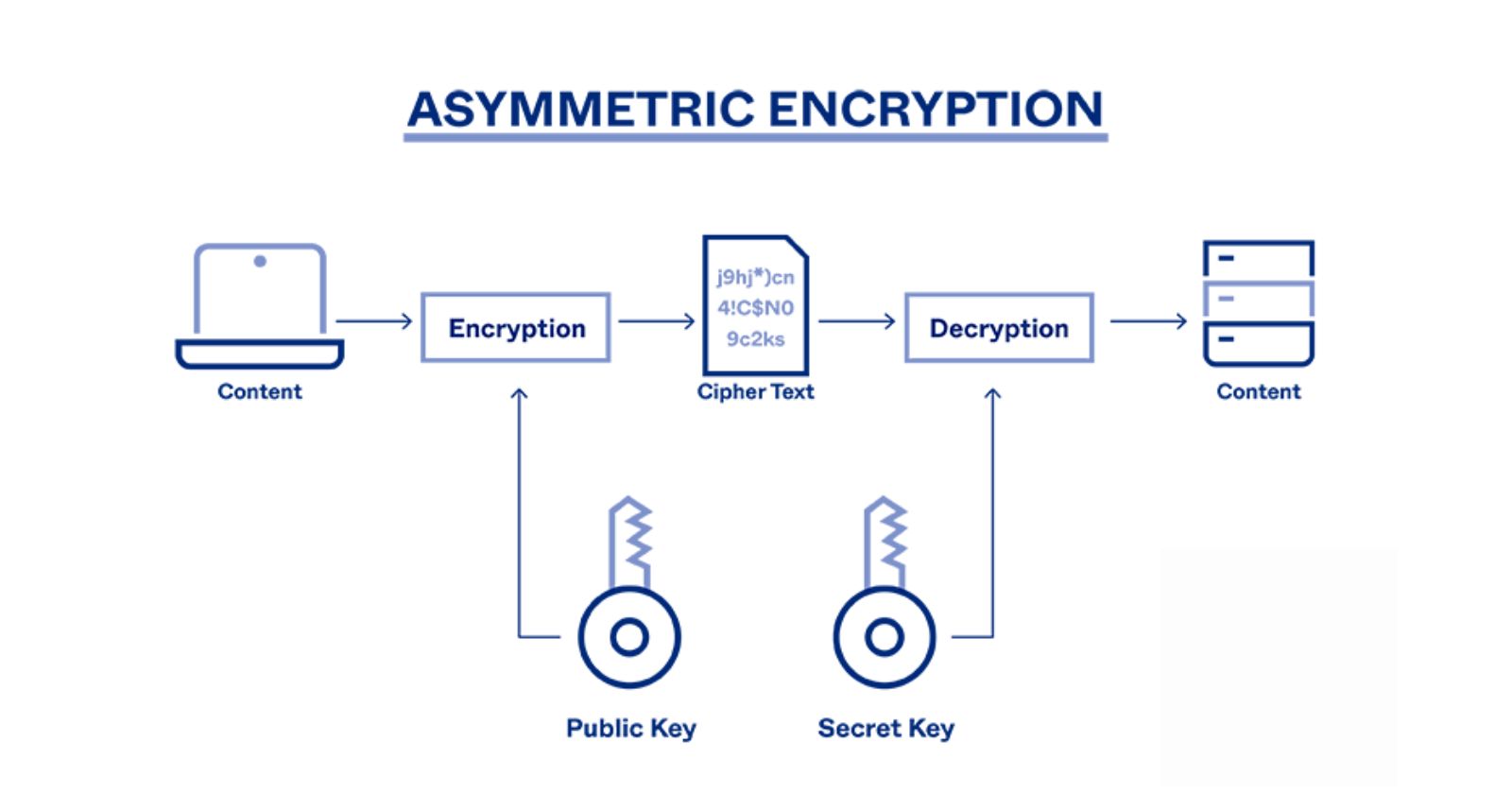
Asymmetric Cryptography-
In asymmetric key cryptography, two keys are used: one for encryption and one for decryption. The public key is used to encrypt the message, and the private key is used to decrypt it. Public and private keys are different; even if everyone knows the public key, only the intended receiver can decrypt the message with their private key. A well-known asymmetric key algorithm is RSA.
Application of Cryptography
There are several applications of cryptography, including:
Secure Communication: Cryptography secures communication channels, such as emails, messaging apps, and voice calls, by encrypting the transmitted data. This ensures that only the person you want can read and understand the message, keeping it safe from snooping and people who shouldn't see it.
Data Protection: Cryptography is used to encrypt sensitive data stored on computers, servers, and other devices. This protects the information from unauthorized access, ensuring confidentiality and integrity. Common examples include disk encryption, file encryption, and database encryption.
Authentication and Authorization: Cryptography helps with authentication and authorization by verifying user identities and granting access to protected resources. Digital signatures, certificates, and authentication protocols ensure the integrity and authenticity of digital identities and transactions.
Secure Transactions: Cryptography secures online transactions over the internet, like e-commerce purchases, online banking, and cryptocurrency transactions. Protocols like SSL/TLS encrypt the communication between web browsers and servers, protecting sensitive financial and personal information from being intercepted or tampered with.
Cryptocurrencies: Cryptocurrencies like Bitcoin and Ethereum use cryptography to keep transactions safe, prevent fraud, and ensure the network stays secure. They use complex codes and keys to protect the transactions, making it almost impossible to alter or fake them.
Conclusion
Cryptography is crucial for keeping our digital information safe. It turns readable data into coded messages to protect it from unauthorized access. Basic terms like plain text, encryption, ciphertext, and decryption are key to understanding how it works. There are two main types of cryptography: symmetric, which uses the same key for both encoding and decoding and asymmetric, which uses a public key for encoding and a private key for decoding.
Cryptography is used in many areas, such as securing communications, protecting stored data, verifying identities, and ensuring safe online transactions. As we use more digital systems, cryptography will become even more important for keeping our information private and secure.
Subscribe to my newsletter
Read articles from Manan Shah directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
