CVE-2024-34240: Latest Stored XSS 0day Vulnerability Unveiled
 Sergio Medeiros
Sergio Medeiros
Late in the evening, I decided to explore some PHP applications focused on Student Information Systems, inspired by my recent success in finding systemic stored XSS vulnerabilities in a private bug bounty program. I visited my favorite source for PHP-related applications, https://codecanyon.net/. This led me to QDOCS Smart School: School Management System. I decided to check out the demo of their latest version, 7.0.0.
Usually, when I start looking for easy-to-find stored XSS "0days," I log in as the administrator. This gives me access to more features on both the front end and back end, allowing me to insert malicious input in various parts of the application. I quickly discovered that the web application was sanitizing special characters and specific HTML elements, which prevents XSS attacks.
However, further investigation revealed that the following endpoints are still vulnerable to my "go-to" XSS payload.
Endpoint: POST /admin/feediscount/edit Parameter: name Endpoint: POST /admin/birthordeath/update_birth Parameters: father_name
I noticed that when I used the following XSS payload structure, I could bypass the existing protections. This allowed my malicious JavaScript code to be stored and executed successfully whenever a user visited any of the modified records associated with fee discounts and birth records.
<details/open/ontoggle=prompt(origin)>
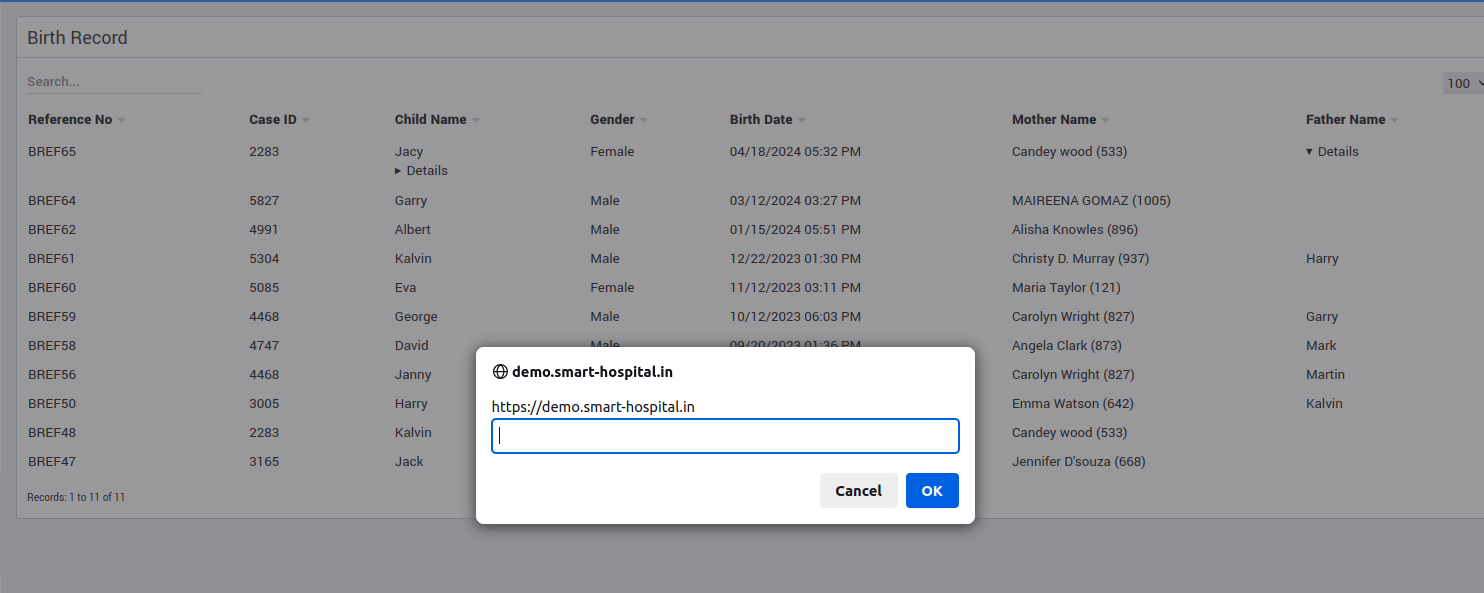
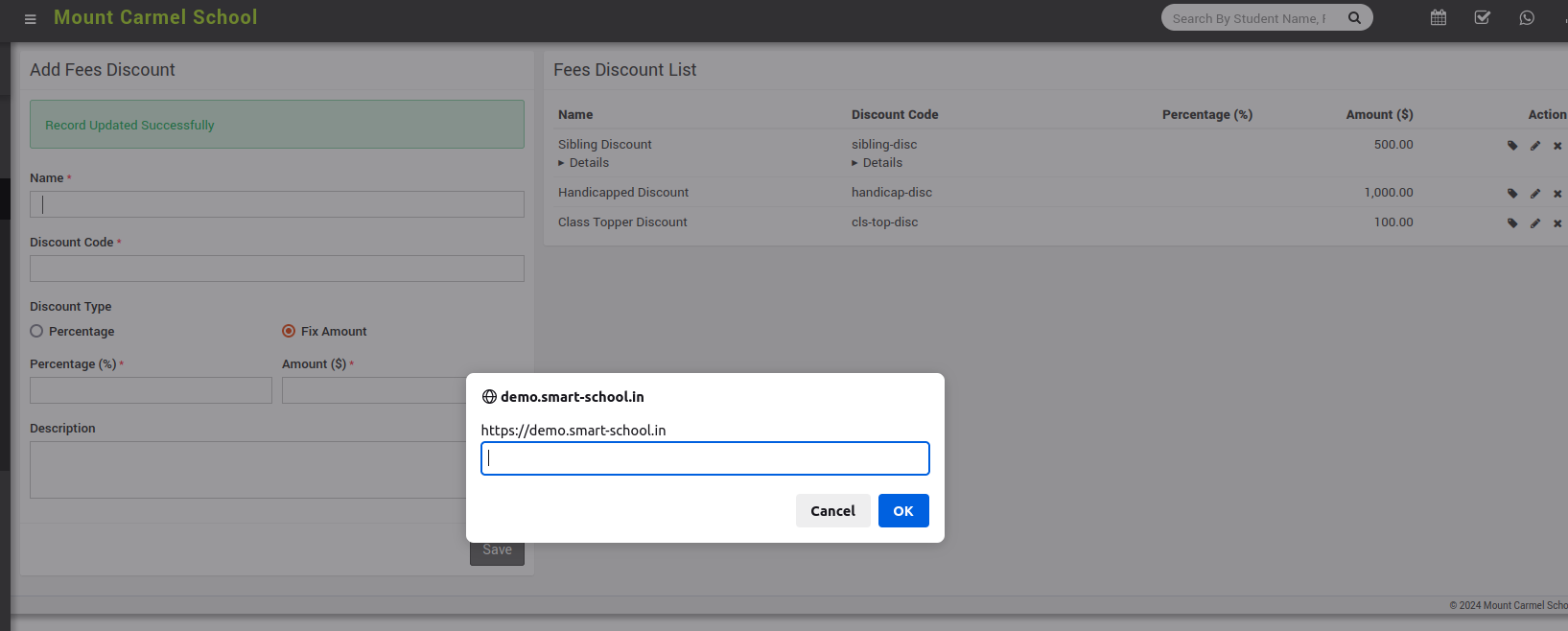
And just like that, we found another stored XSS "0day" in just a few minutes!

I often feel repetitive when wrapping up these articles. I write them with the hope that newcomers to the bug bounty and cybersecurity industry will get excited and motivated to hunt for bugs themselves. I hope my content sparks a strong desire to become a successful bug bounty hunter and skilled hacker.
For those who need a little encouragement, I suggest diving into the concepts you love. This industry is an addiction for me, and I can't go a day without doing something related to hacking. Whether it's reading a technical CVE write-up, watching DEFCON videos, working on PortSwigger Labs, or hacking on bug bounty programs, there's always something to engage with.
If you have any questions or need some guidance, please feel free to reach out to me on Twitter via DM (@grumpzsux). I love helping newcomers in the industry.
Happy hacking my fellow nerds,
- GRuMPz aka Sergio Medeiros
Subscribe to my newsletter
Read articles from Sergio Medeiros directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sergio Medeiros
Sergio Medeiros
| Vulnerability Operations @ Synack | Bug Bounty Hunter. Security Researcher. Wannabe hacker, sharing my thoughts on how to be successful in the cyber security space, after pivoting careers of being a decade long Sales Director.