Web Application Penetration Testing Methodology
 PopLab Agency
PopLab AgencyWeb Penetration Testing Methodology
Some of the Security Testing Methodologies and standards are:
- OWASP (Open Web Application Security Project)
- OSSTMM (Open Source Security Testing Methodology Manual)
- PTF (Penetration Testing Framework)
- ISSAF (Information Systems Security Assessment Framework)
- PCI DSS (Payment Card Industry Data Security Standard)
OWASP Top 10 2021
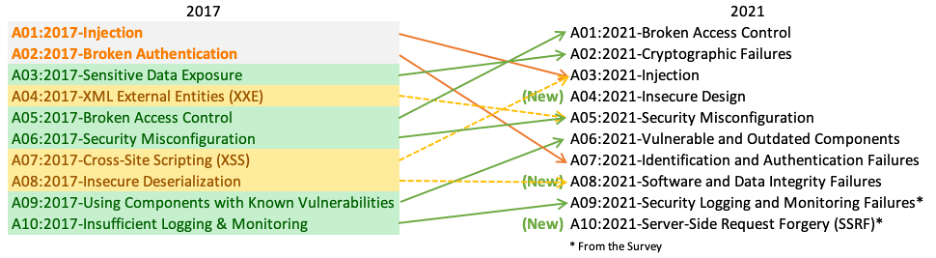
A1:2021 – Broken authentication
A2:2021 – Cryptographic Failures
A3:2021 – Injection
Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
A4:2021 – Insecure Design
Security should be a primary consideration during the design phase of the software development lifecycle. Unfortunately, this is often not the case, resulting in software that is vulnerable to attacks.
A5:2021 – Security Misconfigurations
Security misconfiguration is the most common issue that we see. This is commonly a result of insecure default configurations, incomplete or ad hoc configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information.
Cross-Site Scripting
SQL Injection
Session management
File Upload flaws
File upload flaws can occur due to various reasons, such as insufficient validation and sanitization of uploaded files, lack of proper file type and size validation, inadequate access controls, and poor server-side configuration.
- Unrestricted File Upload
- File Type Validation Bypass
- File Size Validation Bypass
- File Overwrite
- Directory Traversal
Caching Servers Attacks
Cross-Site Request Forgery
Password Cracking
Web Penetration Testing Certifications
If you are interested in getting certified in web app penetration certification, you can opt for the below certifications:
Subscribe to my newsletter
Read articles from PopLab Agency directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
