Step-by-Step Tutorial on Using ConfigMaps and Secrets in Kubernetes
 Mohmmad Saif
Mohmmad Saif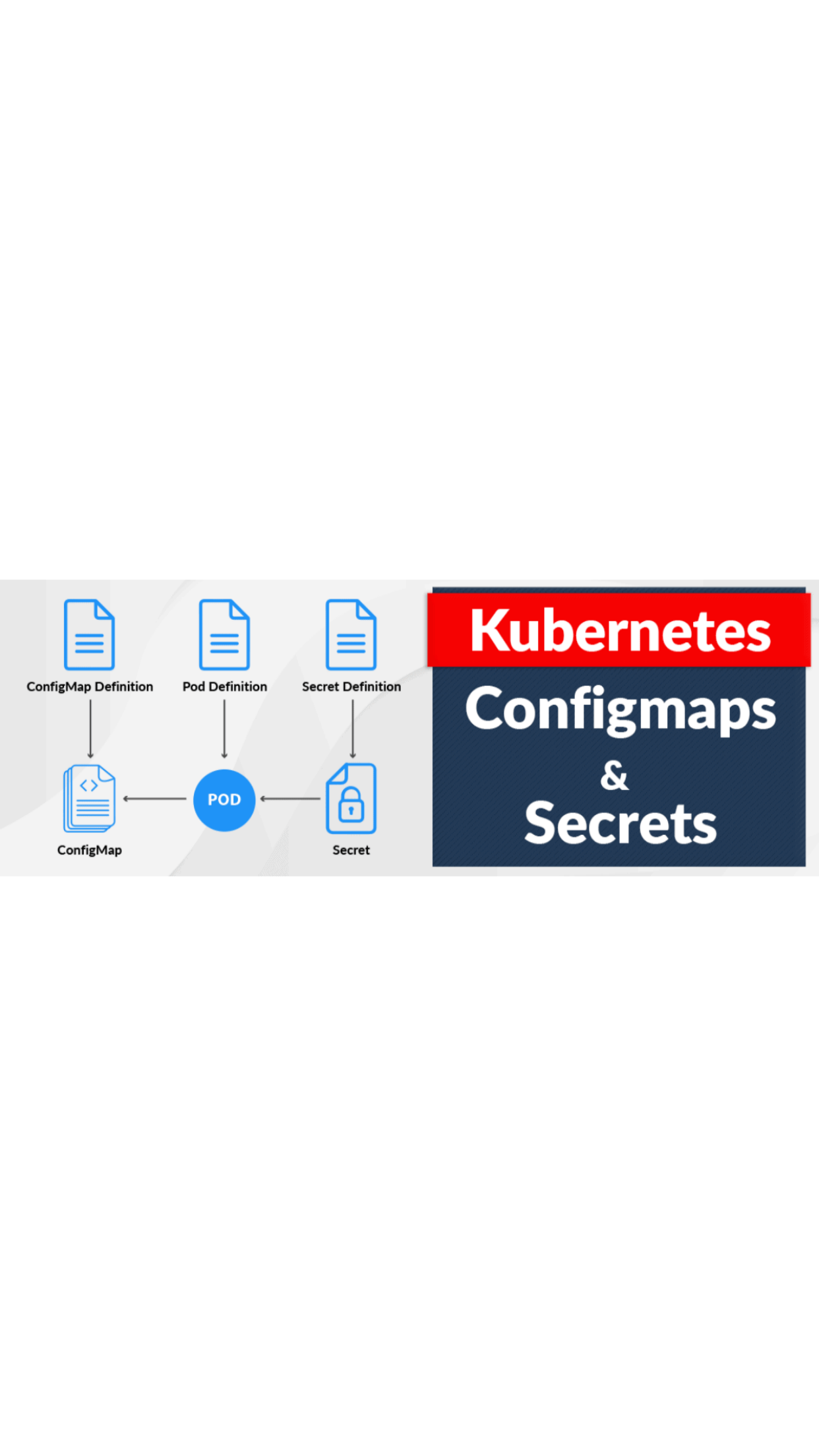
In Kubernetes, ConfigMaps and Secrets are fundamental constructs for managing configuration and sensitive data. Let's dive into more details on each, including how to create, manage, and use them in your applications.
ConfigMaps
ConfigMaps are used to store non-confidential data in key-value pairs. This can be used for configuration files, command-line arguments, environment variables, and more.
Creating a ConfigMap
From Literal Values:
apiVersion: v1 kind: ConfigMap metadata: name: my-config data: key1: value1 key2: value2Alternatively, you can create it using the command line:
kubectl create configmap my-config --from-literal=key1=value1 --from-literal=key2=value2From a File:
kubectl create configmap my-config --from-file=path/to/config/fileFrom a Directory:
kubectl create configmap my-config --from-file=path/to/directory
Using a ConfigMap in a Pod
As Environment Variables:
apiVersion: v1 kind: Pod metadata: name: my-pod spec: containers: - name: my-container image: my-image envFrom: - configMapRef: name: my-configAs a Volume:
apiVersion: v1 kind: Pod metadata: name: my-pod spec: containers: - name: my-container image: my-image volumeMounts: - name: config-volume mountPath: /etc/config volumes: - name: config-volume configMap: name: my-config
Secrets
Secrets are similar to ConfigMaps but are specifically designed to store sensitive data such as passwords, OAuth tokens, and SSH keys. The data in Secrets is base64-encoded.
Creating a Secret
From Literal Values:
apiVersion: v1 kind: Secret metadata: name: my-secret type: Opaque data: username: dXNlcm5hbWU= # base64 encoded value of "username" password: cGFzc3dvcmQ= # base64 encoded value of "password"Alternatively, you can create it using the command line:
kubectl create secret generic my-secret --from-literal=username=user --from-literal=password=passFrom a File:
kubectl create secret generic my-secret --from-file=path/to/secret/fileFrom Environment Variables:
echo -n 'my-password' | base64 kubectl create secret generic my-secret --from-env-file=path/to/env/file
Using a Secret in a Pod
As Environment Variables:
apiVersion: v1 kind: Pod metadata: name: my-pod spec: containers: - name: my-container image: my-image env: - name: USERNAME valueFrom: secretKeyRef: name: my-secret key: username - name: PASSWORD valueFrom: secretKeyRef: name: my-secret key: passwordAs a Volume:
apiVersion: v1 kind: Pod metadata: name: my-pod spec: containers: - name: my-container image: my-image volumeMounts: - name: secret-volume mountPath: /etc/secret volumes: - name: secret-volume secret: secretName: my-secret
Key Differences
Purpose:
ConfigMap: Stores non-sensitive data.
Secret: Stores sensitive data.
Data Encoding:
ConfigMap: Stores data as plain text.
Secret: Stores data as base64-encoded strings.
Use Cases:
ConfigMap: Configuration files, command-line arguments, environment variables.
Secret: Passwords, API keys, tokens, SSH keys.
Security:
ConfigMap: Less secure, designed for non-sensitive data.
Secret: More secure, intended for sensitive information.
Best Practices
Use Secrets for Sensitive Data: Always store passwords, tokens, and keys in Secrets.
Limit Access: Use Kubernetes RBAC to limit access to ConfigMaps and Secrets.
Avoid Hardcoding: Avoid hardcoding sensitive data in your application code.
Use Environment Variables: Use environment variables for configuration to keep your applications portable.
Understanding and using ConfigMaps and Secrets correctly can significantly enhance the security and manageability of your Kubernetes applications.
Subscribe to my newsletter
Read articles from Mohmmad Saif directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mohmmad Saif
Mohmmad Saif
👋Hello I am Mohd Saif, passionate technology enthusiast currently pursuing a bachelor of Computer application degree. 🎓Education: I am currently pursuing a bachelor of Computer application degree with the focus on coding at Bareilly University my education journey has equipped me with strong foundation in Computer science and I am eager to apply my knowledge to real word challenges. 💡Passion for technology: I have always been deeply passionate about technology and I am particular drawn to devops with AWS. 🚀Skills: 🔹Linux 🔹Shell scripting 🔹Python 🔹Ansible 🔹Docker 🔹Kubernetes 🔹Jenkins CI/CD 🔹Maven 🔹Git and GitHub ✨Future goals: My goal is to facilitate seamless collaboration between development and operations teams, ensuring faster releases and high-quality software. I am a proactive learner, constantly exploring new DevOps trends and practices