Configure Iis Web Server On Window Server
 Ibikunle ayobami
Ibikunle ayobami
1. Create a windows Server with IIS installed
Create an Application Security Group(ASG) in the same region as your Server.
Go the Server's NSG and Add an inbound rule on port 80 and Port 443.
Create firewall and attach it to the Server's Vnet to secure your environment from malicious threats..
Once done, Copy your Public IP to a browser and ensure there is connectivity
When writing your blog, you can start from how you installed IIS on the server.
Introduction
WHAT IS IIS WEB SERVER
Internet Information Services (IIS), also known as IIS, is a Microsoft web server that runs on Windows operating systems. It serves as a platform for hosting, deploying, and managing web applications.
Here are some key points about IIS:
Componentization: IIS has a modular architecture where all web server features are managed as standalone components. You can easily add, remove, or replace these components. This modularity allows you to secure the server by reducing the attack surface area. By removing unused features, you achieve the minimum surface area while preserving application functionality. Additionally, it helps improve performance by reducing memory usage and minimizing feature code execution for each request.
Extensibility; Developers can leverage IIS’s modular architecture to build powerful server components that extend or replace existing features.
Reasons to Develop for IIS
Empowering web applications: Extending IIS enables web applications to benefit from functionality that can’t easily be provided at the application layer.
Examples of extensions include custom authentication schemes, monitoring and logging, security filtering, load balancing, content redirection, and state management.
It’s suitable for a wide range of tasks, from media streaming to serving web applications.
Create a windows Server with IIS installed
We all have different ways to start creating, and I'm going to show you one method now.
We all have different ways to start creating, and I'm going to show you one method now.
- My first step is to create my Application Security Group (ASG) and discuss the Network Security Group (NSG) because they work together. When you create an ASG, Azure automatically creates an NSG for you.
WHAT IS Application Security Group (ASG)
An Application Security Group (ASG) is a feature in cloud computing, especially within Microsoft Azure, that helps you manage and secure network traffic to and from your virtual machines (VMs). ASGs allow you to group VMs and set network security policies based on these groups instead of individual IP addresses. This makes it easier to apply and manage network security rules, especially in environments with changing workloads.
Key features and benefits of Application Security Groups include:
Simplified Security Management: By grouping VMs with similar security needs, you can apply security rules to the group instead of managing each VM's security settings individually.
Dynamic Scaling: ASGs handle dynamic changes in your environment, such as adding or removing VMs, without needing to constantly update security rules.
Enhanced Visibility: Grouping VMs with similar roles improves visibility and understanding of your security policies, making it easier to audit and maintain compliance.
Micro-segmentation: ASGs support micro-segmentation, allowing for more detailed security controls within your network, which enhances your overall security posture.
WHAT IS Network Security Group (NSG)
A Network Security Group (NSG) is a critical component in cloud and network security management, especially within cloud platforms like Microsoft Azure. An NSG acts as a virtual firewall to control inbound and outbound traffic to and from network interfaces (NICs), VMs, and subnets. It provides rules that you can configure to allow or deny traffic based on factors such as source and destination IP address, port, and protocol.
Key Features of a Network Security Group:
Inbound and Outbound Rules: Define and control the flow of traffic entering or leaving the network resources.
Rule Prioritization: Rules are processed in priority order (the lower the number, the higher the priority).
Default Rules: NSGs come with default rules that allow or deny traffic, which can be overridden by custom rules.
Application of NSG: Can be applied at both the subnet level and the NIC level, allowing for granular control.
Common Use Cases:
Securing VMs: Protect virtual machines by limiting access to only necessary IP addresses and ports.
Segmenting Networks: Use NSGs to create segments within your virtual networks, improving security.
Regulating Traffic Flow: Ensure only legitimate and necessary traffic flows in and out of your subnets.
Example Scenario:
In an Azure environment, you might set up an NSG to:
Allow HTTP and HTTPS traffic to a web server (Inbound rules for ports 80 and 443).
Deny all other inbound traffic to the web server.
Allow outbound traffic to the internet for updates (Outbound rules for required ports).
Best Practices:
Least Privilege Principle: Only allow the minimal necessary traffic.
Regular Review: Periodically review and update NSG rules to adapt to new security requirements.
Use Tags: Utilize Azure service tags to simplify management of NSG rules for common Azure services.
Logging and Monitoring: Enable logging to track traffic that matches NSG rules for security audits and troubleshooting.
*** Create an Application Security Group(ASG) in the same region as your Server.
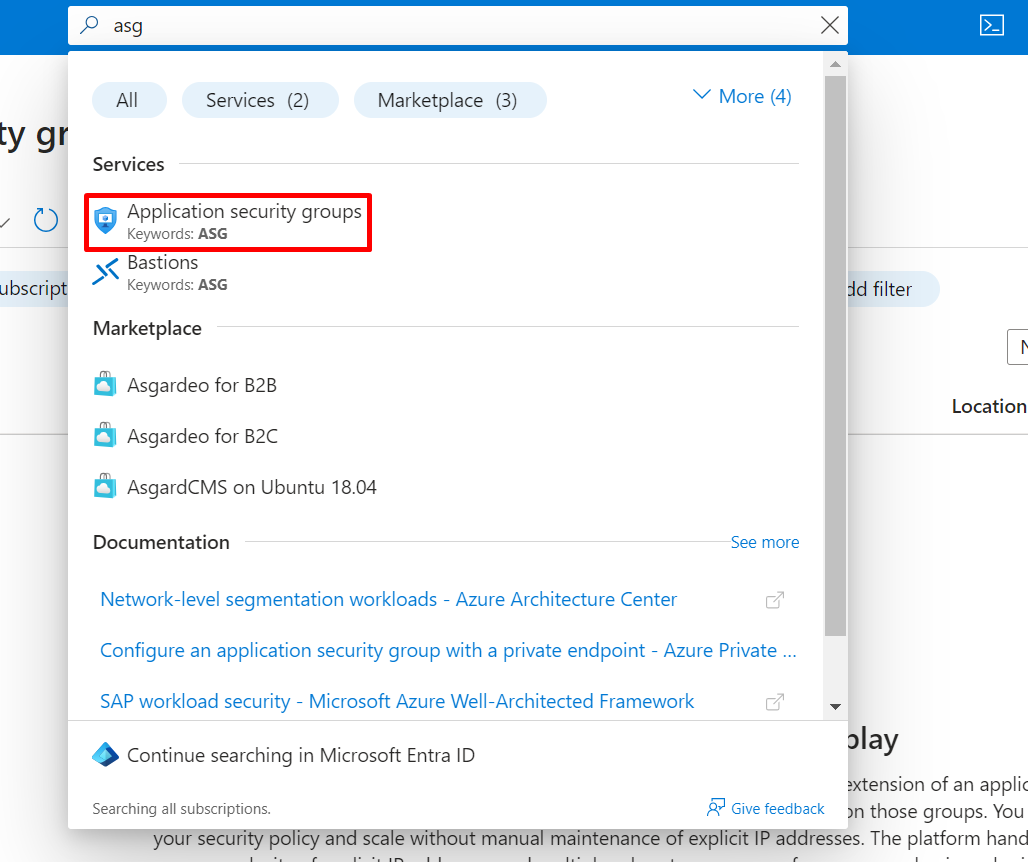
Search for ASG in the search box.
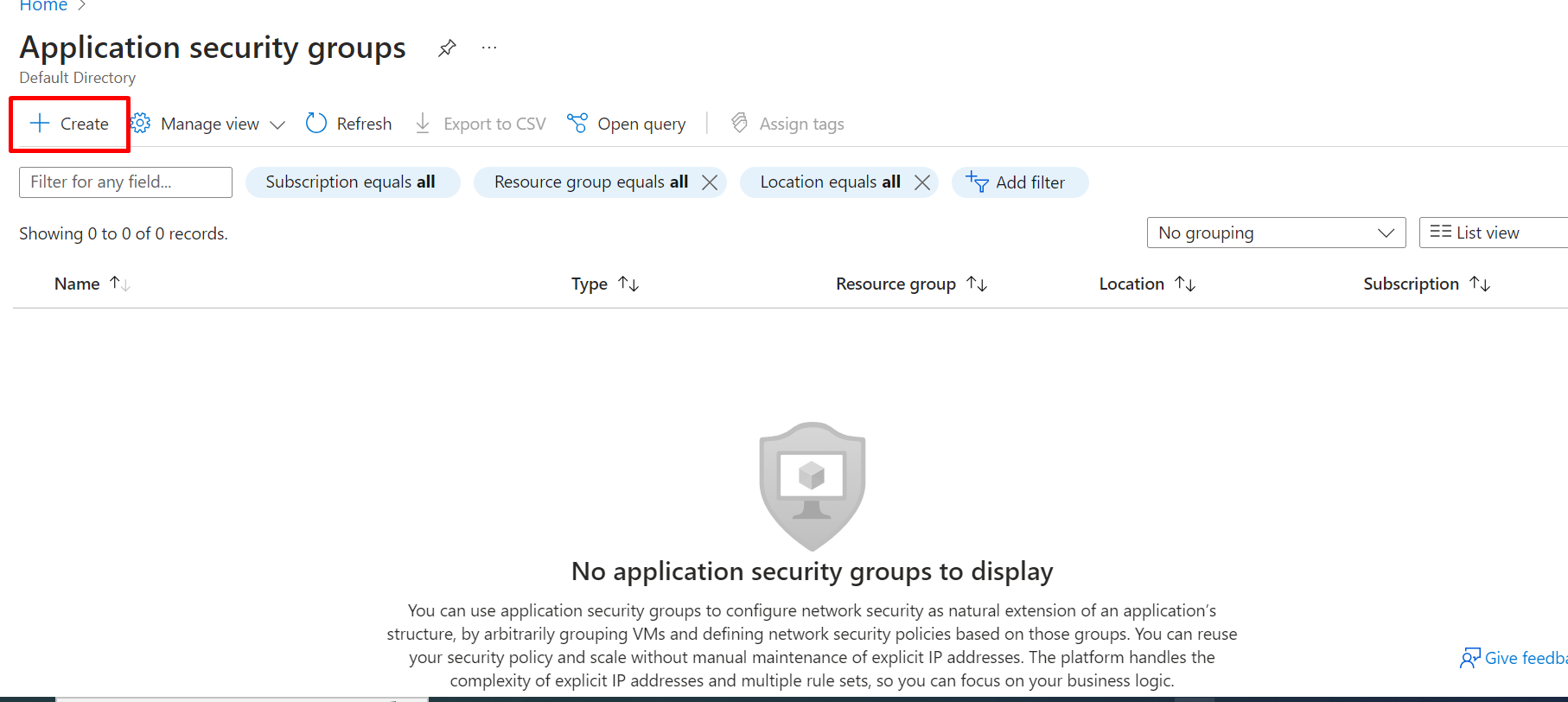
Create a USER
Go to basic and fill in the information.

Click on NEXT.
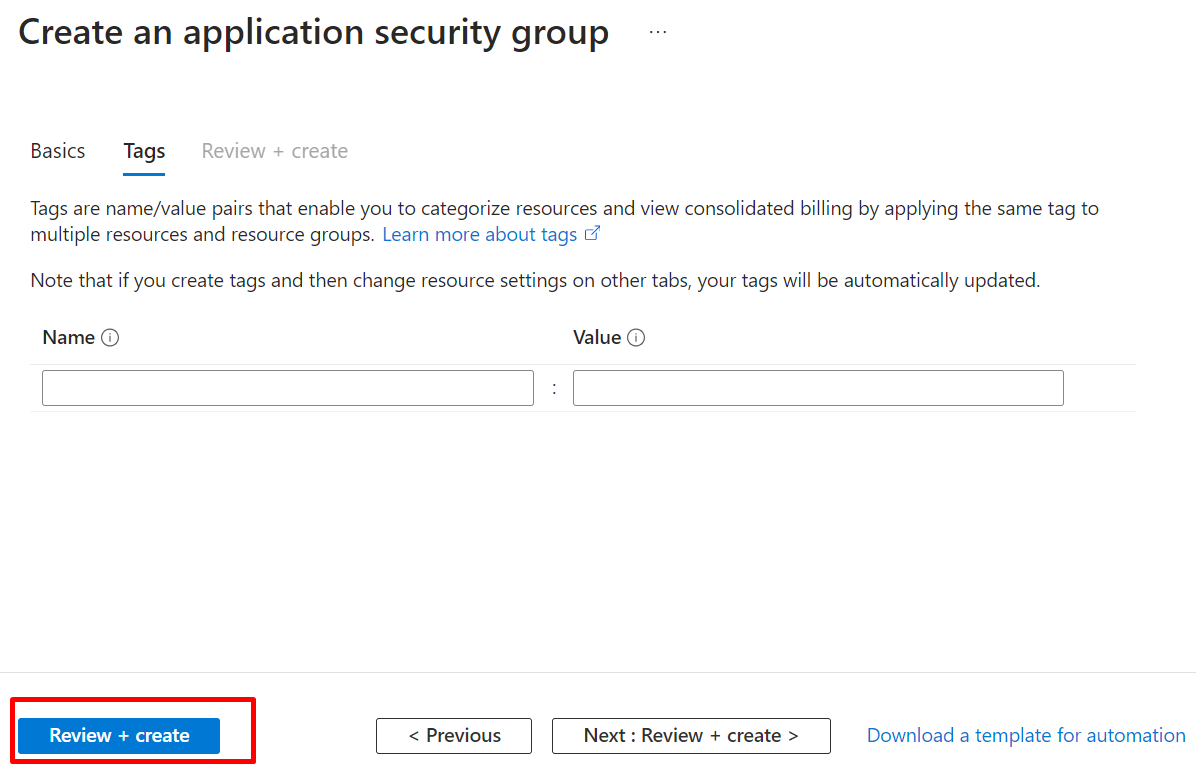
Click on Review + create.
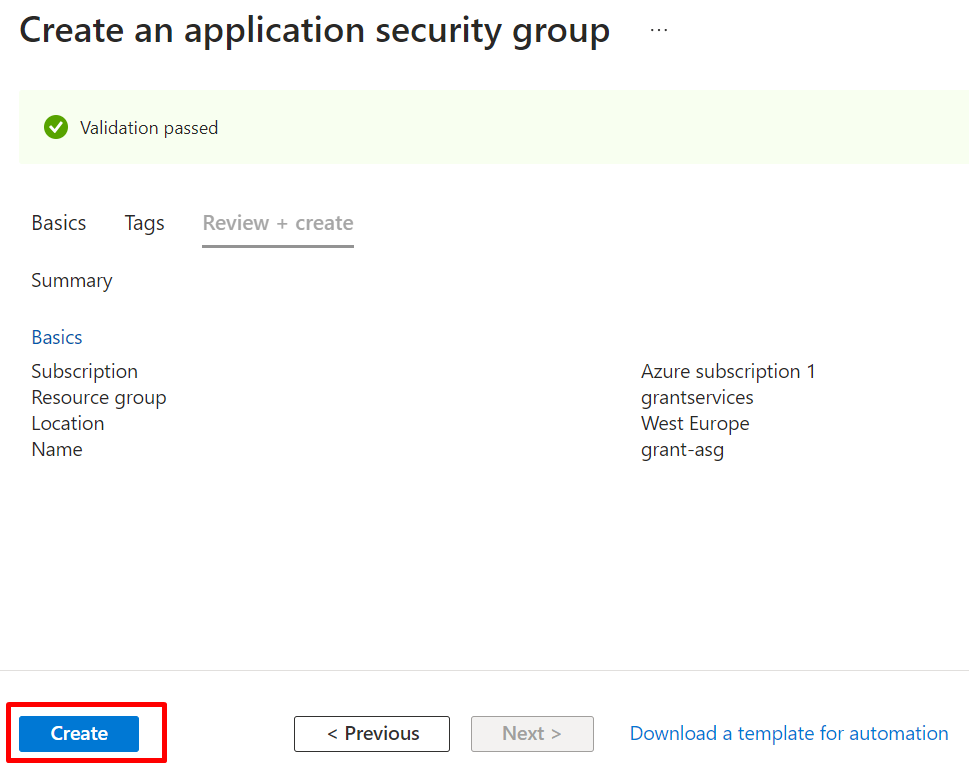
Click on Go to resource.


Now our ASG is created, and the NSG is also created automatically by default.Search for ASG in the search box.

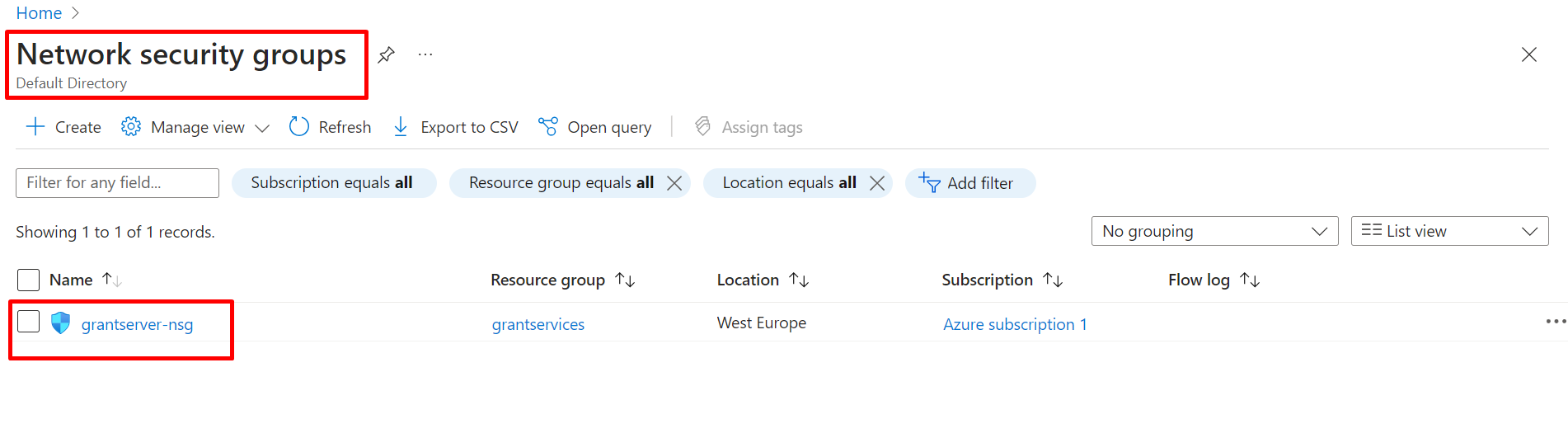
*** Go to the server's NSG and add an inbound rule for port 80 and port 443.
Go to the Network Security Group (NSG), click on it, navigate to the overview, and find the Inbound security rules.

Click on Add and fill the information.
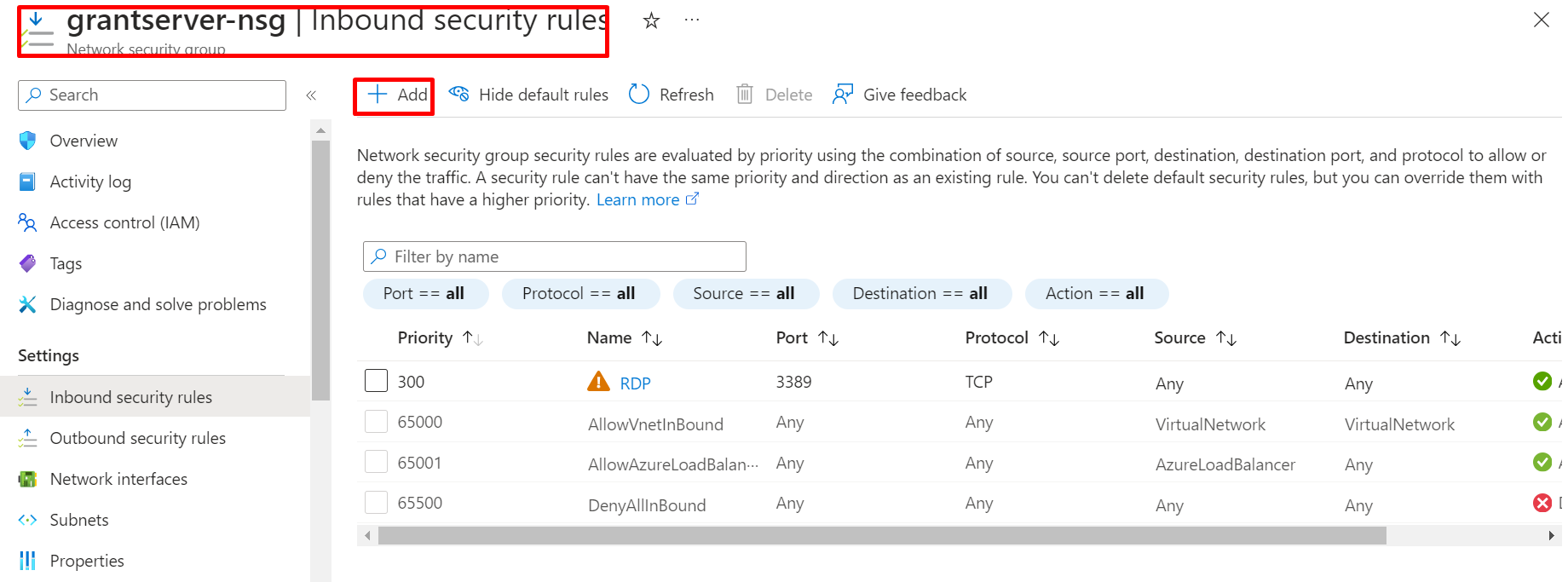


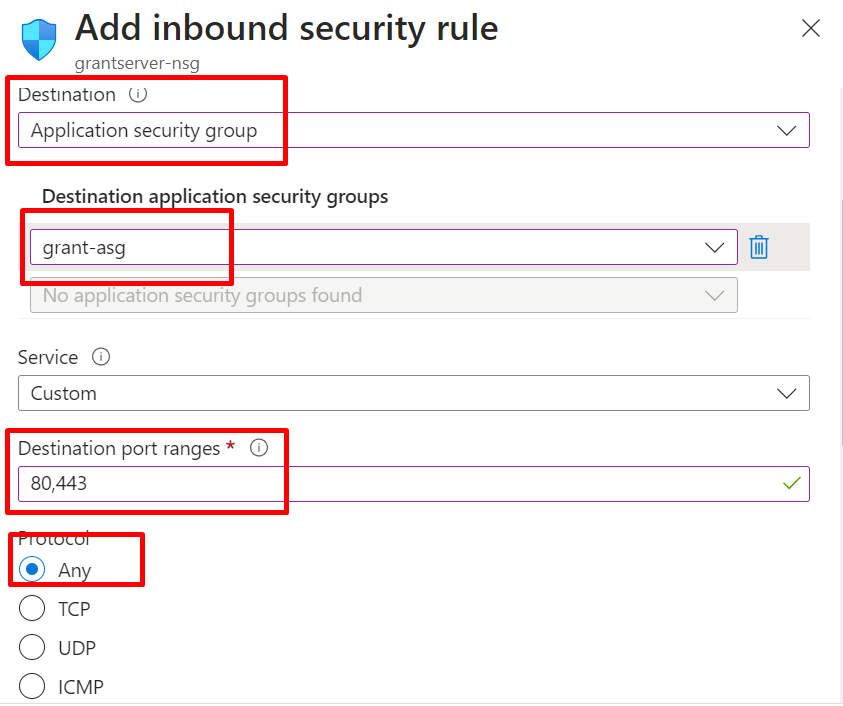


Go to the Network Security Group, click on it, navigate to the overview, and find the Inbound security rules to view the created rules.

Create A Windows Server With IIS installed.
CREATE VIRTUAL MACHINE
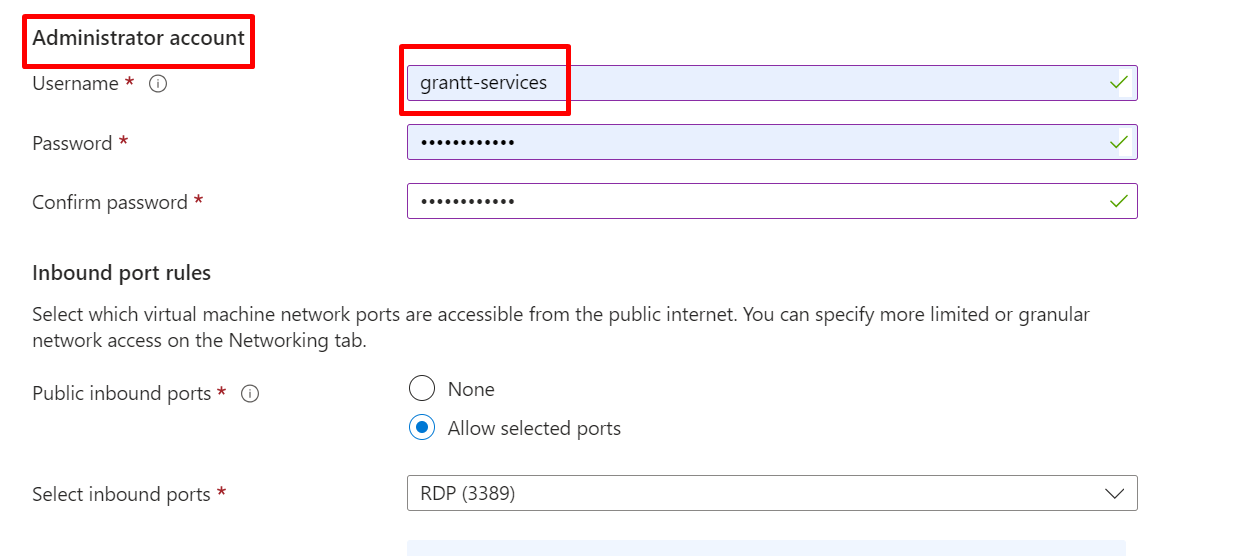
CREATE USER
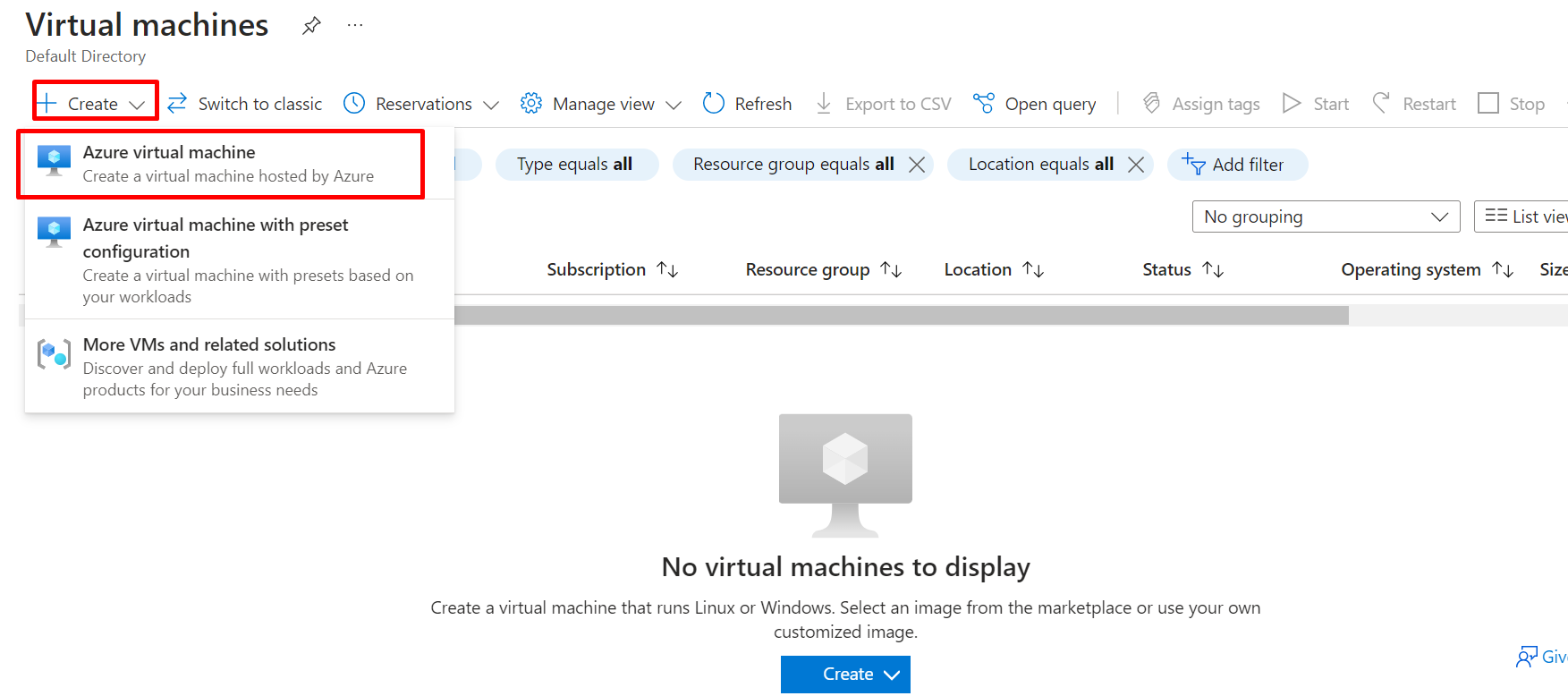

GO TO IMAGE

CLICK ON NEXT

NEXT TO NETWORKING

CLICK ON REVIEW + CREATE

GO TO RESOURCE

NAVIGATE TO OVERVIEW AND CONNECT

CLICK ON DOWNLOAD RDP FILE

CLICK ON CONNECT

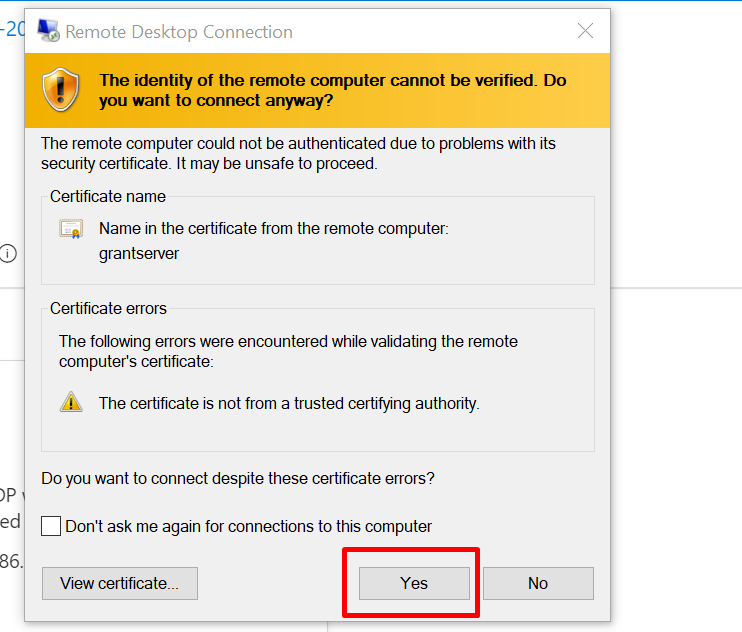
INPUT YOUR PASSWORD

CLICK ON YES
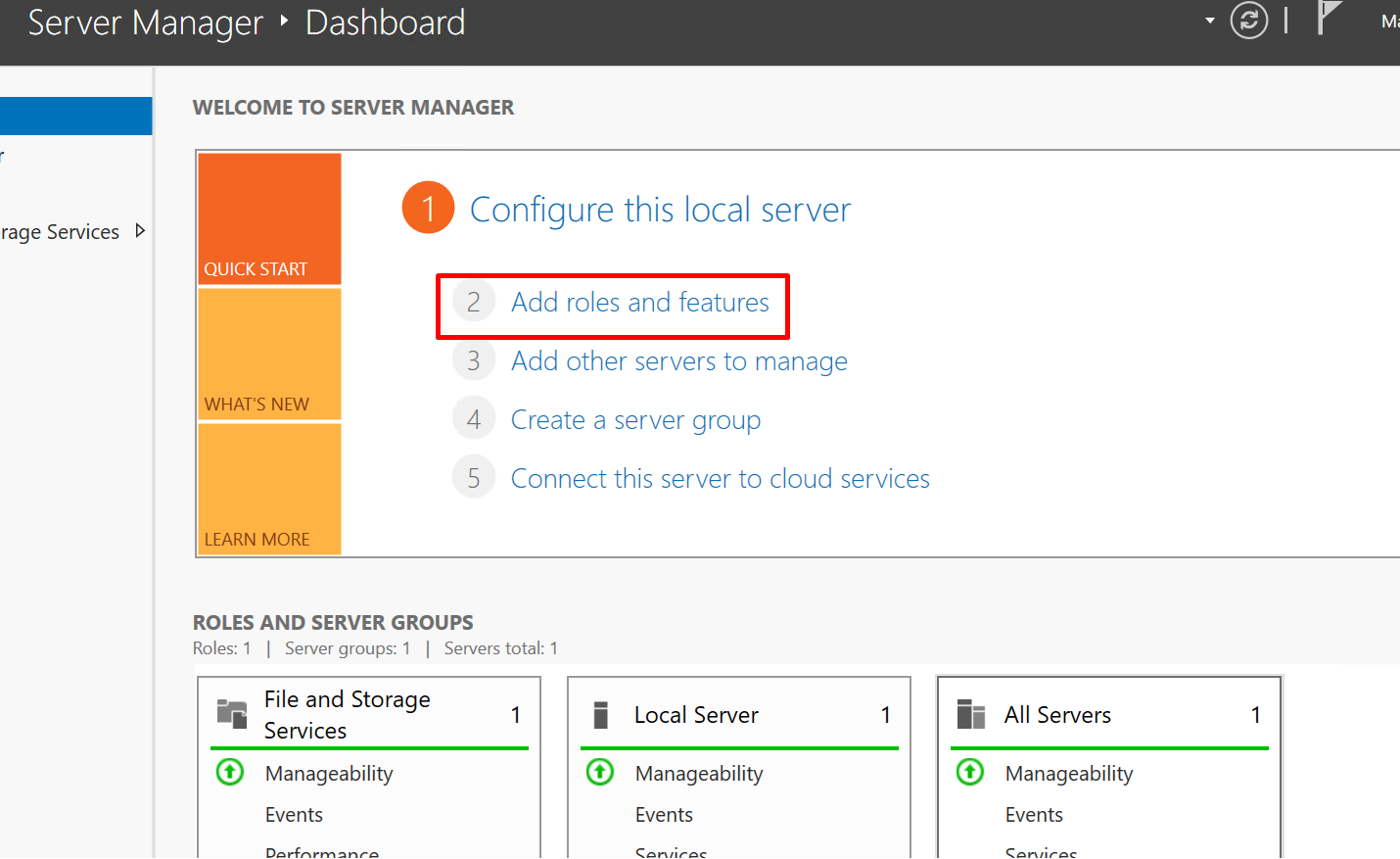
Step 1: Start Server Manager
As with all Windows Server roles, we need to go to the Server Manager to start the installation. Press your "Windows" key and search for Server Manager if it's not already open. Once it's open, click on "Add Roles and Features".

Step 2: Click Next on Wizard
On the first page of the "Add Roles and Features Wizard," click "Next."

Step 3: Select Installation Type
On the "Select Installation Type" page, choose "Role-based or feature-based installation" and click "Next".

[
](https://computingforgeeks.com/wp-content/uploads/2019/10/Add_Roles_and_Features_First_Part-1.png?ezimgfmt=rs:484x345/rscb23/ng:webp/ngcb23)Step 4: Choose Destination Server
Select the server selection and click “Next“
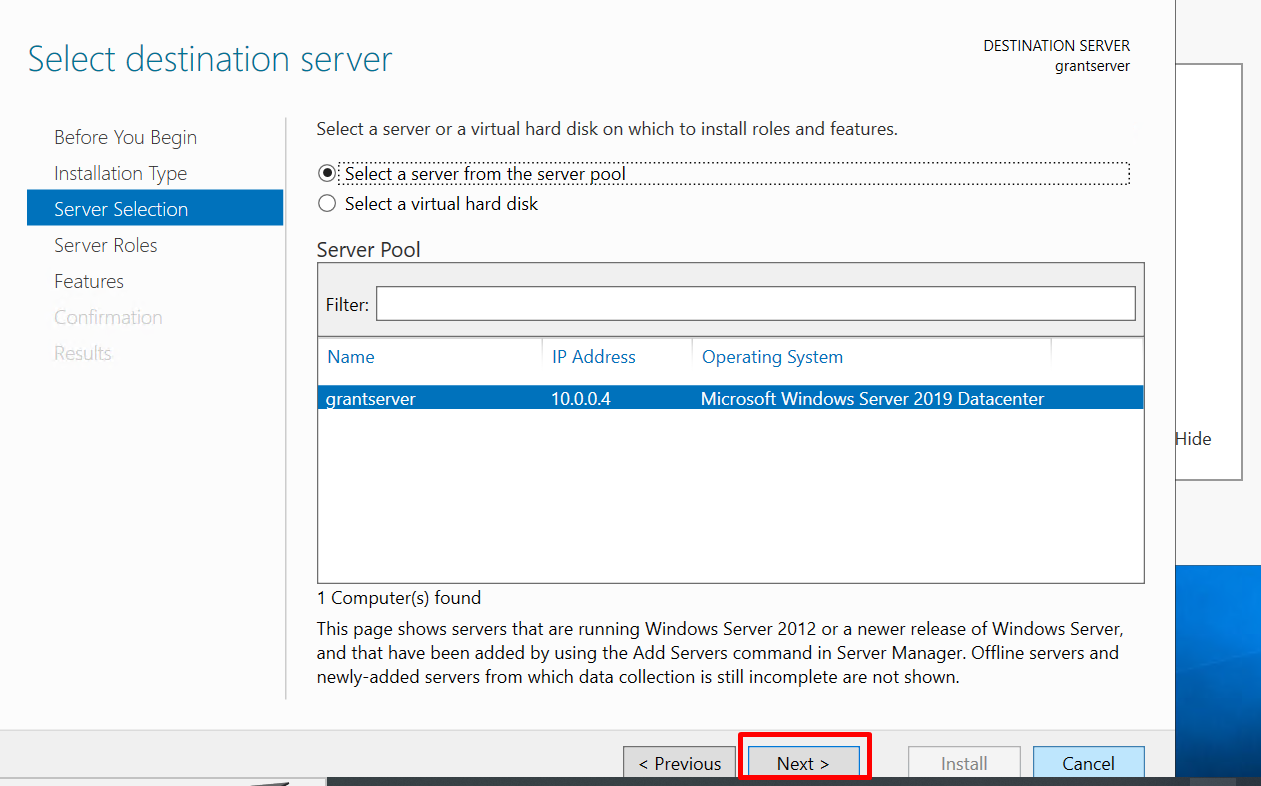
Step 5: Select Roles to install
In the "Select server roles" section, check the "Web Server (IIS)" box. A pop-up window will then appear.
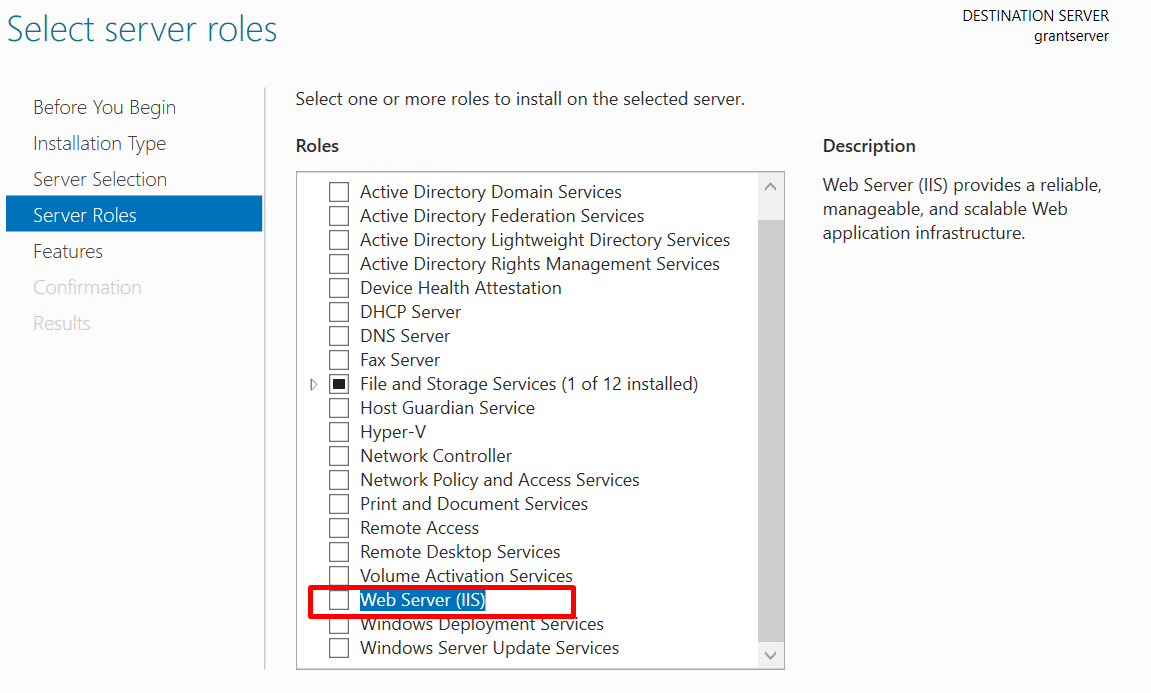
Step 6: Add IIS Features
In the pop-up window, click on "Add Features," then hit "Next." After that, click "Next" on the following three windows as shown below.

CLICK ON NEXT

NEXT

NEXT
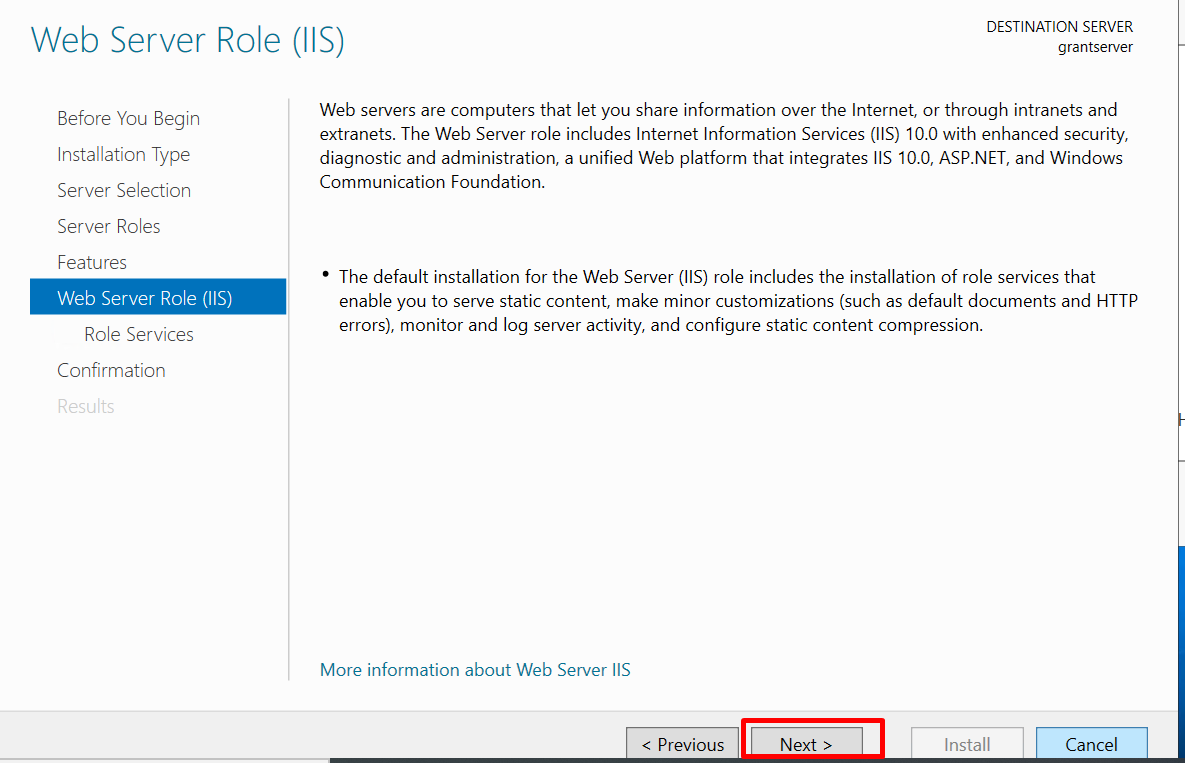

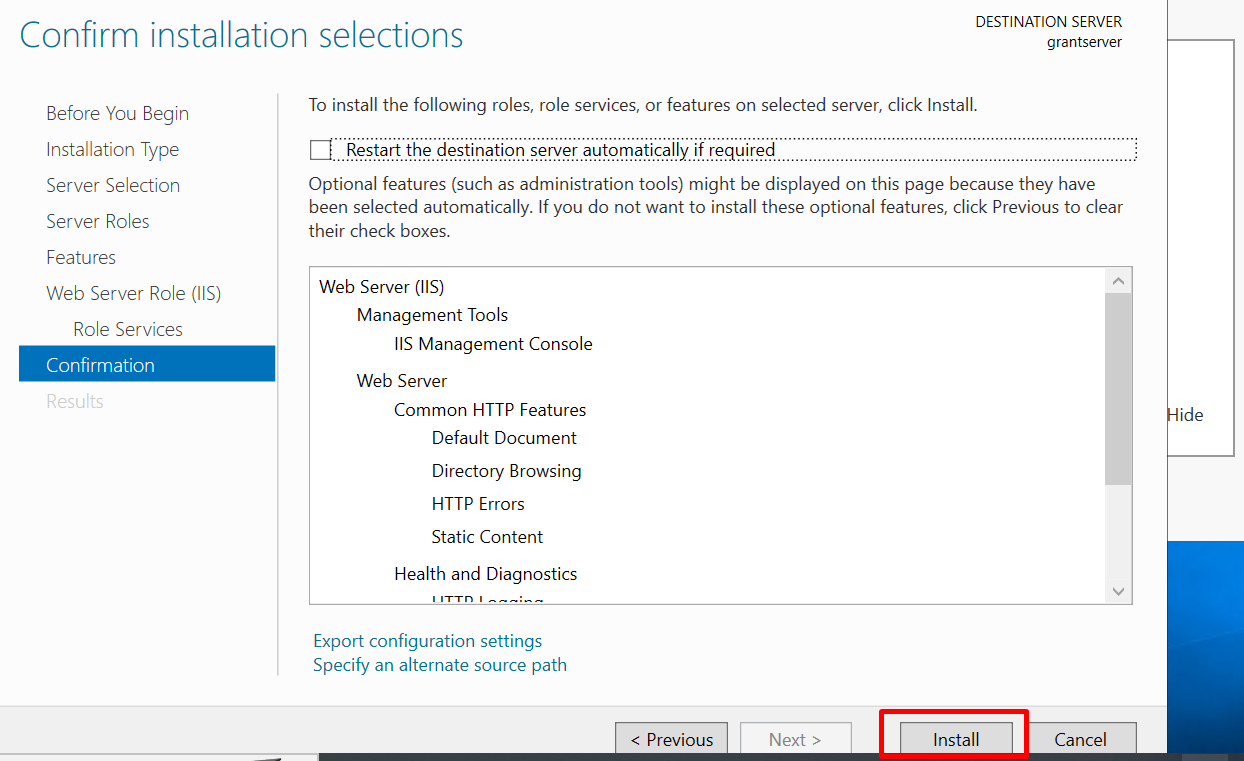
Step 7: Confirm Selections
On the "Confirm installation selections" page, click "Install" and wait for the installation to complete. Once it's done, click "Close"

CLICK ON VIRTUAL MACHINE

CLICK ON THE SERVER THAT HAS BEEN CREATED

SCROLL DOWN TO ASG

CLICK ON ADD ASG


GO TO THE VIRTUAL MACHINE AND COPY THE PUBLIC IP

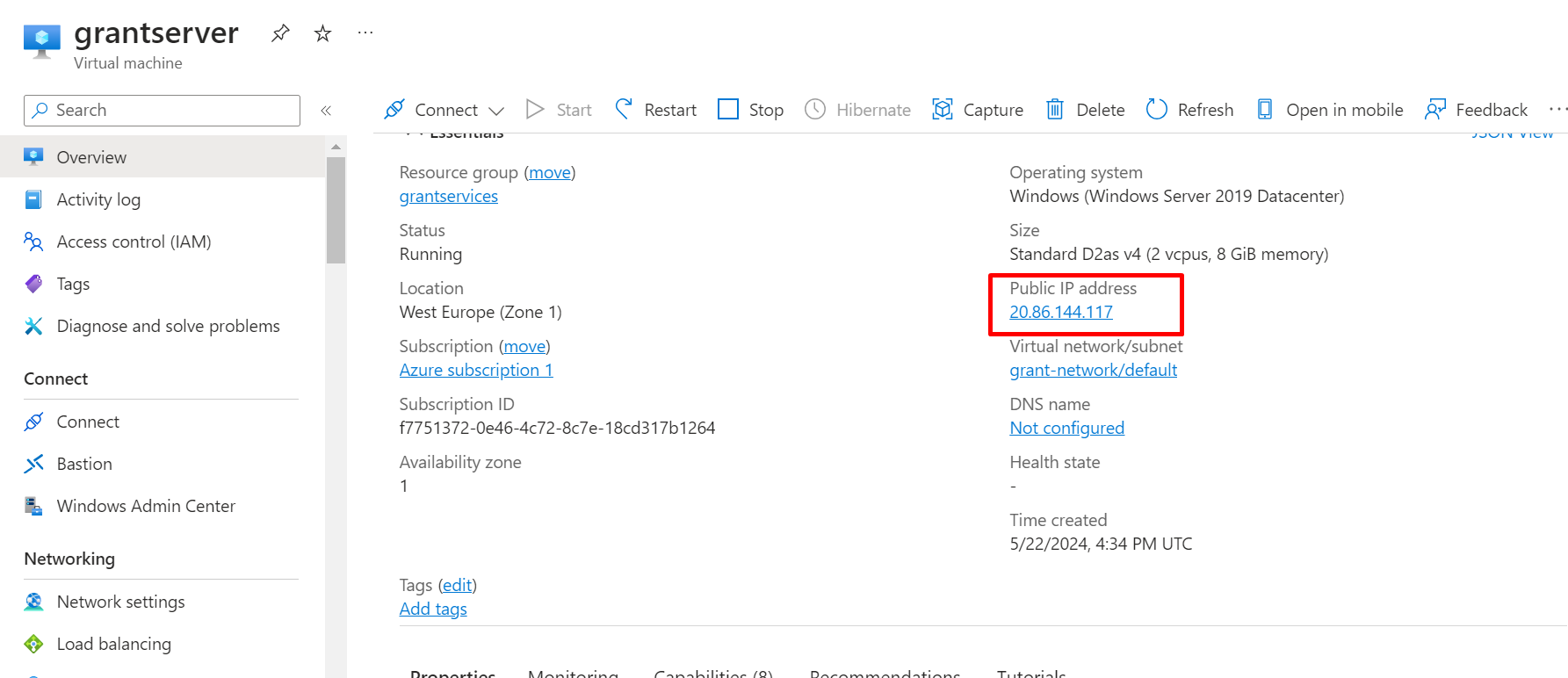
COPY THE IP AND PASTE IT INTO THE BROWSER
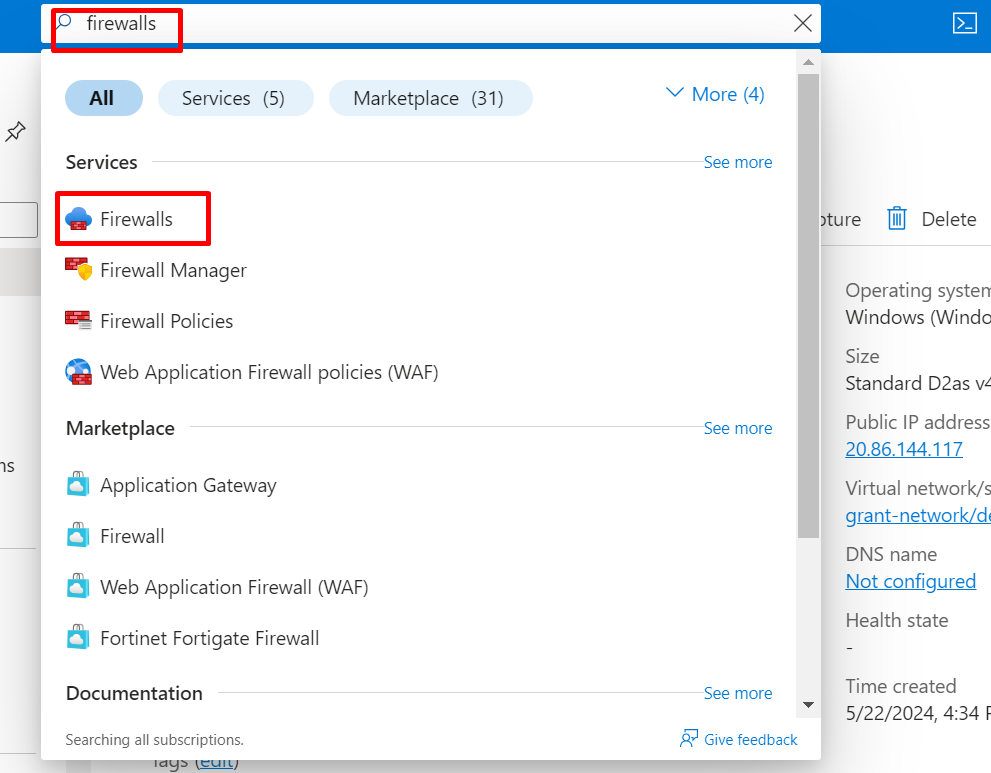
Create a firewall and attach it to the server's VNet to secure your environment from malicious threats.
GO TO THE SEARCH BOX AND SEARCH FOR FIREWALL
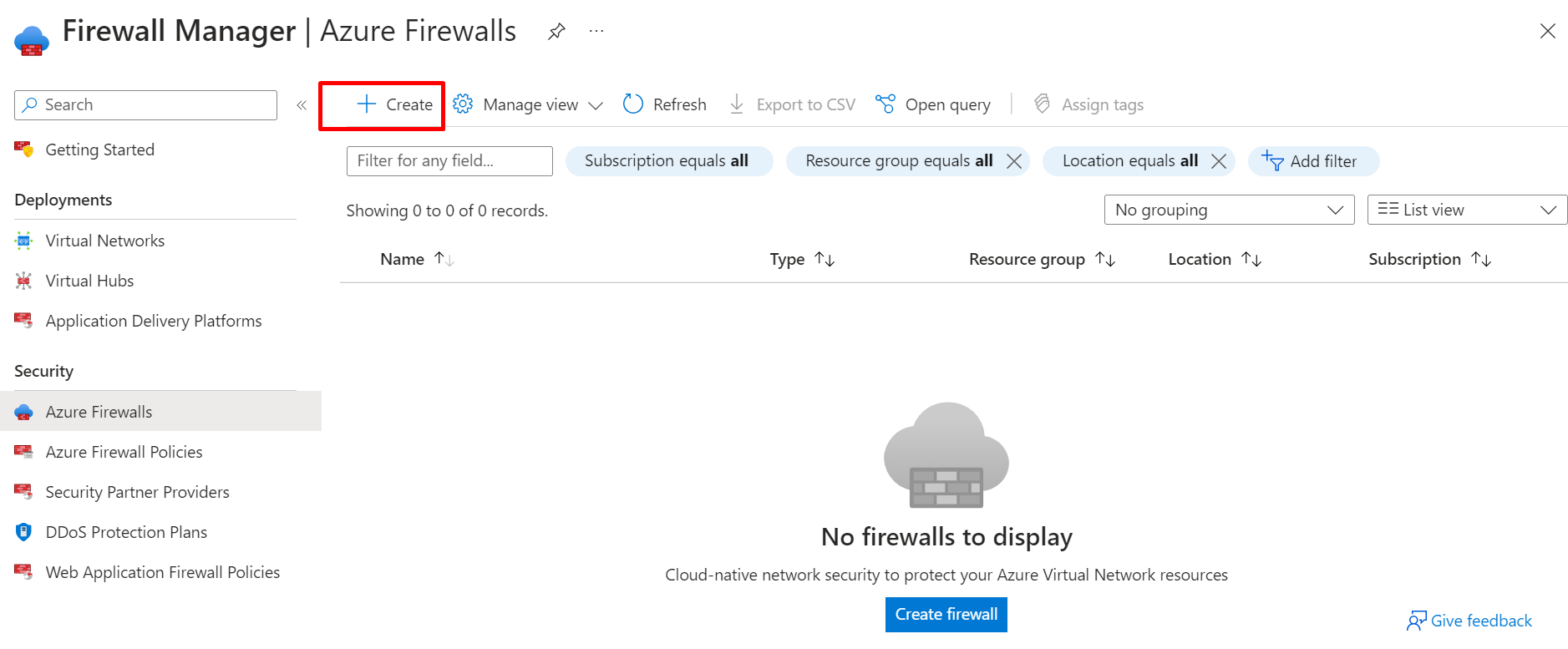
CLICK ON CREATE AND FILL IN THE INFORMATION


GO TO VIRTUAL NETWORKS
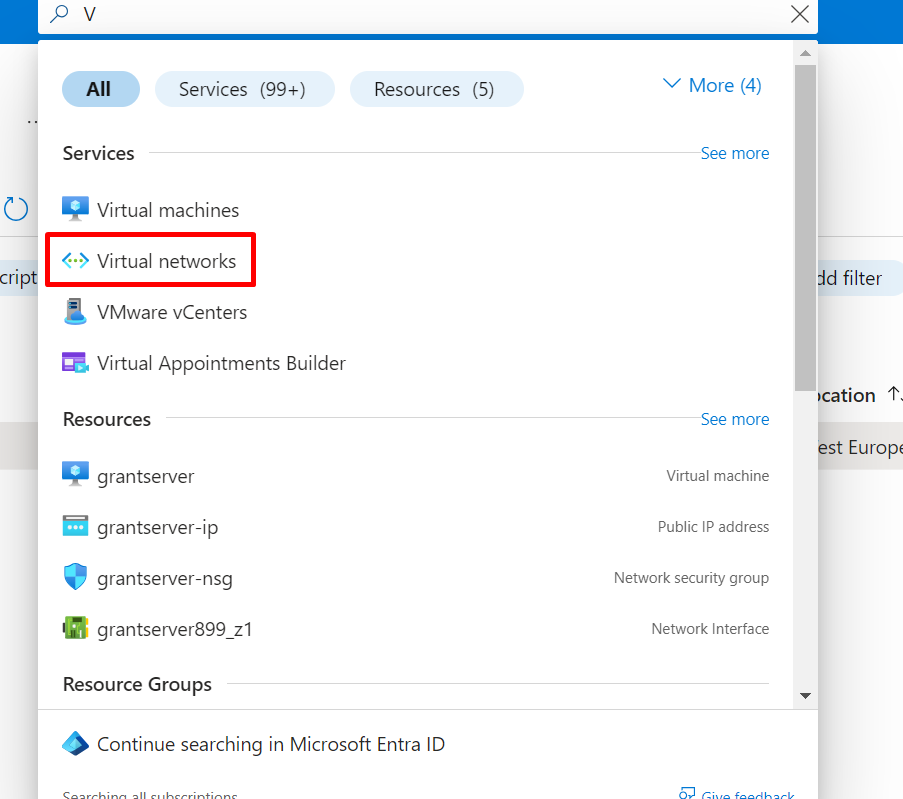
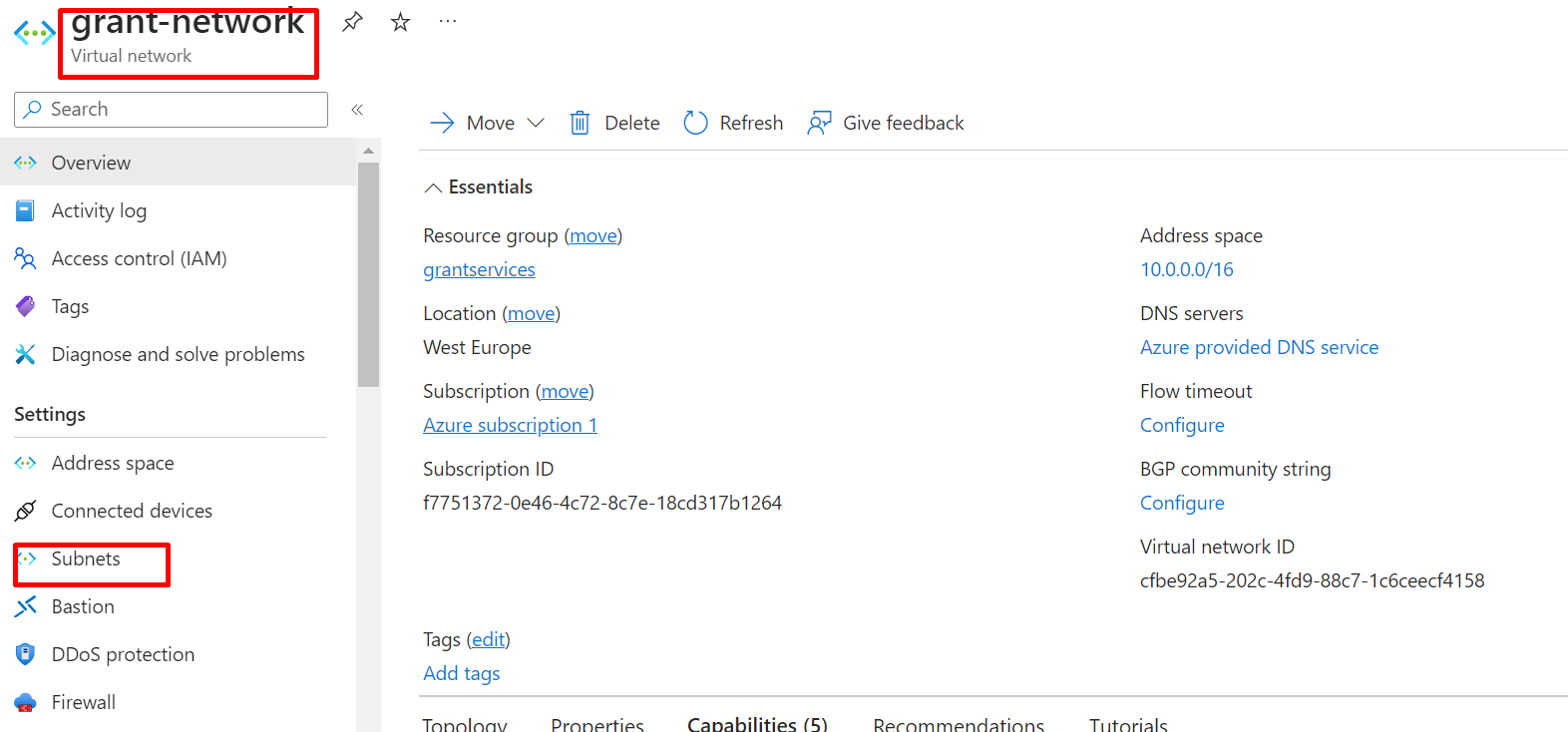
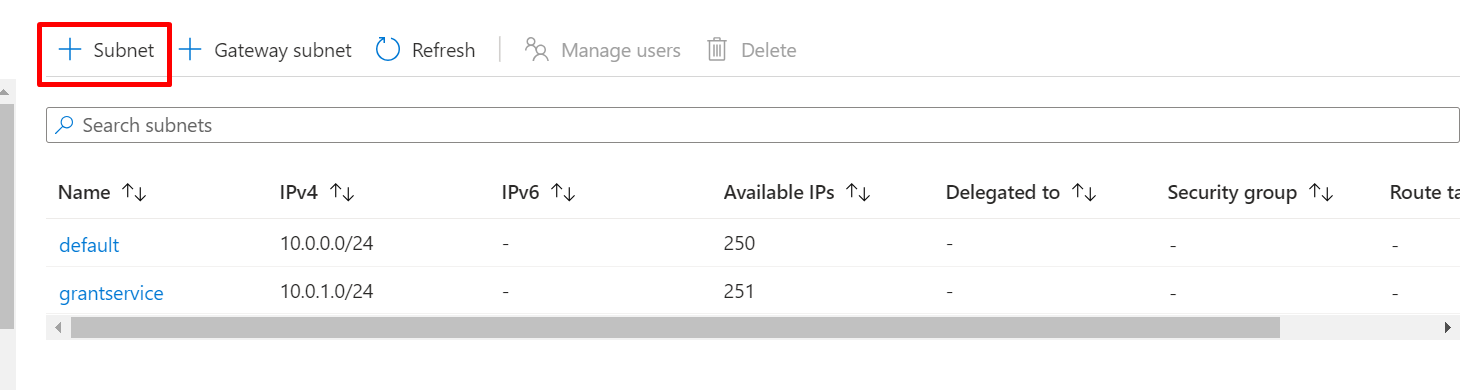
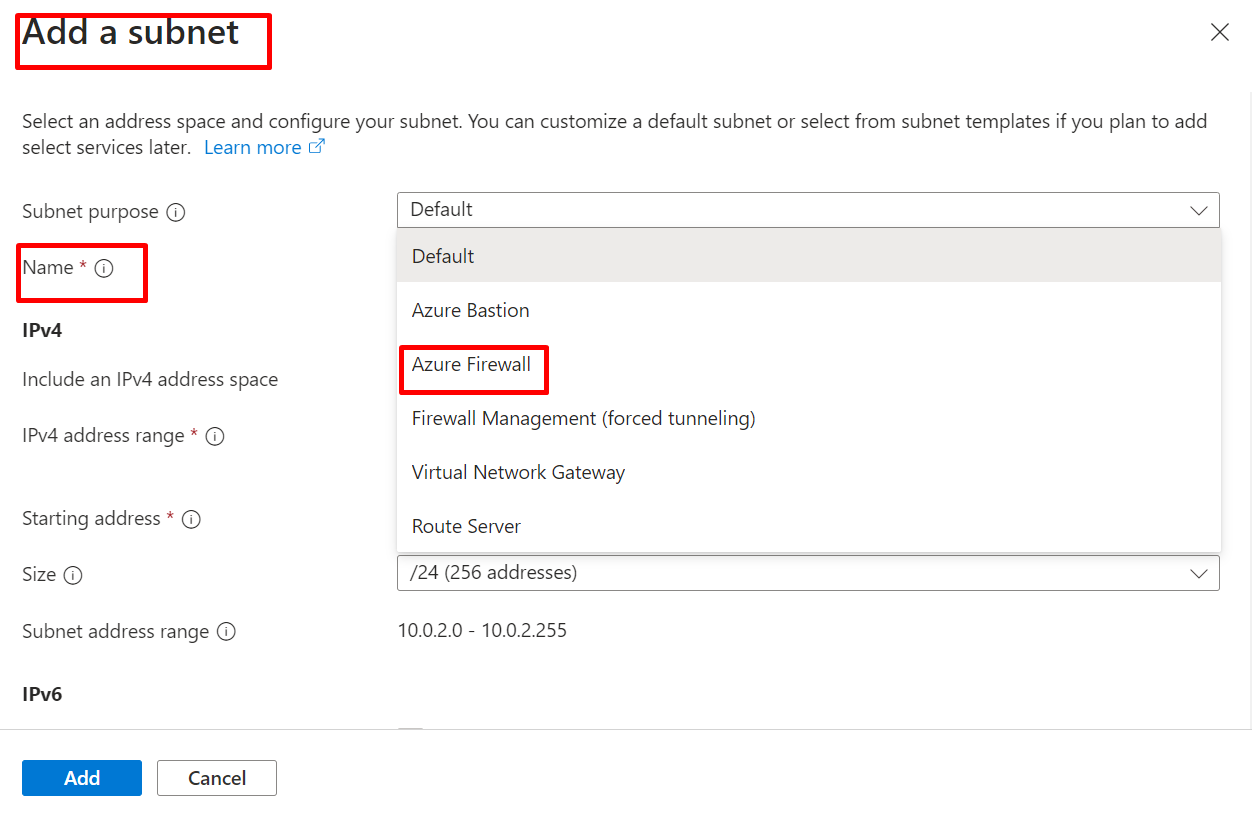




GO TO VIRTUAL NETWORK AND CLICK ON VNET



Summary
By leveraging ASGs, you can effectively manage and scale your network security configurations, making it easier to maintain a secure and well-organized cloud environment.
Subscribe to my newsletter
Read articles from Ibikunle ayobami directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
