Access and Refresh Tokens
 Adnan Ibrahim
Adnan Ibrahim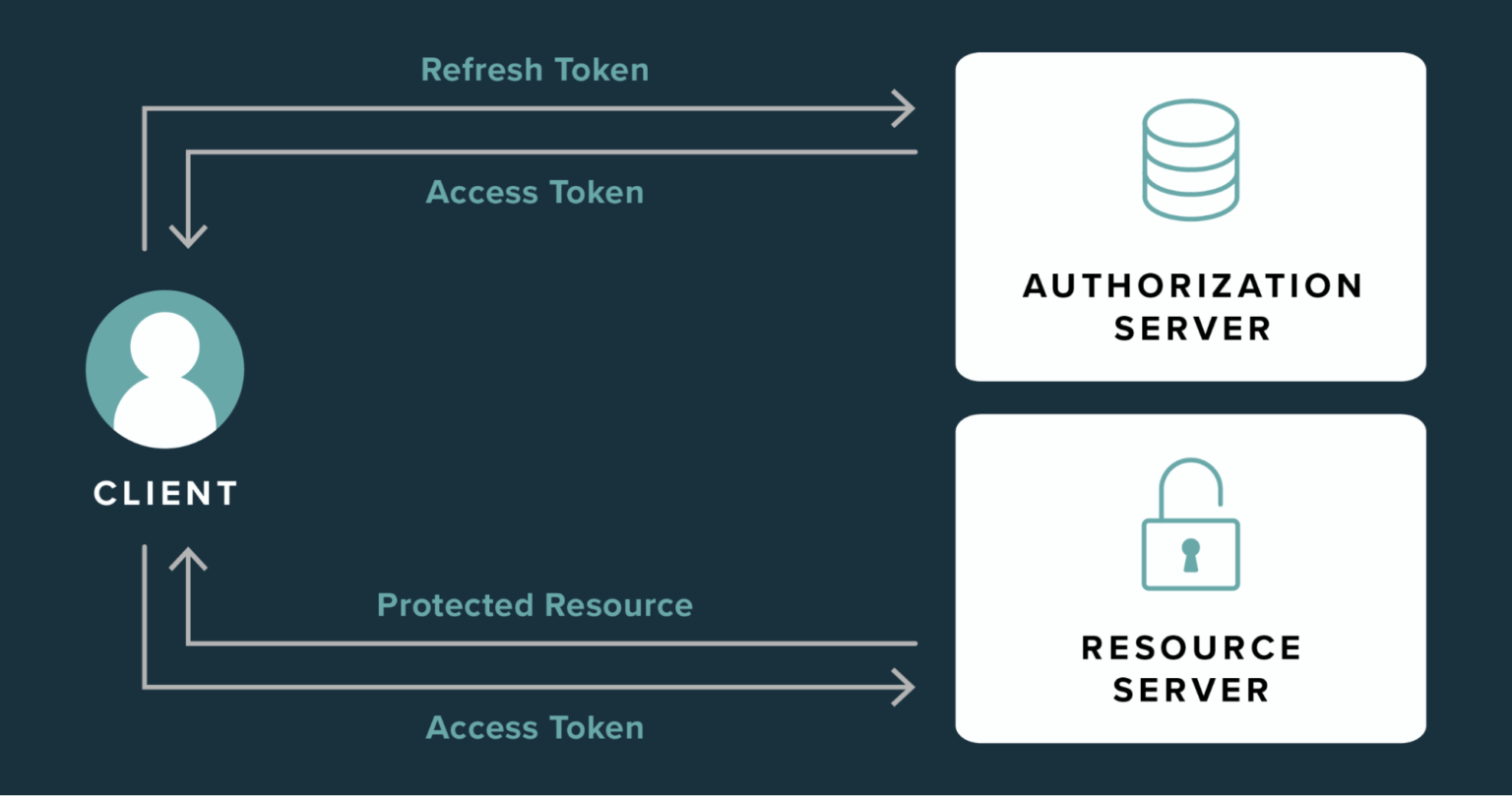
Introduction
In the digital world, security is crucial, especially when it comes to accessing sensitive information. To keep our data safe while allowing seamless access to applications, we use something called "tokens." Two important types of tokens are "access tokens" and "refresh tokens." Let's break down what these are and how they work.
What Are Tokens?
Tokens are like digital keys. Just as you need a key to enter your house, you need a token to access certain parts of an application or website. These tokens ensure that only authorized users can access specific information or service
Access Tokens
An access token is a short-lived token that grants permission to access specific resources or perform certain actions. Think of it as a temporary pass that allows you to enter a restricted area for a limited time.
How Does It Work?
Login: When you log in to an application, you provide your username and password.
Token Issuance: The application verifies your credentials and issues an access token.
Access Granted: You use this token to access different parts of the application. Each time you make a request (like viewing your profile or fetching data), you include the access token.
Expiration: Access tokens have a short lifespan, often lasting only a few minutes to a few hours. After it expires, you need a new token to continue accessing the application.
Why Short-Lived?
Access tokens are short-lived to reduce the risk if they are stolen. Even if someone else gets your token, they can only use it for a short period.
Refresh Tokens
What is a Refresh Token?
A refresh token is a long-lived token that can be used to obtain a new access token once the old one expires. Think of it as a membership card that allows you to renew your temporary pass without logging in again.
How Does It Work?
Issuance: When you first log in, you receive both an access token and a refresh token.
Renewal: When your access token expires, you can use the refresh token to request a new access token.
Validity: Refresh tokens last longer than access tokens, often days, weeks, or even months. However, they are typically stored securely and are not used frequently.
Security Benefits
Refresh tokens add an extra layer of security. Since they are long-lived, they are stored more securely (e.g., server-side). This way, your access can be refreshed without repeatedly asking you to log in, providing both security and convenience.
Subscribe to my newsletter
Read articles from Adnan Ibrahim directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
