AWS VPC (Virtual Private Cloud)
 Codefy Labs
Codefy Labs
In the vast landscape of cloud computing, Amazon Virtual Private Cloud (AWS VPC) acts as a magical realm for developers. Imagine creating a secure, isolated section of the Amazon Cloud that behaves exactly how you need it to. With AWS VPC, you can design your own virtual network environment, complete with custom IP address ranges, subnets, and security settings. This powerful tool allows you to deploy AWS resources in a private, confined space that operates almost like your personal data center, yet harnesses the scalability and power of AWS infrastructure.
Let's Dive into a Lab Exercise:
After exploring what AWS VPC can do, let's roll up our sleeves and dive into some hands-on work. We'll start by creating our own VPC, setting the stage for a practical demonstration of its capabilities. Follow along as we step through the process.
#Before we dive into creating our own VPC, let's first understand the key components of a VPC. This will give us a clearer picture of what we're building and how everything fits together.
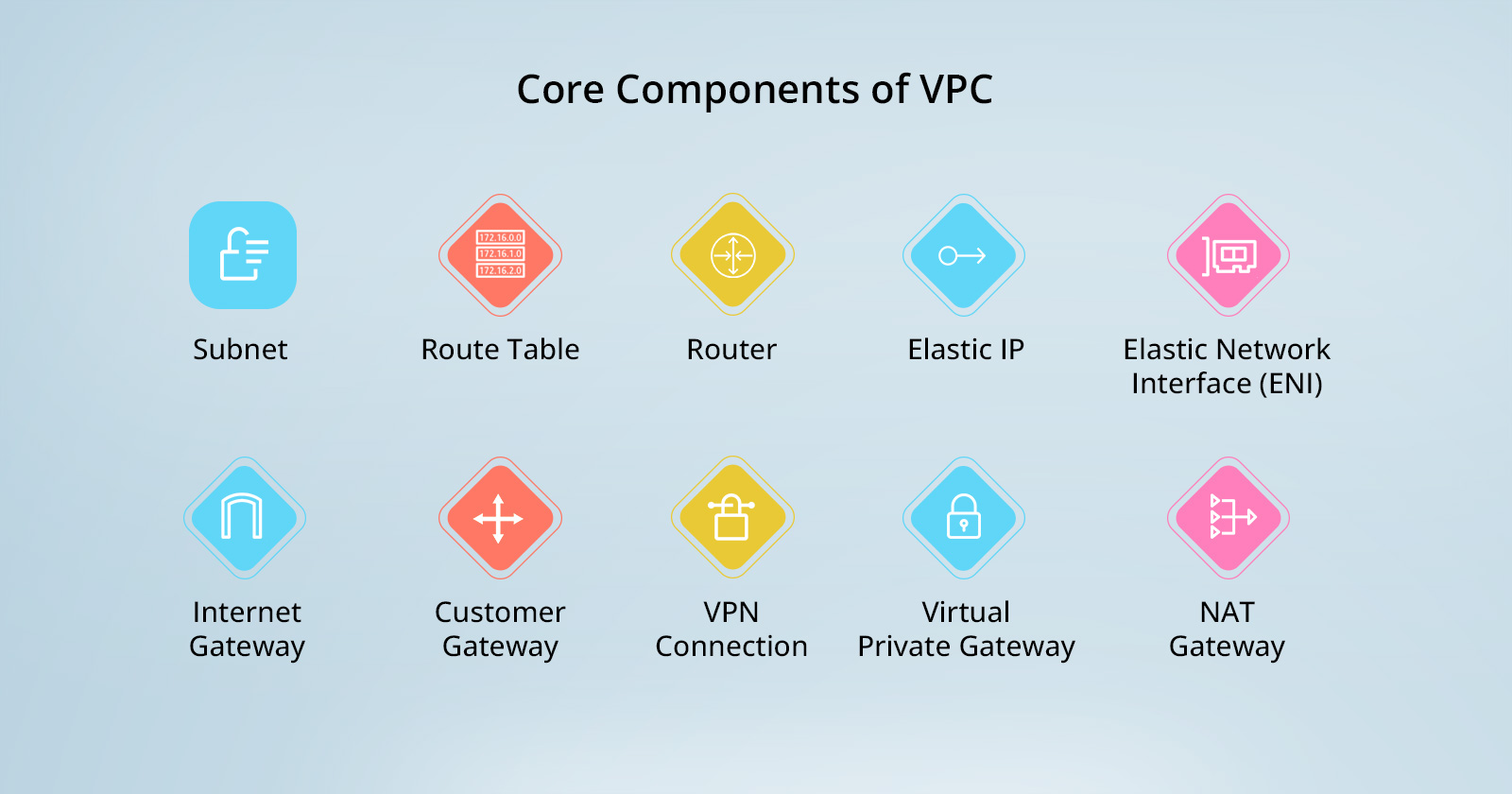
Subnet: A smaller, isolated part of your cloud network where you can place your resources.
Route Table: A set of rules that decide how traffic flows within your network and to the outside.
Router: Helps direct traffic inside your cloud network, like a traffic cop for data.
Elastic IP: A permanent internet address you can give to any resource, making it easy to reach.
Elastic Network Interface (ENI): A virtual plug that connects your virtual machines to the network, letting them talk to other machines.
Internet Gateway: A gateway that connects your cloud network to the wider internet, allowing data in and out.
Customer Gateway: A device or service in your place that connects securely to your cloud network.
VPN Connection: A secure tunnel from your place to your cloud network over the internet, keeping data safe while it travels.
Virtual Private Gateway: The part of your cloud network that connects to your VPN, serving as the door to your private network.
NAT Gateway: Lets your private resources access the internet without being accessed directly from the internet, keeping them safer.
Now let’s create a VPC :
we are going to create our VPC according to our High Availability project architect
In which we will be creating a Virtual Private Cloud (VPC) on Amazon Web Services (AWS) with public and private subnets. So, let’s get started.
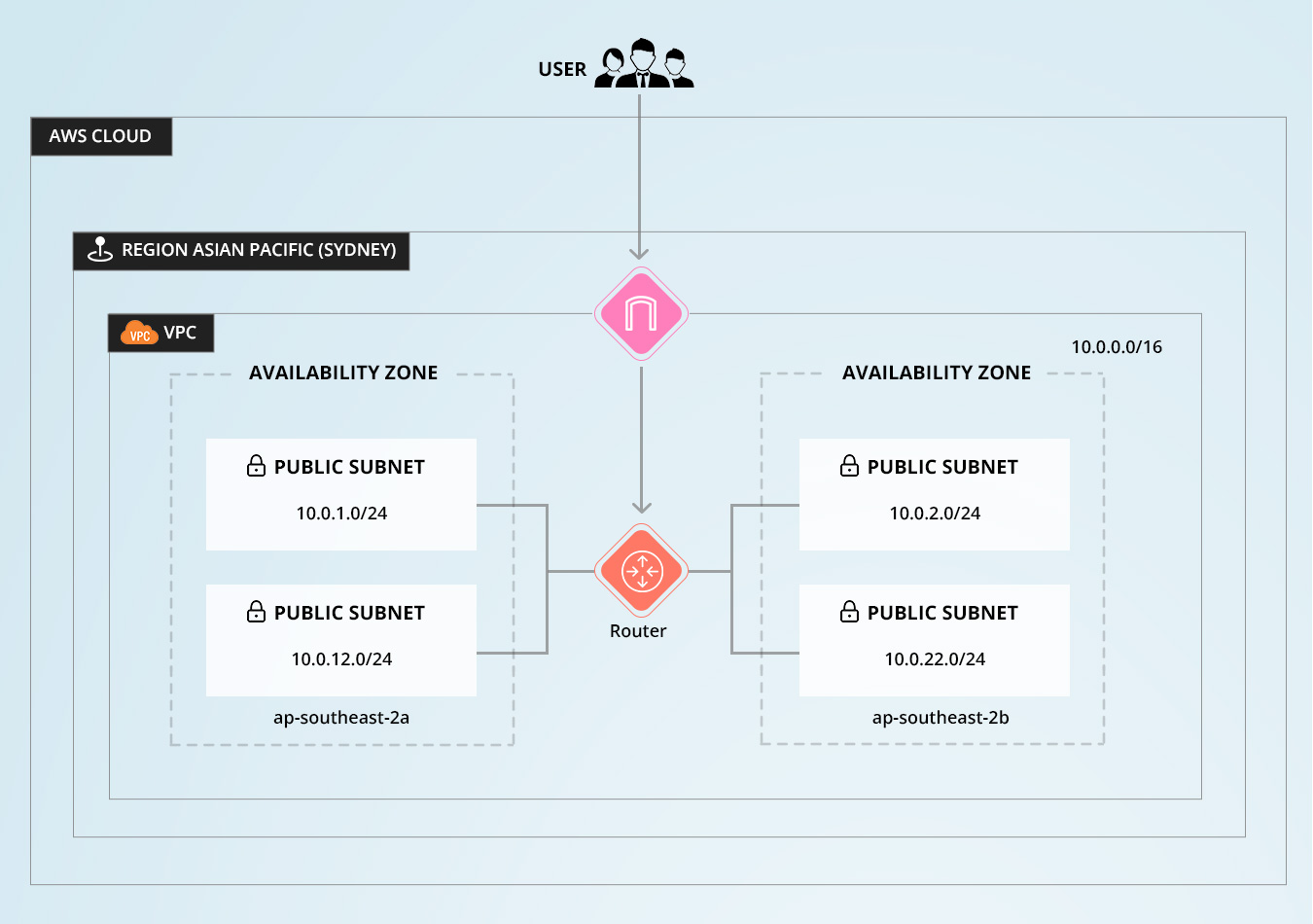
- In the search bar type VPC -> Create VPC -> VPC and more -> Name your VPC -> Add CIDR block 10.10.0.0/16
- Deploying subnets across multiple availability zones enhances the high availability and fault tolerance of your applications. By distributing your resources in this manner, if one availability zone experiences an outage, the remaining zones can continue to manage traffic and handle requests. This setup ensures that your application or service remains operational without disruption, providing a more reliable and resilient environment.
-create two availability zones (AZs) with public and private subnets and customize with
Public subnet : 10.0.1.0/24 , 10.0.2.0/24
Private subnet : 10.0.12.0/24 , 10.0.22.0/24
- If you want to create a NAT gateway, you can choose to deploy it in a single availability zone ('In 1 AZ') or across each availability zone ('1 per AZ'). If you do not require a NAT gateway, simply select 'None'. Additionally, if you wish to utilize an S3 Gateway for accessing services like S3 or DynamoDB directly through your VPC, choose the 'S3 Gateway' option.
- Create VPC
- After clicking on 'View VPC', you'll be presented with details of your VPC environment, including subnets and associated route tables. Here you can review the setup of each subnet, along with its connected route table and any linked internet gateways. If you find that adjustments are needed to better suit your project requirements, you can make those changes directly from this interface.
Route tables
In AWS VPC, route tables guide where network traffic goes. Each VPC has a default route table that you can change but not delete. You can also make custom route tables to manage traffic better for different areas of your network. If a subnet uses more than one route table, the rules in the more detailed table will be used when there's a disagreement.
In my AWS VPC setup, I've established two public and two private route tables to efficiently manage and secure network traffic. The public route tables are configured to allow traffic from the internet to the public subnets, facilitating external communication. On the other hand, the private route tables are designed to handle traffic within the network, ensuring that the data exchanged between the private subnets remains isolated from the outside world. This configuration helps maintain a robust and secure network environment.
Note : If you want to add NAT-GATEWAY
Route table for Private Subnet
Note: To automatically assign public IPv4 addresses to instances in this subnet, enable the 'Auto-assign public IPv4 address' option in the subnet settings.
- Internet gateway
Conclusion
In conclusion, configuring your AWS VPC and its components such as subnets and auto-assigning IP settings can greatly enhance the efficiency and security of your network. By understanding and utilizing these features effectively, you can ensure that your cloud environment is optimized for both performance and reliability.
Subscribe to my newsletter
Read articles from Codefy Labs directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Codefy Labs
Codefy Labs
We build products that scale