Security Groups and NACL in VPC - Part 2
 Rachana
Rachana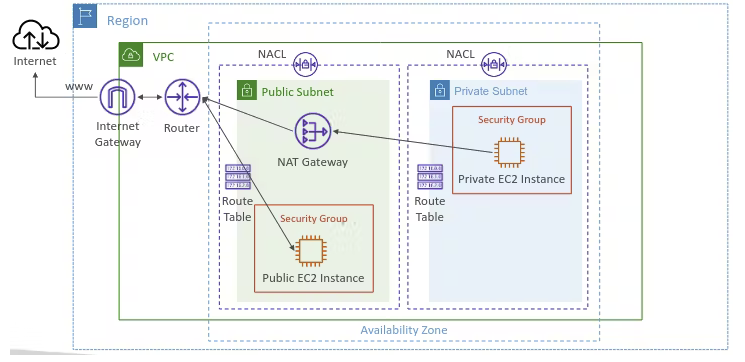
Imagine your cloud infrastructure as a high-tech office building. To keep everything secure, you need a combination of vigilant security guards and smart security gates. In AWS, these roles are played by Security Groups and Network Access Control Lists (NACLs). Let’s break down how they work together to keep your virtual office safe.
Security Groups: Your Personal Bodyguards
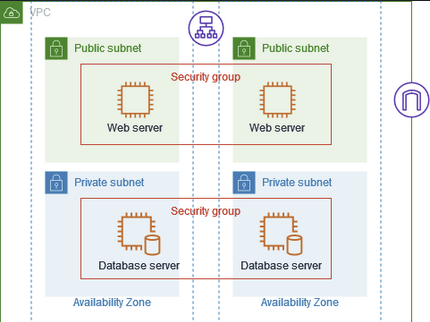
Think of Security Groups as the bodyguards for each room in your office building. They make sure that only the right people can enter and leave each room i.e., each EC2 instance.
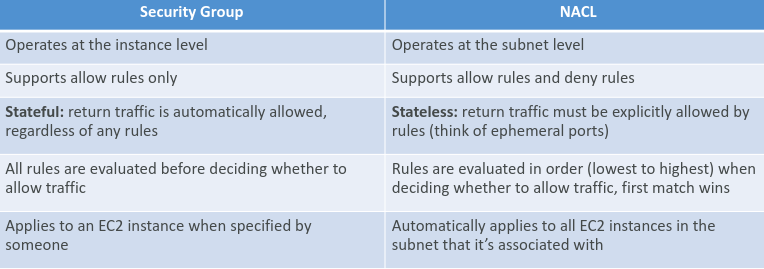
Instance-Level Security: Security Groups are assigned to specific rooms (EC2 instances) and control who gets in and out.
Stateful Inspection: If someone is allowed in (inbound rule), the bodyguard remembers them and lets them out (outbound rule) without checking again. It's like a VIP pass – once you're in, you can move freely.
Custom Rules: You can set rules to allow specific people (IP addresses) or services (ports) to enter and exit. Want to allow web traffic (HTTP) from anywhere? You got it. It can have 'Allow' rules only, so the IP addresses and ports which should be able to access the instances are allowed and any requests from other sources are denied.
Example Rules:
Inbound: Allow HTTP traffic (port 80) from everyone.
Outbound: Allow all outgoing traffic.
In essence, Security Groups at the instance level. And all rules are evaluated before deciding whether to allow traffic.
Network Access Control Lists: The Security Gates
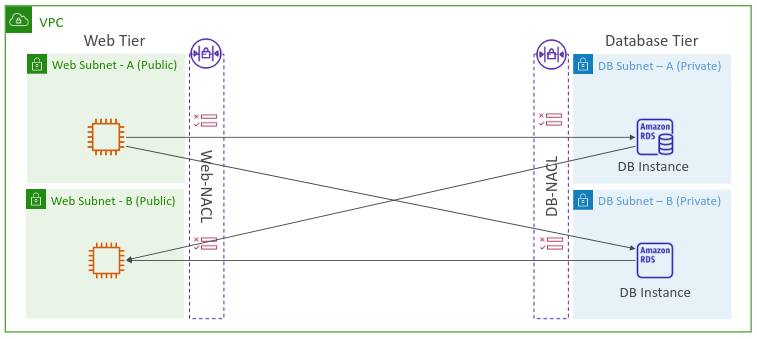
Picture Network ACLs as the initial checkpoint at your office building’s gates, filtering traffic before it even reaches the inner rooms. They control traffic flowing in and out of the entire building (subnets).
Subnet-Level Security: Network ACLs apply to whole floors or sections of your building (subnets), not just individual rooms.
Stateless Checks: Unlike the bodyguards, the security gates don’t remember who passed through. They check every entry and exit independently.
Sequential Rules: Rules are evaluated in order. The first rule that matches a visitor is the one that gets applied, so the order of rules matters. For example, if you define #100 ALLOW 10.0.0.10/32 and #200 DENY 10.0.0.10/32, the IP address will be allowed because 100 has a higher precedence over 200. The last rule is an asterisk (*) and denies a request in case of no rule match.
Unlike Security Groups, NACLs can have allow as well as deny rules, making it the best way to block a specific IP range.
By working together, NACLs and Security Groups provide robust, layered security, protecting your AWS resources from both broad and specific threats.
Subscribe to my newsletter
Read articles from Rachana directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rachana
Rachana
Hi to the fellow tech enthusiasts out there! 👋 I am an aspiring Cloud and DevOps Engineer ☁️ With strong foundation in containerization technologies like Docker and Kubernetes🐳 Capable of building resilient, secure and cost optimized infrastructure on AWS cloud - AWS SAA certified.☁️🔒 Currently learning to build CI/CD pipelines using Jenkins, github-actions, AWS CodePipeline, and many more.🛠️🔄 Exploring other tools like Ansible for configuration management and Terraform for Infrastructure as Code(IaC).🧩📜 Let's connect, learn and grow together! 🌟🤝