AWS Network & Security { Part - I }
 N Chandra Prakash Reddy
N Chandra Prakash Reddy
Security Groups
For protecting your cloud infrastructure, Amazon Web Services (AWS) offers an extensive toolkit. The Security Group is one of AWS security essential elements.
What are AWS Security Groups?
Your EC2 instances virtual firewalls, or AWS Security Groups, manage both incoming and outgoing traffic. They offer an option for deciding which protocols, IP ranges, and ports are permitted or prohibited to connect with your instances.
Key Features of Security Groups
Stateful Nature : Security groups are stateful, which means that regardless of outbound rules, if you approve an incoming request from a specific IP address and port, the response will also be approved.
Instance-Level Security : You can attach more than one Security Group to an instance. Every Security Group is linked to one or more instances.
Granular Control : You have exact control over the traffic on your network by being able to establish rules based on IP addresses, CIDR blocks, or even other Security Groups.
Dynamic Configuration : Modifications to Security Groups are instantly implemented, eliminating the need for your instances to reboot.
How Security Groups Work
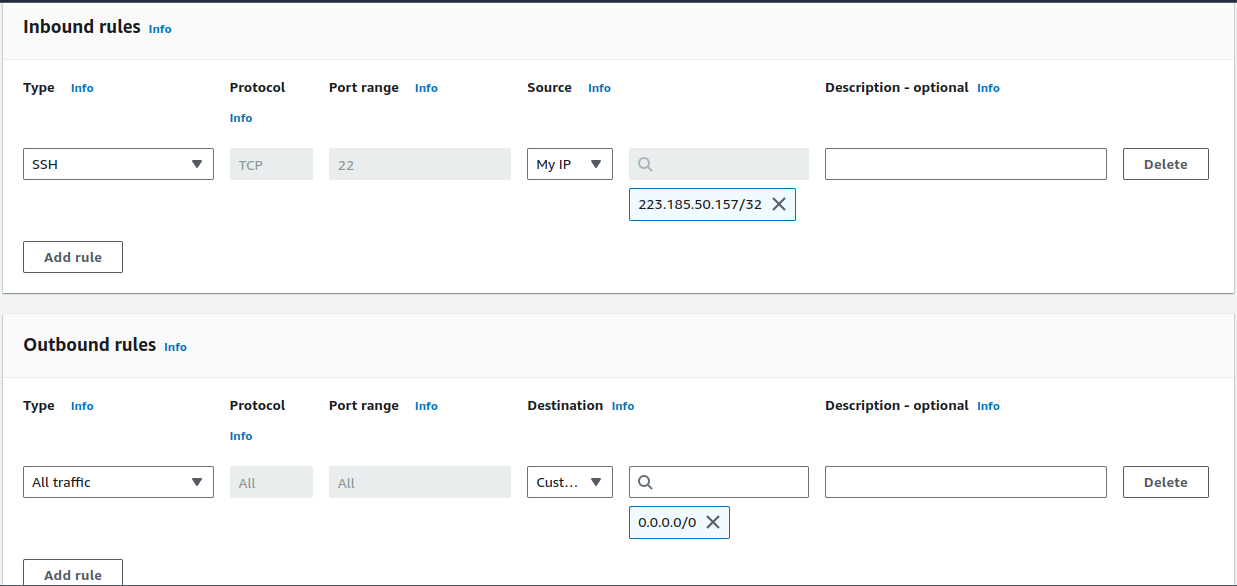
Inbound Rules :
- The inbound traffic to your instances is managed by these rules. You can choose the source (an IP address or another Security Group), the port range, and the type of traffic (such as HTTP or SSH).
Outbound Rules :
- The traffic that leaves your instances is managed by these rules. You can specify the type of traffic, the port range, and the destination, just like with inbound rules.
Creating a Security Group
Open the Amazon EC2 Console : Navigate to the EC2 dashboard in your AWS Management Console.
Select Security Groups: Under the Network & Security section, click on Security Groups.
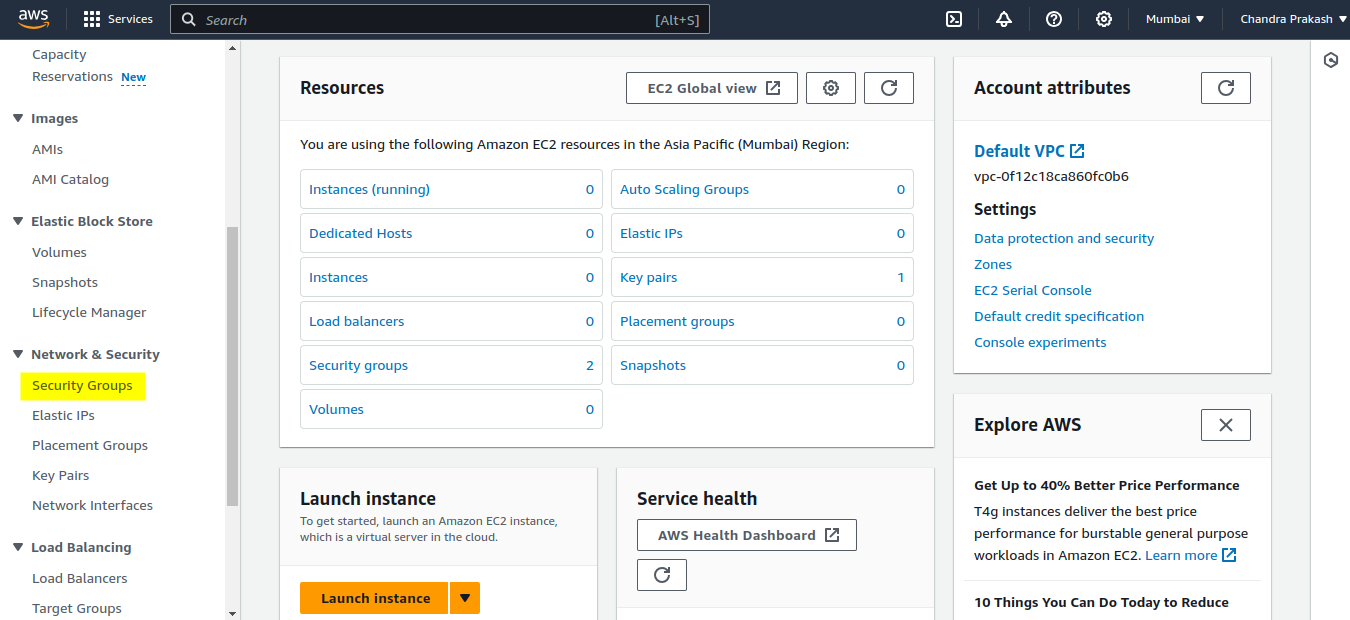
Create Security Group : Click on the Create Security Group button
Configure the Security Group :
Name and Description : Give your Security Group a name and a description.
VPC : Choose the Virtual Private Cloud (VPC) for your Security Group.
Add Inbound Rules : Define the inbound rules based on your requirements.
Add Outbound Rules : Define the outbound rules if necessary (the default allows all outbound traffic).
Review and Create : Review your settings and click Create Security Group.
Best Practices for using Security Groups
Least Privilege Principle : Permit only that traffic which is absolutely required. Stay away of extremely loose regulations.
Use Descriptive Names and Tags : To make maintenance easier, give your Security Groups clear names and tags.
Regular Audits : Make that your Security Groups are still required and configured correctly by reviewing them on a regular basis.
Group by Function : For simpler administration, create Security Groups according to the function of the instances (web servers, database servers, etc.).
Use VPC Flow Logs : Turn on VPC Flow Logs to keep an eye on traffic and spot any odd patterns or possible security problems.
Avoid Using 0.0.0.0/0 : If at all possible, avoid using 0.0.0.0/0 in your inbound rules as this exposes your instance to the public internet.
Restrict SSH Access : To securely access your instances, restrict SSH access to particular IP addresses or make use of a VPN.
Segregate Traffic : To reduce the possibility of spreading out within your network, use separate Security Groups for different types of traffic (such as web and database traffic).
Review Default Rules : Make sure you regularly review and adjust the default rules in your Security Groups.
Implement Network ACLs: Use Network Access Control Lists (ACLs) along with security groups to add another level of subnet protection.
Automation and Documentation : Utilize infrastructure-as-code solutions, such as AWS CloudFormation, to automate Security Group management. Keep thorough records of your security configurations and policies.
Limit Number of Rules : Limit the quantity of rules in every Security Group to prevent complications and possible errors in configuration.
Use Cases
Web Servers : For maintenance purposes, permit SSH traffic from your IP address and HTTP and HTTPS traffic from the internet.
Database Servers: Limit database port access (e.g., 3306 for MySQL, 27017 for MongoDB) to application servers located in the same virtual private cloud (VPC).
Load Balancers : Permit internet traffic to reach the load balancer ports and direct it towards the web servers.
Application Servers : All other traffic is restricted; only traffic from the load balancers on the application's chosen port is allowed.
Monitoring and Logging : Permit communication from particular IP addresses or VPCs to logging and monitoring services such as Prometheus, Grafana, or CloudWatch.
Bastion Hosts : To securely access other instances, create a Security Group that permits SSH access from a particular IP range and use it as a bridge.
- Bastion Hosts : A safe PC that serves as a link between your personal network and the internet is called a bastion host. It shields your internal servers from direct internet exposure while enabling trusted users to connect to them securely. This maintains the security of your network.
Conclusion
Powerful Tool for Network Security : In order to manage network security in your AWS environment, you must use AWS Security Groups.
Enhanced Security : The security of your cloud infrastructure can be greatly improved by knowing how they operate and following to best practices.
Versatility : Both basic web servers and complex multi-tier applications can benefit from Security Groups.
Control and Flexibility : They offer the flexibility and control required to successfully safeguard your resources.
Immediate Changes : Your security policies are updated quickly since Security Group modifications take effect right away.
Integration with Other AWS Services : Security Groups improve total security management by integrating with other AWS services with ease.
Cost-Effective : An affordable alternative to purchasing additional hardware or software for managing security is to use Security Groups.
Subscribe to my newsletter
Read articles from N Chandra Prakash Reddy directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

N Chandra Prakash Reddy
N Chandra Prakash Reddy
-> I'm an enthusiastic DevOps professional with over 3+ years of hands-on expertise in cloud infrastructure management and orchestrating the deployment of applications which are ready for production. -> Excellent problem-solving skills and a proactive learner, staying updated with the latest trends in DevOps and Cloud Computing. 𝐆𝐞𝐭 𝐢𝐧 𝐓𝐨𝐮𝐜𝐡 -> 𝐂𝐨𝐧𝐧𝐞𝐜𝐭 𝐨𝐧 𝐋𝐢𝐧𝐤𝐞𝐝𝐢𝐧 : If you're interested in engaging in technical discussions or connecting professionally, please feel free to connect with me on LinkedIn. -> 𝐄𝐦𝐚𝐢𝐥 : ncpr.0912@gmail.com