How To Stay Ahead of 99% Of Bug Bounty Hunters
 Om
OmHello Everyone, We know that bug bounty is growing popular day by day and many people are getting into this field which is great for the community but it also increases competition within the bug bounty hunters, and thus makes it harder to find bugs as they are already found by other hunters.
In this blog we will talk about some tips that can help you in findings bugs before others do !!
Let’s Begin !!!

1. Clear The Basics !
Before starting to hunt, it is very important to clear your BASICS, for example

Learn About Common Vulnerabilities
Learn about the most common vulnerabilities like SQL Injection (SQLi), Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and Server-Side Request Forgery (SSRF) and familiarize yourself with the OWASP Top Ten.
Here are some resources you can refer:
Web Application Hackers Handbook
Bug Bounty Bootcamp- By Vickie Li
Real-World Bug Hunting- By Peter Yaworski
https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters/blob/master/assets/basics.md
Programming

You must’ve heard people say you don’t need programming to start bug bounty and that’s what most of the people do, so if you want an upper hand I would suggest to learn at least the basics of programming languages so you can at least understand a code. And it can also Help in coding your own scripts.
These are the languages you can learn
Python
Bash
Javascript
You can find many resources for these on Youtube itself.
Security Tools
Get comfortable with using essential tools for example — Burpsuite ,Nmap , Owasp Zap. These will be very essential in your journey.
2. Understand The Application
This is a most common mistake many people do, Just select a target and start putting payloads into the inputs and expects to find bugs, and it even works sometimes, depends on your luck and the target. But if you want to find better bugs you need to understand the Application Properly.
First study the architecture of the application, including its backend, frontend, APIs, and any third-party integrations. This holistic view can help you identify weak points. There are many tools for this like Wappalyzer, BuiltWith Technology Profiler, WhatRuns.
You can also read the website manual or documentation if there is any because that is very important for an attacker to know their application from top to bottom.
Then Start using the website as a normal user and understand the flows and functionalities and note it down somewhere for example let’s take a website like tumblr.com,
On Opening the website first time we see a sign up and login option, let’s note it down.
We can also see the like, reblog, share and follow options, let’s note them down too.

We also see a search bar.
Now in similar way keep noting down stuff and try using everything and seeing how it works.
Note: Keep Your Burpsuite Open While Doing These All So That Your Site Map Keeps Filling Up
So now we have understood the application and have noted down the functionalities for example:
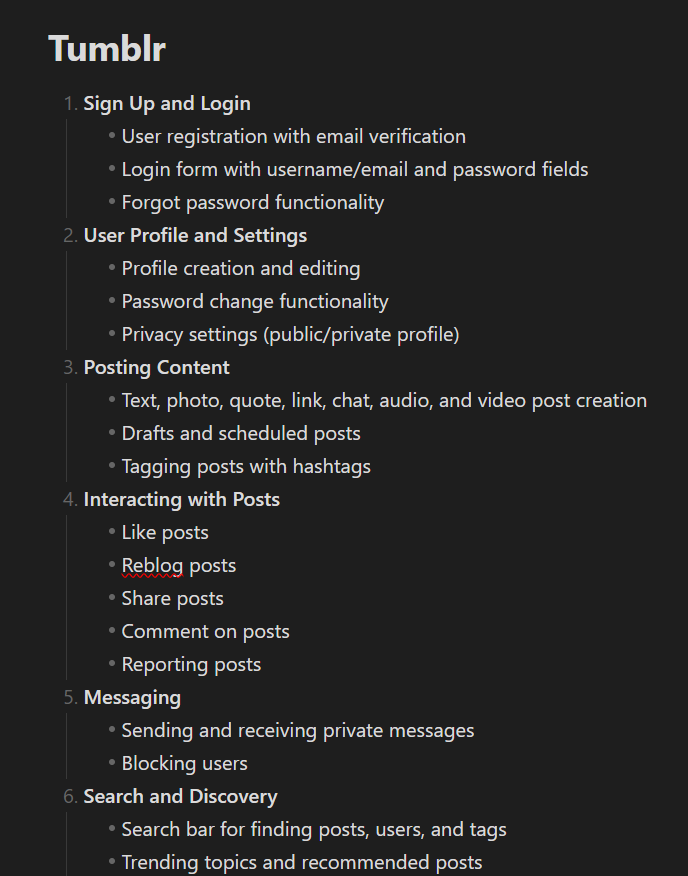
Now in the coming points we will see the use of this.
3. Reconnaissance

What many people do is skip the recon process or just run some common scripts like lazyrecon or just follows other peoples recon process, the problem there is 99% of the people are doing the same thing and if everyone is doing a same thing the probability of you finding the vulnerability first is going to be very less.
So you need to take recon seriously, Utilize every tool out there and create your own custom scripts using them which will also save you some time and you will also find some new things which other people are not able to find
For more detailed recon guide you can checkout this blog-https://medium.com/bugbountywriteup/what-to-do-after-choosing-a-target-part-01-bug-bounty-0e7eda23d324
But remember not to follow anything blindly, create your own recon process
4. Having An Attackers Mentality

This is the most important part to find vulnerabilities, you need to think like and attacker, from the above points you must have all the knowledge you need about the website and it’s functionalities so how do we put that to use?
Let’s see from an example, As we noted down all the functionalities of tumblr earlier, now what can we make out of it.
The first Functionality we had-
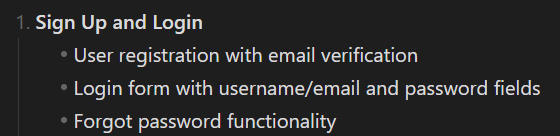
Now we need to think as an attacker and think what could be the potential vulnerabilities in these functionalities, you can use google, youtube for research and find ways to exploit these.
In this case the possible vulnerabilities could be —
SQL Injection in login form
Cross-Site Scripting (XSS) in error messages
Rate limiting bypass on login attempts
Email enumeration vulnerabilities
Weak password policy
CSRF in the password reset process
Now we can test all of these for all the functionalities one by one.
5. Manual Testing
Most of the people just run tools like nuclei, nikto and other automatic tools to find vulnerabilities, unless you are the first one to test on the target, it is very unlikely that you will find a bug through that.
It is not wrong to use automatic scanners, it is a very crucial part of bug hunting, but doing only that and expecting to find bugs is not good.
There are many reasons manual testing is essential
Manual testing allows you to bypass advanced protections and craft custom payloads
Automated tools may overlook complex vulnerabilities that require human intuition and understanding of the application’s logic
Manual testing enhances the quality of your findings by providing detailed proof-of-concept exploits
You can also use the automatic scanners in better way by just knowing what you are doing, for example in nuclei you can select custom templates, if you know your application properly and what language, libraries it is using you can utilize nuclei to its maximum.
You can also use automated tools for scanning particular vulnerabilities like mentioned above, for example one of the possible vulnerabilities in a login form could be sql injection so you could try to run sqlmap on the login form and the same for above vulnerabilities.
You can check my other blogs for detailed guide on manual testing.
6. Be Unique

This is the most important point in this whole blog, Be Unique and creative, many people just finds a checklist from google, or use some other persons methodology and start finding bugs, but to improve your own skills and to find more vulnerabilities you have to be unique. Let’s discuss some common practices most of the bug bounty hunters do which you can avoid-
- Thorough Reconnaissance:
What Most Do: Many hunters run basic automated reconnaissance tools and move on.
How to Stand Out: Prioritize in-depth reconnaissance to uncover hidden subdomains, endpoints, and assets. create your own custom scripts with the help of the available tools online using Generative AI’s to save your time and be more effective
2. Explore Lesser-Known Vulnerability Classes:
What Most Do: Focus on well-known vulnerabilities like XSS, SQLi, and CSRF.
How to Stand Out: Dive into more specialized areas such as deserialization issues, race conditions, SSRF , and web cache poisoning. These areas are often less crowded and can yield higher rewards.
3. Perform Deep and Thorough Testing:
What Most Do: Does surface-level testing using automated tools.
How to Stand Out: Go beyond initial scans by performing deep and thorough manual testing. Understand the application’s backend infrastructure, analyze its business logic, and test every input field, parameter, and API endpoint.
4. Detailed and Professional Reporting:
What Most Do: Submit basic reports with minimal detail.
How to Stand Out: Provide comprehensive, detailed reports that include a clear explanation of the vulnerability, step-by-step reproduction instructions, impact assessment, and remediation suggestions.
5. Stay Updated and Continuously Learn:
What Most Do: Stick to the same methods and knowledge base.
How to Stand Out: Keep yourself updated with the latest security trends, research, and attack techniques. Follow security blogs, read recent papers, participate in Capture The Flag (CTF) challenges.
6. Networking and Collaboration:
What Most Do: Work in isolation.
How to Stand Out: Engage with the bug bounty community, attend conferences, participate in forums, and collaborate with other hunters. Networking can provide you with new insights, tools, and techniques that you might not discover on your own.
7. Start With VDP’s
Begin your bug bounty journey with Vulnerability Disclosure Programs:
Less Competition: VDPs have less competition compared to bug bounty programs with monetary rewards. This can provide a better learning environment.
Experience Building: Participating in VDPs helps you gain experience, improve your reporting skills, and build a reputation within the security community.
Networking Opportunities: Engage with security teams and other hunters through VDPs. This can lead to valuable connections and learning opportunities.
Here is how you can find VDP’s
Bug Bounty Platforms: Check out HackerOne, Bugcrowd, Intigriti, and Open Bug Bounty.
Company Websites: Look for sections like “Security,” “Trust,” or “Responsible Disclosure.”
Securitytxt.org: Use securitytxt.org to find
security.txtfiles disclosing VDP details.Google Dorks: Utilize Google dorks to find VDPs and Bug Bounty Programs. Refer to this list of dorks.

That’s it for this blog, I hope it helped you in some way.
Please Provide feedbacks in the comment section, and I was also thinking to start a Youtube channel to showcase these things practically for better understanding, so please let me know if I should.
Feel free to connect with me on:
Thank you for reading till the end
Please Consider following and liking if you found it helpful.
Subscribe to my newsletter
Read articles from Om directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
