Understanding VPC Endpoints
 Rachana
Rachana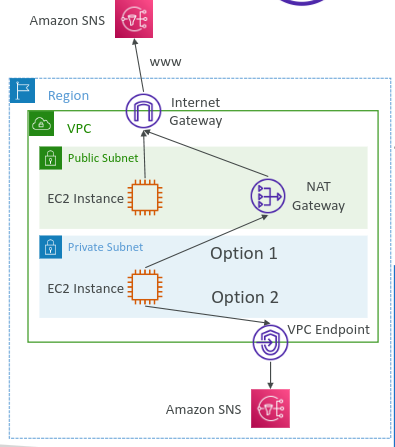
Have you ever wondered how to ensure secure and efficient communication between your AWS services? How can you keep data transfers private and reduce latency while avoiding the need for internet gateways and NAT gateways? Imagine your EC2 instances in VPC needs to retrieve data from S3, or your Lambda functions interacting with DynamoDB. How can these interactions remain within the AWS network, providing faster and more secure communication? The answer lies in leveraging VPC Endpoints. Let's explore how various AWS services can benefit from using VPC Endpoints to enhance security, performance, and simplify your architecture.
By default, every AWS service is publicly exposed through a public URL. However, VPC Endpoints allows you to connect to AWS services using a private network instead of the public Internet, enhancing security and performance.
By using VPC Endpoints, you can eliminate the need for Internet Gateways (IGWs), NAT Gateways (NATGWs), and other network components to access AWS services.
Types of VPC Endpoints
There are two main types of VPC Endpoints:
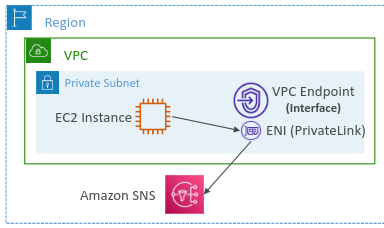
Interface Endpoints (AWS PrivateLink):
Connects to services using private IP addresses within your VPC.
Utilizes Elastic Network Interfaces (ENIs) within subnets.
Commonly used for AWS services like EC2, ECS, CloudWatch.
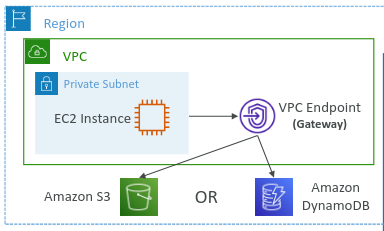
Gateway Endpoints:
Specifically used to connect to Amazon S3 and DynamoDB.
Provides a target in your route table that directs traffic to the specified AWS service.
Free of cost.
Setting Up a Gateway Endpoint for S3
Create a VPC:
- Ensure you have a VPC set up. For this example, assume we have a VPC with CIDR
10.0.0.0/16.
- Ensure you have a VPC set up. For this example, assume we have a VPC with CIDR
Configure Subnets:
- Create subnets within your VPC. Assume
SubnetAwith CIDR10.0.1.0/24.
- Create subnets within your VPC. Assume
Create the Gateway Endpoint:
Go to the VPC console.
In the left navigation pane, choose "Endpoints" and then "Create Endpoint".
Select "AWS services" for the service category and choose "com.amazonaws.<region>.s3" as the service name.
Choose the VPC and subnets you want the endpoint to connect to.
Specify the route tables to associate with the endpoint. This updates the route tables to include a route to S3 using the endpoint.
Update Route Tables:
- The route table associated with the selected subnets will automatically get a route added for S3 traffic.
Example : Lambda Functions and DynamoDB
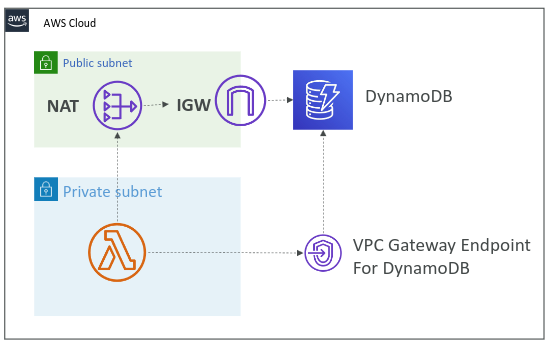
Using a Gateway Endpoint for connecting Lambda functions to DynamoDB is preferred due to its cost efficiency, simplicity, built-in scalability, and enhanced security. Gateway Endpoints provide a straightforward and economical way to ensure secure and efficient communication between your AWS services, keeping your architecture both robust and easy to manage.
Subscribe to my newsletter
Read articles from Rachana directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rachana
Rachana
Hi to the fellow tech enthusiasts out there! 👋 I am an aspiring Cloud and DevOps Engineer ☁️ With strong foundation in containerization technologies like Docker and Kubernetes🐳 Capable of building resilient, secure and cost optimized infrastructure on AWS cloud - AWS SAA certified.☁️🔒 Currently learning to build CI/CD pipelines using Jenkins, github-actions, AWS CodePipeline, and many more.🛠️🔄 Exploring other tools like Ansible for configuration management and Terraform for Infrastructure as Code(IaC).🧩📜 Let's connect, learn and grow together! 🌟🤝