Sitecore Identity Server Behind TLS Termination Proxy
 Łukasz Zięba
Łukasz Zięba
Sitecore deployments can include TLS termination proxy between end user and the origin server, which decrypts incoming HTTPs traffic and forwards it further over plain HTTP. The main benefit is that origin server is offloaded from decryption and can focus on handling web application requests.
Let's consider scenario where Sitecore Identity Server is running on the webserver (IIS) over HTTP, whereas it is accessible via HTTPS by end users in the browser. In typical Sitecore configuration, following error may occurs after entering users credentials on Identity Server login page:
JWT token validation error: "IDX10205: Issuer validation failed. Issuer: 'https://sitecoreIdentityServer'. Did not match: validationParameters.ValidIssuer: 'http://sitecoreIdentityServer' or validationParameters.ValidIssuers: 'null' or validationParameters.ConfigurationManager.CurrentConfiguration.Issuer: 'Null'. For more details, seehttps://aka.ms/IdentityModel/issuer-validation. "
Adding PublicOrigin Setting
Mentioned error comes from protocol mismatch and the easiest way to fix it is to set in Config\Sitecore.IdentityServer.Host.xml file <PublicOrigin> value to the Identity Server URL with HTTPS schema.
<Settings>
<Sitecore>
<IdentityServer>
<PublicOrigin>https://sitecoreIdentityServer</PublicOrigin>
....
</IdentityServer>
</sitecore>
</settings>
The <PublicOrigin> is not documented anywhere, however quick look into Sitecore.Plugin.IdentityServer dll shows that PublicOrigin value is assigned to Origin property of Duende.IdentityServer.Services.IServerUrls class which then is used by Duende IdentityServer.
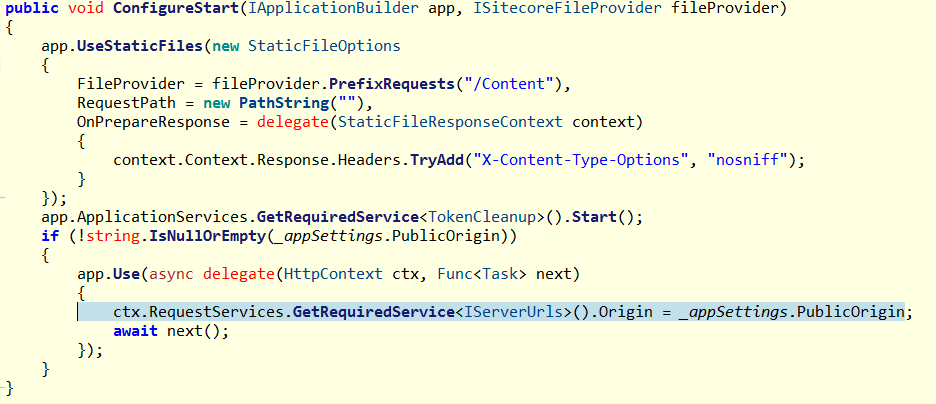
Using <owin.identityProviders> pipeline
It may be the case as well that Content Management instance is running over TLS termination proxy. In this case there may be redirect URL mismatch resulting in validation error on Identity Server side. In order to come around this issue it is possible to override <owin.identityProviders> pipeline processor which configures Identity Providers.
Protocol can be replaced in RedirectToIdentityProviderAsync method which redirects to Identity Server in order validate JSON Web Tokens. We would need to simply replace in redirect URL http with https and we are good.
namespace Feature.IdentityServer.Processors
{
using System.Threading.Tasks;
using Microsoft.IdentityModel.Protocols.OpenIdConnect;
using Microsoft.Owin.Infrastructure;
using Microsoft.Owin.Security.Notifications;
using Microsoft.Owin.Security.OpenIdConnect;
using Sitecore.Abstractions;
using Sitecore.Owin.Authentication.Configuration;
using Sitecore.Owin.Authentication.IdentityServer.Pipelines.IdentityProviders;
public class ProxyAwareIdentityProviderProcessor : ConfigureIdentityServer
{
public ProxyIdentityProviderProcessor(FederatedAuthenticationConfiguration federatedAuthenticationConfiguration, ICookieManager cookieManager, BaseSettings settings, BaseLog log)
: base(federatedAuthenticationConfiguration, cookieManager, settings, log)
{
}
protected override async Task RedirectToIdentityProviderAsync(RedirectToIdentityProviderNotification<OpenIdConnectMessage, OpenIdConnectAuthenticationOptions> notification)
{
await base.RedirectToIdentityProviderAsync(notification);
if (notification.ProtocolMessage.RedirectUri?.StartsWith("http://") == true)
{
notification.ProtocolMessage.RedirectUri = notification.ProtocolMessage.RedirectUri.Replace("http://", "https://");
}
}
}
}
<configuration xmlns:patch="http://www.sitecore.net/xmlconfig/">
<sitecore>
<pipelines>
<owin.identityProviders>
<processor id="SitecoreIdentityServer">
<patch:attribute name="type">Feature.IdentityServer.Processors.ProxyAwareIdentityProviderProcessor, Feature.IdentityServer</patch:attribute>
</processor>
</owin.identityProviders>
</pipelines>
</sitecore>
</configuration>
Subscribe to my newsletter
Read articles from Łukasz Zięba directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Łukasz Zięba
Łukasz Zięba
Works with Sitecore since version 6.4. Writes about Sitecore, web security and web performance. Likes to explore the unexplored.