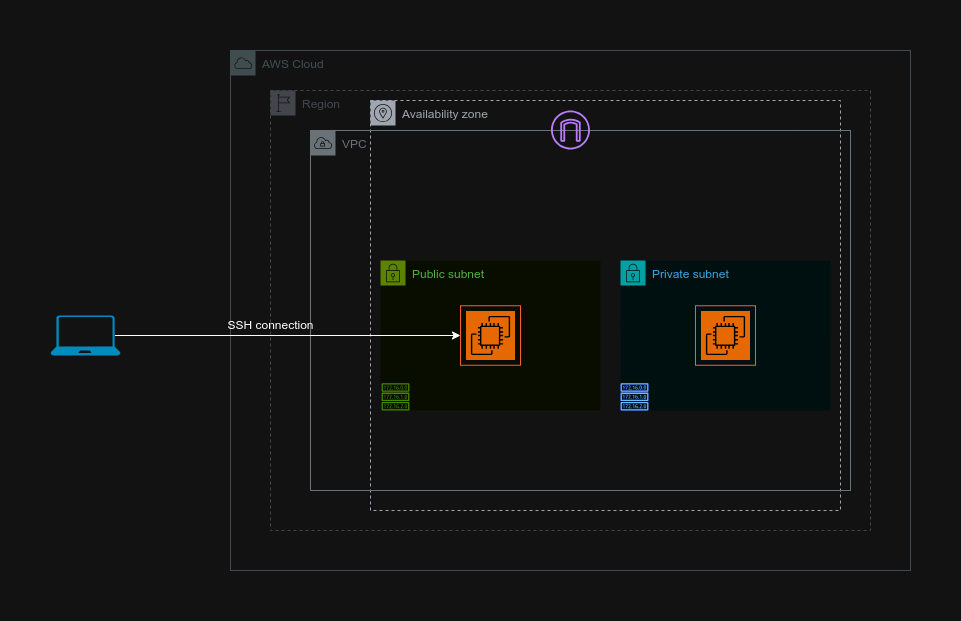
Bastion Host
 SUJAN
SUJAN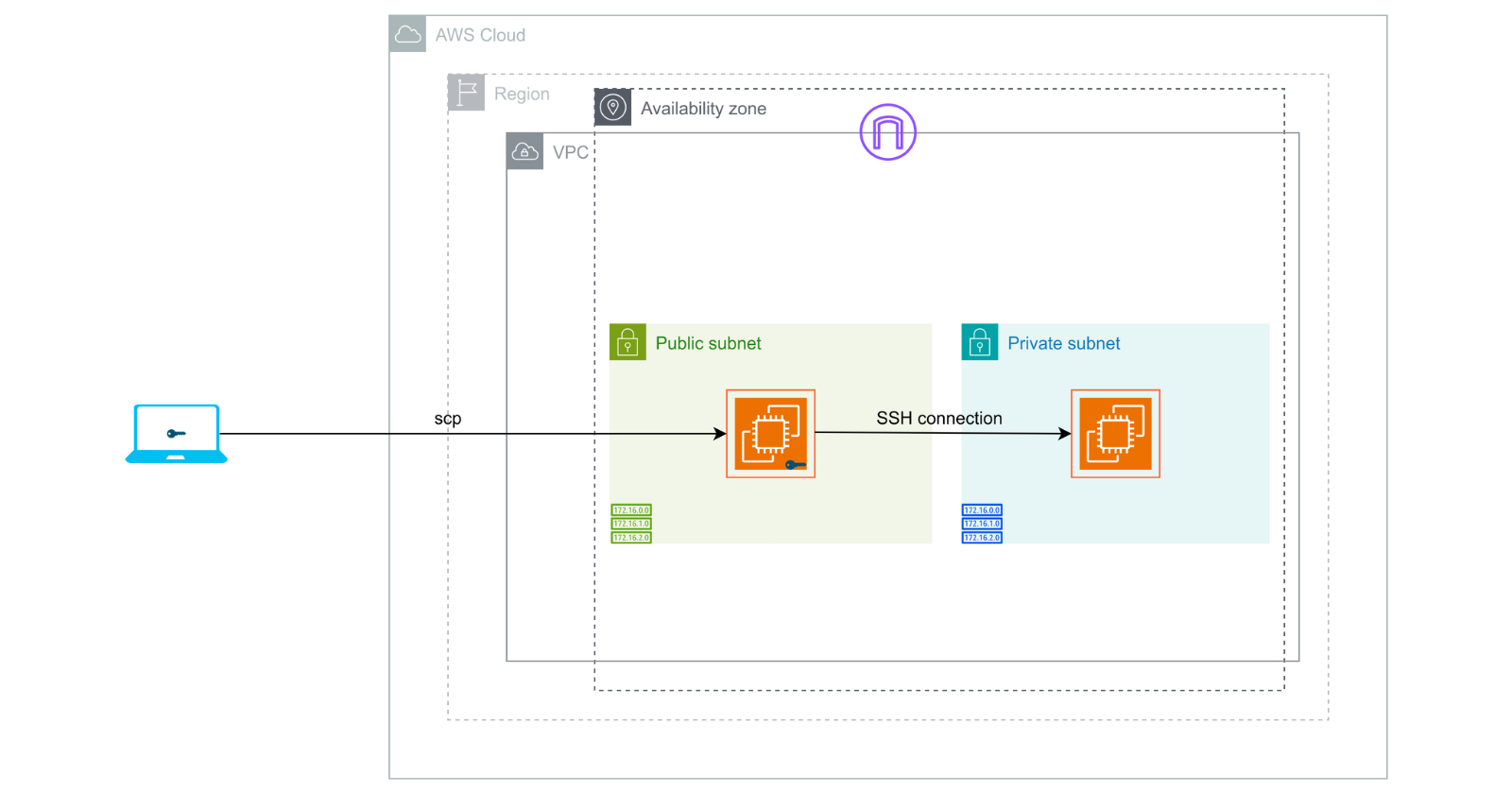
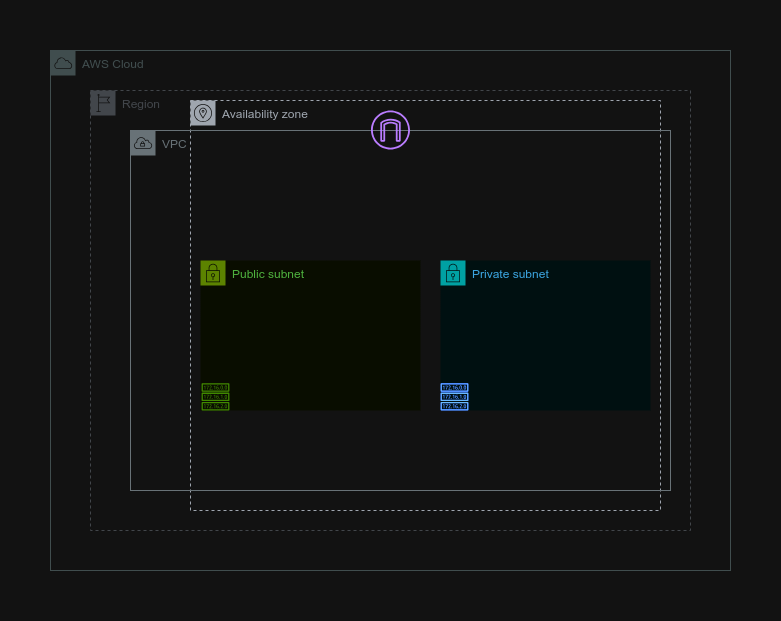
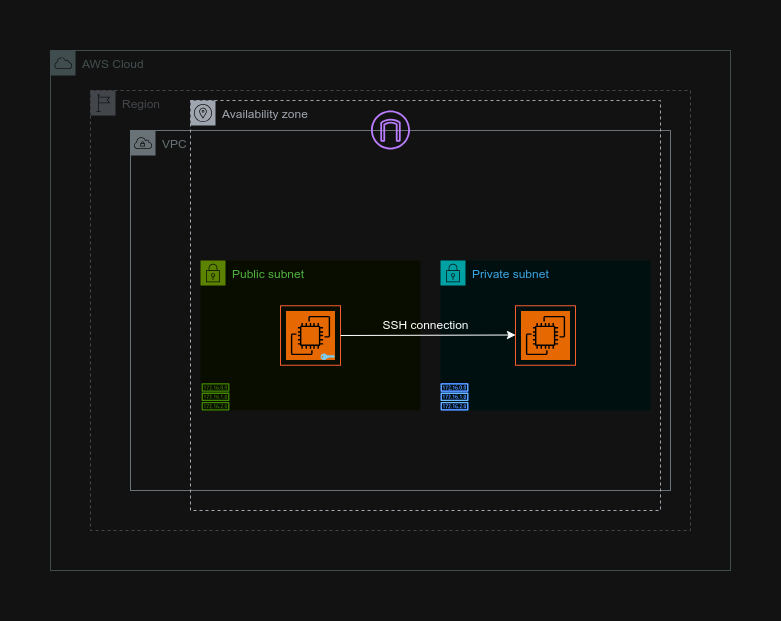
Today, we'll create a Bastion Host, a secure gateway, in our Virtual Private Cloud (VPC). This host will act as a bridge, allowing us to securely access our private instances located in the VPC's private subnet.
Let's dive in right away.
Analogy
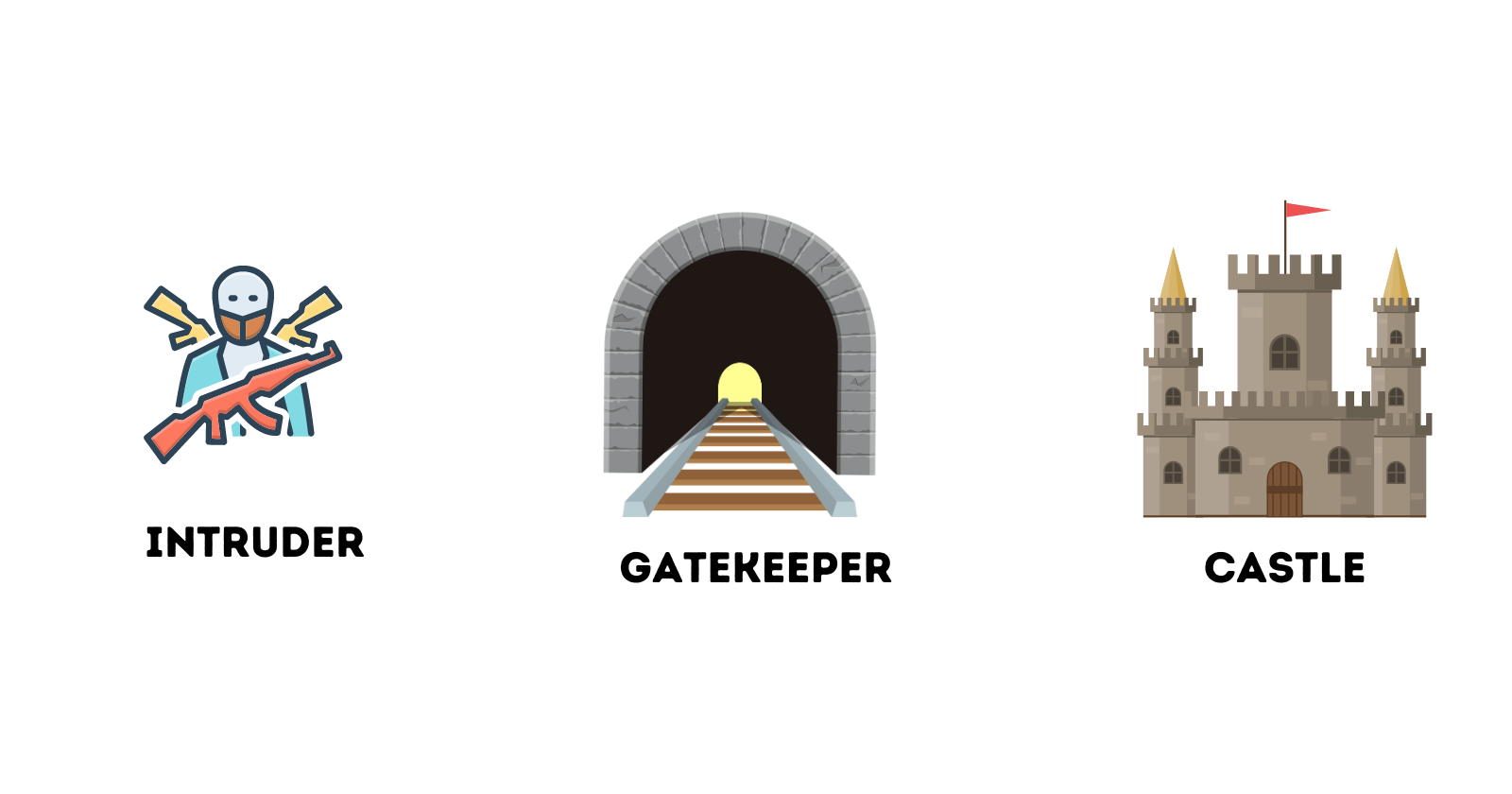
A bastion host is like a secure gatekeeper for your network, ensuring no one can bypass it to get inside. It checks everyone's identity and keeps a record of all entries, allowing only authorized users. With minimal features to reduce risks, it is well-protected against attacks, acting like a vigilant gatekeeper monitoring and controlling access to the castle.
Task 1: Create a VPC
Search for VPC in the search box.
Click on Create VPC.
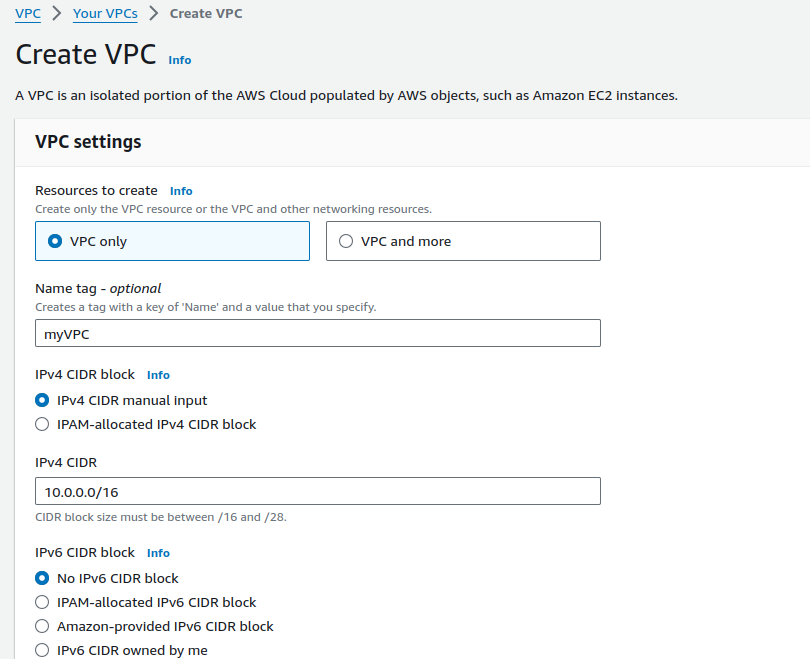
Provide a suitable name for your VPC and provide CIDR range.
Leaving all other configurations as default, Click on Create VPC.
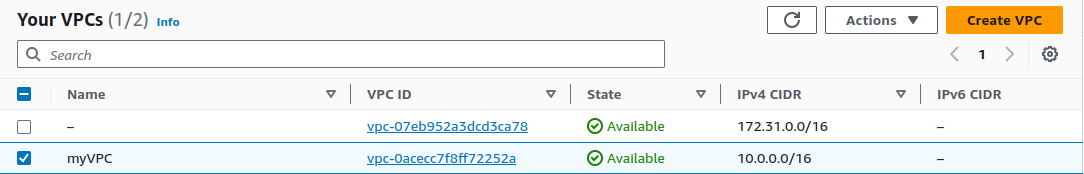
Our VPC is created.
Task 2: Creating an Internet Gateway
Internet Gateway to provide our VPC internet access.
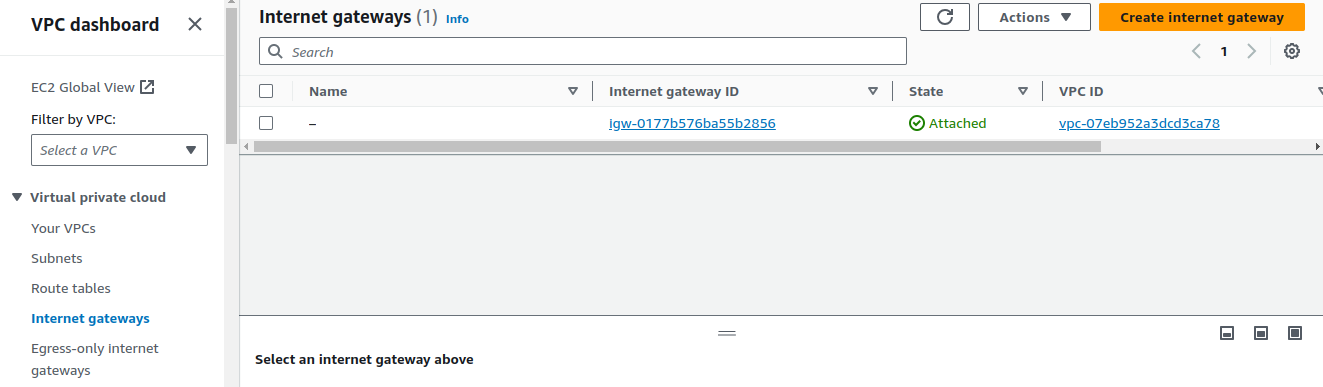
On the VPC dashboard, On Internet gateways, click on Create Internet gateway.
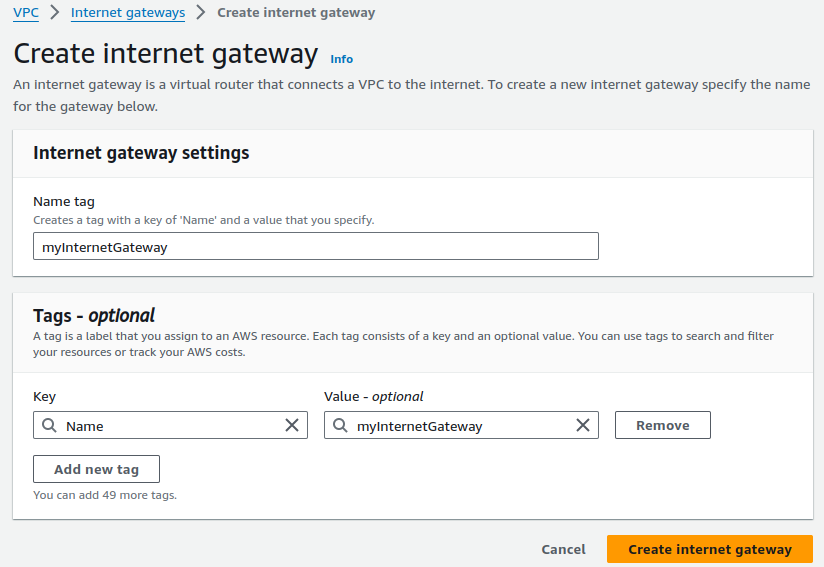
Provide a suitable name for your IG and click on Create internet gateway.
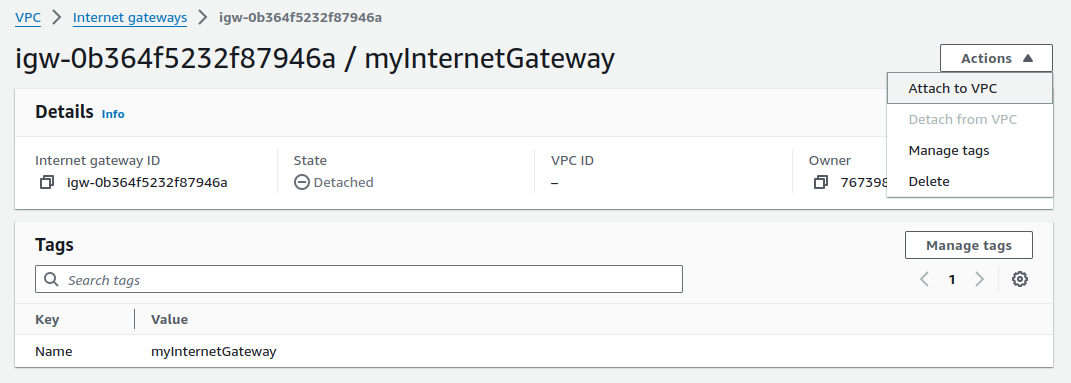
Now, we have to attach it to our VPC.
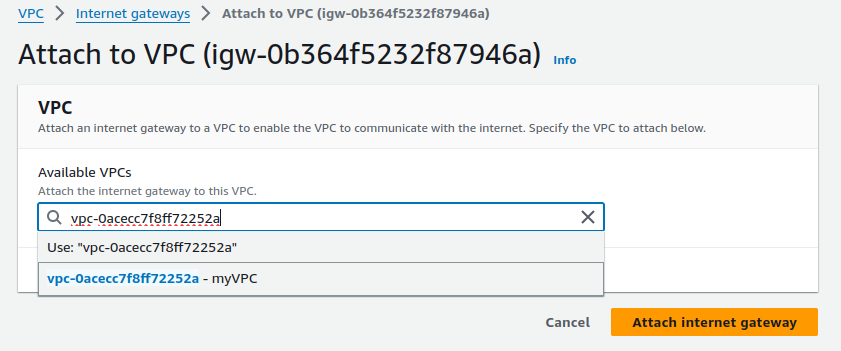
Select your VPC and click on Attach internet gateway.
Task 3: Creating Subnets
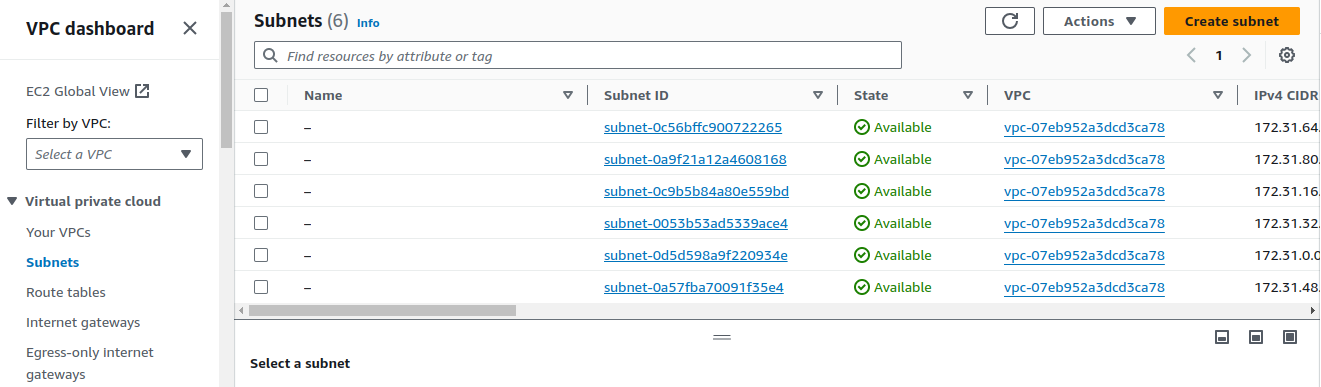
On the VPC dashboard, On Subnets, click on Create subnet.
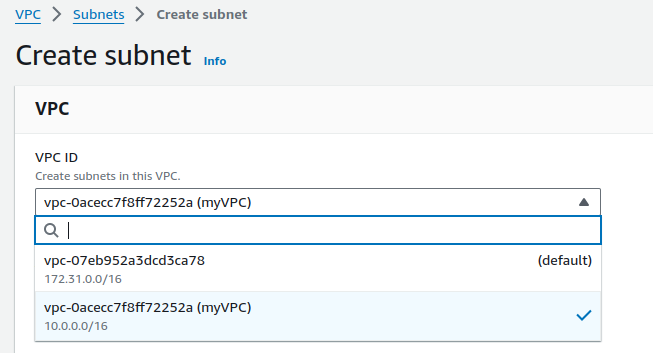
Select your VPC.
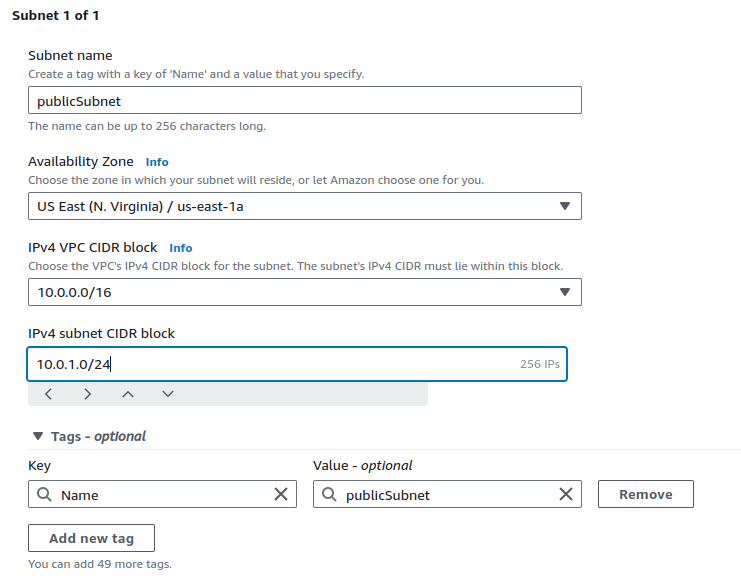
First, we are going to create Public subnet. Provide a suitable name for your subnet and an eligible CIDR range.
For this project, we're only using single Availability Zone.
Click on Add new subnet.
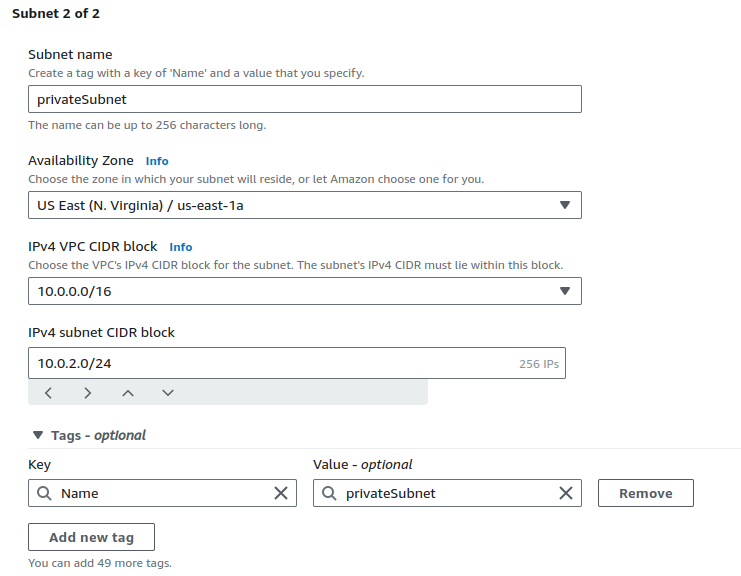
Now, we'll set up our Private subnet. Provide a suitable name, choose the AZ and an eligible CIDR range.
Click on Create subnet.
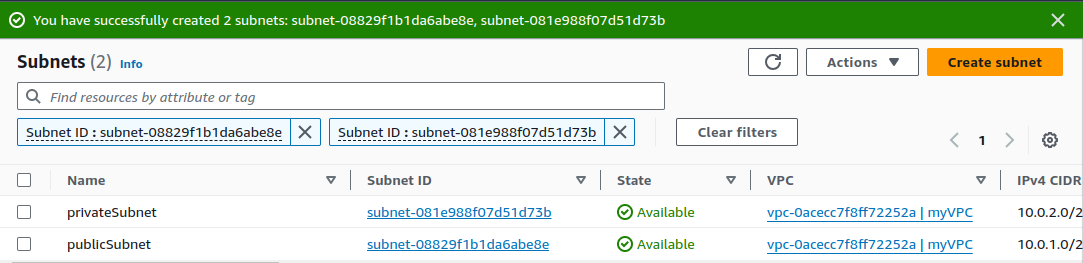
We've successfully created two subnets.
Task 4: Creating Route Tables
On VPC dashboard, On Route tables, click on Create route table.
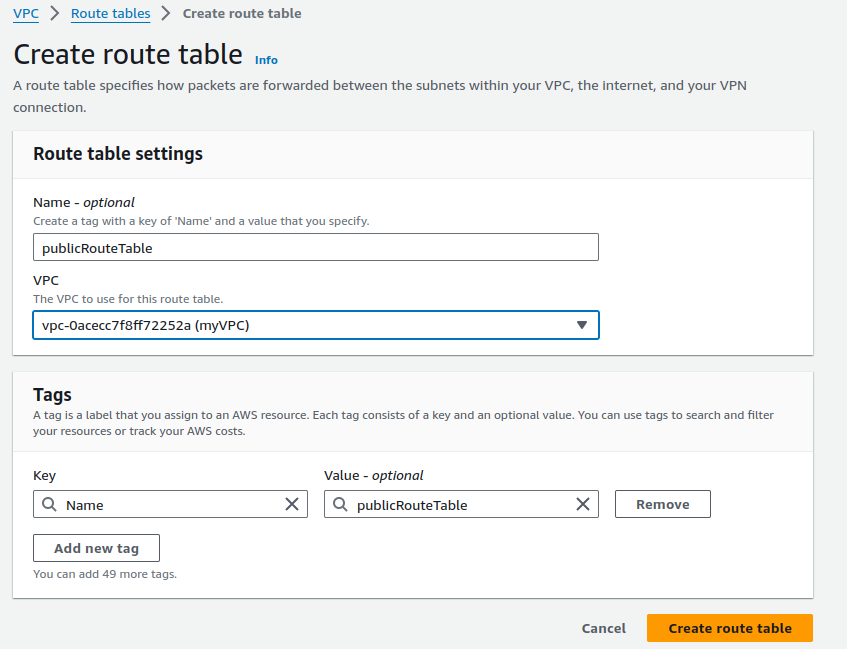
Provide name for your route table, select your VPC and click on Create route table.
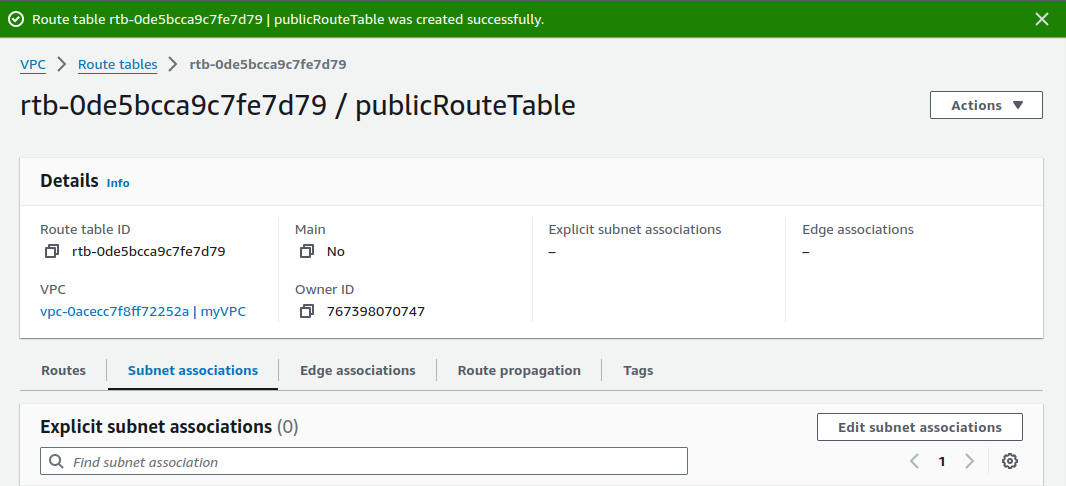
After creating route table, on Subnet associations, click on Edit subnet associations.
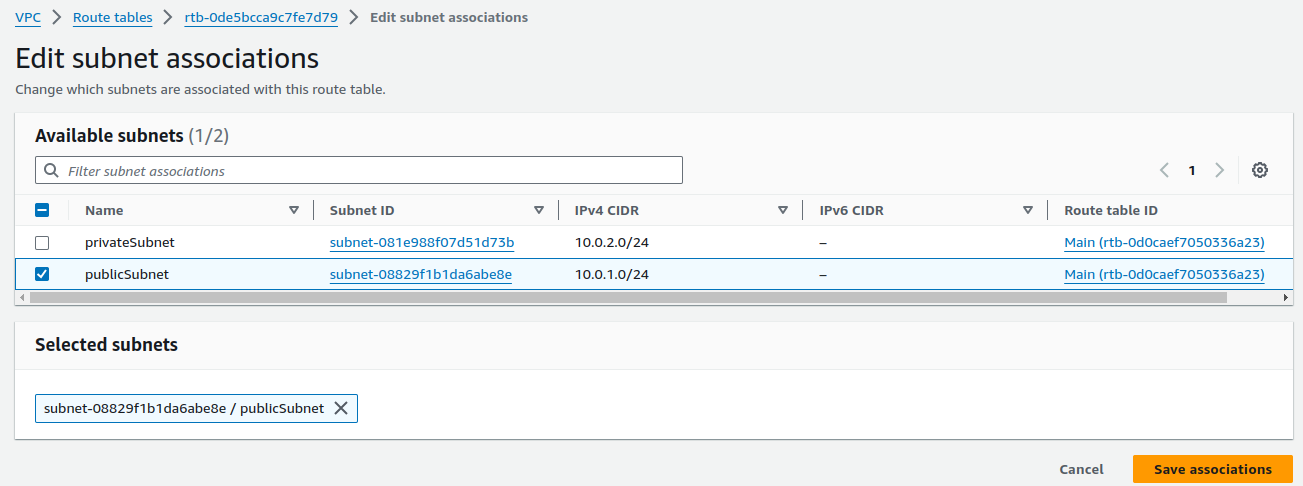
Tick your Public subnet and click on Save associations.
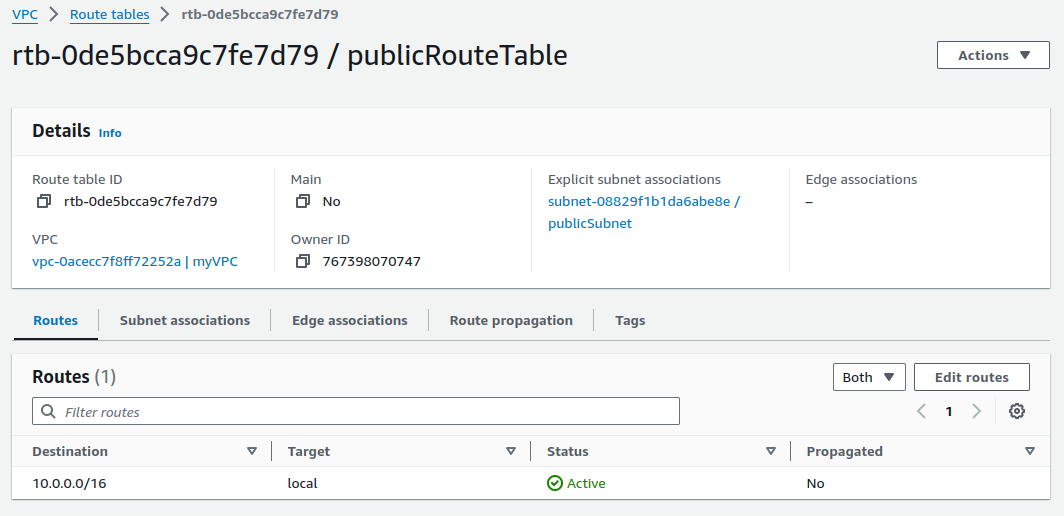
Now, Click on Edit routes.
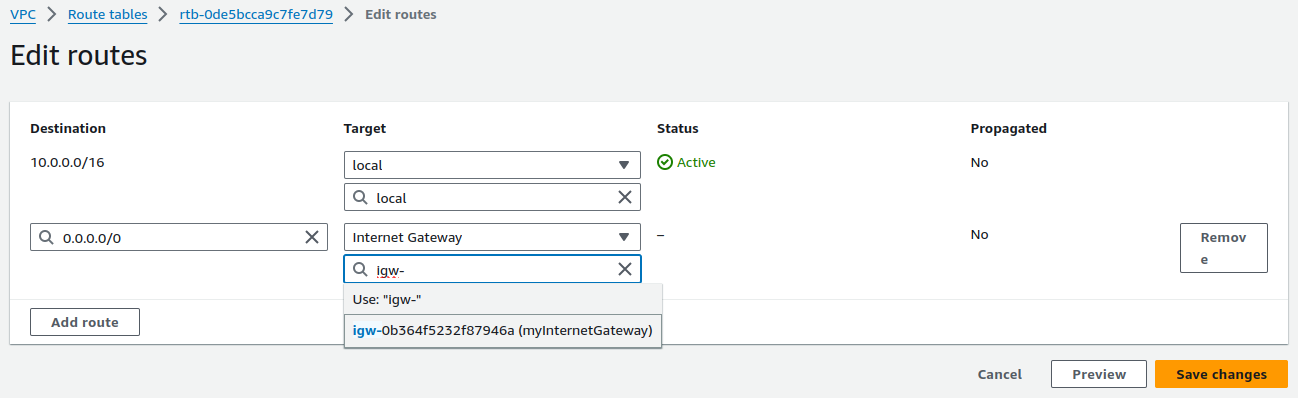
Add route and configure the above configurations. Select your Internet Gateway and click on Save changes.
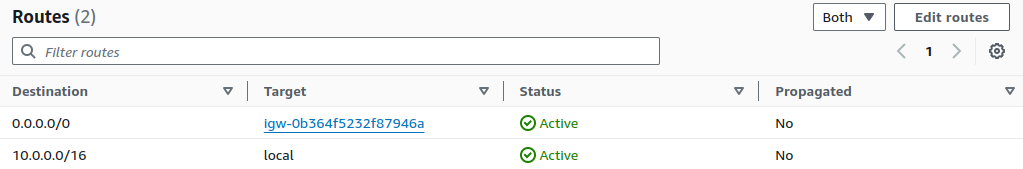
The Public subnet can access the Internet now.
Now, it's time to set up our Private subnet.
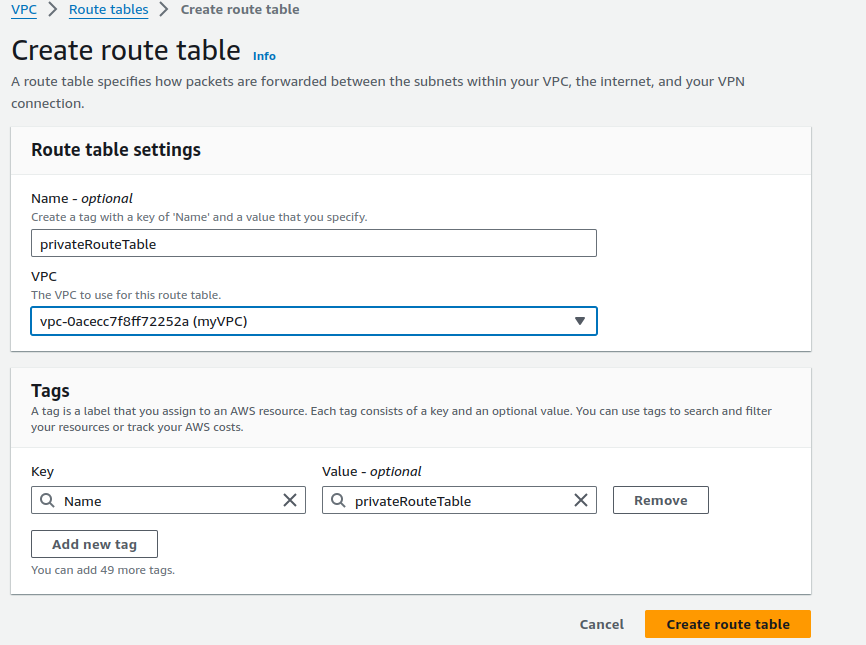
Provide name for your Private route table and select your VPC and click on Create route table.
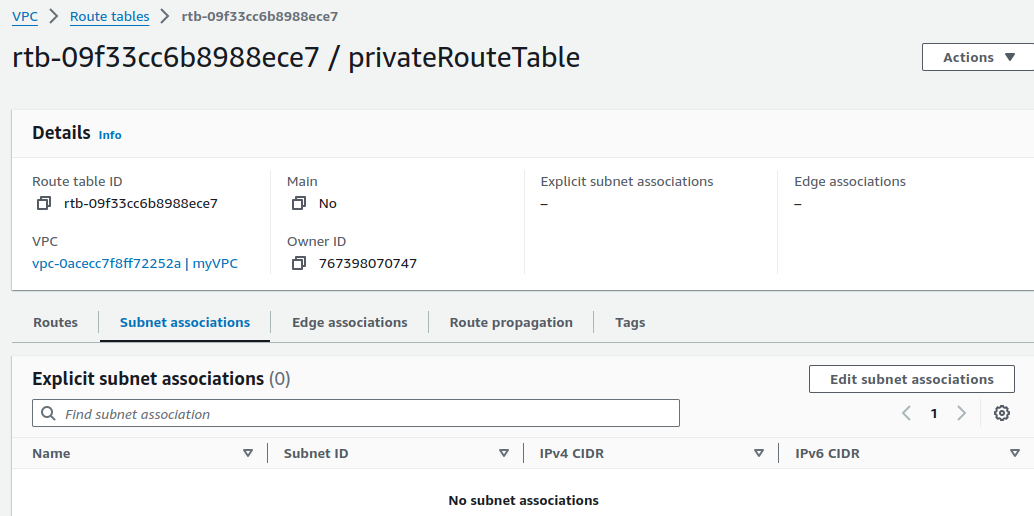
On Subnet associations, click on Edit subnet associations.
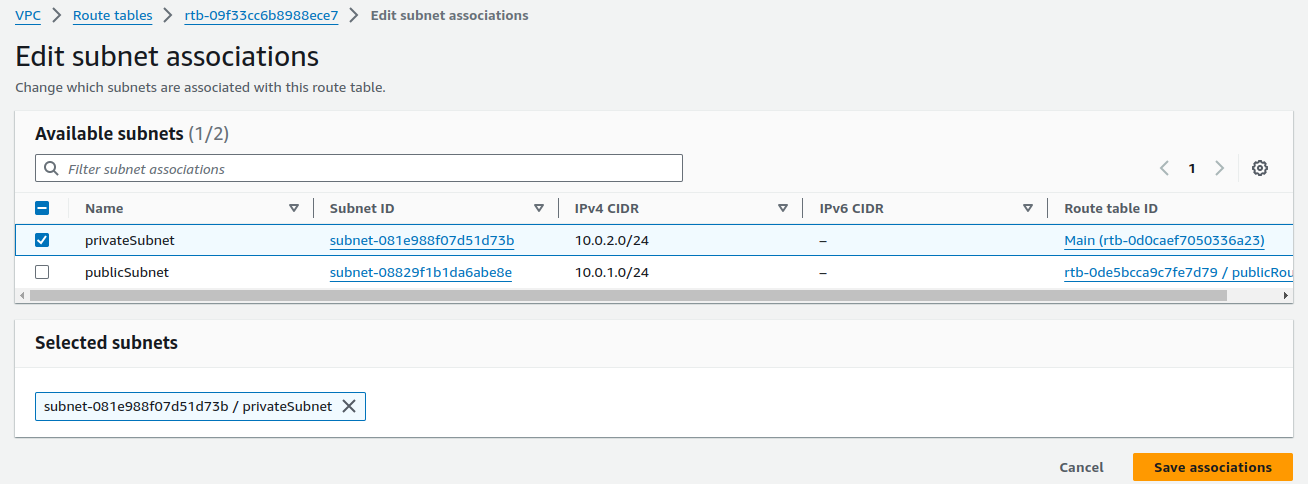
Tick your Private subnet and click on Save associations.
For this Private route table, we do not have to configure any additional routes.
The route table entry 10.0.0.0/16 with the target local indicates that traffic within this IP range is allowed to communicate within the VPC.
Task 5: Creating EC2 instances
Search for EC2 on the search box.
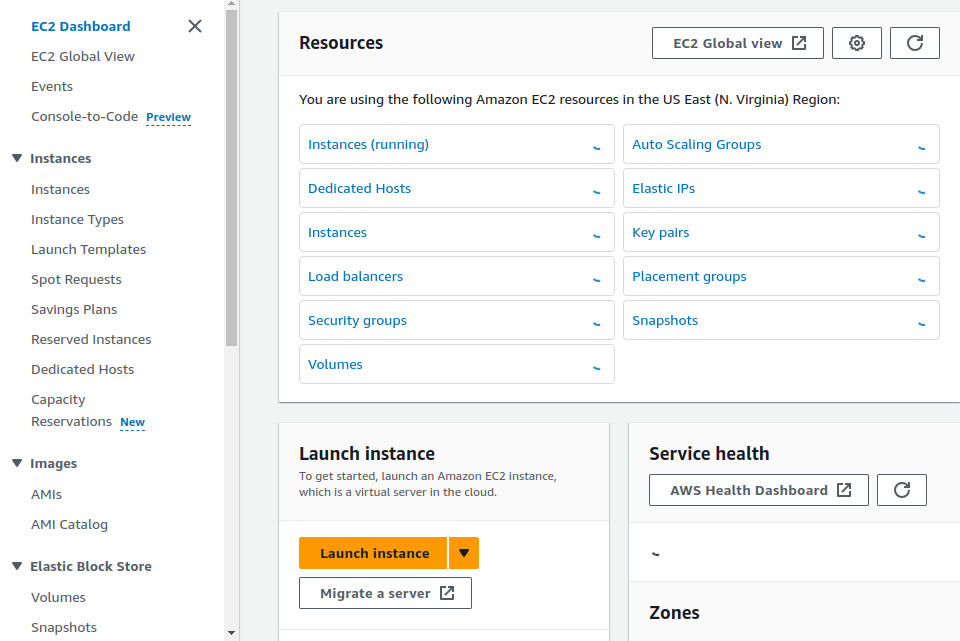
Click on Launch instance.
We'll create our Bastion Host first.
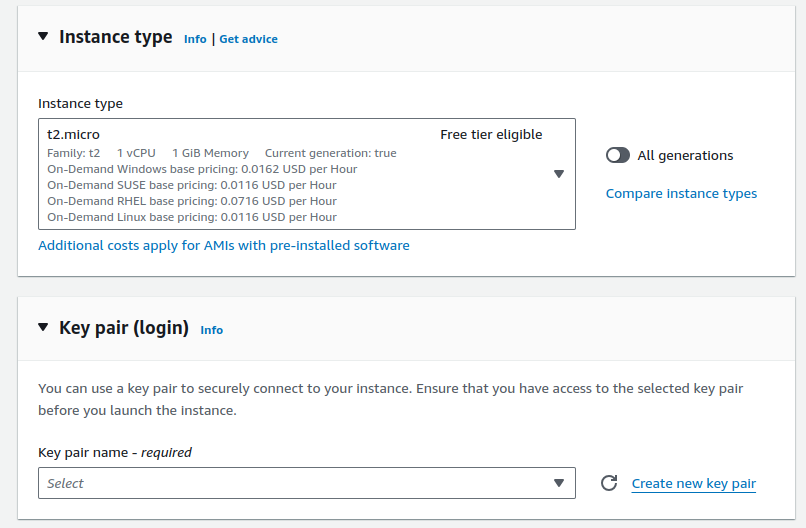
Provide name for your Bastion Host, select Ubuntu as an AMI, choose free tier instance if available.
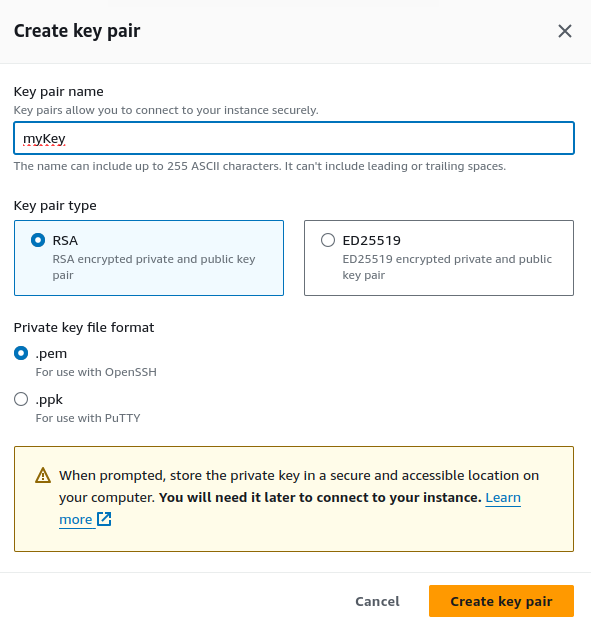
Create a new key pair.
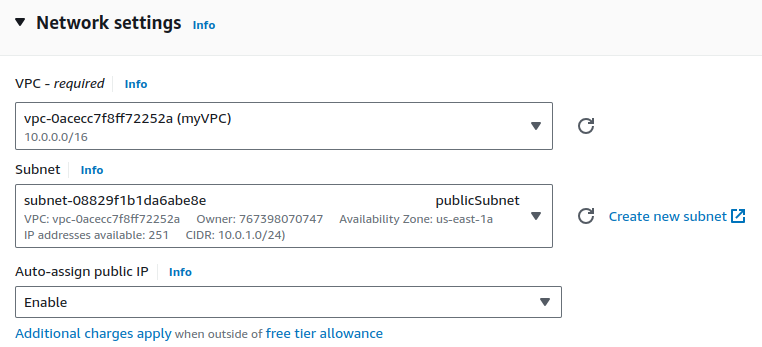
Edit Network settings. Select your VPC, choose your Public subnet and Enable Auto-assign public IP.
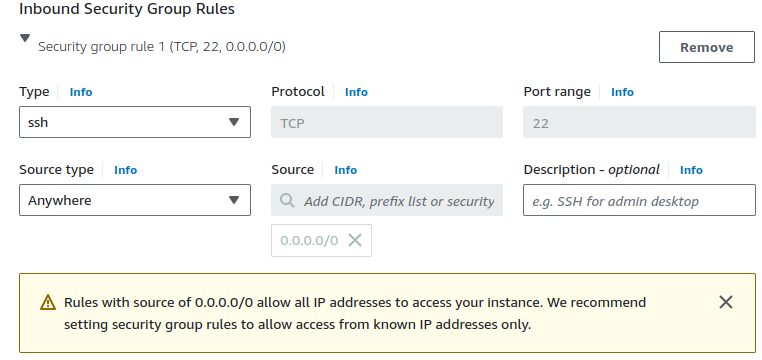
By default, we're provided with an Inbound Security Group Rules.
We can SSH into this instance from anywhere on the internet.
Leaving all other configurations as default, click on Launch instance.
Now, let's create Private instance. Click on Launch instances.
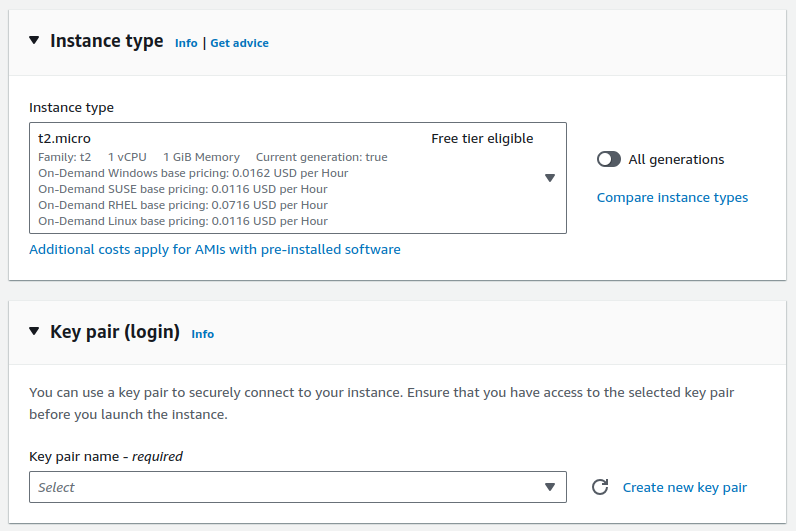
Provide a name for your instance, select your AMI, select the instance type, and create a new key pair. You can also use an existing key pair that was created earlier.
I'm creating separate keys for different instances.
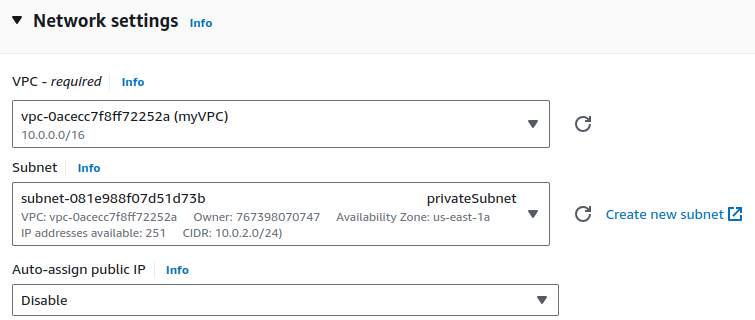
Edit Network Settings. Select your VPC, choose your Private subnet and leave Auto-assign public IP as default.
In the Inbound Security Group Rules, the Source type should not be set to "Anywhere." We must configure it to allow SSH access only from the resources that resides in our Public subnet.
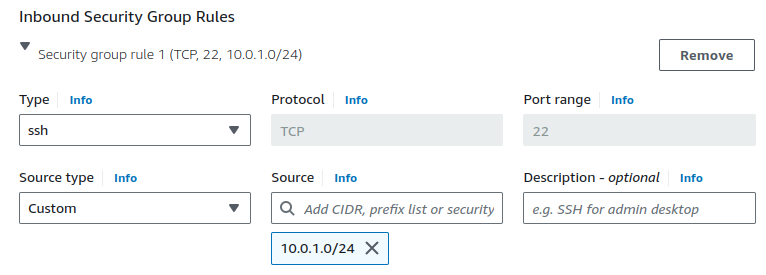
This ensures that only instances within the Public subnet can SSH into the instance.
Leave all other configurations as default and Click on Launch instance.
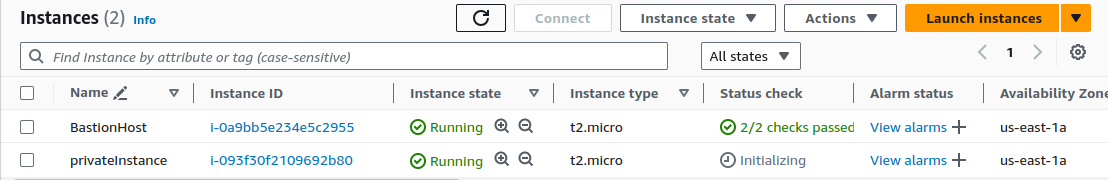
We've created two instances.
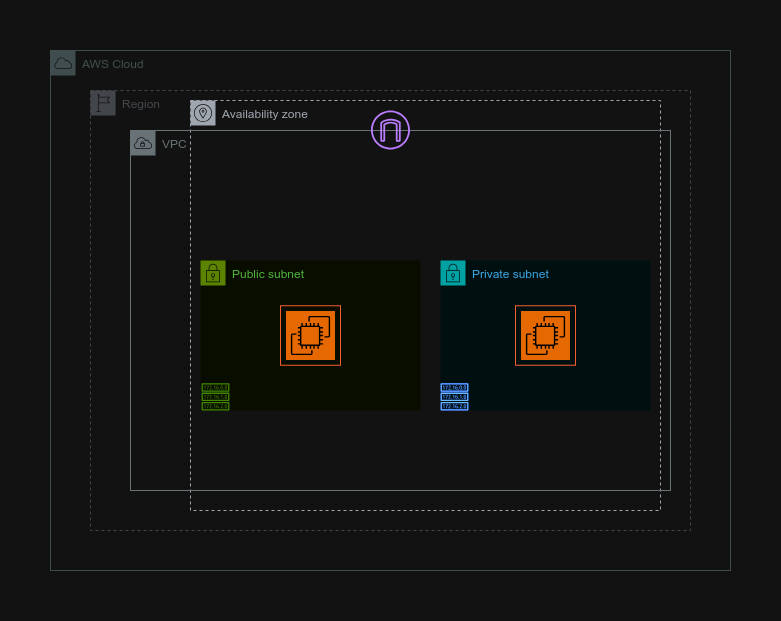
Task 6: SSH into our Bastion Host
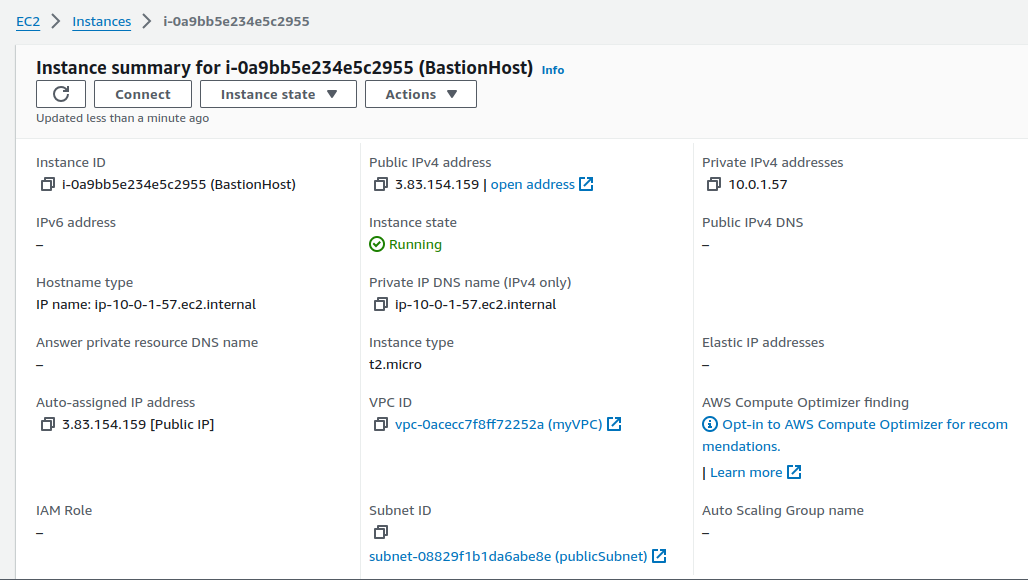
Select your Bastion Host and now click on Connect.
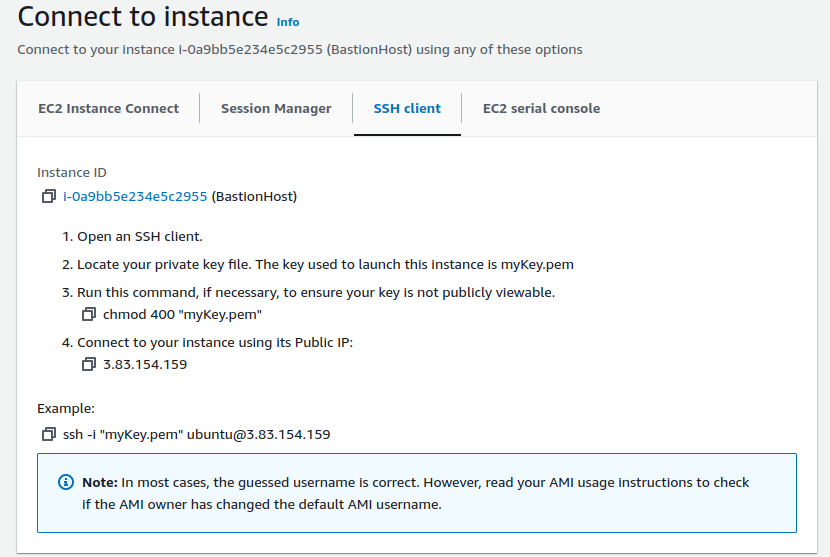
On SSH client, we have to follow some steps shown there.
I'm in my SSH client, i.e., terminal.
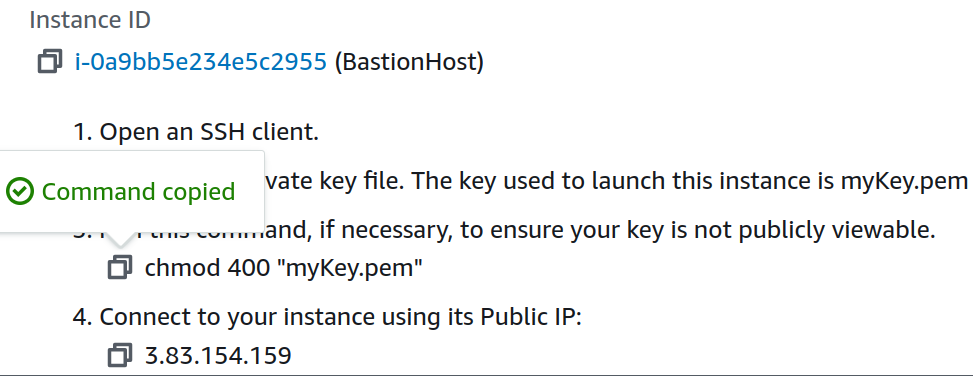
Copy the command and paste into your terminal.

You can view your permissions using the following command:
ls -l

We have changed the file permissions to make it readable by the owner only.
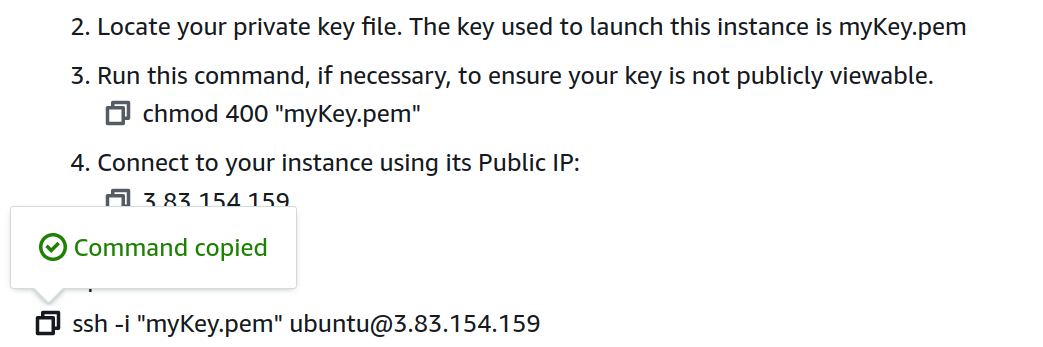
Copy the command & paste into your terminal.
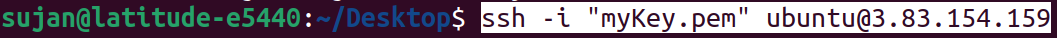
Make sure your key file is present in your working directory; otherwise, provide the full path to the key file.
Proceed with yes.
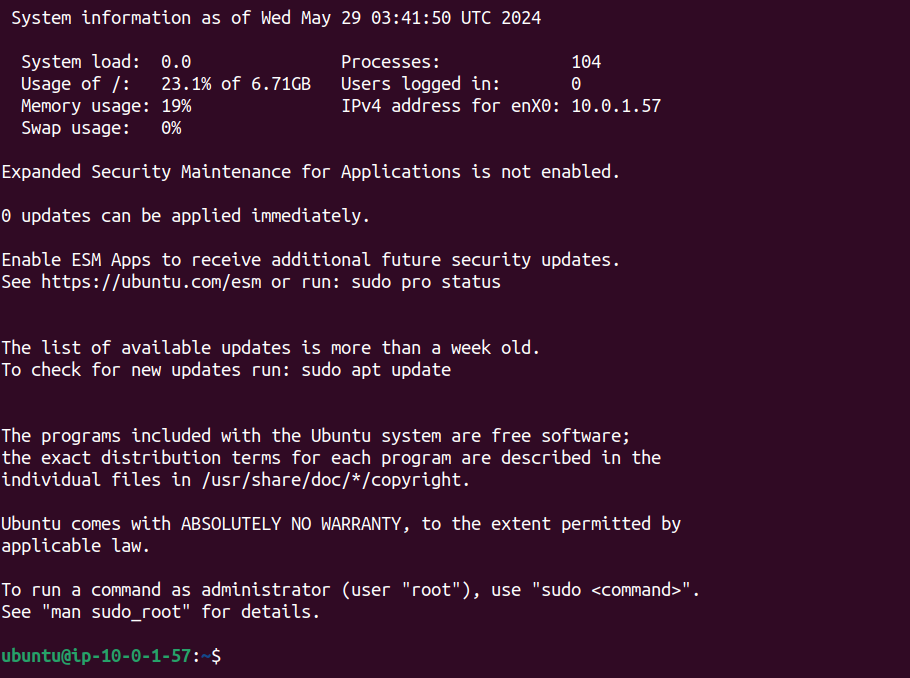
Now, we have logged into our instance using SSH.
Task 7: Copying the Key File
Open new terminal in your local computer.
We're copying the private key file that is in our local computer to our Bastion Host.
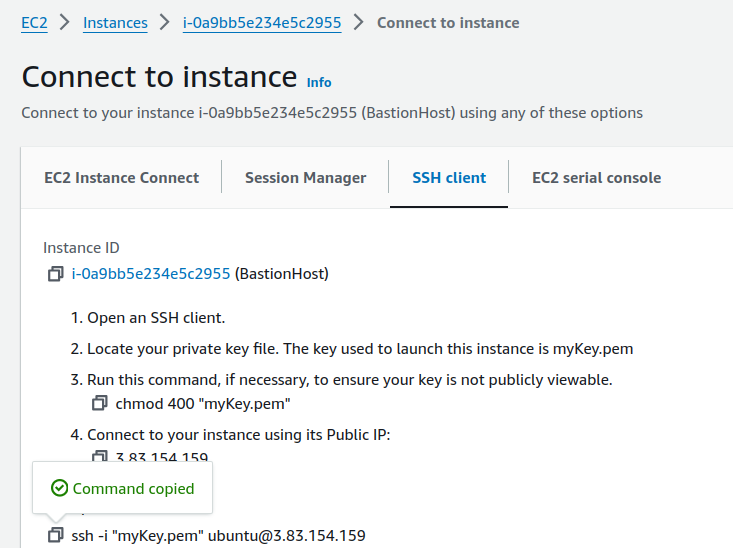
ssh -i "myKey.pem" ubuntu@3.83.154.159
For ease, copy the command that we use to SSH into our instance. It's so to modify it a bit.
Paste the command in your Desktop's terminal.
scp -i "myKey.pem" privateKey.pem ubuntu@3.83.154.159:/path/to/destination/
Replace and add commands/configurations as required.
Here's a breakdown of the command:
scpstands for Secure Copy. It is a command-line utility that allows you to securely copy files and directories between two locations.-i my-key.pem: Specifies the identity file (private key) to use for authentication.privateKey.pem: Specifies the source file on your local machine that you want to copy.ubuntu@3.83.154.159:/path/to/destination/: Specifies the destination on the remote
Alright.
To see your present working directory, In your Bastion terminal, type command:
pwd
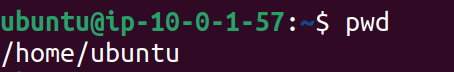
Now, replace the /path/to/destination/ with your pwd location in your Desktop's terminal.
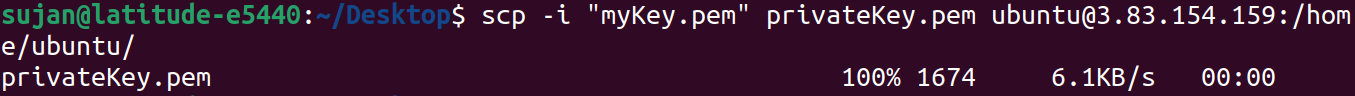
Now see if the key has been successfully copied into our Bastion Host by listing files/folders in our Bastion's terminal.
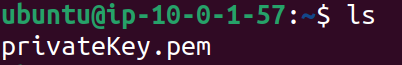
We can see that the private key has been copied from our local computer to the remote instance.
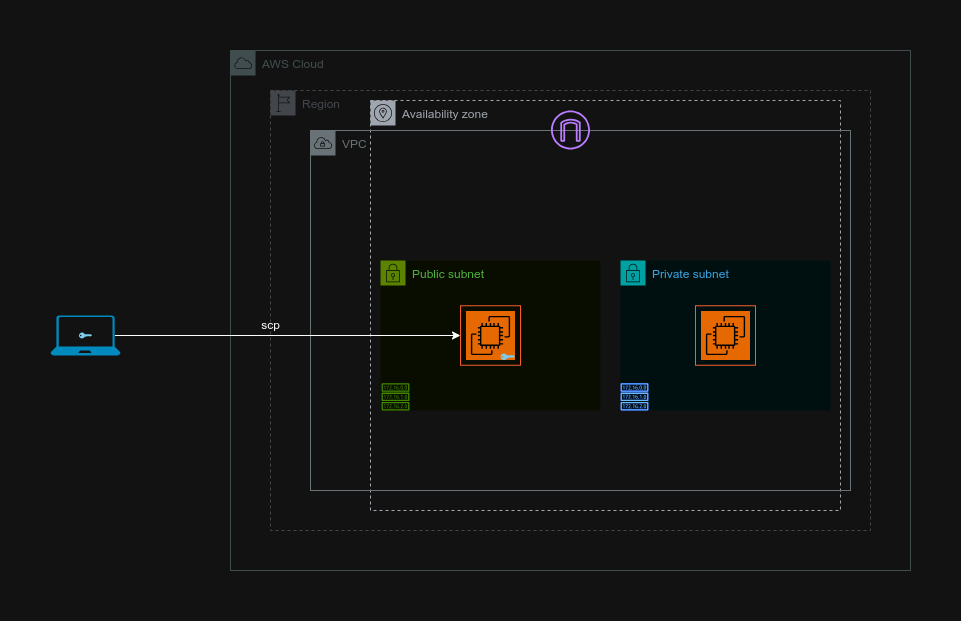
Task 8: SSH Login to Private Instance
It's time to SSH log in into our Private instance.
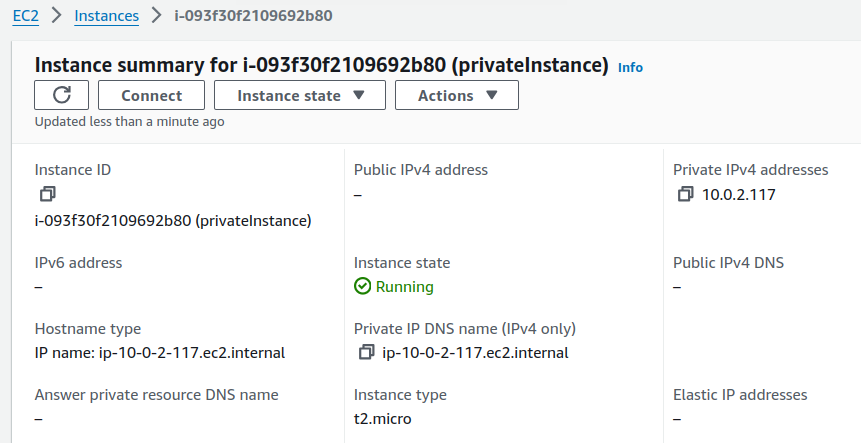
Select your Private instance and click on Connect.
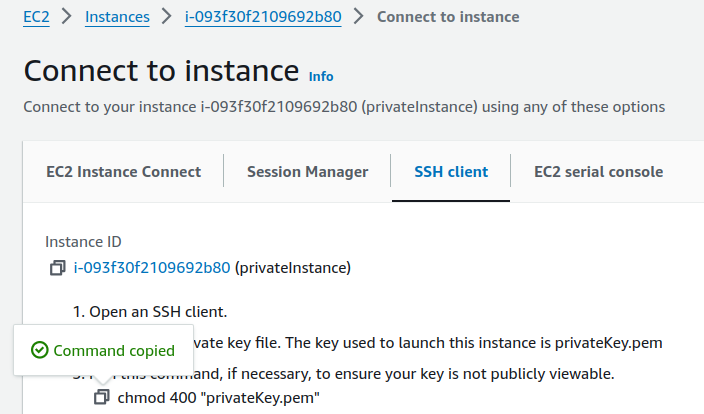
Copy the command.
But before that, let's see what permissions are set initially,
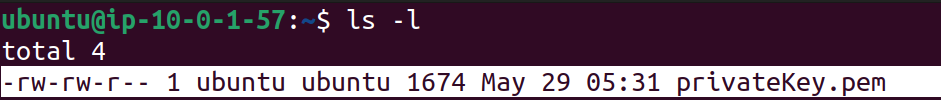
We can see there are read/write for Owner, read/write for Group & read permissions for Others.
It is recommended to set the permissions of the file or directory to the minimum necessary for the required operations.
So, let's do that.
Paste the command that you had copied into the Bastion's terminal.
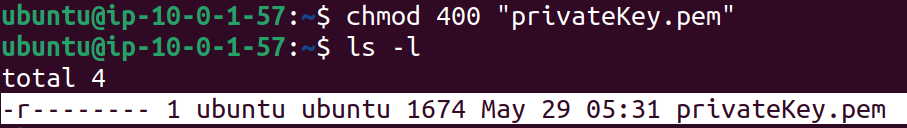
We can see the file permissions have been changed now.
Now, copy the SSH command.
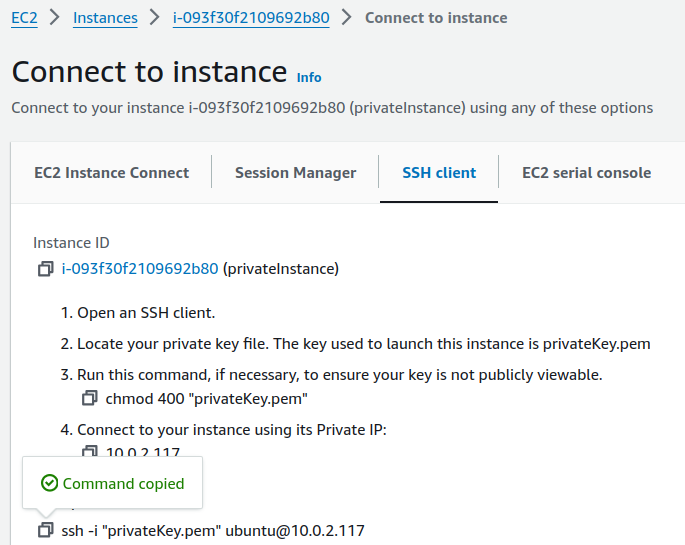
Paste into your terminal.
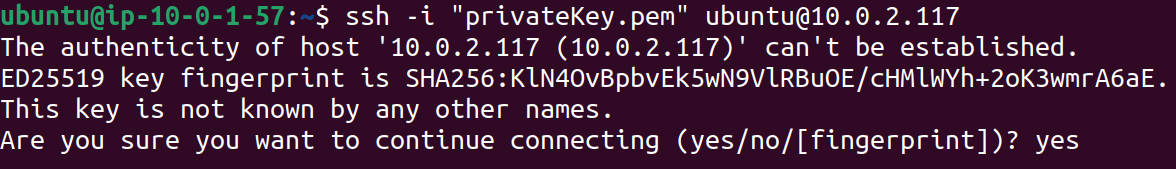
Proceed with yes.
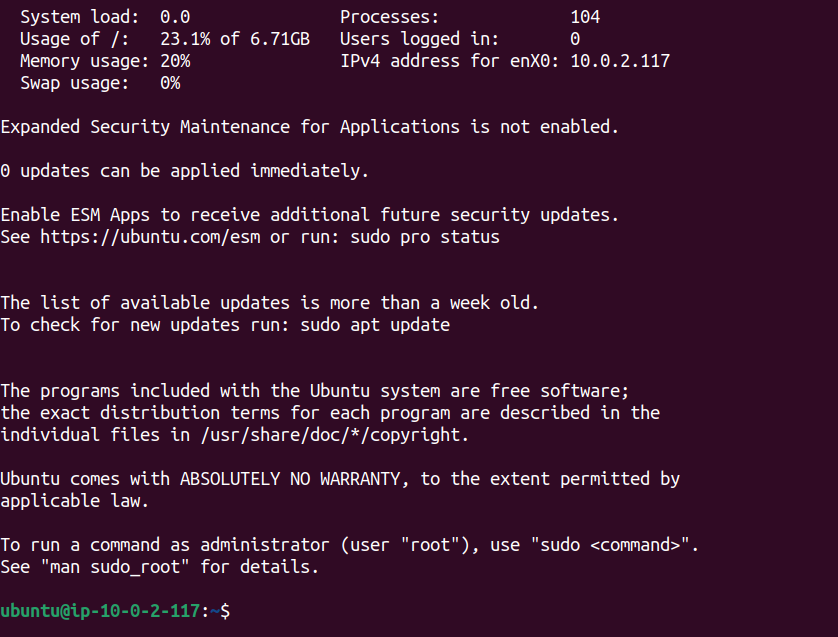
Now we are into our Private instance.
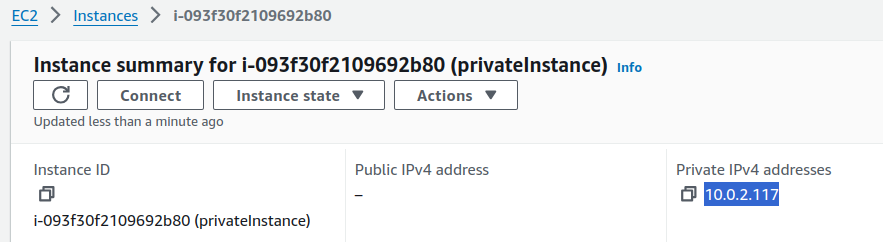
You can verify this by examining the details in the instance configurations.
Alright, that's our work done.
Conclusion
This configuration helps keep our Private instance secure by limiting direct access from the internet. Instead, we can access it securely through the Bastion host. This setup is a common practice for enhancing security in cloud environments.
Task 8: Clean Up
Terminating instances.
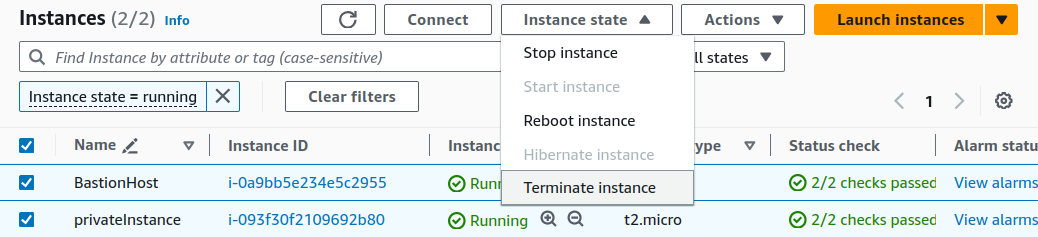
Select both of your instances, on Instance state, click on
Terminate instance.Deleting Route tables.

Search for VPC in the search box.
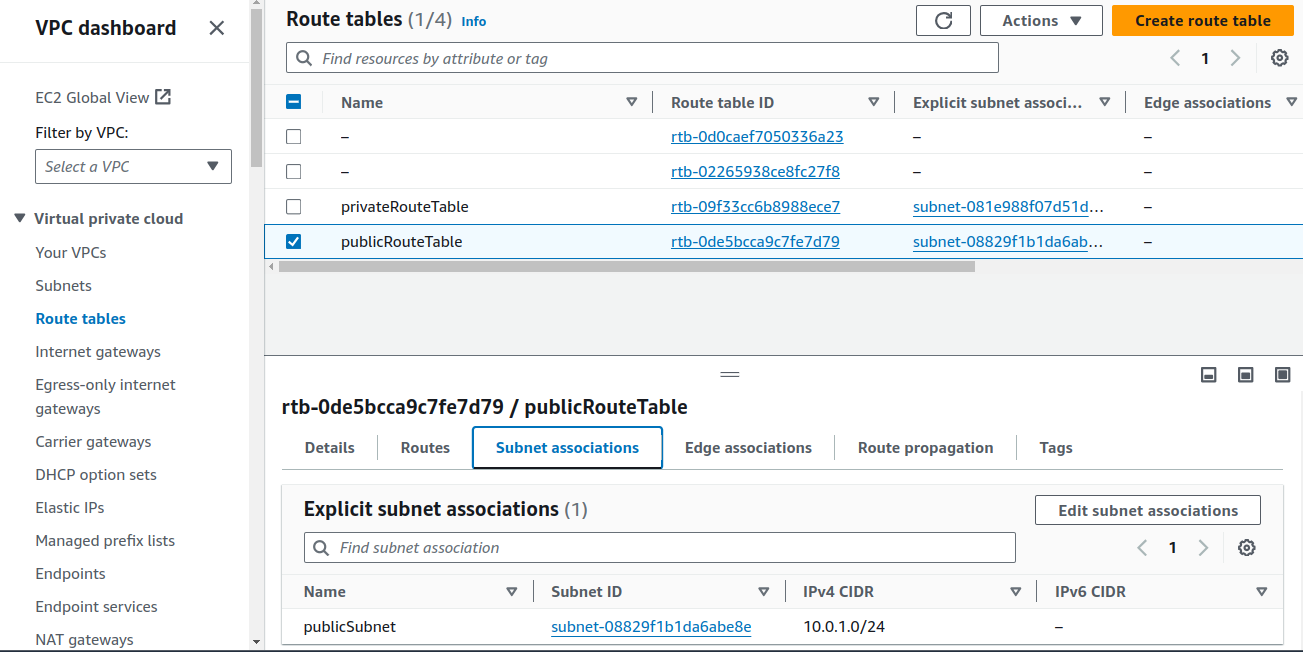
On Route tables Subnet associations, click on
Edit subnet associations.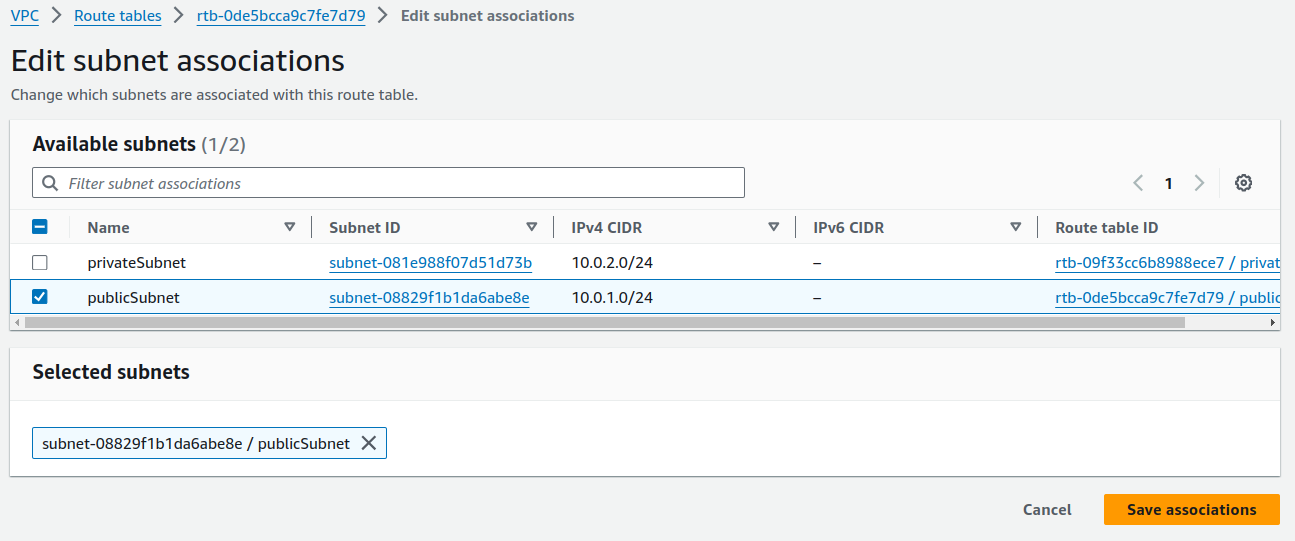
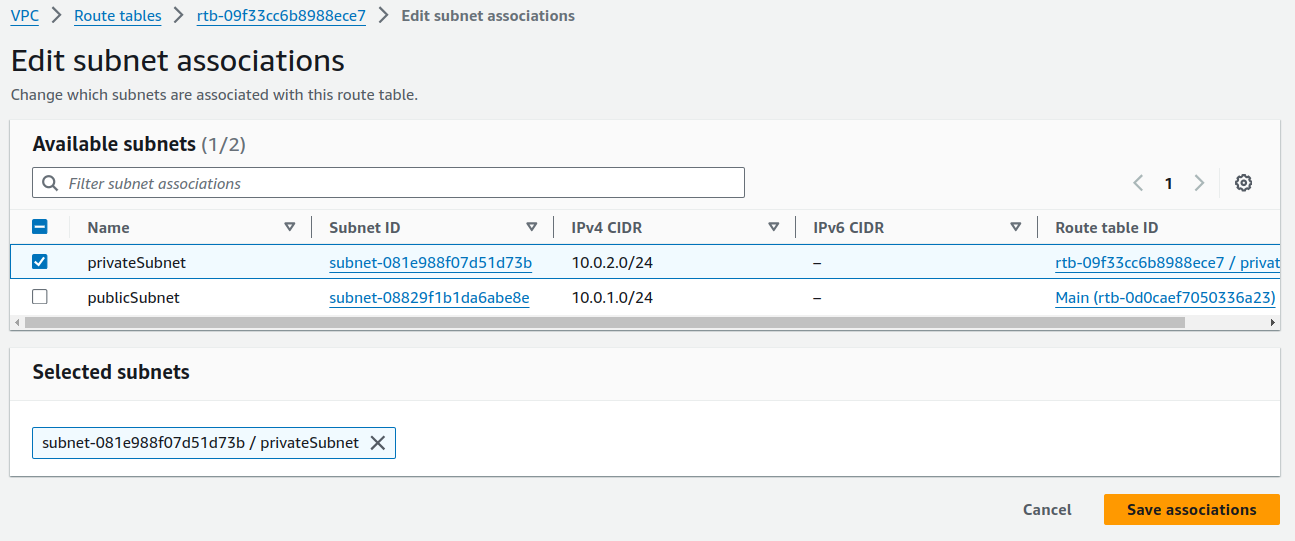
Uncheck the box and click on
Save associations. Do the same for Private Route tables.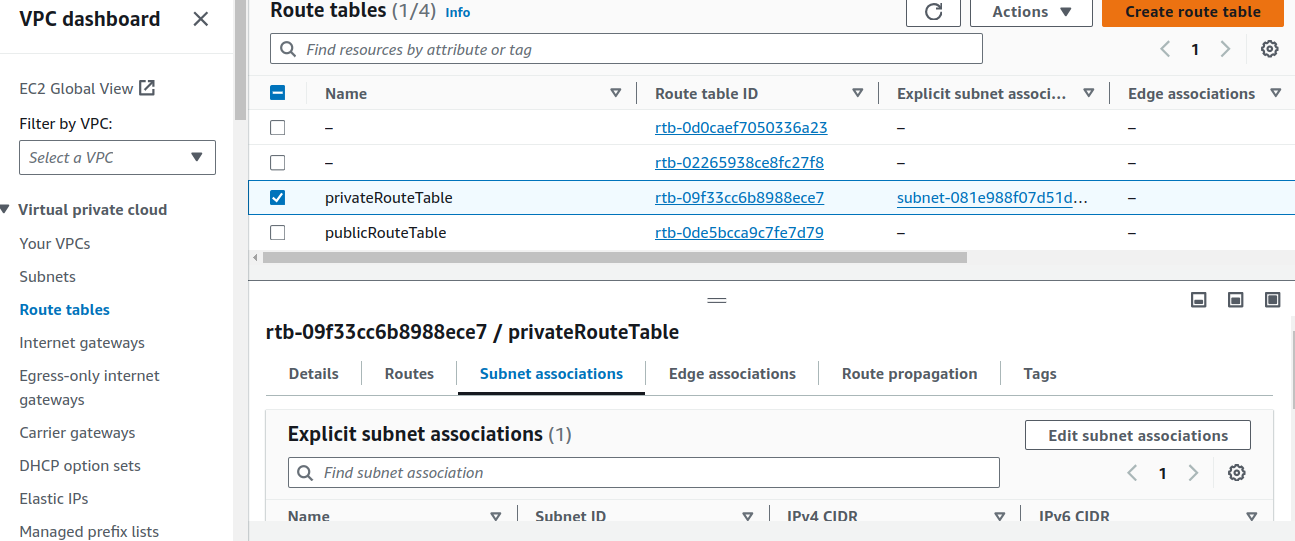
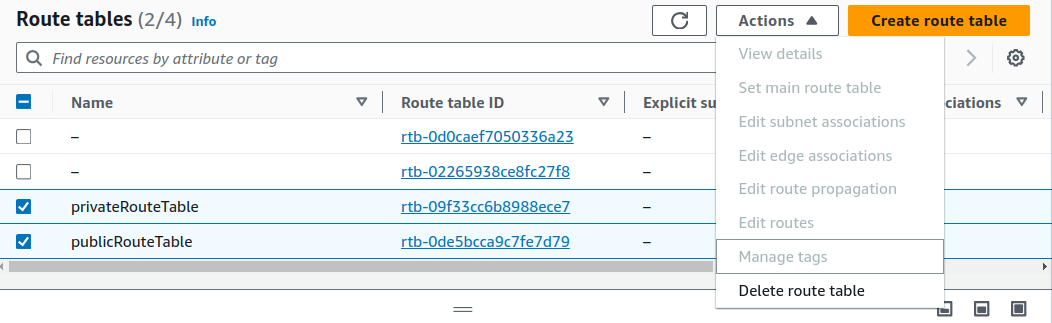
Now, as we do not have any associations, we can delete the route tables.
Deleting Subnets
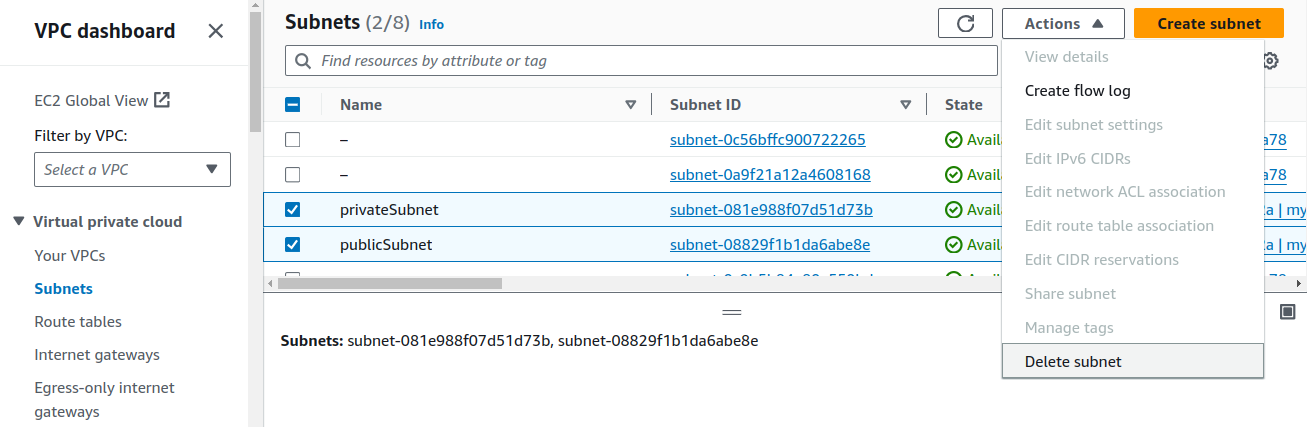
Tick both of your subnets and on Actions panel, click
Delete subnet.Deleting Internet Gateway.
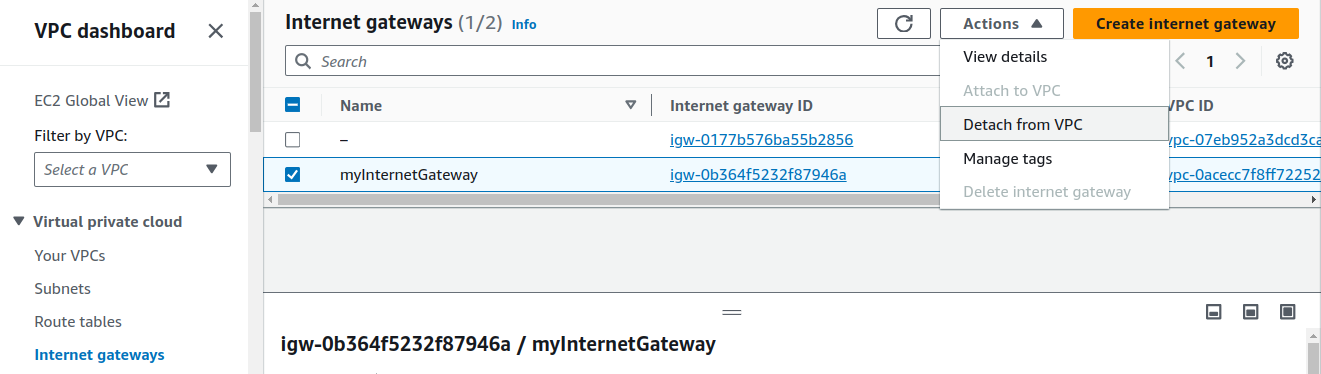
Before we are able to delete the IG, we've to detach it from our VPC.
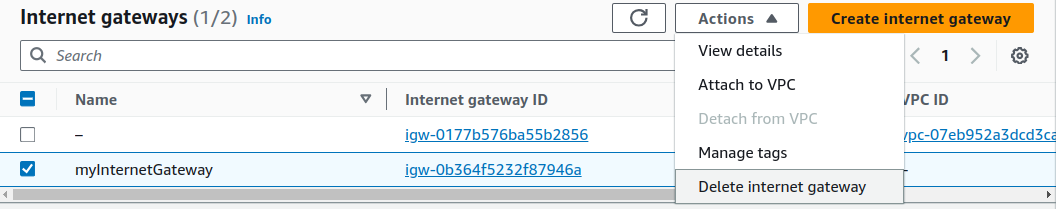
After detaching from our VPC, we can delete our Internet gateway.
Deleting VPC.
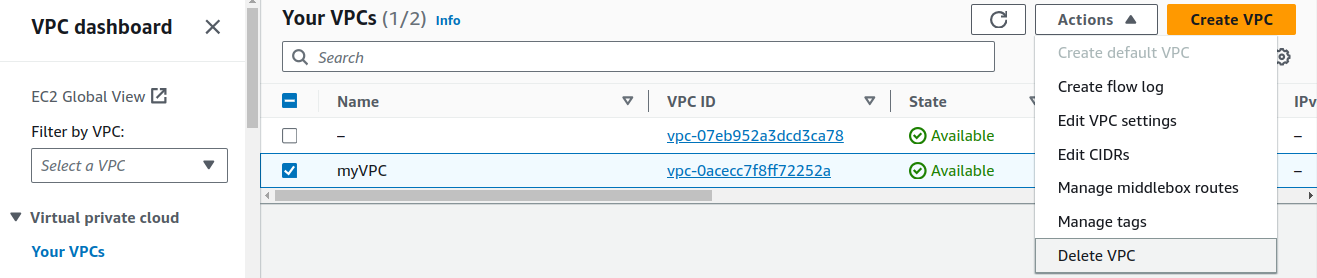
Now, we have cleaned up our resources that we had used in our lab session.
Alright folks, See you in the next one!
Subscribe to my newsletter
Read articles from SUJAN directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

SUJAN
SUJAN
Hello people. I am here to document my learnings. See yah!!