Docker Scout Image details view
 Megha Sharma
Megha Sharma
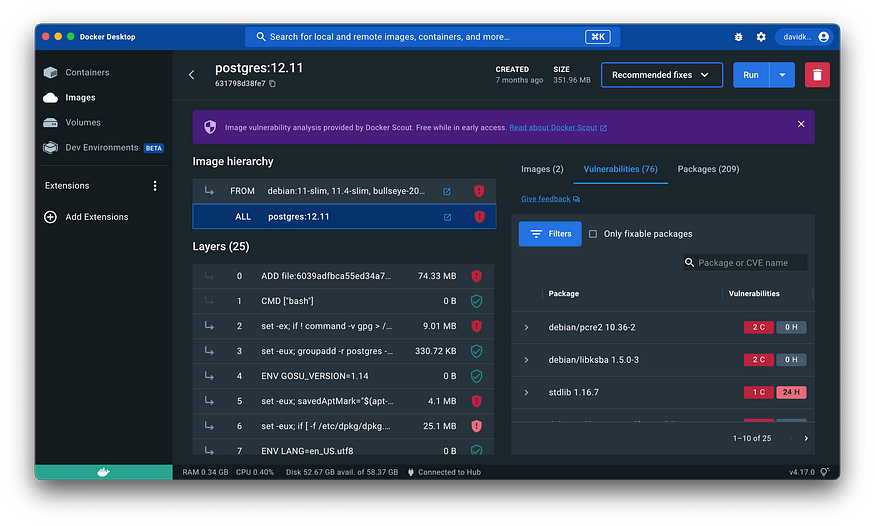
The image details view shows a breakdown of the Docker Scout analysis. You can access the image view from the Docker Scout Dashboard, the Docker Desktop Images view, and from the image tag page on Docker Hub. The image details show a breakdown of the image hierarchy (base images), image layers, packages, and vulnerabilities.
Docker Desktop first analyzes images locally, where it generates a software bill of materials (SBOM). Docker Desktop, Docker Hub, and the Docker Scout Dashboard and CLI all use the package URL (PURL) in this SBOM to query for matching Common Vulnerabilities and Exposures (CVEs) in Docker Scout’s advisory database.
👉 Image hierarchy
The image you inspect may have one or more base images represented under Image hierarchy. This means the author of the image used other images as starting points when building the image. Often these base images are either operating system images such as Debian, Ubuntu, and Alpine, or programming language images such as PHP, Python, and Java.
Selecting each image in the chain lets you see which layers originate from each base image. Selecting the ALL row selects all layers and base images.
One or more of the base images may have updates available, which may include updated security patches that remove vulnerabilities from your image. Any base images with available updates are noted to the right of Image hierarchy.
👉 Layers
A Docker image consists of layers. Image layers are listed from top to bottom, with the earliest layer at the top and the most recent layer at the bottom. Often, the layers at the top of the list originate from a base image, and the layers towards the bottom added by the image author, often using commands in a Dockerfile. Selecting a base image under Image hierarchy highlights with layers originate from a base image.
Selecting individual or multiple layers filters the packages and vulnerabilities on the right-hand side to show what the selected layers added.
👉 Vulnerabilities
The Vulnerabilities tab displays a list of vulnerabilities and exploits detected in the image. The list is grouped by package, and sorted in order of severity.
You can find further information on the vulnerability or exploit, including if a fix is available, by expanding the list item.
When you inspect an image in Docker Desktop or Docker Hub, Docker Scout can provide recommendations for improving the security of that image.
👉 Recommendations in Docker Desktop
To view security recommendations for an image in Docker Desktop:
Go to the Images view in Docker Desktop.
Select the image tag that you want to view recommendations for.
Near the top, select the Recommended fixes drop-down button.
The drop-down menu lets you choose whether you want to see recommendations for the current image or any base images used to build it:
Recommendations for current image:
The recommendations for the current image view helps you determine whether the image version that you’re using is out of date. If the tag you’re using is referencing an old digest, the view shows a recommendation to update the tag by pulling the latest version.
Select the Pull new image button to get the updated version. Check the checkbox to remove the old version after pulling the latest.
Recommendations for base image:
The base image recommendations view contains two tabs for toggling between different types of recommendations:
Refresh base image
Change base image
These base image recommendations are only actionable if you’re the author of the image you’re inspecting. This is because changing the base image for an image requires you to update the Dockerfile and re-build the image.
👉 Refresh base image
If the selected base image tag is the latest available version, or if it’s outdated.
If the base image tag used to build the current image isn’t the latest, then the delta between the two versions shows in this window. The delta information includes:
The tag name, and aliases, of the recommended (newer) version
The age of the current base image version
The age of the latest available version
The number of CVEs affecting each version
At the bottom of the window, you also receive command snippets that you can run to re-build the image using the latest version.
👉 Change base image
This tab shows different alternative tags that you can use, and outlines the benefits and disadvantages of each tag version. Selecting the base image shows recommended options for that tag.
For example, if the image you’re inspecting is using an old version of debian as a base image, it shows recommendations for newer and more secure versions of debian to use. By providing more than one alternative to choose from, you can see for yourself how the options compare with each other, and decide which one to use.
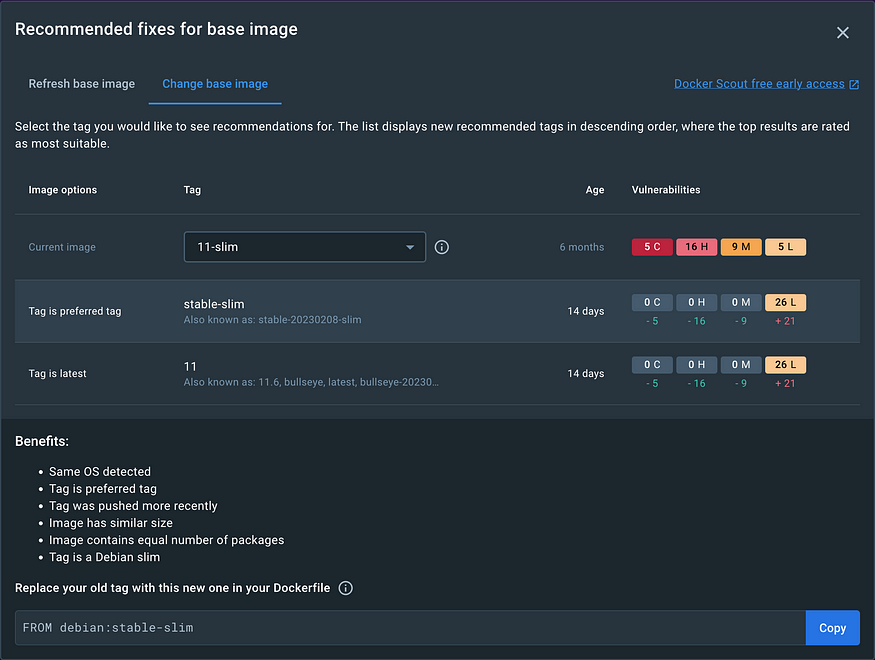
Select a tag recommendation to see further details of the recommendation. It shows the benefits and potential disadvantages of the tag, why it’s a recommended, and how to update your Dockerfile to use this version.
👉 Advisory database sources and matching service
Reliable information sources are key for Docker Scout’s ability to surface relevant and accurate assessments of your software artifacts. Given the diversity of sources and methodologies in the industry, discrepancies in vulnerability assessment results can and do happen.
Docker Scout integrates with various advisory databases to offer comprehensive security reports and vulnerability assessments. The key advisory database sources and the matching service in Docker Scout include:
CVE (Common Vulnerabilities and Exposures) Database: The CVE database is a widely recognized source of information about security vulnerabilities. It provides unique identifiers (CVEs) for each vulnerability, along with detailed descriptions.
NVD (National Vulnerability Database): The NVD is a repository of standards-based vulnerability management data. It includes CVE data along with additional analysis, including severity scores (CVSS), impact ratings, and fix information.
OSV (Open Source Vulnerability) Database: A collaborative project aiming to provide an open and distributed database of vulnerabilities in open-source projects. It aggregates information from various ecosystems like Python, JavaScript, Go, and others.
Vendor-Specific Databases: Many software vendors maintain their own databases of vulnerabilities specific to their products. These databases are crucial for getting the most accurate and up-to-date information for proprietary or specialized software components.
Security Advisories from Linux Distributions: Various Linux distributions such as Debian, Ubuntu, Red Hat, and Alpine publish their own security advisories. These advisories are critical for vulnerabilities specific to the packages and versions used in these distributions.
👉 Advisory database sources
Docker Scout aggregates vulnerability data from multiple sources. The data is continuously updated to ensure that your security posture is represented using the latest available information, in real-time.
Docker Scout uses the following package repositories and security trackers:
Alpine secdb
AlmaLinux Security Advisory
Amazon Linux Security Center
Bitnami Vulnerability Database
CISA Known Exploited Vulnerability Catalog
CISA Vulnrichment
Debian Security Bug Tracker
Exploit Prediction Scoring System (EPSS)
GitHub Advisory Database
GitLab Advisory Database
Golang VulnDB
inTheWild, a community-driven open database of vulnerability exploitation
National Vulnerability Database
Oracle Linux Security
Python Packaging Advisory Database
RedHat Security Data
Rocky Linux Security Advisory
RustSec Advisory Database
SUSE Security CVRF
Ubuntu CVE Tracker
Wolfi Security Feed
Chainguard Security Feed
When you enable Docker Scout for your Docker organization, a new database instance is provisioned on the Docker Scout platform. The database stores the Software Bill of Materials (SBOM) and other metadata about your images. When a security advisory has new information about a vulnerability, your SBOM is cross-referenced with the CVE information to detect how it affects you.
👉 Supported package ecosystems
Docker Scout supports the following package ecosystems:
.NET
GitHub packages
Go
Java
JavaScript
PHP
Python
RPM
Ruby
alpm(Arch Linux)apk(Alpine Linux)deb(Debian Linux and derivatives)
Subscribe to my newsletter
Read articles from Megha Sharma directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Megha Sharma
Megha Sharma
👋 Hi there! I'm a DevOps enthusiast with a deep passion for all things Cloud Native. I thrive on learning and exploring new technologies, always eager to expand my knowledge and skills. Let's connect, collaborate, and grow together as we navigate the ever-evolving tech landscape! SKILLS: 🔹 Languages & Runtimes: Python, Shell Scripting, YAML 🔹 Cloud Technologies: AWS, Microsoft Azure, GCP 🔹 Infrastructure Tools: Docker, Terraform, AWS CloudFormation 🔹 Other Tools: Linux, Git and GitHub, Jenkins, Docker, Kubernetes, Ansible, Prometheus, Grafana