Initiating Your Path in Ethical Hacking
 GnanaAslin 2000
GnanaAslin 2000Ethical hacking, also known as penetration testing or white-hat hacking, is the practice of deliberately probing and testing a computer system, network, or web application to discover security vulnerabilities that could be exploited by malicious hackers. Unlike malicious hacking, ethical hacking is performed with the permission of the system owner, and its primary goal is to improve security and protect sensitive data.
1. Understand the Basics and Importance of Ethical Hacking
Definition and Purpose: Ethical hacking, or penetration testing, involves authorized attempts to breach computer systems and networks to identify security vulnerabilities. Its main goal is to strengthen an organization’s digital infrastructure.
Importance: This strategic investment not only helps prevent potential breaches but also mitigates risks associated with data theft, financial loss, and reputation damage. By understanding the tactics and techniques used by malicious actors, individuals can better defend against cyber threats and contribute to a more secure digital landscape. If you're ready to enhance your cybersecurity knowledge and skill set, check out this link for more information: Ethical Hacking Training Course in Pune.

2. Acquire Necessary Skills and Knowledge
Technical Skills: Proficiency in programming languages (e.g., Python, Java, C++), networking concepts (e.g., IP addresses, subnets, firewalls), and operating systems (e.g., Linux, Windows, macOS) is crucial.
Ethical and Legal Knowledge: Understand and adhere to ethical guidelines and legal requirements, ensuring your actions do not cause harm and are within the boundaries of the law.
Key Tools: Familiarize yourself with essential tools like Nmap for port scanning, OpenVAS for vulnerability scanning, and Wireshark for network traffic analysis.
3. Gain Practical Experience
Hands-On Practice: Use platforms like Hack The Box, TryHackMe, and Capture The Flag (CTF) competitions to practice your skills in a controlled environment.
Home Lab: Set up a home lab with virtual machines to simulate real-world scenarios and practice different hacking techniques.
Ethical Hacking Training: Enroll in online courses and bootcamps that offer structured learning paths, practical labs, and mentorship. Websites like Coursera, Udemy, and ACTE provide comprehensive ethical hacking training.
4. Obtain Relevant Certifications
Certified Ethical Hacker (CEH): This certification, offered by the EC-Council, covers a wide range of topics, including foot printing, scanning, enumeration, and hacking web servers.
Offensive Security Certified Professional (OSCP): This certification focuses on hands-on offensive security skills, with a heavy emphasis on practical experience.
CompTIA Security+: This certification provides a broad understanding of cybersecurity concepts and is a good starting point for beginners.
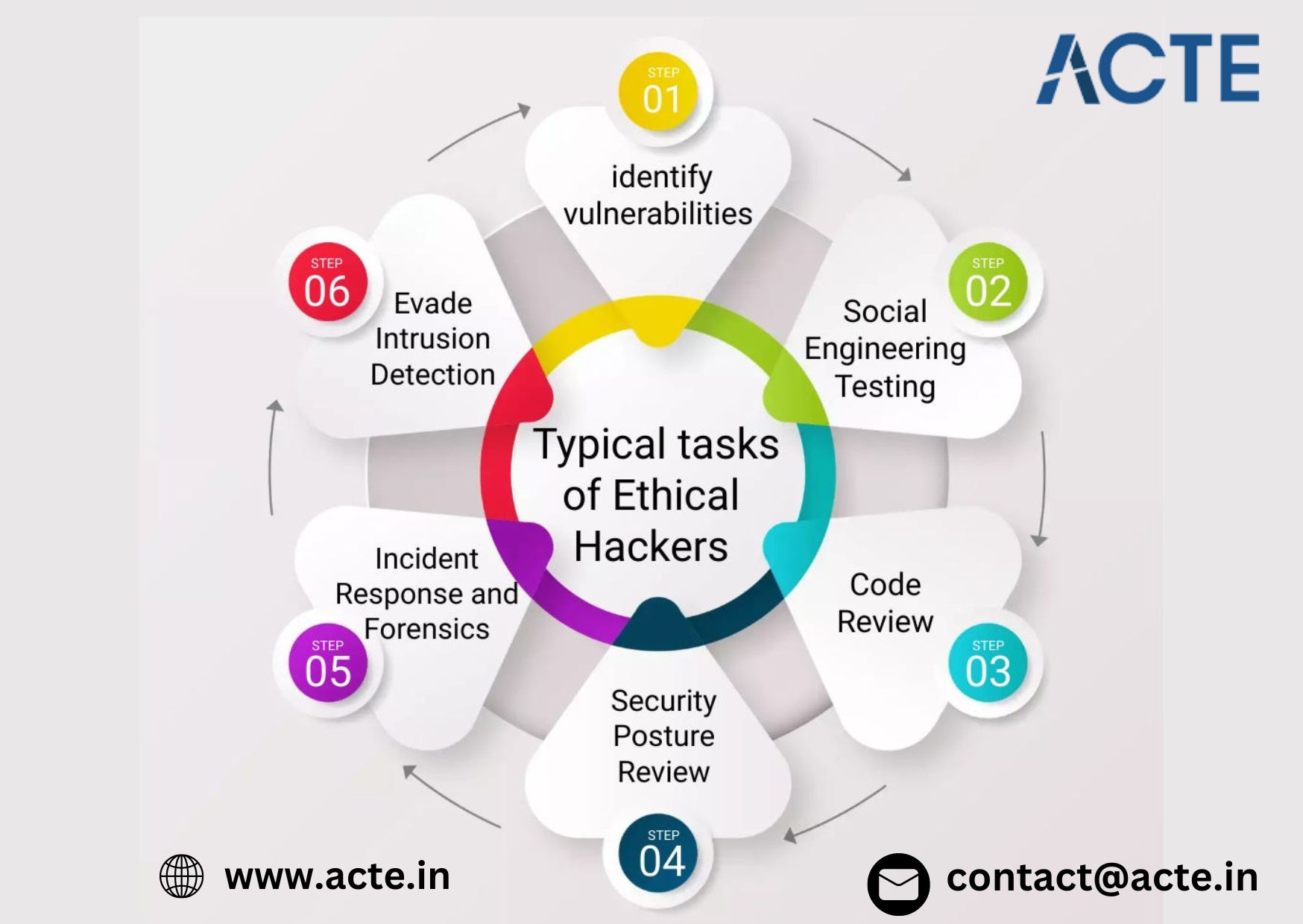
5. Stay Updated and Network
Conferences and Workshops: Attend events to connect with experts, gain insights, and seek mentorship from experienced professionals. If you're interested in advancing your skills in ethical hacking, consider exploring opportunities for ethical hacking online training. It's a convenient way to learn from industry leaders and enhance your expertise in cybersecurity. For more information on ethical hacking online training, visit Ethical Hacking Online Training.
Industry Trends: Stay informed about the latest vulnerabilities, threats, and trends by following cybersecurity blogs, news sites, and forums.
Professional Communities: Engage with communities such as the Information Systems Security Association (ISSA), (ISC)², and local hacking meetups to network and learn from other professionals.
CONCLUSION
An essential component of contemporary cybersecurity, ethical hacking is vital to the protection of digital assets and infrastructures. Ethical hackers assist companies in reducing risks and safeguarding sensitive data from hostile attacks by proactively detecting and fixing security flaws. The increasing sophistication and frequency of cyberattacks have led to a growing need for proficient ethical hackers, underscoring the significance of their knowledge in upholding strong security protocols.
Subscribe to my newsletter
Read articles from GnanaAslin 2000 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
