The Mechanics Behind the Internet
 Emmanuel Enchill
Emmanuel EnchillTable of contents
- Introduction
- The Client’s Preparation - Completing the Query
- Searching for the Address of the Domain Named google.com
- You Need to Transmit Genuine Packets
- Let Us Whisper Discreetly, Lest Eavesdroppers Comprehend
- At the Post of the MTTD of the Server Farm
- You Get Served by the Web Server
- Get Served Better, Prioritize the Preferences
- The Storage Vault
- Conclusion
Introduction
In the current digital era, searching the web has become second nature to millions worldwide.
Yet, behind this seemingly mundane action lies a complex web of processes and technologies that orchestrate our journey across the vast landscape of the internet.
Join me on an exploratory journey to peel back the mystery surrounding the quintessential question: What happens when you type google.com into your browser and press the enter key?
In this writeup, we will delve into web protocols, server interactions, and data transmissions and uncover the intricate dance between user input and the labyrinth of interconnected systems that ultimately deliver the desired pages to the screens from the point of view of a boy named Kay.
Kay, a primary four pupil, rushes home to grab his laptop, which he had received the previous day as a birthday gift from his uncle. He quickly turns it on. After the initial setup, he is now determined to hit the World Wide Web to learn more about a topic he had barely grasped the concepts during the history lesson earlier that day.
He fires up the browser, turns on the Wi-Fi, quickly types google.com in the search bar, and hits the enter key. He remains still, his eyes on the screen as his uncle’s voice echoes in his mind, reminding him that Google will always help him find what he wants on the web.
The Client’s Preparation - Completing the Query
Upon pressing the enter key, the browser (client) converts the address Kay typed into https://www.google.com/.
The complete address is a Uniform Resource Locator (URL) used to access resources on the internet. It is a specific type of Uniform Resource Identifier (URI) that provides a means of locating the resource by describing its primary access mechanism.
The URL consists of the scheme and the host. The scheme specifies the protocol the browser is using to access the resource. Some popular schemes include http, https, and ftp. The host is the domain name of the Internet Protocol (IP) address for the server where the resource is.
Kay’s client (the browser) uses the HTTPS protocol scheme to request the resources at the host, www.google.com.
Searching for the Address of the Domain Named google.com
Resources we request on the internet are on various servers around the world. Each server has an IP address that enables it to communicate with agents, such as browsers, APIs, other servers, etc. These addresses are either IPv4 or IPv6.
The IPv4 is an address with four numbers separated by dots, as in 127.0.0.1. The IPv6 is an eight-hexadecimal number separated by colons. An example is 2001:0db8:85a3:0000:0000:8a2e:0370:7334
IP addresses are difficult to internalize, left alone to remember. Technology known as Domain Name System (DNS) stores the IP addresses. This system forms the phone book of the internet. A DNS resolver, a crucial part of the DNS infrastructure, converts domain names to their equivalent IP addresses.
Immediately after rewriting the URL, the client begins its quest with the DNS lookup. It first checks its local cache for the IP address of the requested domain. If not found, it checks the operating system (OS) cache and proceeds to the router’s cache if it is not found in the OS cache.
If the address is still not found in the router’s cache, the client looks up the Internet Service Provider (ISP). If not found there, the ISP initiates a DNS lookup by pinging other DNS resolvers, which will ping others to get the IP address. When found, the address of google.com, 216.58.209.78, is returned to the client.
It is important to note that the IP address varies based on the geographical location of the client and the network infrastructure.
A Memorandum of Understanding to Connect
The client now has the IP address of the domain it requested for. It connects to the server holding the resources using the Transmission Control Protocol (TCP) and the Internet Protocol (IP).
The TCP/IP are communication protocols that specify and control how data transfers over the internet. The IP provides a unique address to each node on the network and controls the routing of data packets from one communication device to the other. Aside from the IP, other protocols like the User Datagram Protocol (UDP) and the File Transfer Protocol (FTP) are available.
The TCP ensures reliable data transmission by addressing issues related to lost, duplicate, out-of-order, and corrupted packets. It organizes data into segments and guarantees their integrity during the transfer.
A packet is a piece of the message transferring over the internet. Each packet has three main parts; header, payload, and trailer. The header describes the packet’s contents, origin, and destination. The payload is the actual data, and the trailer is the footer of the packet.
With the IP address at hand, the browser initiates a three-way handshake with the server. It first sends a packet known as SYN, short for Synchronize. It indicates to the server its intention to establish a connection.
Upon receipt, the server analyzes the packet and determines if it is safe to connect with the client. If it is deemed safe, the server responds with a SYN-ACK packet, which is short for Synchronize–Acknowledge. This packet informs the client of the server’s readiness to connect.
The client finally acknowledges the receipt of the response by sending an ACK packet, which is short for Acknowledge, connecting, and paving the way for them to communicate.
You Need to Transmit Genuine Packets
Before a packet of the client's request reaches the server, it undergoes evaluation by a security system, namely the firewall.
A firewall is a network security device and, or program that monitors and filters incoming and outgoing network traffic based on established policies. It ensures only safe and authorized packets pass through to the servers.
The hardware security device, positioned between a network and the internet, keeps the local network safe from malicious activity emanating from the internet.
The software firewall is installed on a server and configured to ensure that only authorized packets pass to the servers.
As such, even before the first SYN packet of the client reaches the server, it is evaluated by the firewall.
Let Us Whisper Discreetly, Lest Eavesdroppers Comprehend
The client has successfully passed the security checks and established a connection with the server.
They proceed to communicate discreetly, capitalizing on the security of the Hypertext Transfer Protocol Secure (HTTPS) and the Transport Layer Security (TLS), formerly Secure Socket Layer (SSL).
HTTPS is a communication protocol that enables the server and the client to communicate. It is part of the application layer and manages the communication between servers and browsers, executing tasks such as transferring files, retrieving web pages, and sending emails.
HTTPS is the secure form of HTTP, with the ‘S’ denoting that all the communications between the browser and the server are encrypted. The web browser will indicate a padlock icon next to the address bar for secured websites. This encryption is activated using the Secure Socket Layer.
The SSL is the standard technology for securing and safeguarding sensitive data transmitted over the network. The encryption uses algorithms to scramble the data in transit. The scrambled data, even if it happens to be intercepted by hackers, appears to be random gibberish, thus preventing unauthorized persons from understanding the contents of the data.
Despite its wide use, the SSL has been deprecated and replaced with Transport Layer Security (TLS). The TLS is a cryptographic protocol designed for secure communication over a computer network. It ensures privacy and integrity by encrypting the data, supports server authentication, and establishes a secure connection between the client and the server.
The encryption is one of the factors that assures Kay of the safety of his identity and the contents of his searches and messages as he uses the internet.
At the Post of the MTTD of the Server Farm
Kay’s client is just one in a billion requesting google.com. Given the volume of these requests, companies employ the traffic regulation technology, the load balancer, to manage the traffic flow.
A load balancer is a technology that efficiently regulates incoming traffic from clients among the server farm. This technology conceals the configuration of the servers from the clients; all the responses will appear to come from the same server.
Load balancing technology uses algorithms to manage traffic to the servers. There are various algorithms currently in use. Among them include the random, the round-robin, the fastest, the least connections, the observed, and the predictive algorithms.
These algorithms model the load balancer as the intermediary between the client and the servers, performing tasks including efficient traffic distribution, acting as an HTTP reverse proxy, and caching of contents and images to reduce the traffic load to the servers. These improve user experience, enhance security and resilience, and facilitate website scaling.
In the event of server downtime due to poor health, corruption of programs, faulty hardware infrastructure, or other factors, the load balancer transfers its traffic to the next available server.
You Get Served by the Web Server
The Google web server serving the static files required to build the google.com frame receives the request from the load balancer.
A web server is a technology that handles HTTP requests from clients and serves static content. Various web servers exist, such as the Apache HTTP Server, Nginx, and Microsoft Internet Information Service (IIS).
These servers deliver static files such as HTML, CSS, JavaScript, and images to clients without modification. They manage incoming HTTP requests and send appropriate responses such as 200 OK for successful retrieval of resources or 404 NOT Found for the unavailability of the resources.
Web servers can also modify URLs or redirect requests to different URLs for better resource management and act as a load balancer. Companies like Google receive billions of requests daily; they may specialize their servers by dedicating servers to serve images, CSS, HTML, or JavaScript files.
In this scenario, a web server requests the static resources from the other servers, assembles them, and puts them on standby, ready to serve them packet by packet, improving the performance and reliability of the servers.
Get Served Better, Prioritize the Preferences
Although the client's requests are static files, some of the requests will be dedicated to the application server by the web server.
The application server hosts web applications and provides dynamic content by executing server-side scripts and programs. Some application servers include Apache Tomcat, Microsoft .NET Framework, Node.js, and Django.
Aside from providing dynamic web pages, the application server also manages the business logic of applications, ensuring that data is processed correctly before being sent to the client. It also communicates with the database to store and retrieve contents requested by the user and maintain user sessions, including user state and authentication.
The application server differs from the web server in several respects. A web server optimizes the delivery of static content. An application server, on the other hand, focuses on processing application logic, which can be resource-intensive.
A web server can operate independently or in conjunction with an application server. However, the application server typically requires a web server to handle initial HTTP requests and pass them to the application server for processing.
In the case of the request by Kay’s client, Google’s application server will manage account preferences and a host of other settings and processes as Kay continues to use the internet.
The Storage Vault
Companies keep track of website visitors by collecting anonymous data about them as they browse. They utilize this data to enhance their services, products, and visitors’ browsing experience. The collected data persists in databases.
A database is an organized collection of structured information or data stored electronically in a computer system. It consists of a Database Management System (DBMS), a Schema, and a query language. It allows for efficient storage, retrieval, and manipulation of the data.
After gathering the necessary static resources, the web server forwards requests for dynamic contents, if any, to the application server interacting with the database. The application server uses the DBMS to send queries, retrieve data, and update records based on the business logic.
Despite requesting static content, Google’s web server will forward vital metadata about Kay to the application server for the database. The saved data is for personalizing Kay’s browsing experience.
The image below, sourced from the internet summarizes the process.
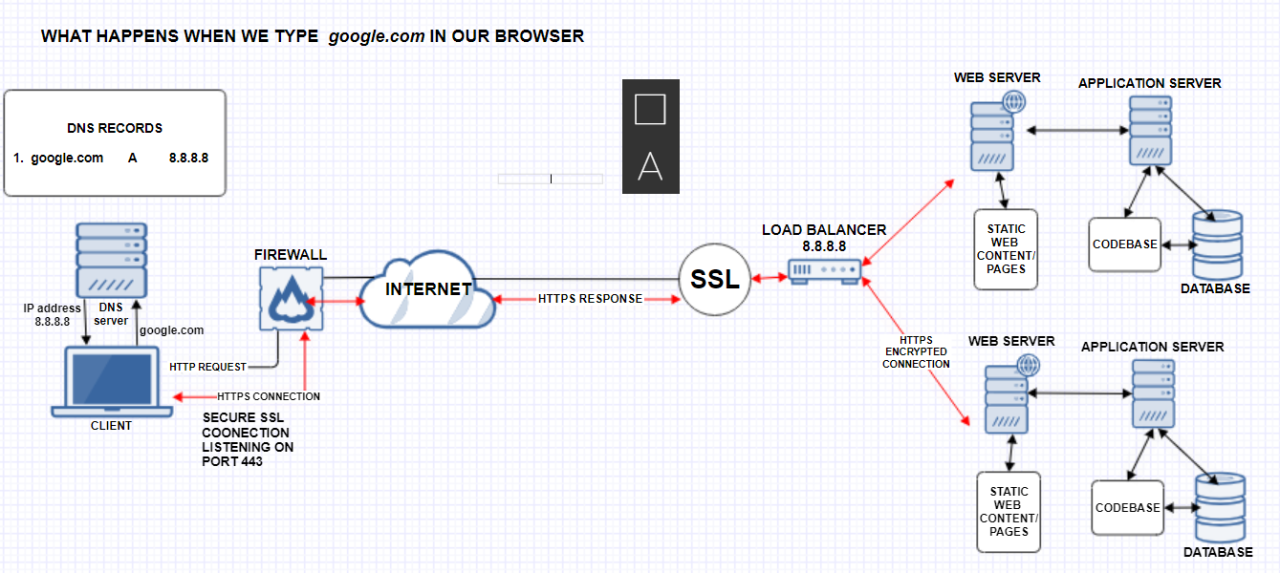
Conclusion
In conclusion, the journey that unfolds when you type "google.com" into your browser and press enter involves fascinating technological interactions and processes.
The instantaneous process is a complex dance of networking, server-side logic, and client-side rendering, all working jointly to deliver a seamless browsing experience.
Understanding this intricate sequence not only underscores the sophistication of modern web architecture but also highlights the remarkable engineering that powers everyday internet use.
After the browser renders the page, Kay smiles, clicks in the search bar, and begins typing, “Which ethnic group in Ghana was first to …”
Subscribe to my newsletter
Read articles from Emmanuel Enchill directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Emmanuel Enchill
Emmanuel Enchill
I am a passionate software engineer in training at ALX. I have a strong preference for back-end development. I am on course to share my learning journey with you.