Establish a Secure Connection between GitHub Actions and Google Cloud Platform (GCP) using Workload Identity Federation.
 Merlin Saha
Merlin Saha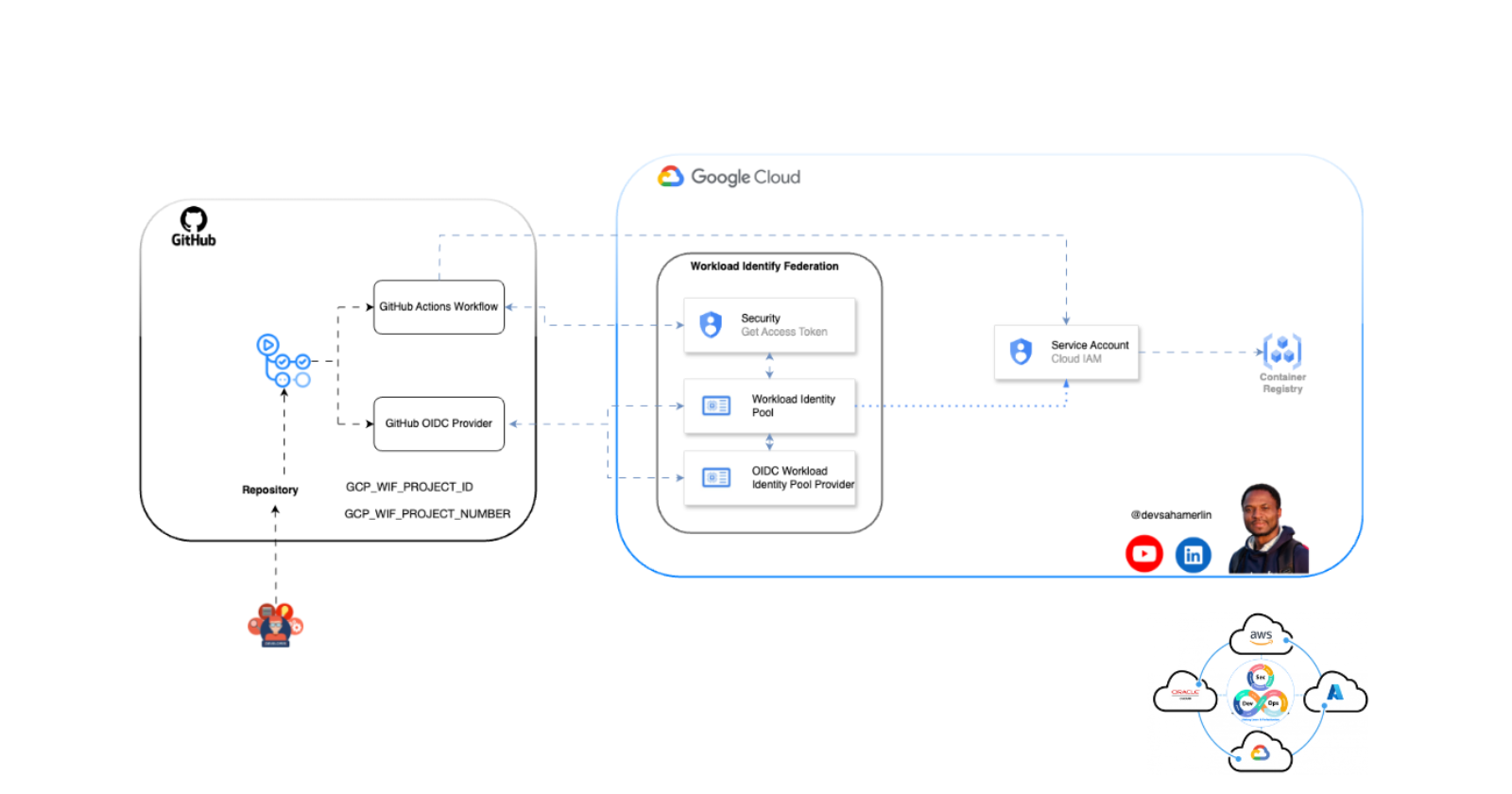
GitHub Actions makes it easy to automate your software development workflows, including building, testing, and deploying your applications to various environments. When deploying to Google Cloud Platform (GCP), you typically need to authenticate with GCP using a service account key. However, managing and rotating these keys can be cumbersome and pose a security risk if the keys are accidentally exposed.
Workload Identity Federation is a feature in GCP that allows you to securely authenticate to GCP services without needing to manage service account keys. Instead, you can use a Google Cloud identity (such as a service account) to grant access to your GitHub Actions workflow, and GCP will automatically authenticate the workflow based on the configured identity.
Here's how to set it up:
Create Workload Identity Federation Pool and Provider in GCP
Go to the IAM & Admin section and click on Workload Identity Federation in the GCP Console and click on "CREATE POOL".
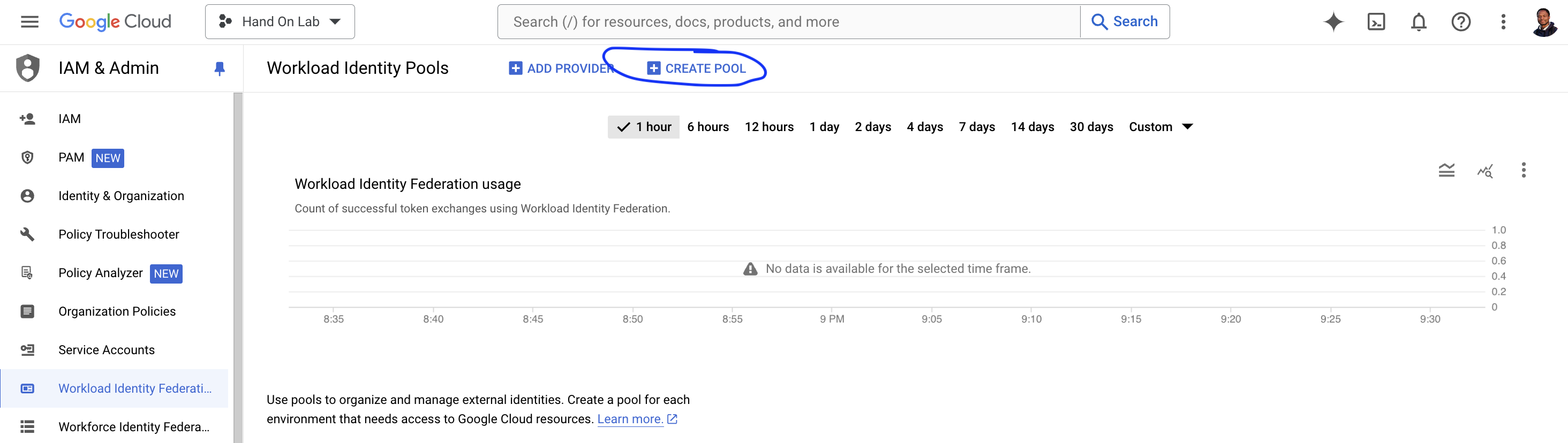
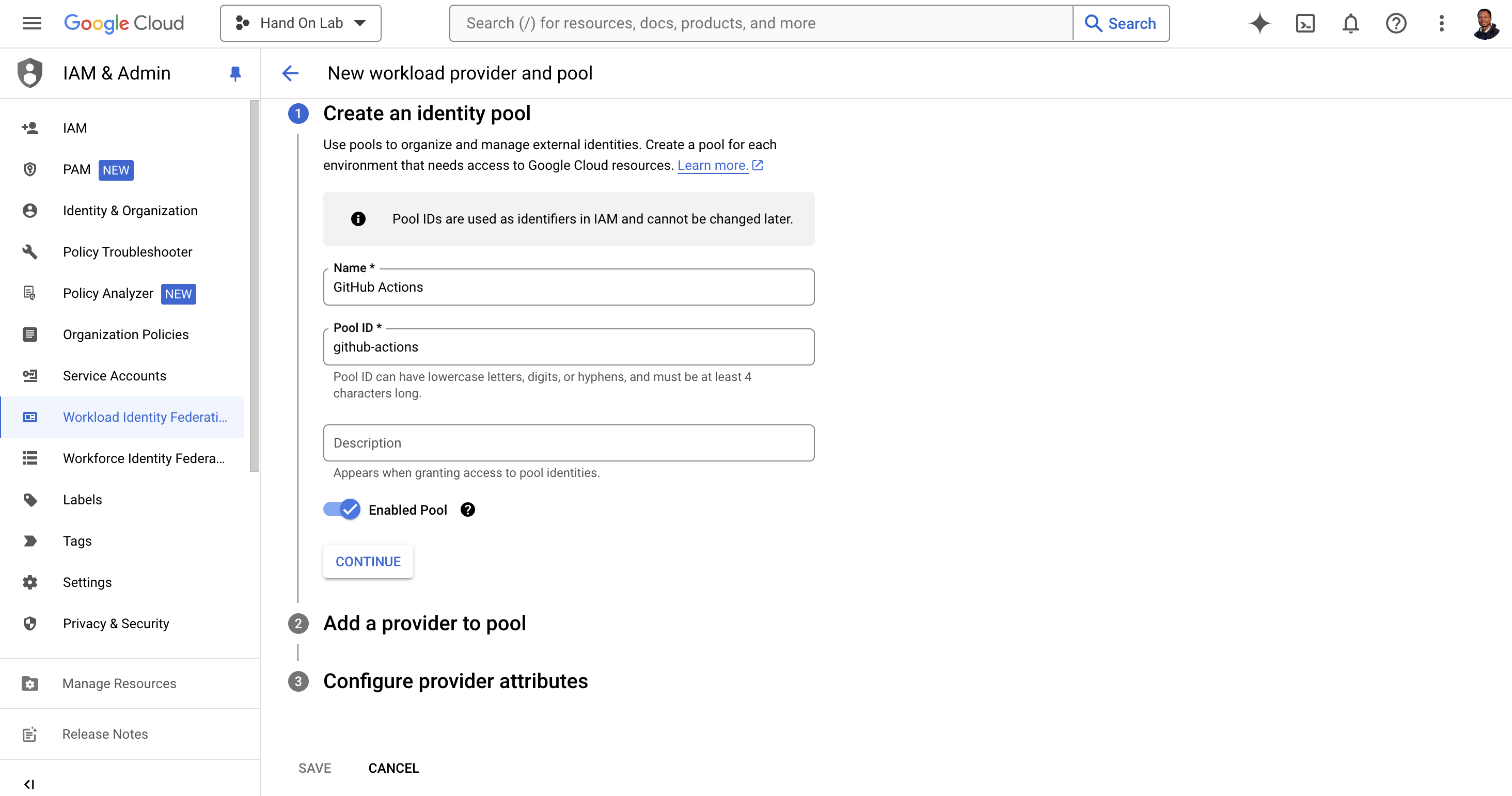
Create an identity pool: Specify the required information and click on "CONTINUE"
Add a provider to pool: select
OpenID Connect (OIDC)in Select a provider and addhttps://token.actions.githubusercontent.comin Issuer (URL)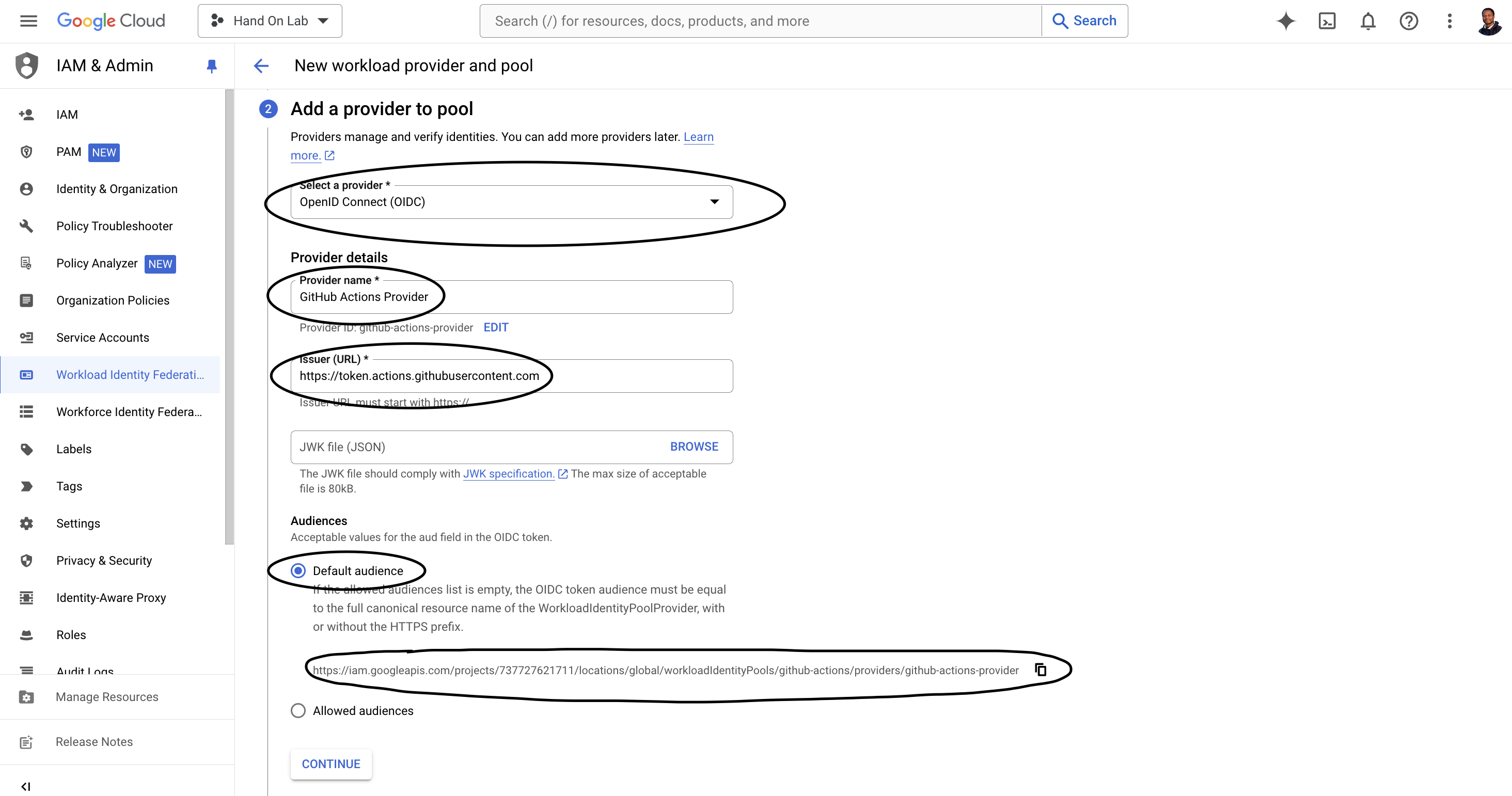
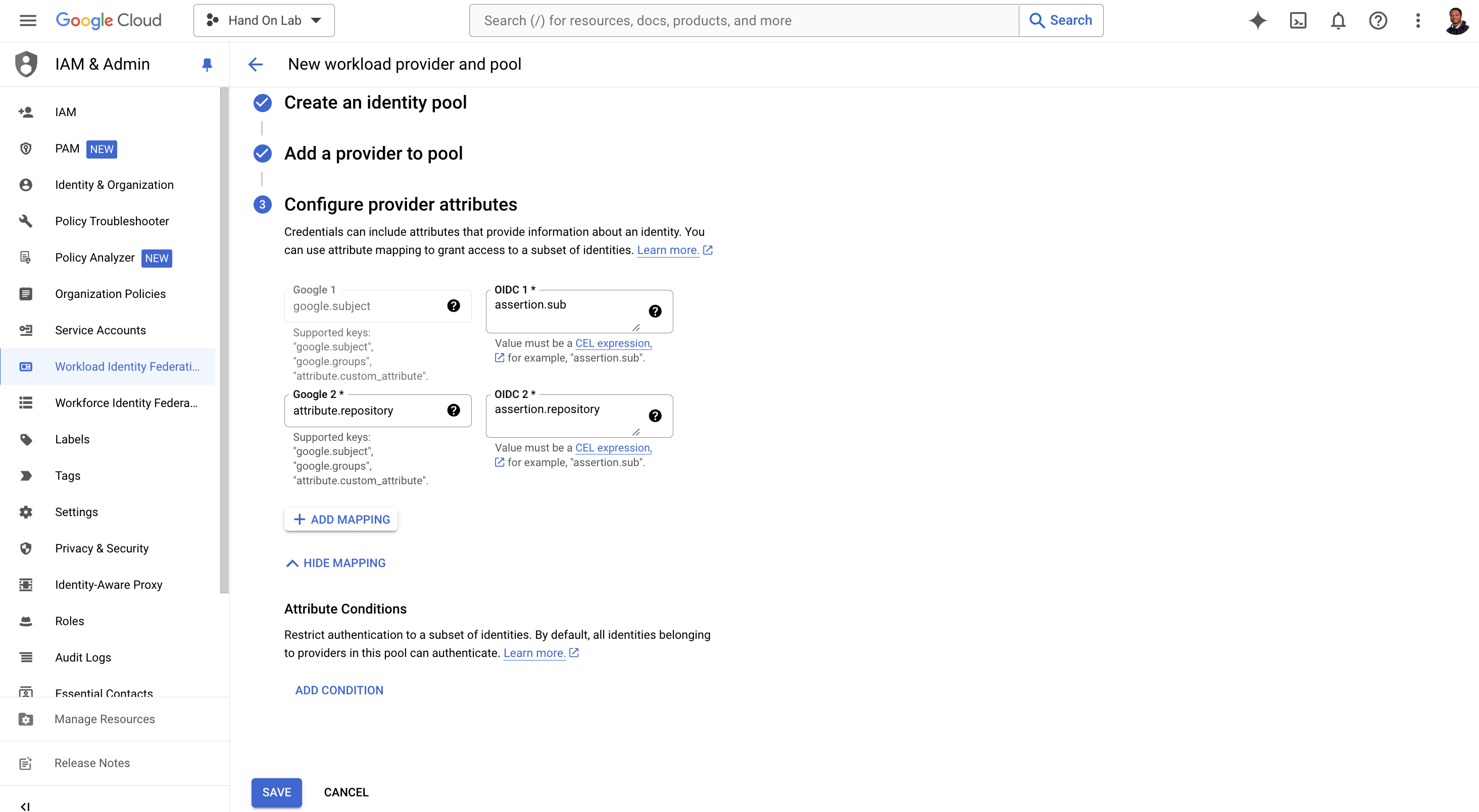
Configure provider attributes as like this:
google.subject = assertion.sub attribute.repository = assertion.repositorySave the pool andprovider
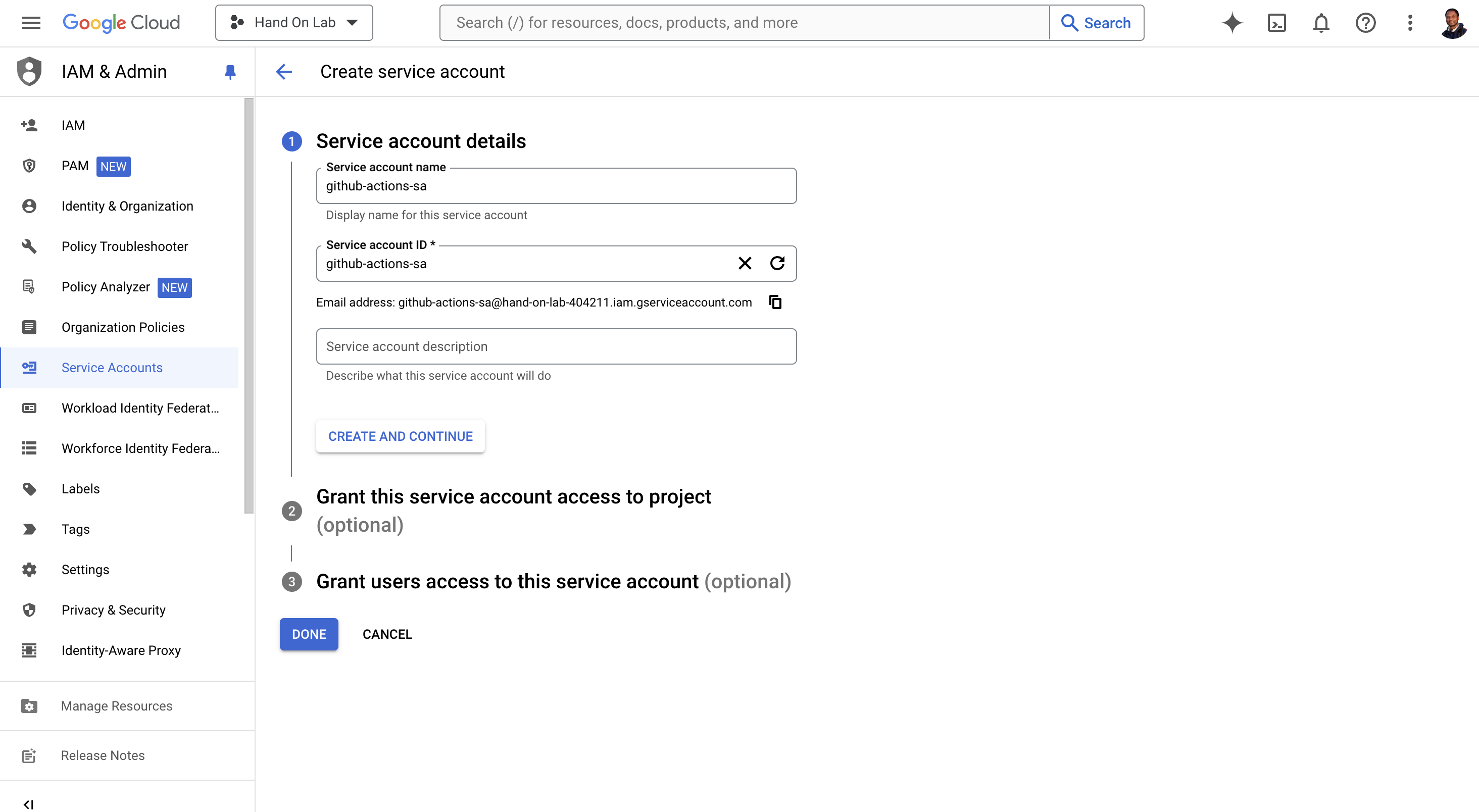
Create a Google Cloud service account
Go to the Service Accounts section in the GCP Console.
Click "Create Service Account."
Provide a name for the service account (e.g., "github-actions-sa").
Optionally, you can add a description.
Click "Create and Continue."
On the next screen, skip granting roles for now, and click "Done."
Grant required role to Google Cloud service account
roles/iam.workloadIdentityUser # And Add Annother Role your need to specific task, eg: roles/artifactregistry.writer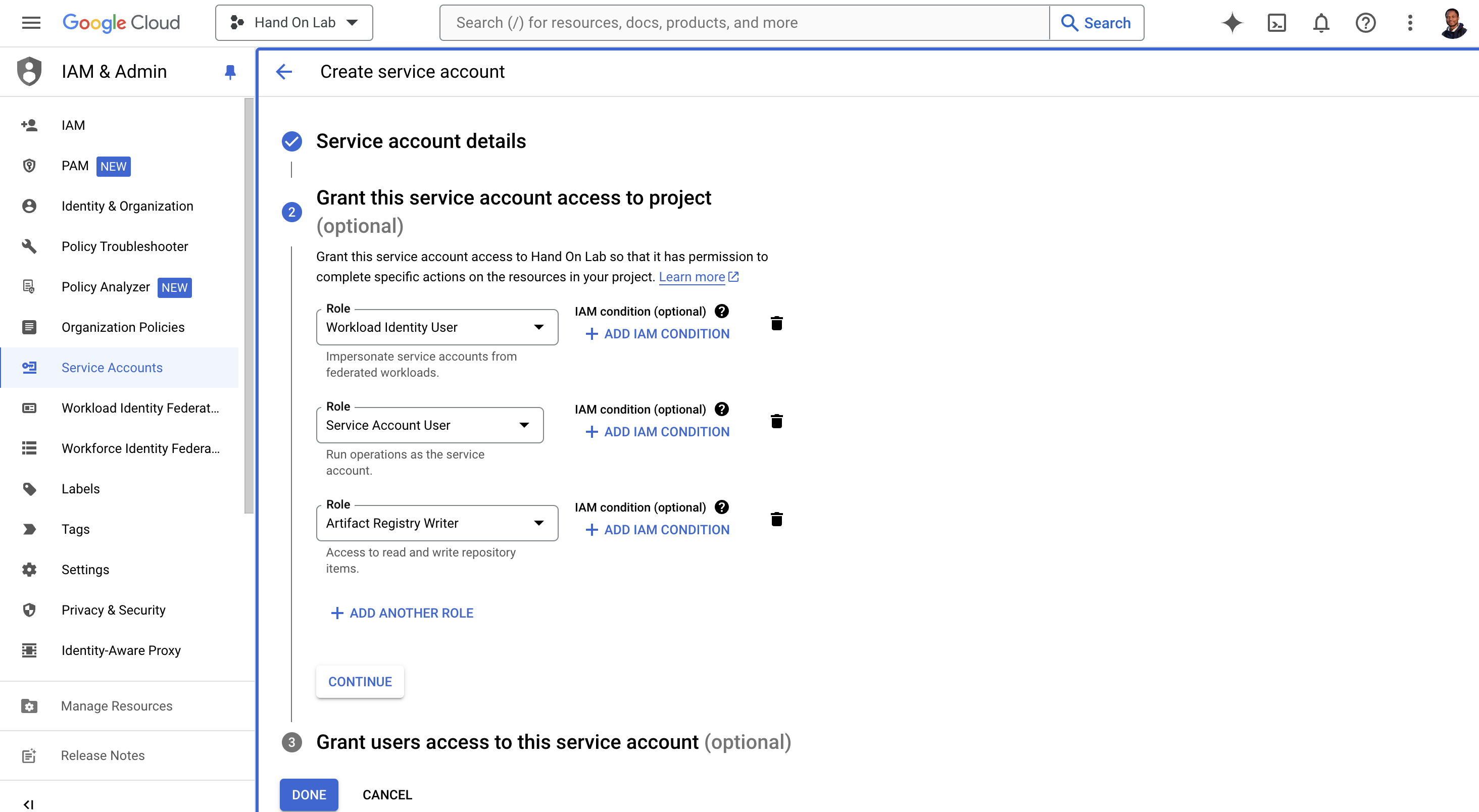
Click on "DONE"
UpdateWorkload Identity Federation to add service github-actions-sa@<project_id>.iam.gserviceaccount.com
Click on GitHub Actions Display Name
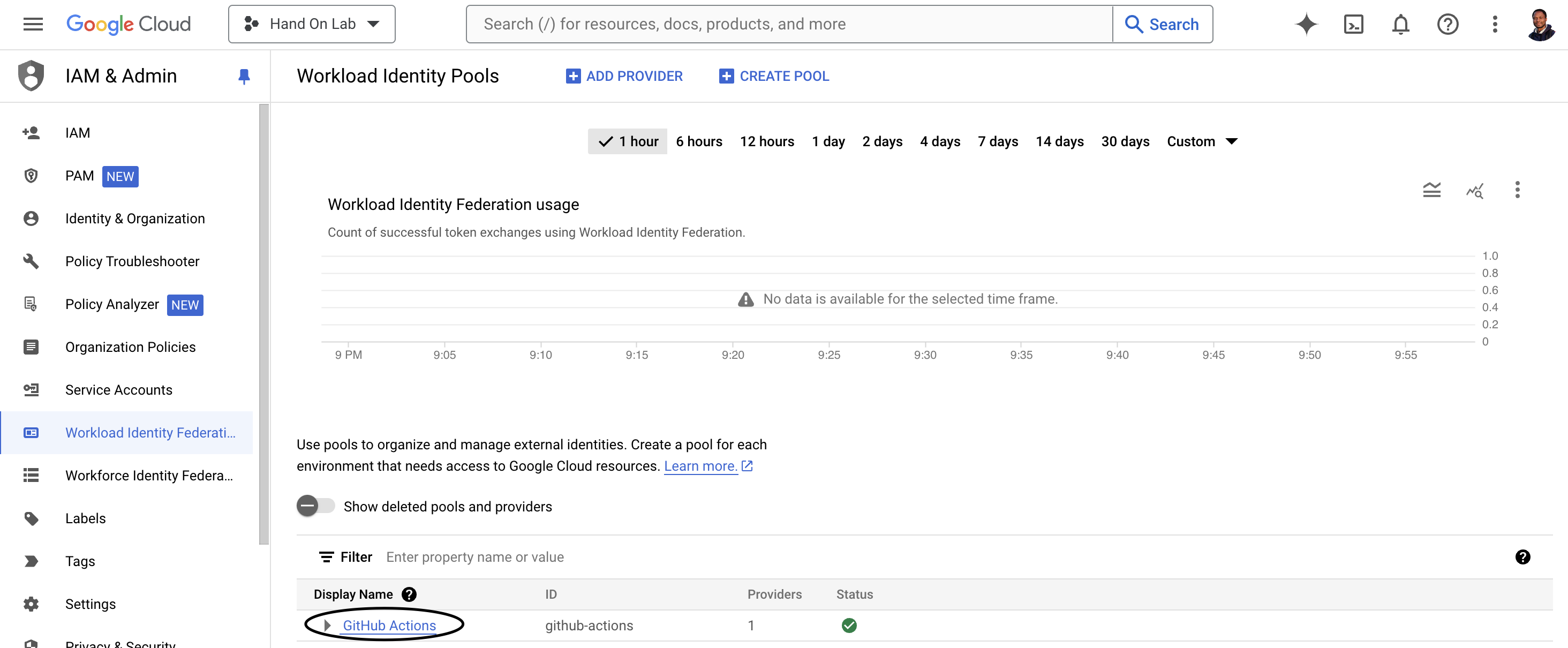
And Click Grant Access
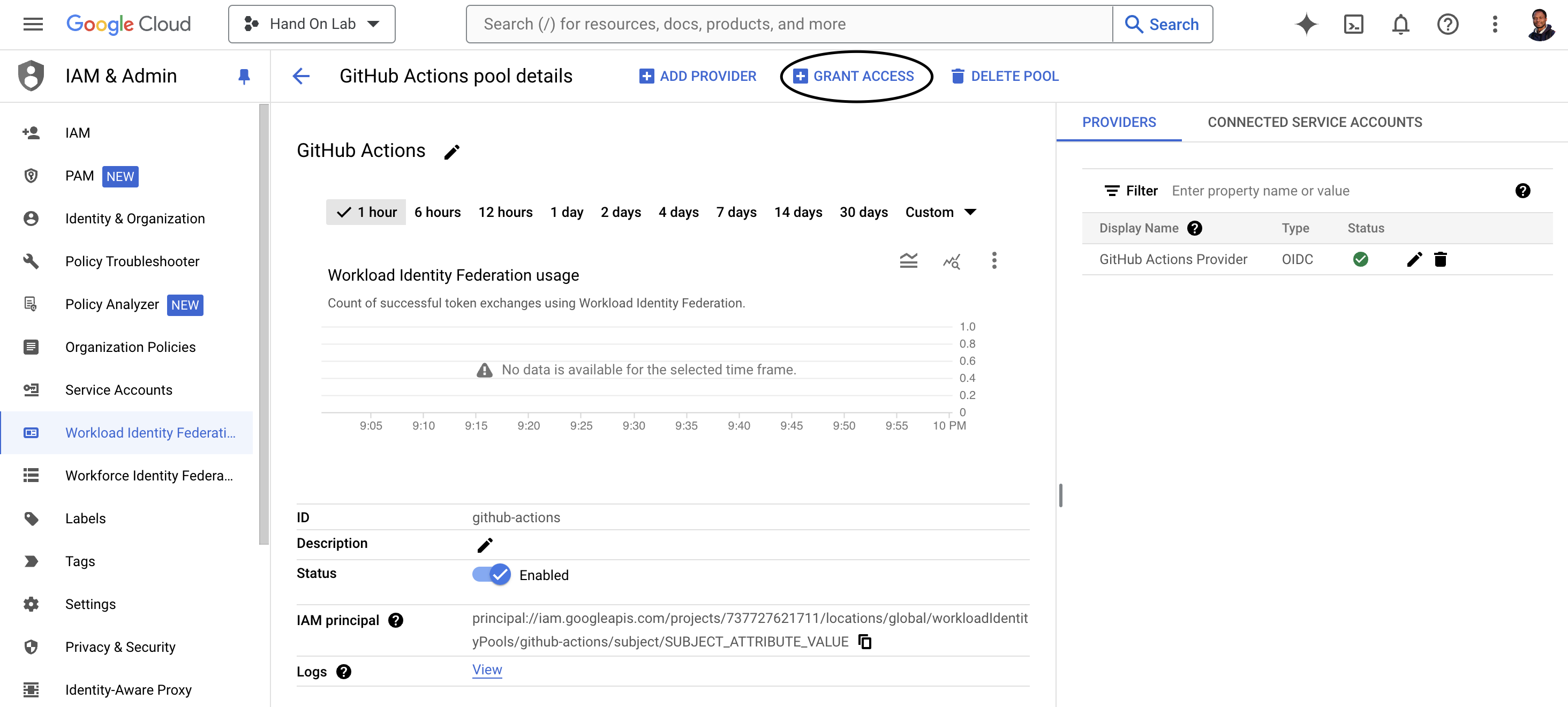
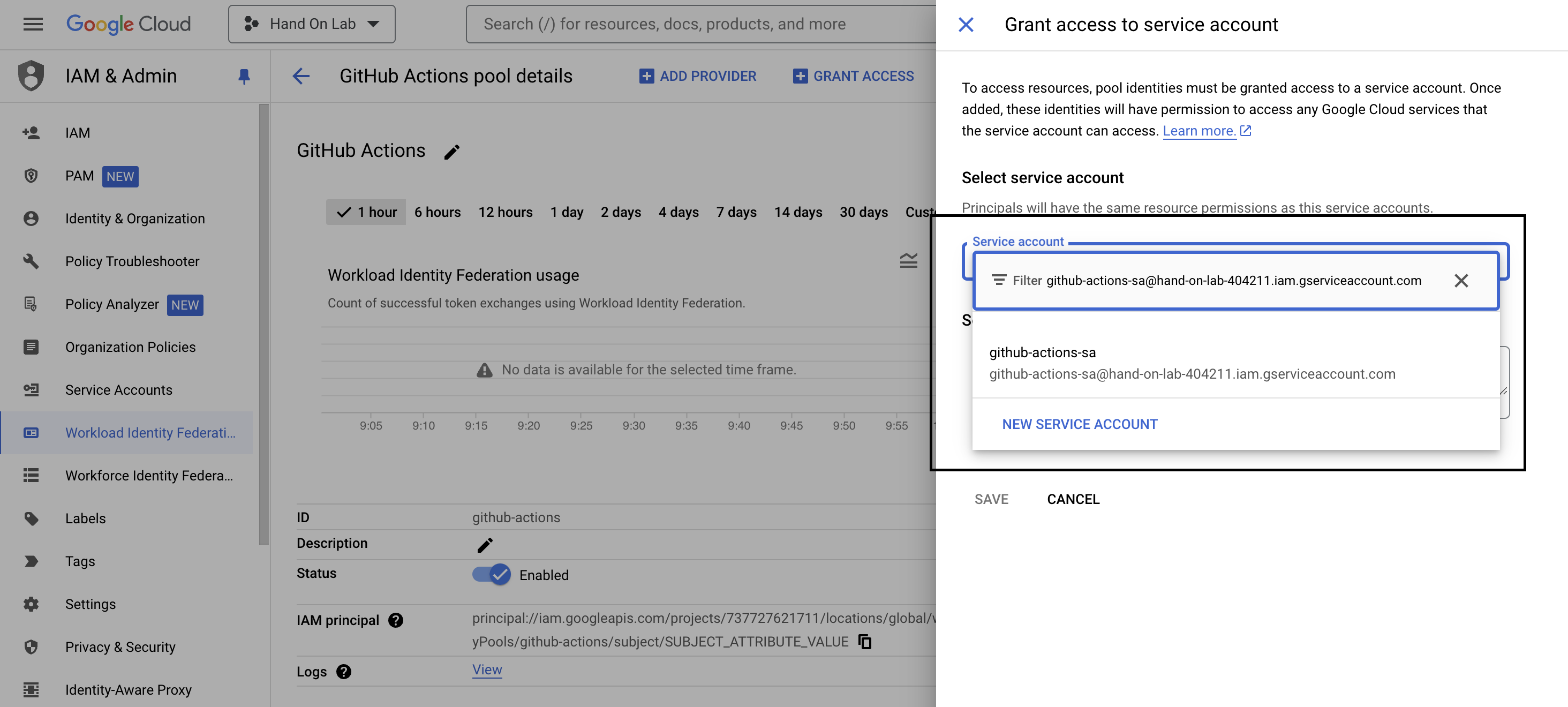
Add your SA email
Add your GitHub Repository like this:
github_account/github_repositoryand Click on "SAVE" in the popup page, click on DISMISS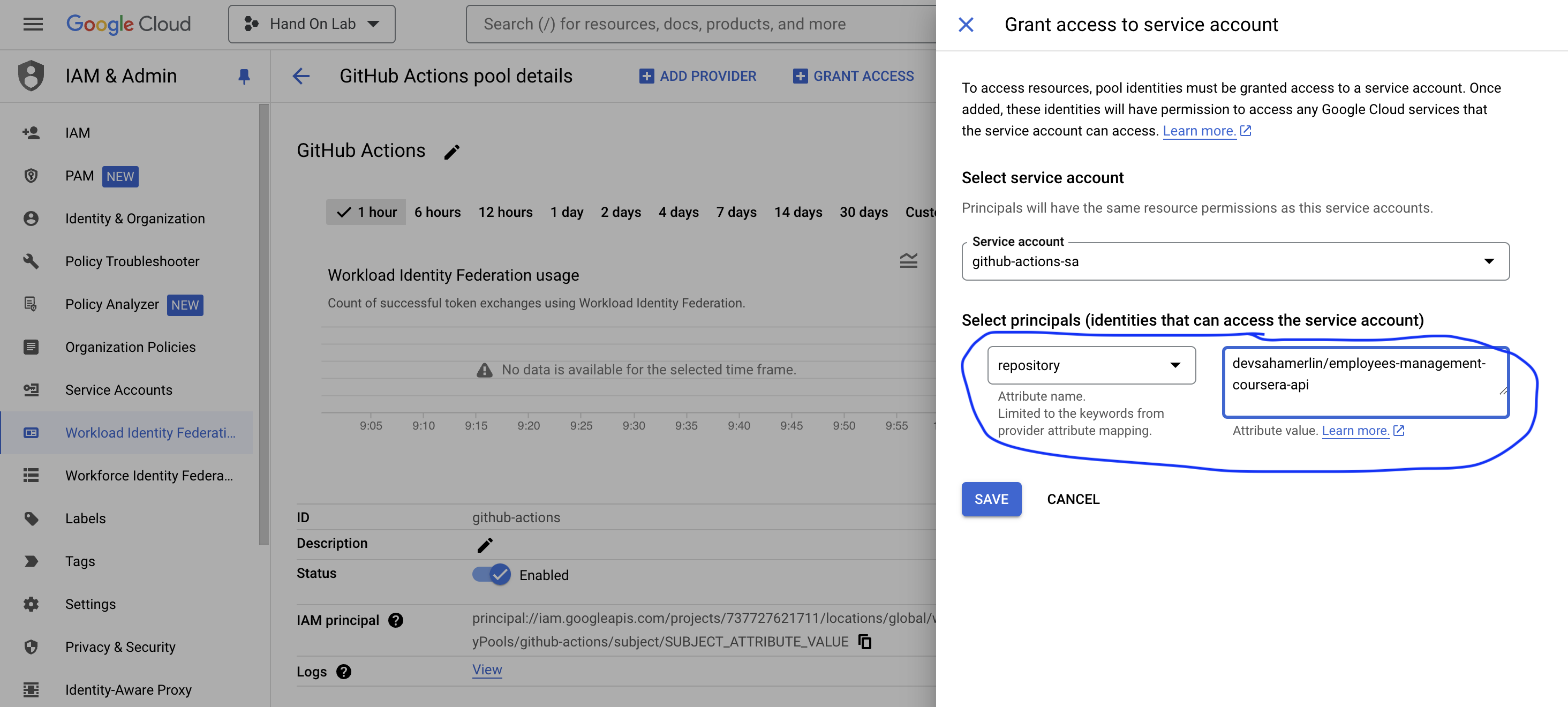
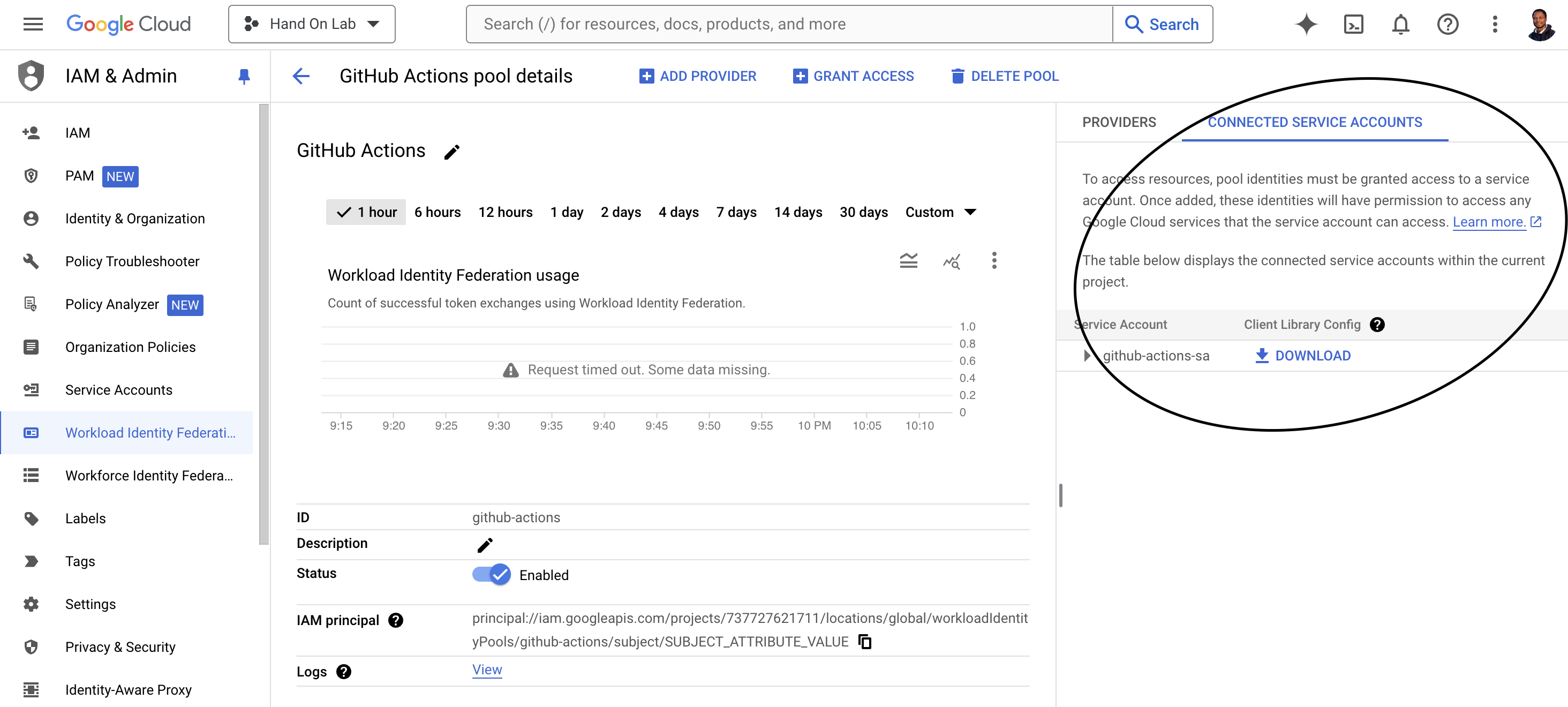
Your provider CONNECTED SERVICE ACCOUNTS should look like this
Use Workload Identity Federation in your GitHub Actions workflow
Copy Pool ID and Provider ID in Workload Identity Federation in this case is
github-actionsandgithub-actions-provider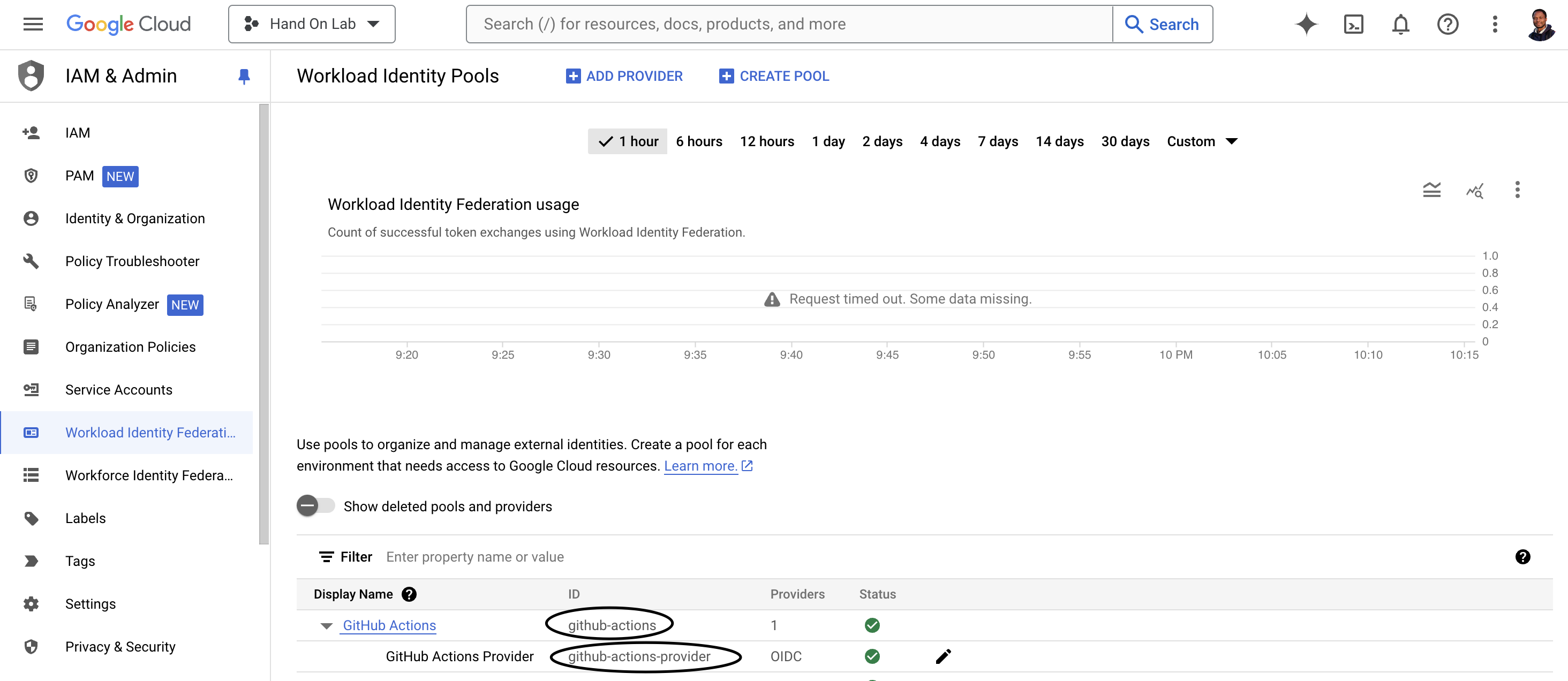
In your GitHub repository, create a new workflow file (e.g.,
.github/workflows/upload.yml).In the workflow file, add the following step to authenticate with GCP using Workload Identity Federation: change
<GCP_PROJECT_NUMBER>and<GCP_PROJECT_ID>- id: 'auth' name: 'Authenticate Google Cloud' uses: 'google-github-actions/auth@v1' with: create_credentials_file: true workload_identity_provider: 'projects/<GCP_PROJECT_NUMBER>/locations/global/workloadIdentityPools/github-actions/providers/github-actions-provider' service_account: 'github-actions-sa@$<GCP_PROJECT_ID>.iam.gserviceaccount.com'Replace the
workload_identity_providervalue with the one you configured in step 3, and theservice_accountvalue with the email address of the service account you created in step 2.After the authentication step, you can use the authenticated context to interact with GCP services, such as deploying to Cloud Run, uploading files to Cloud Storage, or running commands on Compute Engine instances
Full code exemple: https://github.com/devsahamerlin/employees-managements-api
Congratulations! By using Workload Identity Federation, you no longer need to manage and rotate service account keys manually. GCP will automatically authenticate your GitHub Actions workflow based on the configured identity, providing a more secure and convenient way to authenticate to GCP services.
Note that, this is a high-level overview of the process, and you may need to adjust the configuration based on your specific requirements and GCP project setup.
Subscribe to my newsletter
Read articles from Merlin Saha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Merlin Saha
Merlin Saha
Specialising in Cloud Architecture and Application Modernisation, Saha Merlin is a Cloud Solutions Architect and DevSecOps Specialist who helps organizations build scalable, secure, and sustainable infrastructure. With six years of specialized experience in highly regulated industries—split equally between insurance and finance—he brings deep understanding of compliance requirements and industry-specific challenges to his technical implementations. His expertise spans various deployment models including Container-as-a-Service (CaaS), Infrastructure-as-a-Service (IaaS), and serverless platforms that drive business outcomes through technical excellence. He strategically implements open source technologies, particularly when SaaS solutions fall short or when greater control and autonomy are essential to meeting business requirements. Saha integrates DevSecOps practices, Green IT principles to minimize environmental impact, and Generative AI to accelerate innovation. With a solid foundation in Software Engineering and nine years of diverse industry experience, he designs cloud-native solutions that align with both industry standards and emerging technological trends.