Optimizing Authentication Flow : A Deep Dive into Access & Refresh Tokens
 Mihir Chaple
Mihir Chaple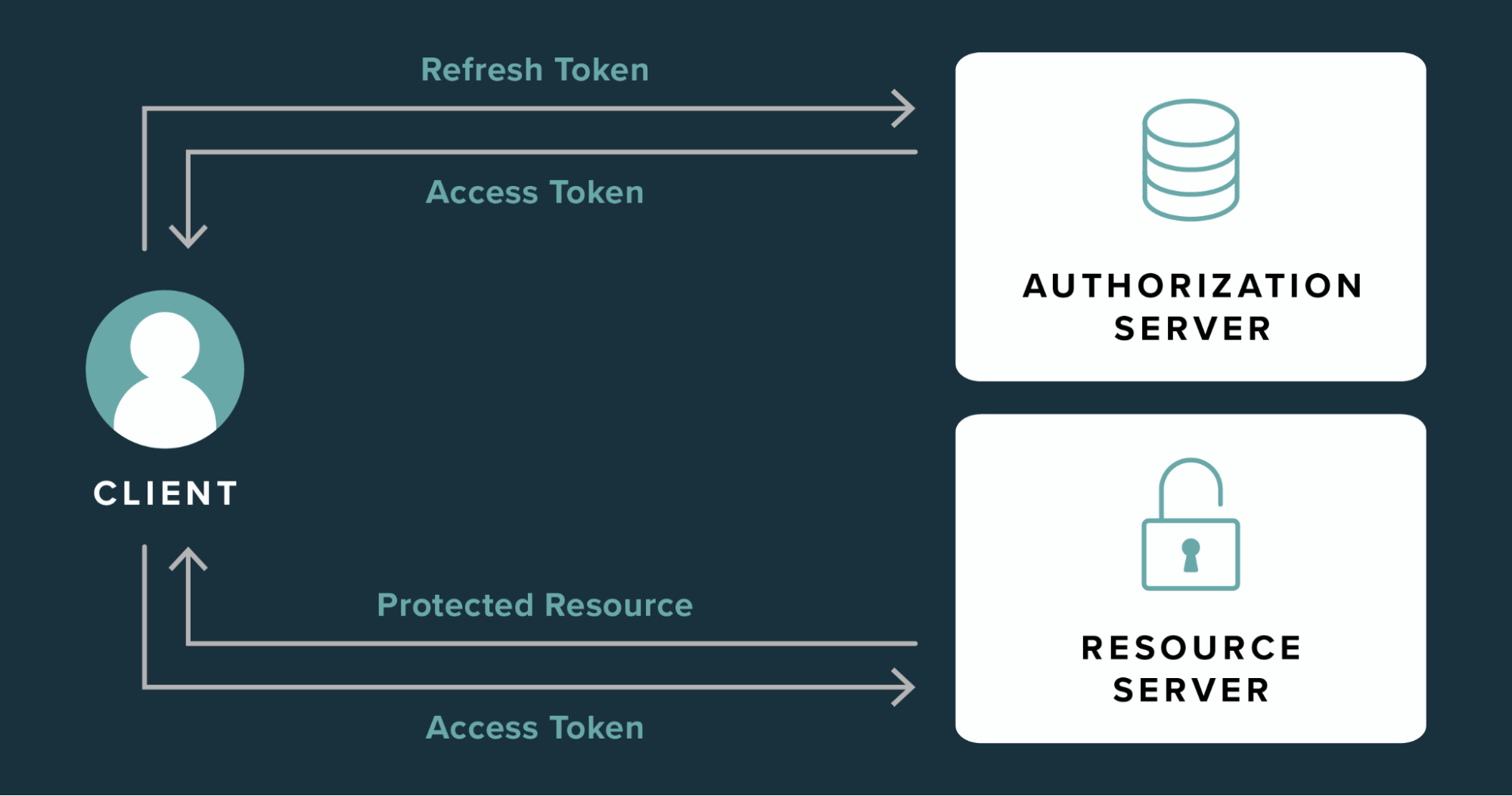
What is Access Token ?
Access tokens are used in token-based authentication to allow an application to access an API. The application receives an access token after a user successfully authenticates and authorizes access, then passes the access token as a credential when it calls the target API. The passed token informs the API that the bearer of the token has been authorized to access the API and perform specific actions specified by the Scope that was granted during authorization.
What is Refresh Token ?
It is a unique token that is used to obtain additional access tokens. This allows you to have short-lived access tokens without having to collect credentials every time one expires. Refresh tokens, stored as HTTP-only cookies, enable prolonged re-authentication without exposing sensitive information to client-side JavaScript.
Difference between Access Token and Refresh Token ?
In Terms of duration :
Access Token : Generally refresh token are short lived ranging from minutrs hrs upto one day.
Refresh Token : Generally access token are long lived ranging from 1, 5 or upto 10 days in some scenarios.
In Terms of data collection :
Access Token : Contains large amount of information as compared to refresh token, may contain all the data of the user to generate access token.
Refresh Token : Contains little amount of data as compared to access token , mainly contains userid password and some other field as per requirements as it is use for generate token for long term access to the user.
In terms of Authentication and authorization :
Access Token : Access token plays major role in authentication.
Refresh Token : Refresh tokens play a critical role in maintaining authorization while improving user experience.
In terms of usage :
Access Token :
Grants access to protected resources: The primary function is to authorize access to specific functionalities or data on a server.
Short-lived for security: Designed to expire quickly (minutes) to minimize the risk of unauthorized access if compromised.
Sent with authorization requests: Included in the header of API calls to verify the user's identity and permissions for that specific action.
Refresh Token :
Obtains new access tokens: Used by the client application to acquire fresh access tokens without prompting the user to re-login.
Maintains user sessions: Enables applications to maintain user sessions for extended periods by refreshing access tokens before they expire.
Longer lifespan for convenience: Issued with a longer validity period (days/weeks) compared to access tokens to avoid frequent login prompts.
Stored securely: Must be kept confidential on the authorization server due to its role in obtaining new access tokens.
Tech stack combination that can be used for the development :
Server-Side Languages : Java, Python, Node.js, PHP etc.
Security Libraries: JWT (JSON Web Token)
Databases : Sql, NoSql, MongoDB
Closure :
From the above document we can come to conclusion that using Access Tokens and Refresh Tokens increases the usability promotes more safer and secure environment in terms of authentication as well as authorization . Also, one of the best libraries to do so is JWT (JsonWebToken) and which is advised to use with languages such as JavaScript..
! ! Thanks for visiting !!
Subscribe to my newsletter
Read articles from Mihir Chaple directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
