Understanding Cross-Site Request Forgery (CSRF)
 Cloud Tuned
Cloud Tuned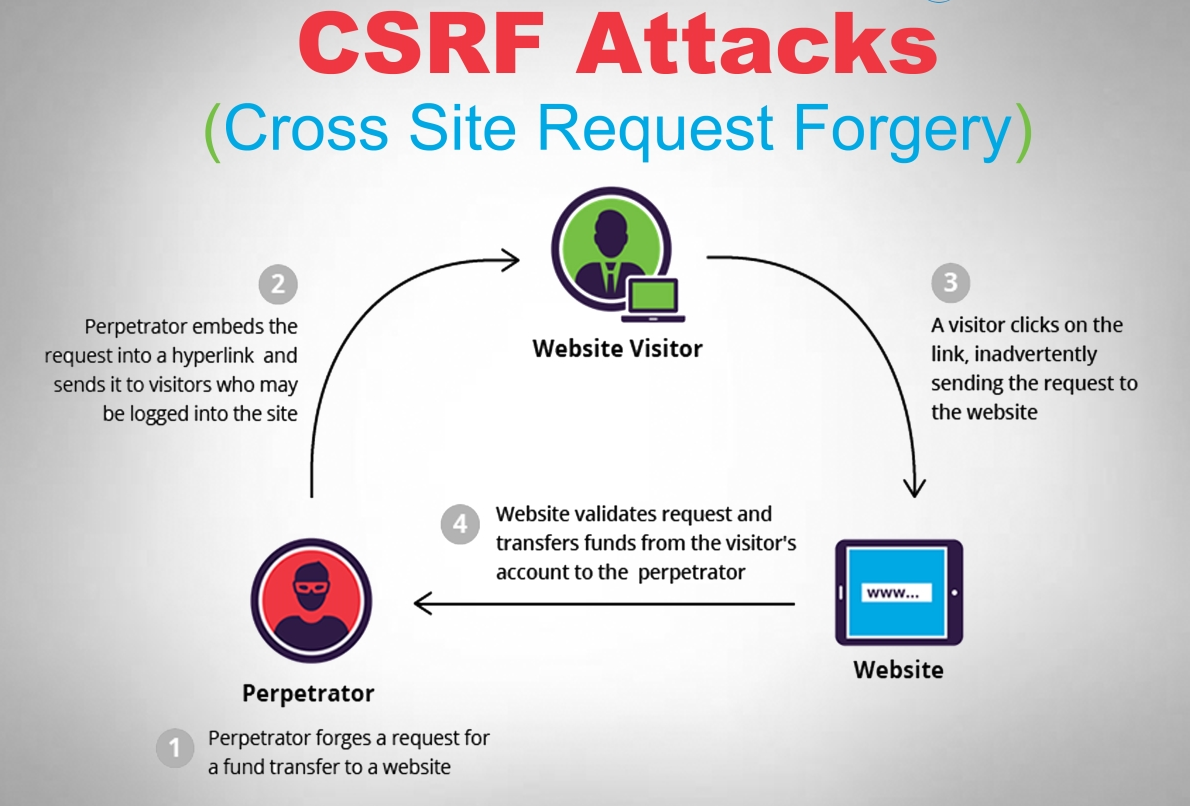
Understanding Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is a type of security vulnerability that occurs when an attacker tricks a user's browser into executing unwanted actions on a web application where the user is authenticated. This attack is often carried out by embedding malicious code in a trusted website or email, which then sends unauthorized requests to the target web application. In this article, we'll explore CSRF in more detail, understand how it works, and discuss methods for preventing it.
How CSRF Works
Authentication: The victim user logs into a trusted website and establishes a session with the web application.
Malicious Code Injection: The attacker embeds malicious code (e.g., in a phishing email or compromised website) that contains requests to the target web application.
Execution: The victim user unknowingly triggers the malicious code, causing their browser to send unauthorized requests to the target web application.
Attack Success: If the target web application does not have proper CSRF protections in place, it processes the unauthorized requests as if they were legitimate, leading to potential data modification or unauthorized actions.
Preventing CSRF Attacks
CSRF Tokens: Implement CSRF tokens as part of the web application's authentication mechanism. These tokens are unique per session and per request and are included in all forms and AJAX requests. The server verifies the token with each incoming request to ensure its authenticity.
SameSite Cookies: Set the SameSite attribute on cookies to prevent them from being sent in cross-origin requests. This helps mitigate the risk of CSRF attacks by limiting the scope of cookies to same-site requests only.
Origin Header Validation: Validate the Origin header or referer header on incoming requests to ensure they match the expected values. This helps detect and block requests coming from unauthorized origins.
Use of HTTP Methods: Ensure that sensitive actions in the web application require the use of specific HTTP methods (e.g., POST, PUT, DELETE) and do not allow these actions to be performed via GET requests. This prevents CSRF attacks from being carried out using simple GET requests.
Conclusion
Cross-Site Request Forgery (CSRF) is a serious security vulnerability that can lead to unauthorized actions and data breaches in web applications. By understanding how CSRF attacks work and implementing proper security measures, developers can protect their applications and users from this threat. Techniques such as CSRF tokens, SameSite cookies, and origin header validation can help mitigate the risk of CSRF attacks and ensure the integrity and security of web applications.
Are you interested in learning more about web application security, vulnerabilities, or best practices for secure development? Share your thoughts in the comments below and subscribe to our blog newsletter for updates on similar topics and more insightful content!
Subscribe to my newsletter
Read articles from Cloud Tuned directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
