Transparent Encryption
 Umair Khan
Umair Khan
- Cilium supports both IPsec and WireGuard to transparently encrypt traffic between nodes.
What is Transparent Encryption
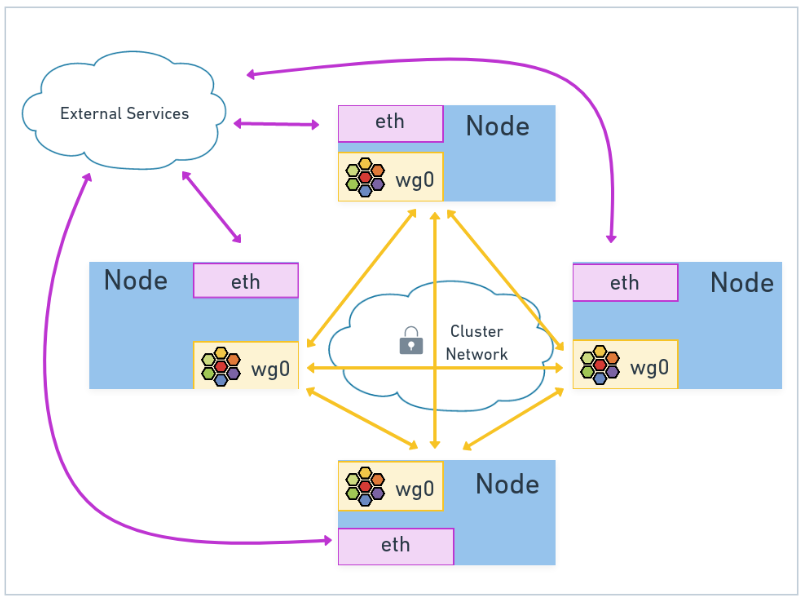
Microservices inside cluster typically communicate across Kubernetes nodes that may be physically separated over a network that we may not have full control over.
By encrypting the traffic between nodes in our cluster, we no longer have to implicitly trust the network itself, and we don’t have to worry about other systems sharing the network being able to read sensitive information passed between microservices in different nodes in your cluster.
Kubernetes doesnot have a native feature to encrypt data intransit inside cluster. For that Cilium offers an easy way to enable transparent node to node encryption using WireGuard or IPsec.
WireGuard
WireGuard and IPsec are both protocols to provide in-kernel transparent traffic encryption.
WireGuard is a simple to use, lightweight, virtual Private Network (VPN) solution that is built into the Linux kernel.
WireGuard is a peer-based VPN solution. A VPN connection is made between peers simply by exchanging public keys (like exchanging SSH keys).
When WireGuard or IPsec is enabled in Cilium, the Cilium agent running on each cluster node will establish a secure tunnel to other Cilium-managed nodes in the cluster.
Enabling Transparent Encryption
WireGuard must be installed and eabled on all nodes Kernal.
Enable WireGuard using Helm.
helm upgrade cilium cilium/cilium --namespace kube-system --reuse-values --set l7Proxy=false --set encryption.enabled=true --set encryption.type=wireguardRestart Cilium damonset.
kubectl rollout restart daemonset/cilium -n kube-systemAfter restart
CiliumNodeswill be annontated with WireGuard public key.
kubectl get -n kube-system CiliumNode kind-worker -o json | jq .metadata.annotationsVerify encryption.
kubectl exec -n kube-system -ti ds/cilium -- cilium status |grep EncryptionIf we check the IP devices available in the Cilium agent pods, we should see a new device named cilium_wg0.
kubectl exec -n kube-system -ti ds/cilium -- ip link | grep cilium
Subscribe to my newsletter
Read articles from Umair Khan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
