Managing State in Terraform: Best Practices for AWS Deployments
 Sanket Nimkar
Sanket Nimkar
Terraform is a powerful tool for defining and provisioning infrastructure as code (IaC). One of its core component is the state file, which is used track the state of your infrastructure. Managing this state is crucial for ensuring the reliability and consistency of your deployments. In this blog, we'll explore the concept of Terraform state, its importance, and best practices for managing it. We'll also highlight how to use remote state storage in AWS S3 with state locking using DynamoDB.
Understanding Terraform State
Terraform state is a highly critical aspect of how Terraform operates. It keeps track of the resources it manages, mapping your configuration to the actual resources in your infrastructure. The state file (usually terraform.tfstate) contains information such as resource IDs, attributes, and dependencies, allowing Terraform to determine what needs to be created, updated, or destroyed.
Why is Terraform State Important?
Resource Tracking: Terraform uses the state file to map real-world resources to your configuration. Without this mapping, Terraform don't know how to update or destroy resources.
Plan Generation: The state file allows Terraform to generate an accurate execution plans. By comparing the state with the desired configuration, Terraform can determine the necessary changes.
Concurrency Control: The state file helps manage concurrent operations, ensuring that multiple users or processes do not change the configured resources at the same time.
Best Practices for Managing Terraform State
Use Remote State Storage: Storing the state file locally is convenient for small projects but can lead to issues in collaborative environments. Remote state storage enables multiple team members to access and update the state file safely.
Enable State Locking: To prevent concurrent modifications, use state locking. This ensures that only one Terraform process can modify the state at a time, avoiding potential conflicts.
Version Control for State Files: Avoid storing state files in version control systems. Instead, use remote storage solutions that provide versioning and access controls.
Encrypt State Files: Since state files contain sensitive information, such as resource IDs and attributes, ensure they are encrypted both at rest and in transit.
Automate Backups: Regularly back up your state files to prevent data loss. Most remote storage solutions offer automated backup options.
Use Workspaces: For managing multiple environments (e.g., development, staging, production), use Terraform workspaces to keep state files isolated.
Using Remote State Storage in AWS S3 with State Locking Using DynamoDB
Storing your Terraform state remotely in AWS S3 with state locking using DynamoDB is a robust solution for managing state in a collaborative environment.
Setting Up S3 for Remote State Storage
Create an S3 Bucket: Create a new S3 bucket to store your Terraform state files. Ensure the bucket name is unique globally.
aws s3api create-bucket --bucket s3-terraform-state-2024 --region ap-south-1 --create-bucket-configuration LocationConstraint=ap-south-1You can specify different region.
Enable Versioning: Enable versioning on the S3 bucket to keep a history of state files.
aws s3api put-bucket-versioning --bucket s3-terraform-state-2024 --versioning-configuration Status=EnabledSet Bucket Policies: Apply appropriate bucket policies to control access and ensure that only authorized users can read/write the state files.
You can see your bucket on AWS console
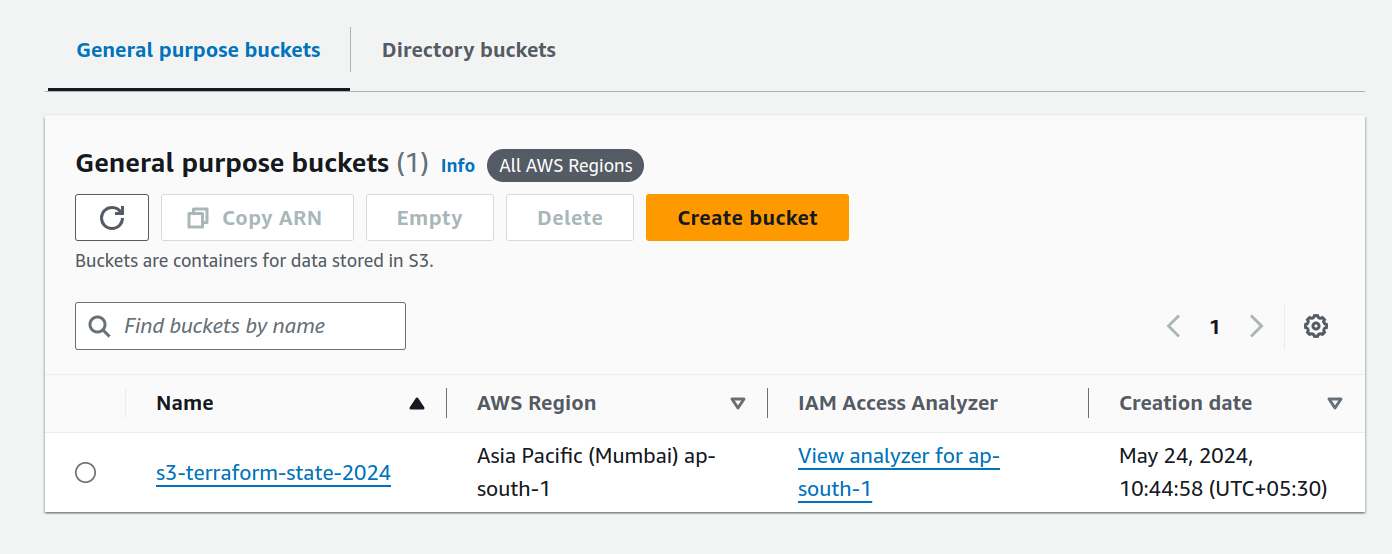
Setting Up DynamoDB for State Locking
Create a DynamoDB Table: Create a DynamoDB table to manage state locking. The table should have a primary key named
LockID.aws dynamodb create-table --table-name terraform-state-lock \ --attribute-definitions AttributeName=LockID,AttributeType=S \ --key-schema AttributeName=LockID,KeyType=HASH \ --provisioned-throughput ReadCapacityUnits=5,WriteCapacityUnits=5You can see created dynamoDB table on AWS console
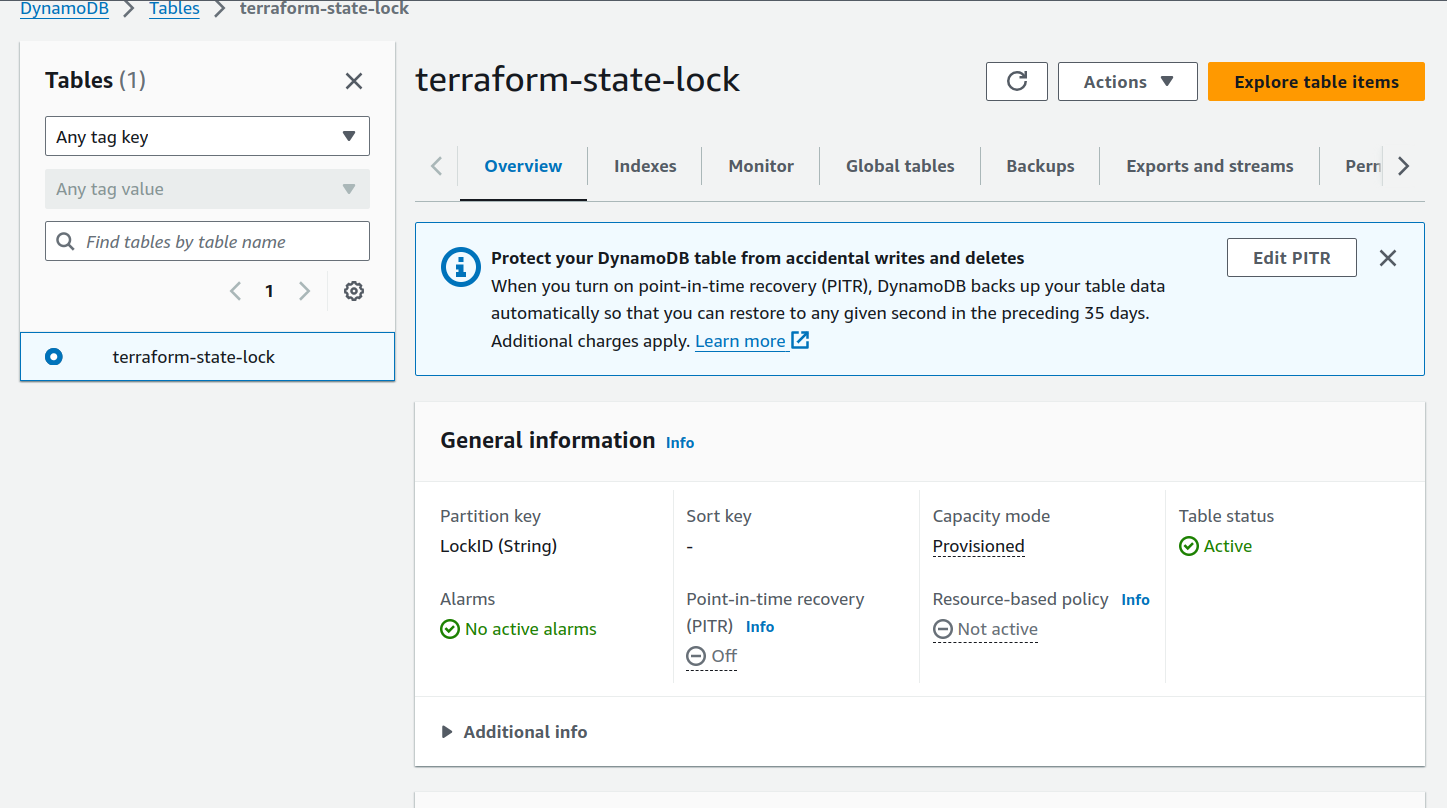
Configuring Terraform to Use S3 and DynamoDB
Backend Configuration: In your Terraform configuration file, specify the backend as S3 and enable DynamoDB for state locking.
terraform { backend "s3" { bucket = "s3-terraform-state-2024" key = "terraform.tfstate" region = "ap-south-1" dynamodb_table = "terraform-state-lock" encrypt = true } }Initialize the Backend: Initialize the backend configuration.
terraform init
Example Terraform Configuration
Create a Terraform Configuration File (main.tf)
resource "aws_iam_user" "example_user" { name = "example_user" path = "/" }Initialize the Terraform Configuration
terraform initApply the Terraform Configuration
Apply the Terraform configuration to create the IAM user
terraform applyTerraform will display a plan of the actions it will take. Review the plan and confirm by typing yes when prompted.
Review the Output
You can see example_user user should get created
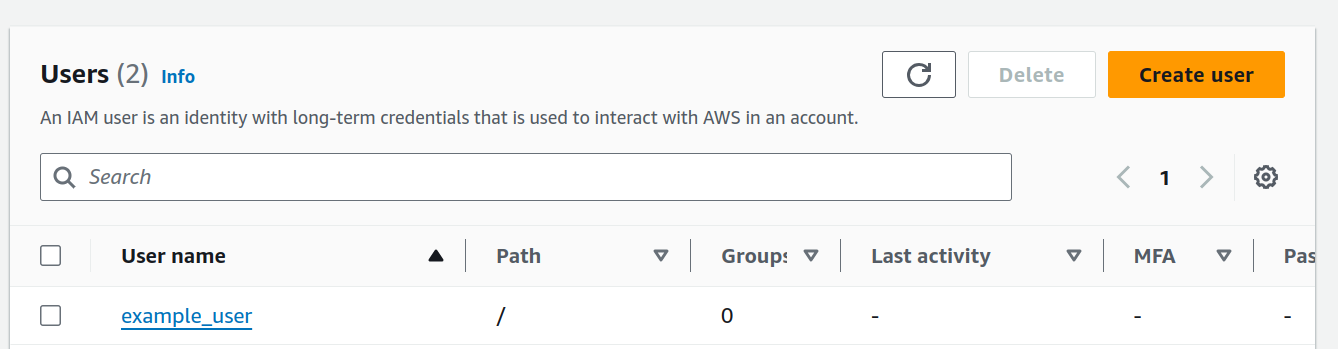
S3 Remote state file
Once you are done with above step, you can see state lock file must have been created under the bucket name s3-terraform-state-2024
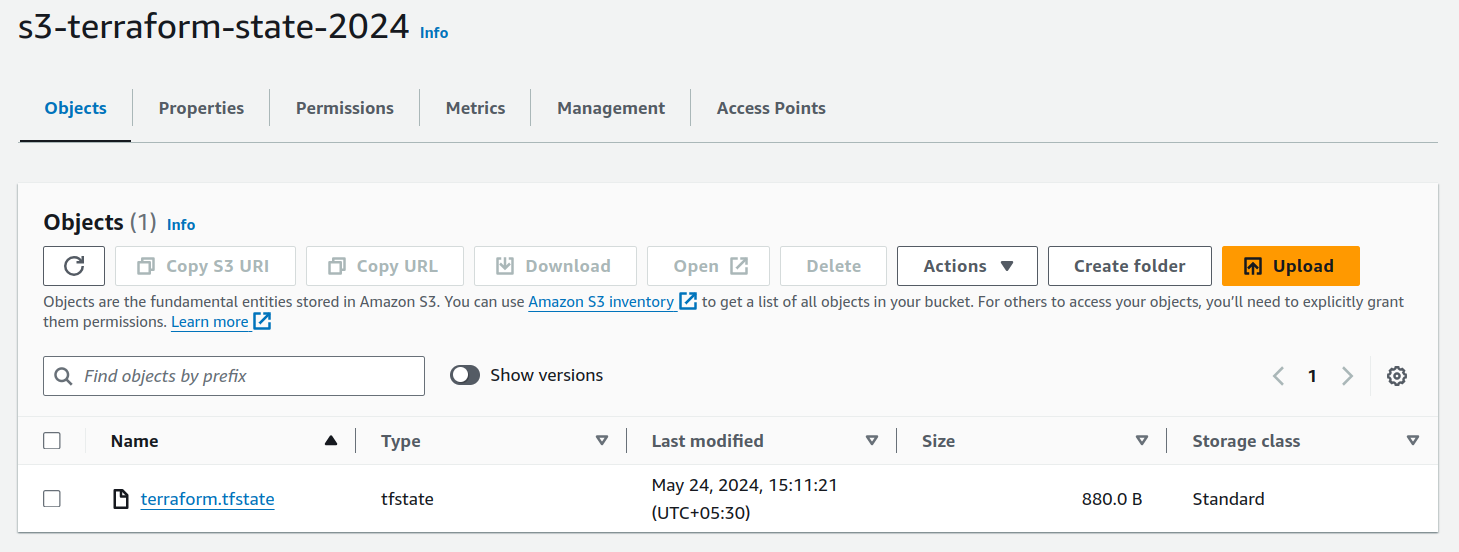
Please note that this terraform.tfstate file is encrypted and with version (even if you delete this file AWS will keep a version of deleted file)
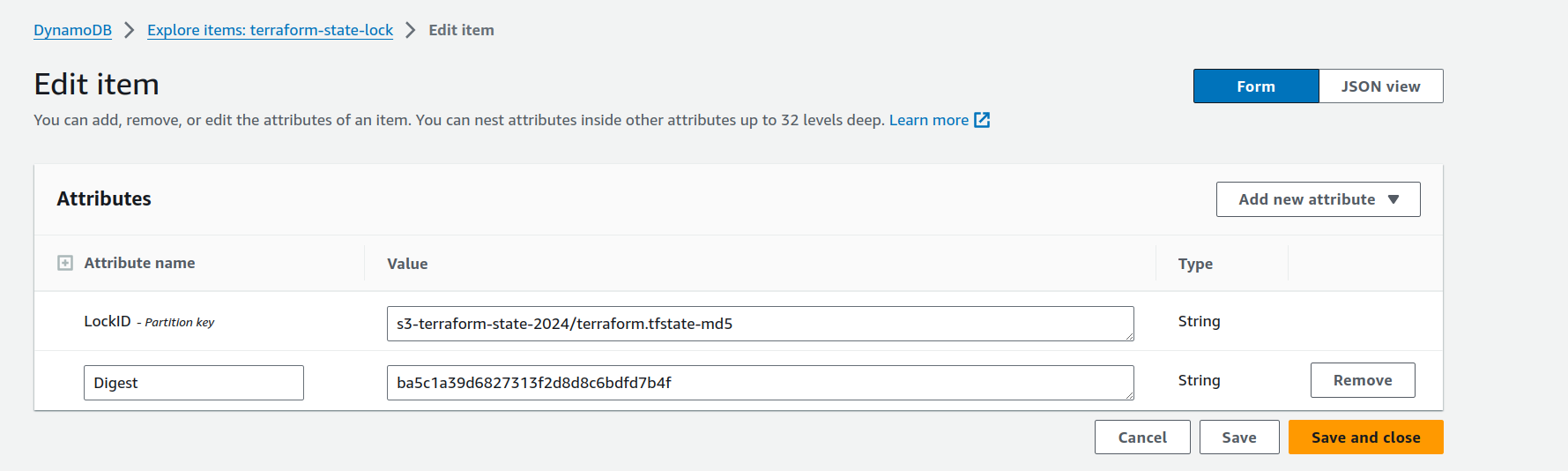
Also you can see the lock record inside dynamoDB Table
Conclusion
Managing Terraform state effectively is crucial for maintaining the integrity and reliability of your infrastructure deployments. By using remote state storage in AWS S3 and enabling state locking with DynamoDB, you can ensure that your state files are secure, consistent, and accessible to your team. Implementing these best practices will help you avoid common failure scenarios and enhance your Terraform workflow, making your infrastructure management more robust and scalable.
Subscribe to my newsletter
Read articles from Sanket Nimkar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
