Beginner's Guide to AWS Networking
 Vishnu Mohan
Vishnu Mohan
Introduction
In this series of articles we are going to take an overview of AWS Networking Services at high level. The goal is to get an understanding of all the core networking concepts within AWS which are key for implementing a good architecture for any AWS solutions at scale. This article is going to be a broken down into a series.
Overview
AWS networking revolves around creating a secure and scalable network environment for your resources in the AWS cloud. In this lecture we will be looking at all the key networking services you'll need to understand for your DevOps role
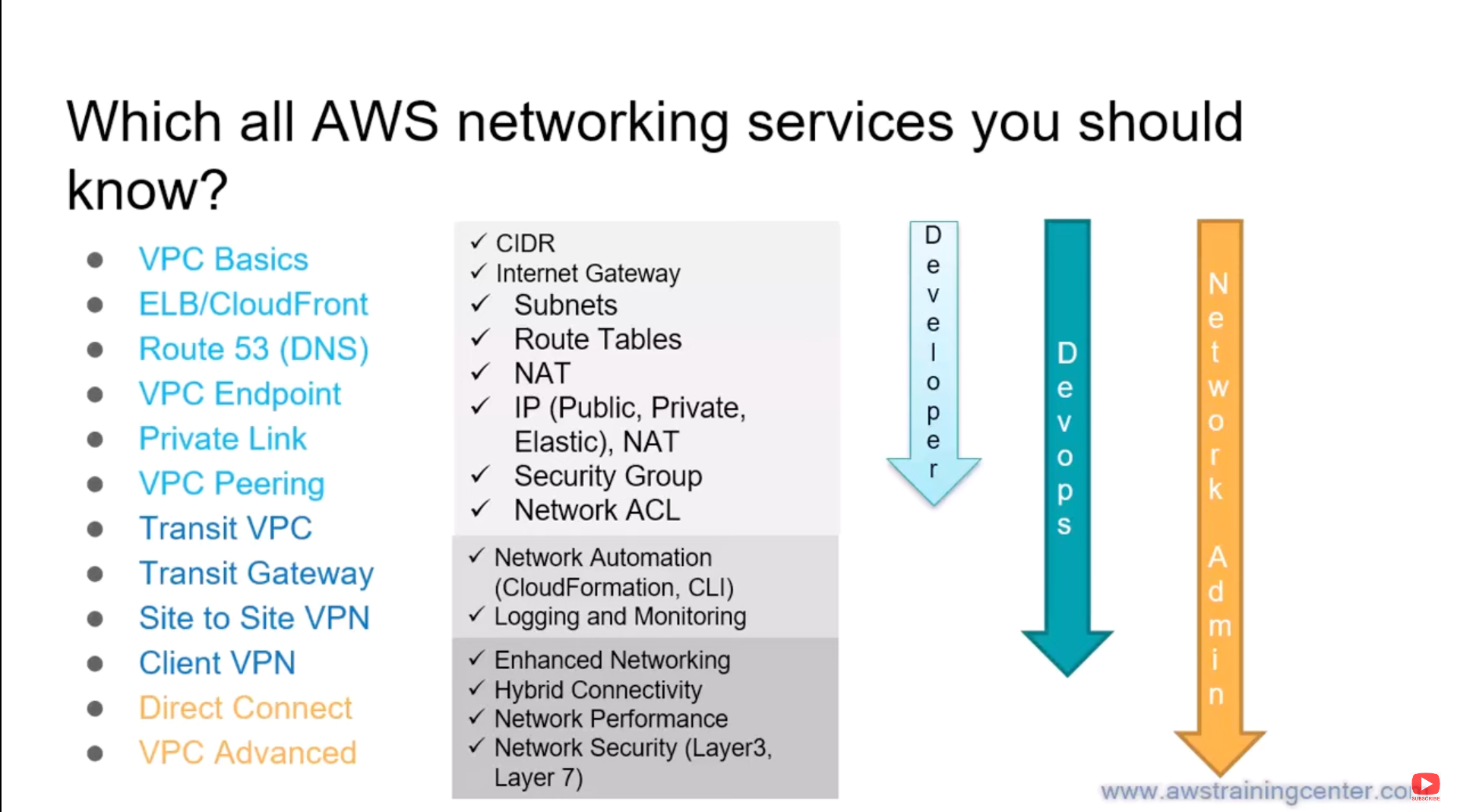
Virtual Private Cloud
VPC is a private network within your AWS, which provides a logically isolated section of the AWS cloud where you launch your resources like EC2, this means that AWS doesn’t provide you a separate hardware for your networking needs but VPC will create a virtual environment for your network within the AWS cloud that is distinct from the public internet or other VPCs. You can think of it as a dedicated network space handover to you by AWS as a service.
This Isolation the benefits of security by preventing access for public internet into your cloud and control over the network configurations which allows you to customise your network environment to meet your specific security and performance needs
When launching an EC2 instance, you have the option to choose either a default VPC or a VPC that you've already created. The default VPC has a limited functionality and might not be suitable for most production deployments.
Types of scopes in a VPC
There are two scopes for VPC, regional scope which means a VPC is confined to a single region and when you create a VPC, the resources launched within that VPC (EC2 instances, databases, etc.) can only communicate with other resources that resides in the same VPC (notice there can be multiple Availability Zones within a VPC).
A Subnet scoped VPC, which is enabled by a Subnet, a Subnet is a smaller segment within a VPC, which define the IP address range for resources within that subnet. This segmentation can be limited to a single availability zone within a region. We will talk more about subnets and availability zones in a later section of this article
IP addressing for VPC
The IP addresses for your VPC are represented using Classless Inter-Domain Routing (CIDR) notation. A VPC must have an associated IPv4 CIDR block. When creating a VPC, you define the CIDR block that specifies the overall IP address range for the entire VPC and by default VPCs use private IP ranges. Even though you can configure a VPC CIDR block with a public IP range, it won't automatically make resources within the VPC publicly accessible. You'll still need to set up additional mechanisms like internet gateways for internet access
Since subnets are further diving the VPC into smaller sections, each subnet also requires a CIDR block to define the IP address range for resources deployed within that subnet and this CIDR block must be a subset of the CIDR block of the entire VPC, in other words the range of IP addresses for a subnet cannot extend beyond the overall range available for the entire VPC.
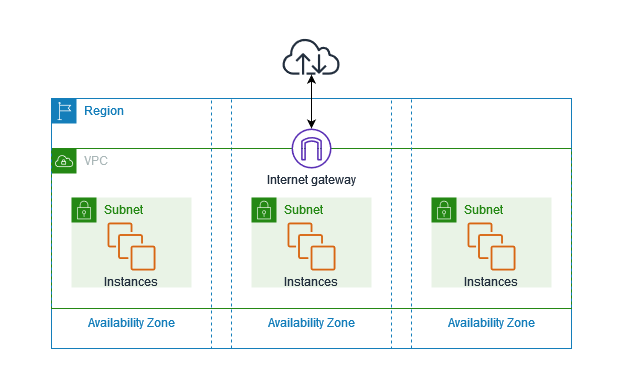
Route Table and Routing in VPC
Similar to a general computer network, when creating a VPC, it comes with a default traffic router for directing network traffic within that VPC. By default this router facilitates all the communication between the resources within a VPC and to destinations outside, such as the internet or other VPCs.
In a router the Route Table is one of the key components which is responsible for the routing decision, this route table acts as a routing map for VPC by setting up rules which determines how the traffic is directed to its specified destination.
There are two main types of route tables the main route table and the custom route table. The main route table are the default ones created by the VPC, they controlling traffic for any subnet that isn't explicitly linked to a different route table. The custom route table can be created by the user to manage a specific aspects such as to direct traffic to internet gateways, virtual private gateways, or other resources within your VPC.
Each route table(both custom and main) rule consist of a destination which defines the IP address range (CIDR) of the traffic which you want to route, and a target which specifies where the traffic should be directed. This target can be anything from, a resource within the same VPC (denoted by “Local”) or an Internet gateway etc.
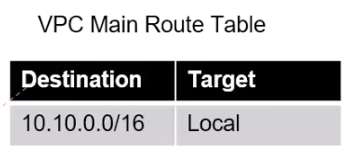
The route table based on the rules find a route that match the destination IP address of the traffic and the first matching route determines where the traffic is sent
A VPC can have multiple route tables, but each subnet can only be associated with one route table at a time.
A working scenario:
Initiation: When a resource within a subnet tries to communicate with another resource, it creates a network packet containing the destination IP address.
Matching Route: The subnet consults the route table associated with it and searches for an entry with a destination CIDR block that matches the destination IP address of the packet.
Target Identification: Once a matching route is found, the target specified in the route table entry is identified. This could be a subnet ID, internet gateway, NAT gateway, or VPC peering connection.
Packet Forwarding: The packet is forwarded to the target identified in the route table entry.
Subnets
In AWS each resource are hosted in separate geographical locations called regions, within a region we have multiple isolated locations called Availability Zones (AZ). When launching an EC2 instance in AWS, you can choose a subnet or use the default VPC subnet. A subnet reside entirely within an availability zone and it cannot span over zones. This separation between subnets in different AZs enhances fault tolerance. If an AZ experiences an outage, resources in other AZs remain operational. Overall subnets help to organise and logically isolate VPCs.
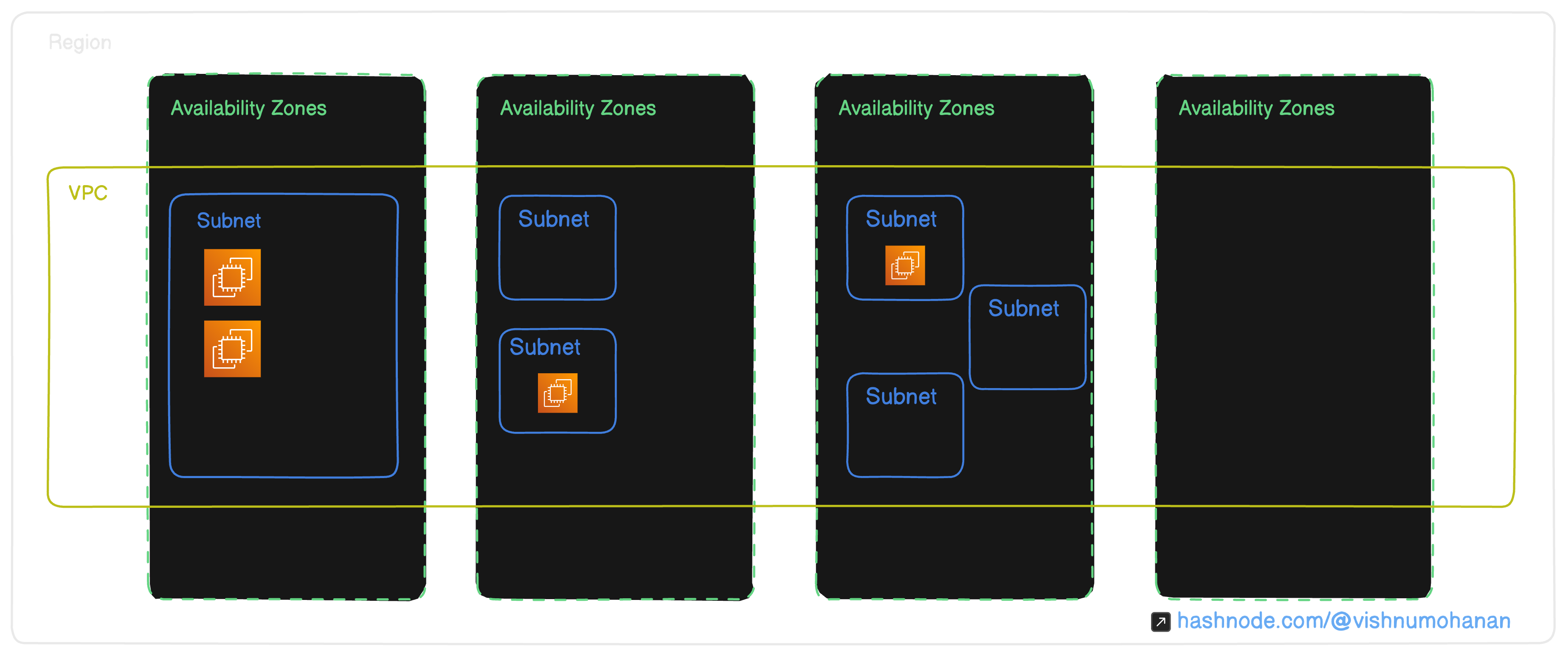
Another aspect of having subnets is the flexibility it provides in controlling the flow of traffic by defining security groups that applies to a specific subnet. This way we can have granular control over the traffic in and out of each subnets.
Summary
To summarise, VPCs are logically isolated cloud network dedicated for you from the rest of the cloud and the outside world and subnets provide logical isolation within VPC to help us better manage routing and security of our instances, whereas AZs provide physical isolation within a VPC to help improve fault tolerance by creating multiple subnets, each in a separate AZ, and launch your instances across these subnets. It is important to configure your route tables appropriately, to ensure resources in different subnets (and potentially different AZs) can communicate seamlessly.
So far we’ve covered the major components of networking in AWS including VPC, subnets, availability zones and route tables, in the coming section we will look in detail how routing is done within and outside of VPCs and components like Internet Gateway, Network address translation Gateway and more.
Subscribe to my newsletter
Read articles from Vishnu Mohan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vishnu Mohan
Vishnu Mohan
Software Engineer | Cloud Security