Deploying a Highly Available E-commerce Application on AWS
 Siddhant Bhattarai
Siddhant Bhattarai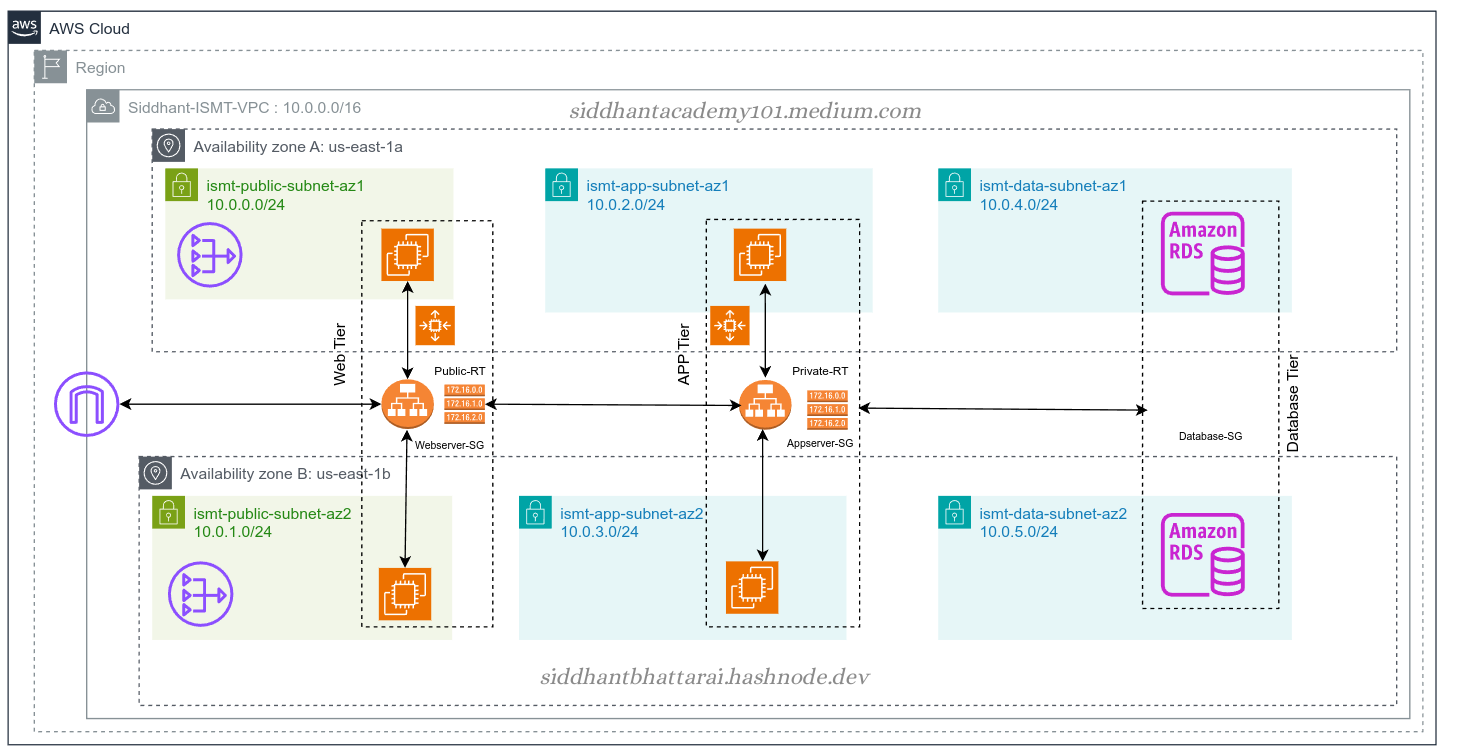
In this blog, we will guide you through deploying a highly available and secure e-commerce application on AWS. We'll use various AWS services and best practices to ensure scalability, fault tolerance, and security.
Scenario:
You have been hired by a rapidly growing e-commerce company, ShopEase, to prepare their infrastructure for a major marketing campaign. The campaign is expected to draw a significant amount of traffic to their online store, and the company needs to ensure that its systems are robust, scalable, and secure to handle this influx. As the lead cloud architect, your task is to design and implement a cloud infrastructure solution that meets the following requirements:
Scalability: The infrastructure must handle sudden spikes in traffic efficiently.
High Availability: Ensure the application is highly available with minimal downtime.
Security: Protect sensitive customer data and internal application data.
Separation of Concerns: Separate different tiers of the application for better security and manageability.
Fault Tolerance: Ensure the system can tolerate failures and continue operating without significant disruption.
Step 1: Setting Up the VPC and Subnets
Create a VPC:
Open the Amazon VPC console.
Click on Create VPC.
Name your VPC (e.g.,
Ecommerce-VPC), and set the CIDR block to10.0.0.0/16.Click Create VPC.
Create Subnets:
Create public subnets in two availability zones (e.g.,
us-east-1aandus-east-1b).Subnet 1 (us-east-1a):
10.0.0.0/24(Name:Public-Subnet-A)Subnet 2 (us-east-1b):
10.0.1.0/24(Name:Public-Subnet-B)
Create private subnets in the same availability zones.
Subnet 3 (us-east-1a):
10.0.2.0/24(Name:Private-Subnet-A)Subnet 4 (us-east-1b):
10.0.3.0/24(Name:Private-Subnet-B)
Create database subnets in the same availability zones.
Subnet 5 (us-east-1a):
10.0.4.0/24(Name:Database-Subnet-A)Subnet 6 (us-east-1b):
10.0.5.0/24(Name:Database-Subnet-B)
Important: Associate the database subnets with the private route table to ensure instances do not have direct internet access. Instead, outgoing traffic should be routed through the NAT Gateway.
Step 2: Configuring the Internet Gateway and NAT Gateway
Create an Internet Gateway:
Go to the VPC dashboard.
Click Internet Gateways and then Create Internet Gateway.
Name it (e.g.,
Ecommerce-IGW).Attach the Internet Gateway to your VPC.
Create a NAT Gateway:
Allocate an Elastic IP address for the NAT Gateway.
Go to NAT Gateways and click Create NAT Gateway.
Select one of your public subnets and assign the Elastic IP.
Click Create NAT Gateway.
Step 3: Configuring Route Tables
Public Route Table:
Create Route Table:
Go to Route Tables in the VPC dashboard and click Create route table.
Name it (e.g.,
Public-RT) and select your VPC.Click Create.
Associate Subnets:
Select the newly created route table and go to the Subnet Associations tab.
Click Edit subnet associations.
Select your public subnets (
Public-Subnet-AandPublic-Subnet-B) and click Save associations.
Add Route:
Go to the Routes tab and click Edit routes.
Click Add route.
Destination:
0.0.0.0/0Target: Select the Internet Gateway (
Ecommerce-IGW) from the dropdown.Click Save routes.
Private Route Table:
Create Route Table:
Go to Route Tables in the VPC dashboard and click Create route table.
Name it (e.g.,
Private-RT) and select your VPC.Click Create.
Associate Subnets:
Select the newly created route table and go to the Subnet Associations tab.
Click Edit subnet associations.
Select your private subnets (
Private-Subnet-AandPrivate-Subnet-B) and your database subnets (Database-Subnet-AandDatabase-Subnet-B), then click Save associations.
Add Route:
Go to the Routes tab and click Edit routes.
Click Add route.
Destination:
0.0.0.0/0Target: Select the NAT Gateway from the dropdown.
Click Save routes.
Step 4: Security Groups Configuration
Webserver Security Group:
Go to the EC2 dashboard and click Security Groups.
Create a new security group (e.g.,
Webserver-SG).Allow inbound traffic on port 80 (HTTP) and 443 (HTTPS) from anywhere (
0.0.0.0/0).
Appserver Security Group:
Create another security group (e.g.,
Appserver-SG).Allow inbound traffic on the application port (e.g., 8080) from the webserver security group.
Database Security Group:
Create a security group for the database servers (e.g.,
Database-SG).Allow inbound traffic on the database port (e.g., 3306 for MySQL) from the application server security group.
Step 5: Launching Instances
Launch Web Servers:
Go to the EC2 dashboard and click Launch Instance.
Select an appropriate AMI and instance type.
Place instances in the public subnets and associate them with the
Webserver-SG.
Launch Application Servers:
- Repeat the process for the application servers, but place them in the private subnets and associate them with the
Appserver-SG.
- Repeat the process for the application servers, but place them in the private subnets and associate them with the
Step 6: Setting Up Amazon RDS
Create an RDS Instance:
Go to the RDS dashboard and click Create database.
Choose the database engine (e.g., MySQL).
Select Multi-AZ deployment for high availability.
Place the database instances in the database subnets.
Assign the
Database-SGsecurity group to the RDS instances.
Step 7: Configuring Load Balancers (Optional)
Create an Application Load Balancer:
Go to the EC2 dashboard and click Load Balancers.
Create an Application Load Balancer and configure it to distribute traffic across the web servers in the public subnets.
Set up appropriate listeners and target groups.
Step 8: DNS Configuration (Optional)
Set Up Route 53:
Go to the Route 53 dashboard and create a hosted zone for your domain.
Create DNS records to point to your load balancer or directly to the web server instances if not using a load balancer.
Conclusion
By following these steps, you will have successfully deployed a highly available, scalable, and secure e-commerce application on AWS. This architecture ensures fault tolerance and high availability by distributing resources across multiple availability zones and using managed services like Amazon RDS. Additionally, using security groups and NAT gateways ensures that your application and data remain secure.
Happy deploying!
Subscribe to my newsletter
Read articles from Siddhant Bhattarai directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Siddhant Bhattarai
Siddhant Bhattarai
I am a versatile professional with expertise in multiple domains, including DevSecOps, AWS Cloud Solutions, AI/ML, and Cyber Security. With over 5 years of experience in the field, I have honed my skills and dedicated myself to various roles and responsibilities. If you're looking for opportunities for collaboration, insights, or exciting ventures in these domains, I'm open to connecting. Please don't hesitate to reach out – I'm excited to engage with professionals, learners, and enthusiasts who share my passion for these fields!