OSCP Journey: Introduction to Domain Enumeration with PowerView
 Ghassan Amaimia
Ghassan AmaimiaTable of contents

I - Introduction :
Once we have successfully compromised our target, the next critical phase involves conducting comprehensive domain enumeration to gather detailed information about the Active Directory environment. To facilitate this process, we will leverage a powerful post-exploitation tool known as PowerView. This robust utility is essential for identifying key assets, uncovering domain trusts, and enumerating critical AD objects, providing us with the necessary insights to advance our attack strategy.
II - PowerView Introduction :
PowerView is an exceptionally powerful and versatile PowerShell-based enumeration tool designed to gather detailed information about an organization's Active Directory domain and forest. It is invaluable for security professionals seeking to map out domain structures, identify key assets, and understand the intricacies of the AD environment.
Installing PowerView :
Installing PowerView is straightforward. Begin by visiting the official repository through this link. Once there , download the
PowerView.ps1file.
Now we need to open our cmd and navigate to Downloads folder :
cd C://users/user/Downloadsthen our first step is to bypass execution policy using the command and run PowerView :
powershell -ep bypass . .\PowerView.ps1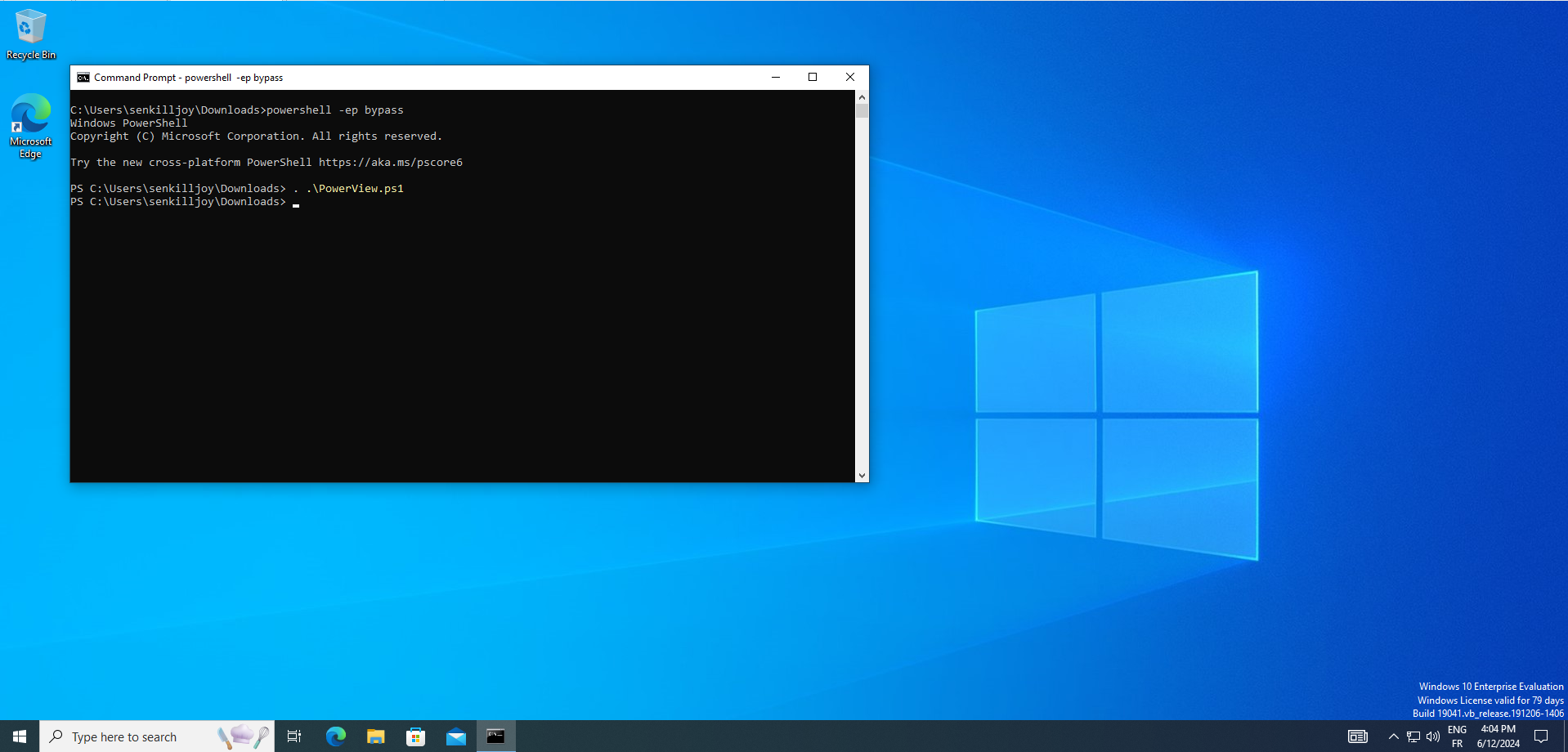
Executing Commands :
As we delve into PowerView, we'll introduce a few essential commands to provide insight into its capabilities. These commands serve as a starting point for understanding PowerView's functionality and its utility in Active Directory enumeration. For a comprehensive list of commands and their usage, I've provided a cheat sheet link below, allowing you to further explore PowerView's extensive toolkit.
Get-NetDomain :retrieves information about the current Active Directory domain. This includes details such as the domain name, domain controllers, domain SID, and other domain-related properties. It is a fundamental command for understanding the basic structure and attributes of the domain you are enumerating.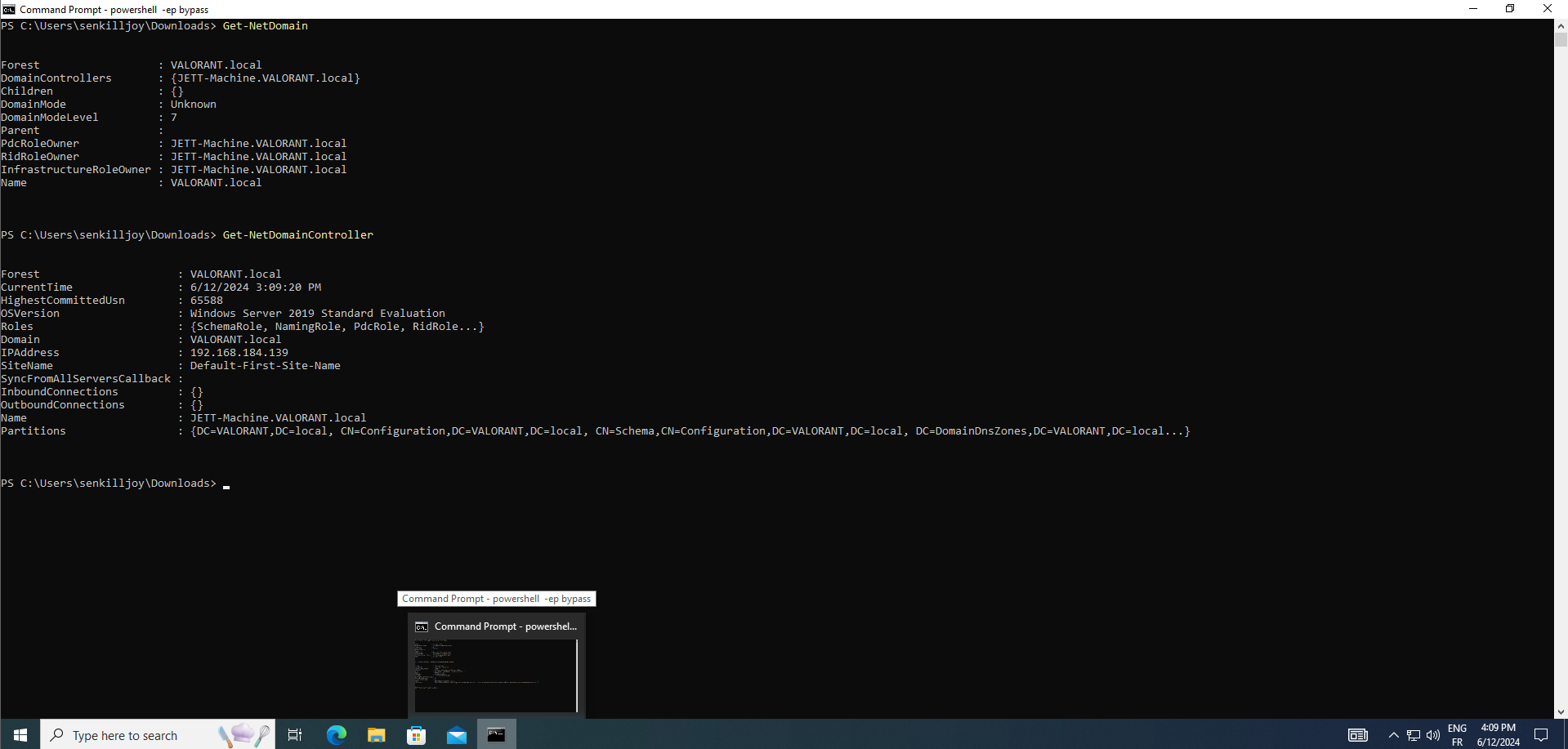
Get-NetGPO :enumerate Group Policy Objects (GPOs) within the Active Directory environment. It provides valuable insights into the GPOs applied across the domain, including their names, unique identifiers (GUIDs), permissions, and other associated attributes. This information is crucial for understanding the configuration and security policies enforced within the domain, aiding in reconnaissance and potential exploitation strategies.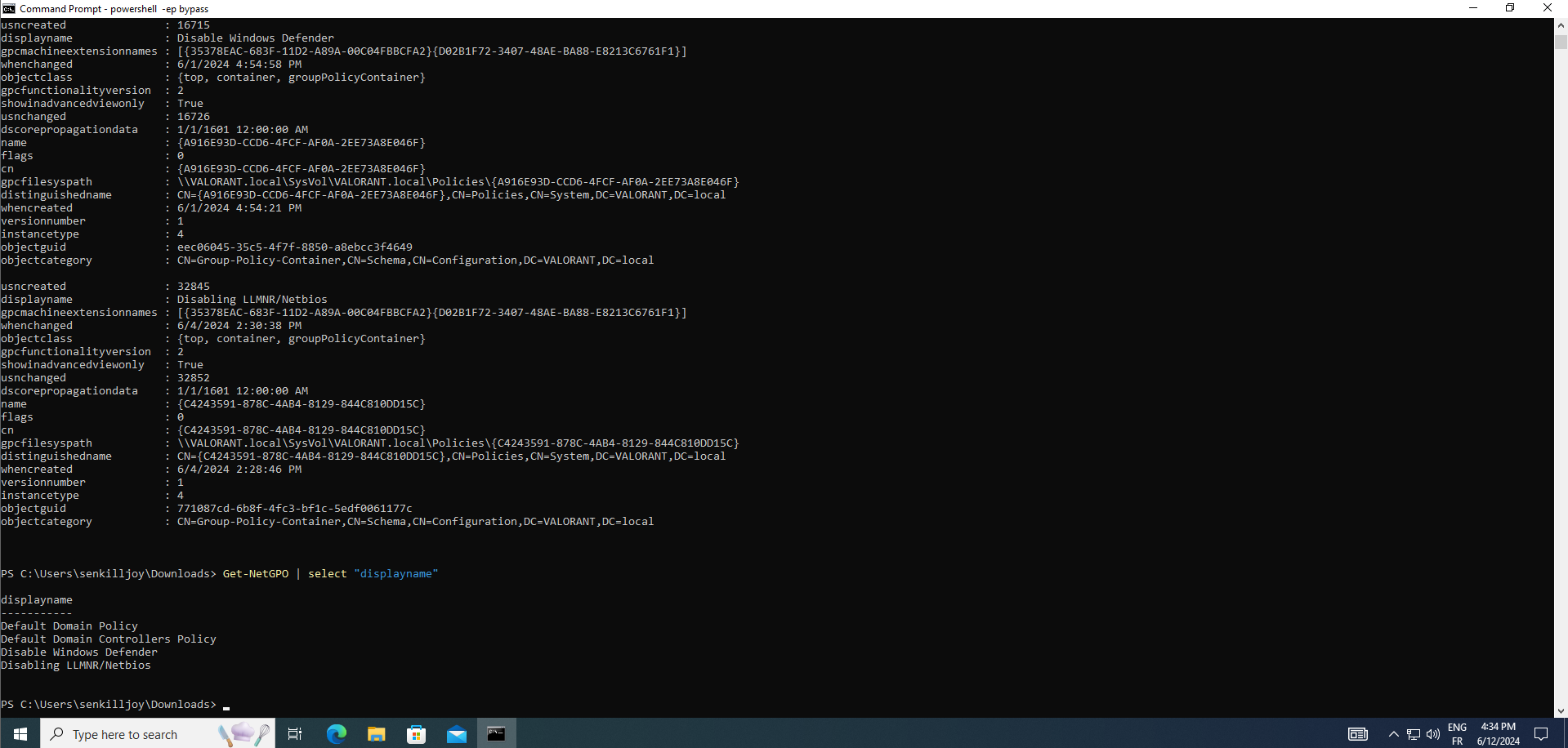
Get-DomainPolicy :retrieve information about domain-wide policies within the Active Directory environment. This command provides insight into various domain policies, including password, account lockout, Kerberos, and other security settings enforced across the domain. Understanding these policies is crucial for assessing the security posture of the domain and identifying potential vulnerabilities or misconfigurations that could be exploited by adversaries.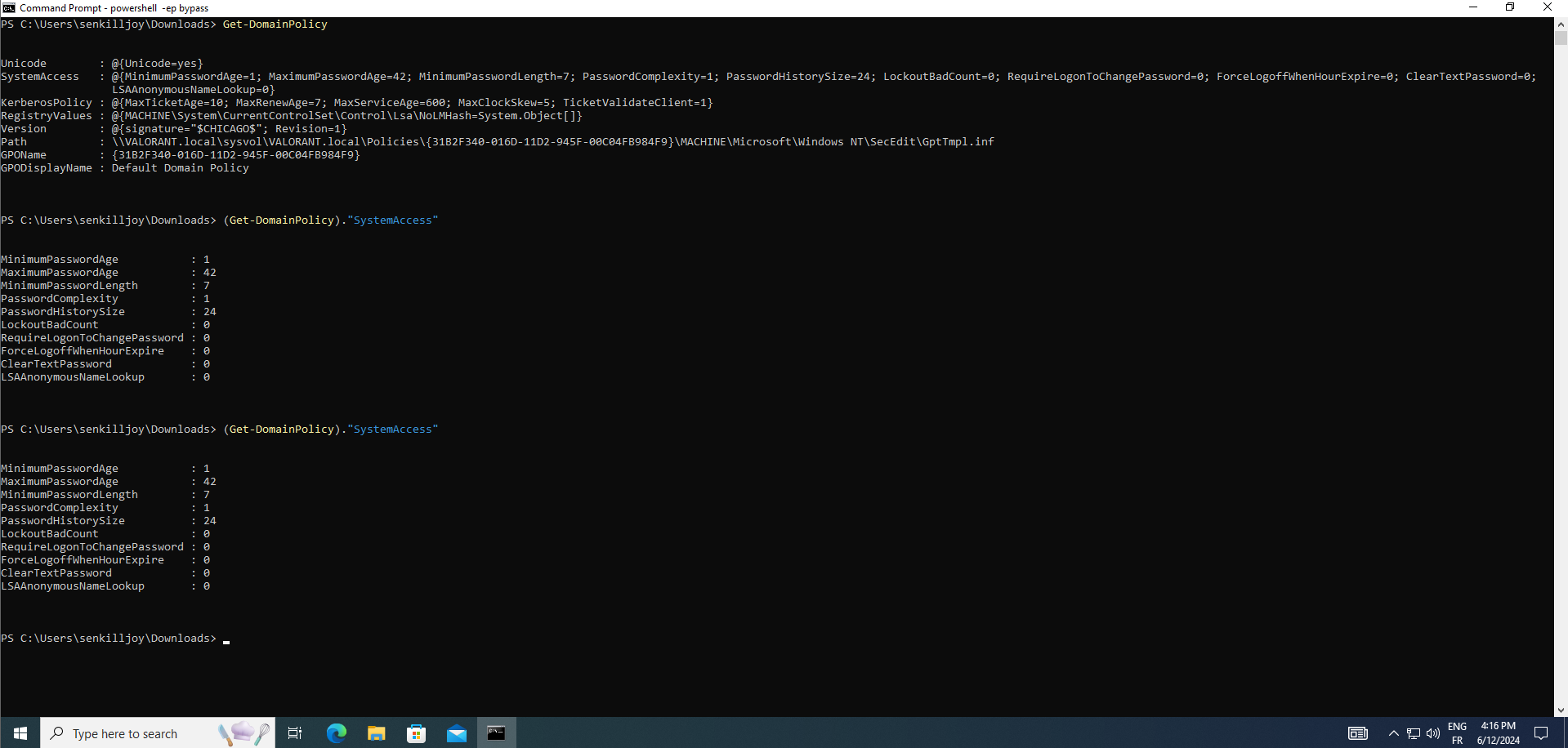
Get-NetUser :enumerate user accounts within the Active Directory domain. It retrieves comprehensive details about domain users, including their usernames, security identifiers (SIDs), group memberships, last login times, and other relevant attributes. This command is instrumental for reconnaissance purposes, allowing security professionals to gather intelligence on user accounts present within the domain, aiding in the identification of potential security risks or privileged accounts that may require further scrutiny.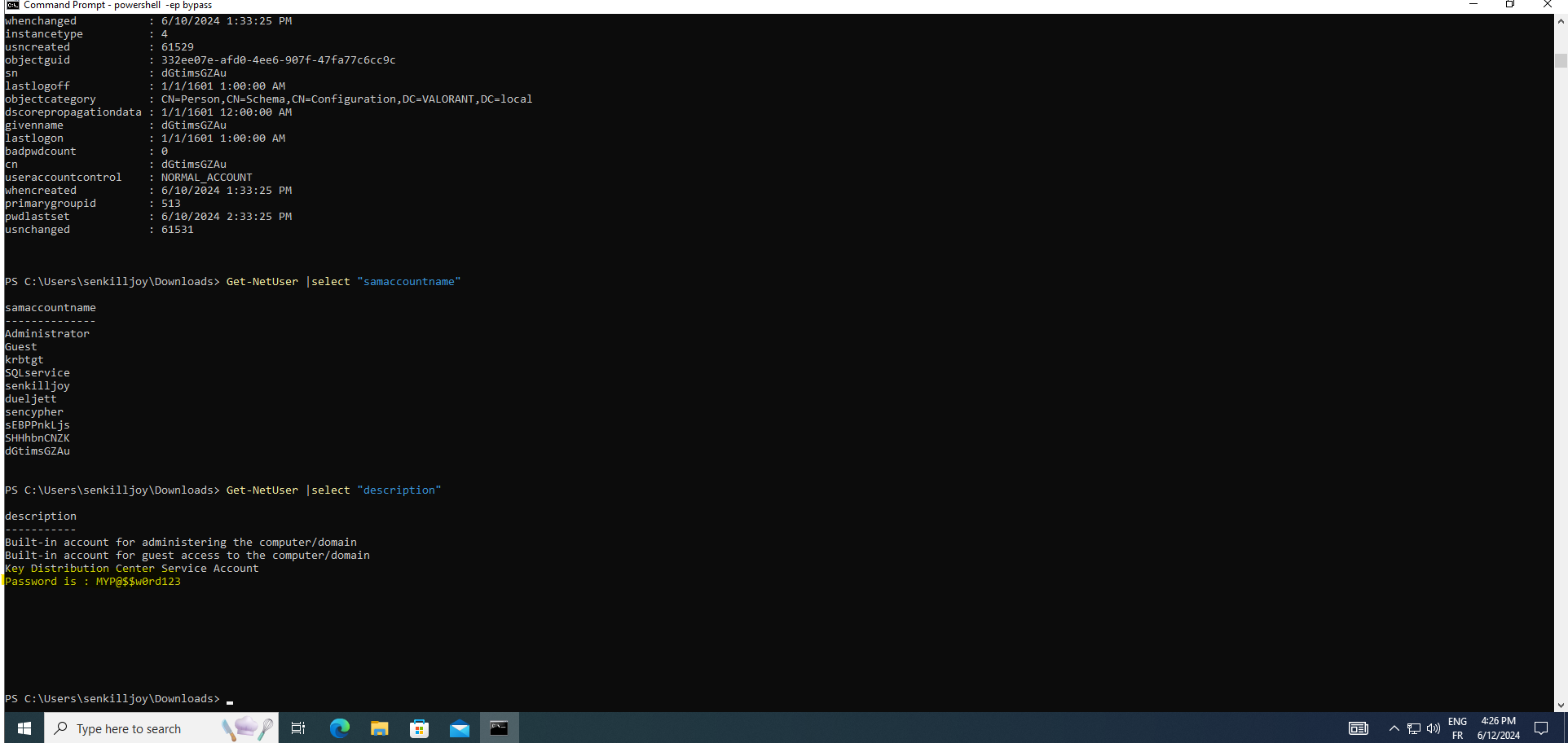
III - Conclusion :
In the realm of cybersecurity, domain enumeration stands as a critical phase in the post-exploitation process, offering a wealth of insights into an organization's Active Directory infrastructure. Through our exploration of PowerView, we've unveiled a potent arsenal for navigating the complexities of domain enumeration with precision and efficiency.
With PowerView as our ally, we've gained the ability to uncover vital domain attributes, such as user accounts, group memberships, GPO configurations, and more, empowering us to bolster our understanding of the target environment and refine our attack strategies accordingly.
As we conclude our journey through PowerView, it becomes evident that mastering this tool is not merely about acquiring technical prowess, but also about adopting a strategic mindset to leverage its capabilities effectively. By harnessing the power of PowerView, cybersecurity professionals can elevate their reconnaissance efforts, fortify their defenses, and stay one step ahead of potential adversaries in the ever-evolving landscape of digital security.
Cheat Sheet link : https://zflemingg1.gitbook.io/undergrad-tutorials/powerview/powerview-cheatsheet
Subscribe to my newsletter
Read articles from Ghassan Amaimia directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ghassan Amaimia
Ghassan Amaimia
I am a dedicated cybersecurity student with a passion for protecting digital landscapes and a keen interest in ethical hacking. Currently, I am preparing for the prestigious Offensive Security Certified Professional (OSCP) certification. This certification will enhance my skills and knowledge in penetration testing and network security. With a strong commitment to continuous learning and professional growth, I aim to contribute to the ever-evolving field of cybersecurity.