Docker Networking
 Haaris Sayyed
Haaris Sayyed
Docker is a containerization platform that uses OS-level virtualization to package software applications and their dependencies into reusable units called containers. Docker containers can be run on any host with Docker or an equivalent container runtime installed, whether locally on your laptop or in a remote cloud.
Docker includes a networking system for managing communications between containers, your Docker host, and the outside world. Several different network types are supported, facilitating a variety of common use cases.
This blog post delves into Docker networking, explaining its importance, types, and how to use it effectively.
What is Docker Networking?
Docker networking is the system that allows Docker containers to communicate with each other and with the outside world. It is essential for running multi-container applications where different services need to interact, such as a web server connecting to a database.
How Docker Networking Works
Docker uses your host’s network stack to implement its networking system. It works by manipulating iptables rules to route traffic to your containers. This also provides isolation between Docker networks and your host.
iptables is the standard Linux packet filtering tool. Rules added to iptables define how traffic is routed as it passes through your host’s network stack. Docker networks add filtering rules which direct matching traffic to your container’s application. The rules are automatically configured, so you don’t need to manually interact with iptables.
Docker containers are assigned their own network namespace, a Linux kernel feature that provides isolated virtual network environments. Containers also create virtual network interfaces on your host that allow them to communicate outside their namespace using your host’s network.
Types of Docker Networks
Docker provides several network drivers, each serving different use cases. The main types are:
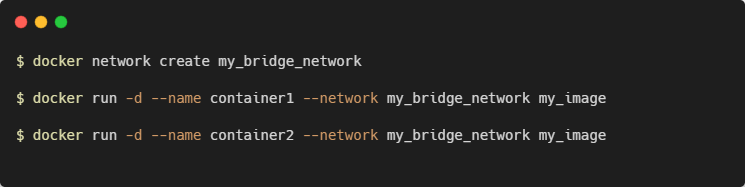
1. Bridge Network
The bridge network is the default network driver used when a container is started without specifying a network. It creates a private internal network on the host, allowing containers to communicate with each other and the host.
Each container in the network is assigned its own IP address. Because the network’s bridged to your host, containers are also able to communicate on your LAN and the internet. They will not appear as physical devices on your LAN, however.
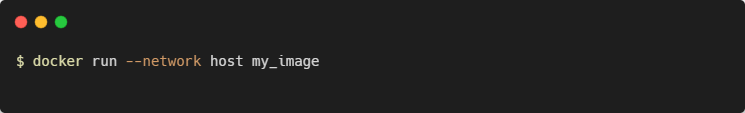
2. Host Network
The host network driver removes network isolation between the container and the Docker host. The container uses the host's networking directly. This means a container process that listens on port 80 will bind to <your_host_ip>:80
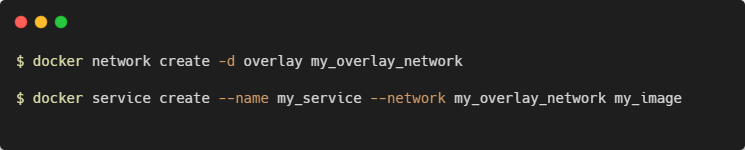
3. Overlay Network
The overlay network enables containers running on different Docker hosts to communicate with each other securely. This network driver is essential for Docker Swarm and Kubernetes.
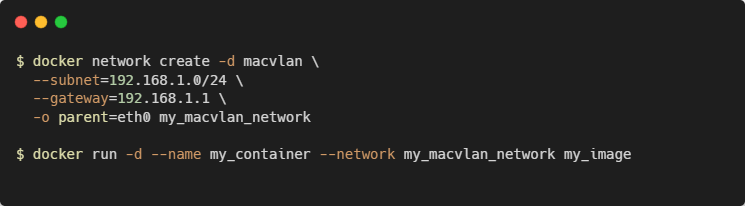
4. Macvlan Network
The Macvlan network driver assigns a MAC address to each container, making it appear as a physical device on the network. This allows containers to communicate with external networks directly.
5. None Network
The none network driver disables all networking for a container. It is useful for containers that do not need network connectivity.

Which Network Type Should I Use?
Bridge networks are the most suitable option for the majority of scenarios you’ll encounter. Containers in the network can communicate with each other using their own IP addresses and DNS names. They also have access to your host’s network, so they can reach the internet and your LAN.
Host networks are best when you want to bind ports directly to your host’s interfaces and aren’t concerned about network isolation. They allow containerized apps to function similarly to network services running directly on your host.
Overlay networks are required when containers on different Docker hosts need to communicate directly with each other. These networks let you set up your own distributed environments for high availability.
Macvlan networks are useful in situations where containers must appear as a physical device on your host’s network, such as when they run an application that monitors network traffic. IPvLAN networks are an advanced option for when you have specific requirements around container IP addresses, tags, and routing.
None networks are useful for isolated tasks that do not require network access.
Docker Networking Commands
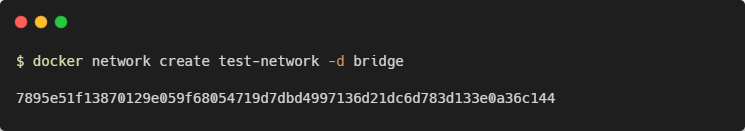
Creating Networks
You can specify the driver to use, such as bridge or host, by setting the -d flag. A bridge network will be created if you omit the flag.
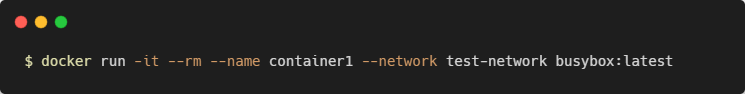
Connecting Containers to Networks
You can attach new containers to a network by setting the --network flag with your docker run command. Run this command in your terminal window:
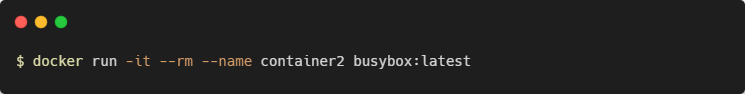
Next, open new terminal window and start another Ubuntu container, this time without the --network flag:
Now try communicating between the two containers, using their names:

The containers aren’t in the same network yet, so they can’t directly communicate with each other.
Use your first terminal window to join container2 to the network:
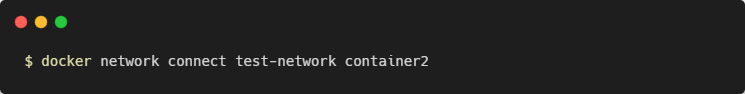
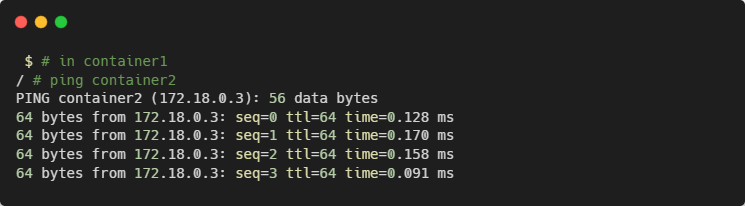
The containers now share a network, which allows them to discover each other:
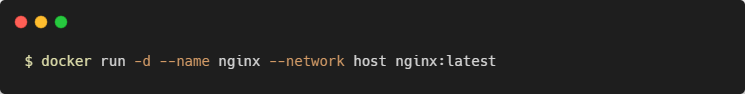
Using Host Networking
You can enable host networking for a container by connecting it to the built-in host network:
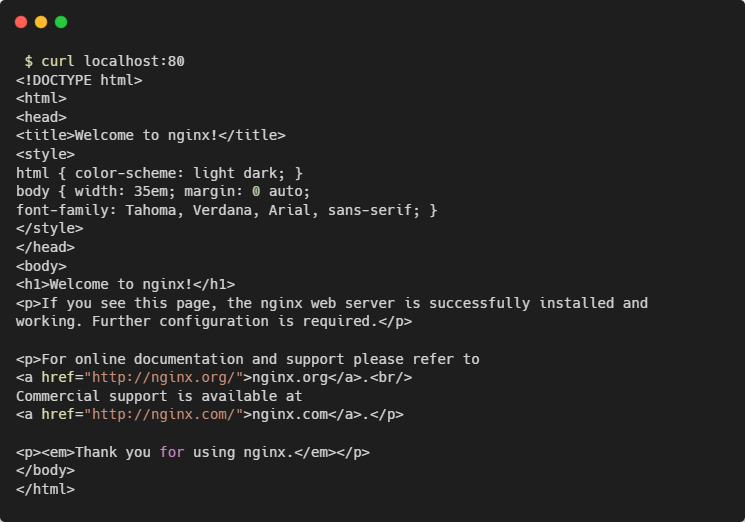
NGINX listens on port 80 by default. Because the container’s using a host network, you can access your NGINX server on your host’s localhost:80 outside the container, even though no ports have been explicitly bound:
Disabling Networking
When a container’s networking is disabled, it will have no connectivity available – either to other containers, or your wider network. Disable networking by attaching your container to the none network:
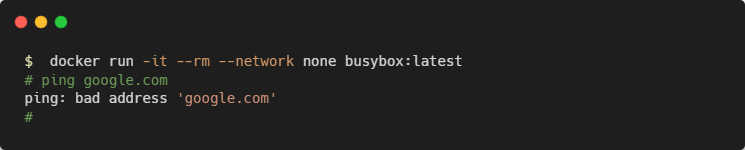
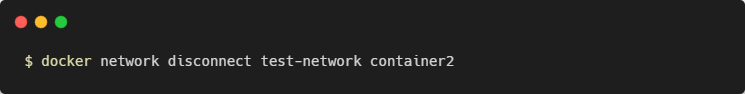
Removing Containers from Networks
Docker lets you freely manage network connections without restarting your containers.
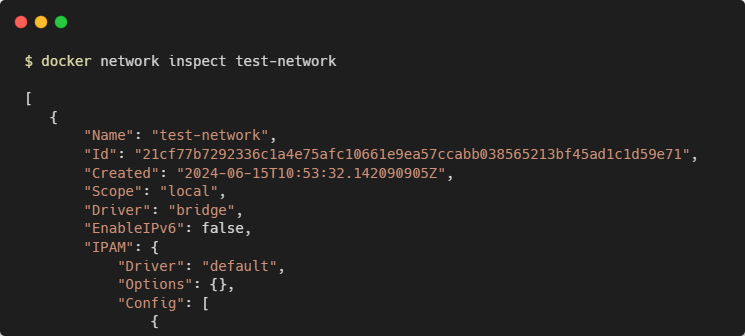
Inspect a Network
List Docker Networks

Delete Network

Automatically Delete All Unused Networks

Best Practices for Docker Networking
Use Appropriate Network Drivers: Choose the right network driver based on your application's needs. For instance, use the overlay network for distributed systems and the bridge network for standalone applications.
Isolate Networks: Use separate networks for different components of your application to enhance security and manageability.
Monitor Network Traffic: Regularly monitor network traffic to ensure there are no bottlenecks or security issues.
Keep Network Configurations Simple: Avoid overly complex network configurations that can become difficult to manage and troubleshoot.
Leverage Docker Compose: Use Docker Compose to define and manage multi-container applications with ease. It simplifies the network configuration process.
Conclusion
Docker networking is a powerful feature that enables seamless communication between containers and external systems. Understanding the different network drivers and their use cases is crucial for building efficient and secure containerized applications. By following best practices and leveraging Docker's networking capabilities, you can ensure your applications are well-connected and robust.
Happy containerizing!

Subscribe to my newsletter
Read articles from Haaris Sayyed directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
