How to Monitor Custom IAM Users in Your AWS Organization
 Kaustav Chakraborty
Kaustav Chakraborty
Managing AWS accounts is one of the most challenging jobs for any Platform / Security team. While maintaining availability and security, monitoring who is getting access to AWS accounts is essential.
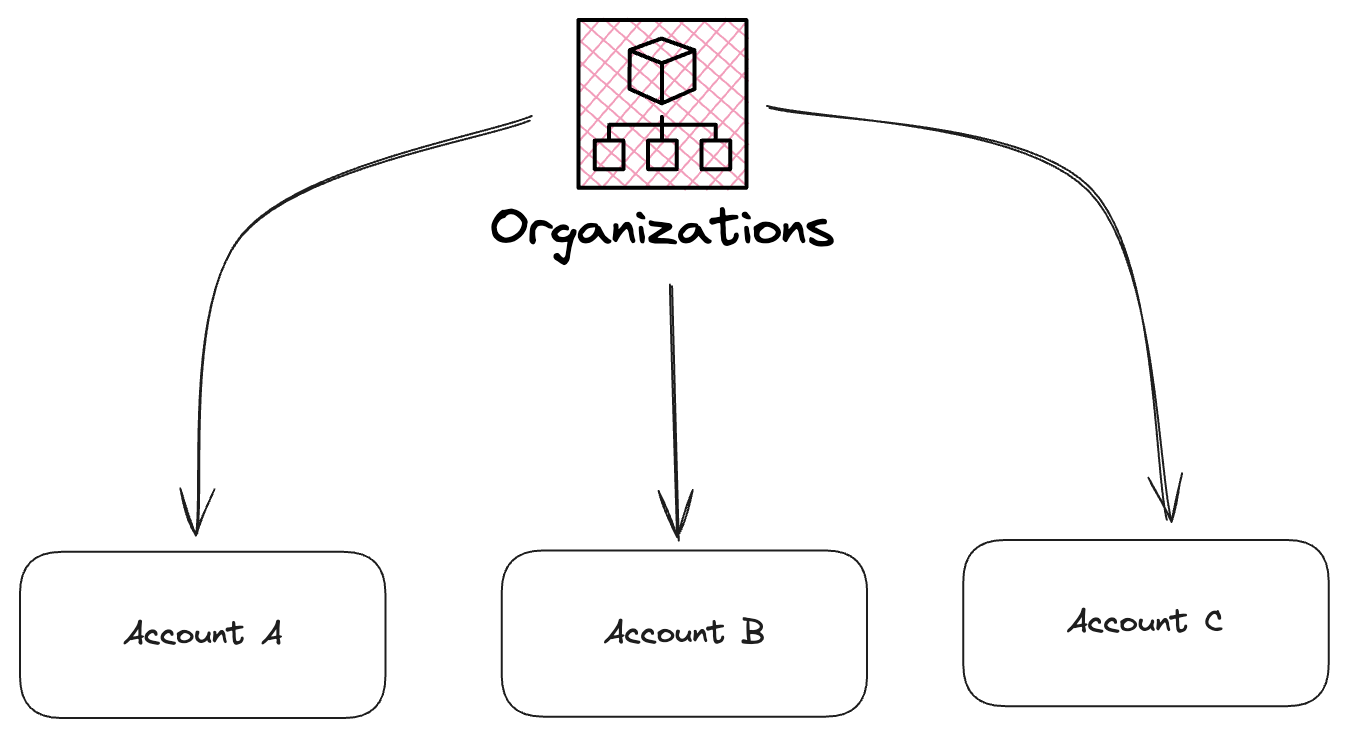
Let’s assume the CTO of PlatformSecurityTech (an imaginary IT company) asked their Platform team to create a few accounts for their product offerings. Right after the request, the team set up 3 accounts per the above diagram and handed them to the company. The team used AWS Identity Center to manage its users securely and maintain further security.
Since users of Account A and Account B had unrestrictive permissions for their day-to-day needs (it could be a lack of understanding of programmatic access through SSO), many IAM users were created. Among them, a few were not even used for months 🤔. It was getting difficult to maintain their usage. The team decided to perform bi-weekly audits on existing IAM users in different accounts and later monitor them.
It’s easy if you have one or two accounts to monitor. But in an ideal world, there are many of them. Going through each one is not only tiring but also time-consuming. They decided to go ahead with Advance Query in AWS Config to increase productivity and provide a seamless experience in monitoring those IAMs.
Given they restructured the organization as below,
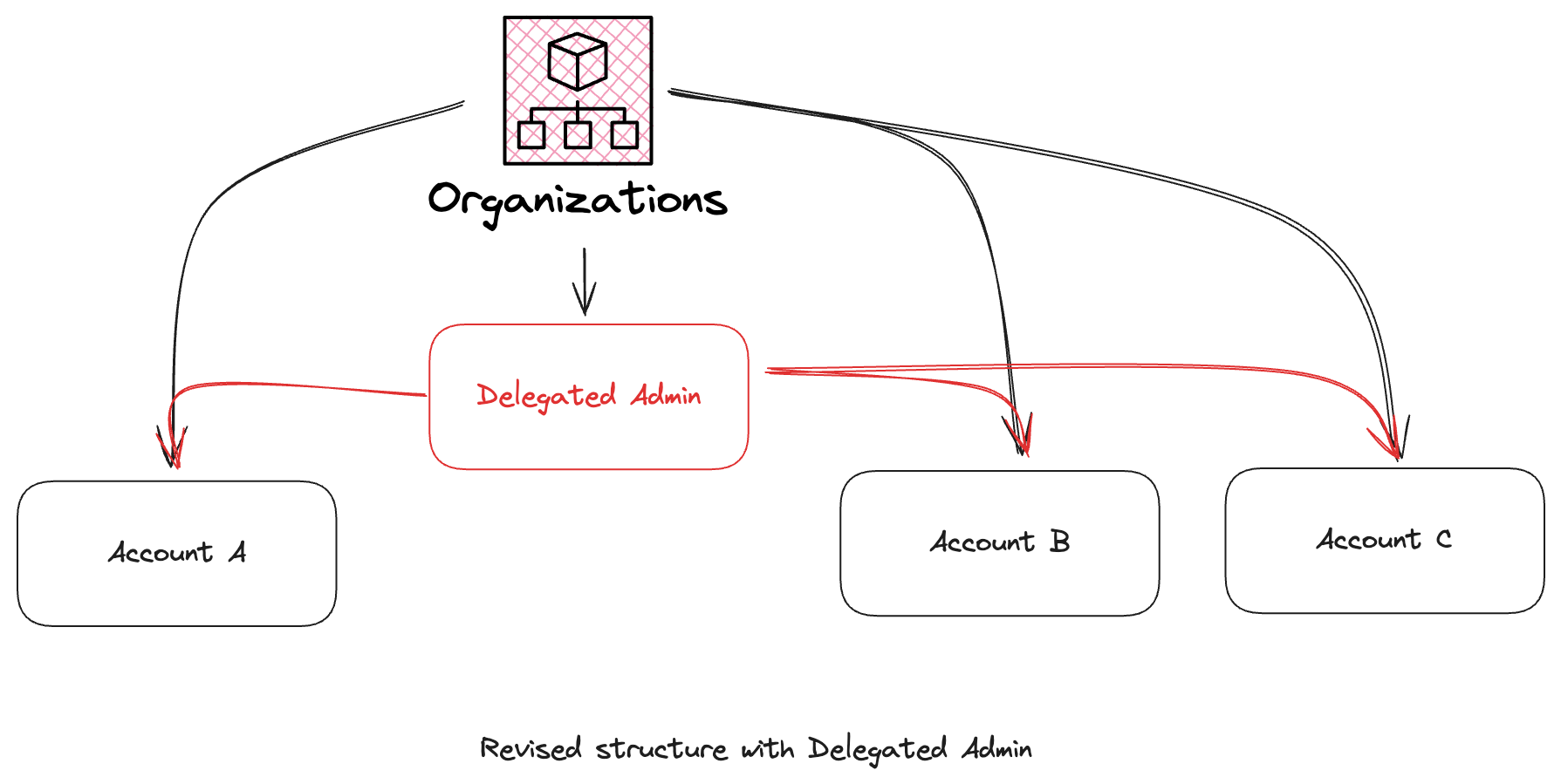
Here, they developed another AWS account called Delegated Admin, which manages all the administrative work (non-root account). Due to its nature, this new account is connected with all other accounts and can fetch data and perform specific activities in those accounts. Assuming AWS Config is configured in the new account, you can now observe your account’s activity. Now, to check the existing IAM users,
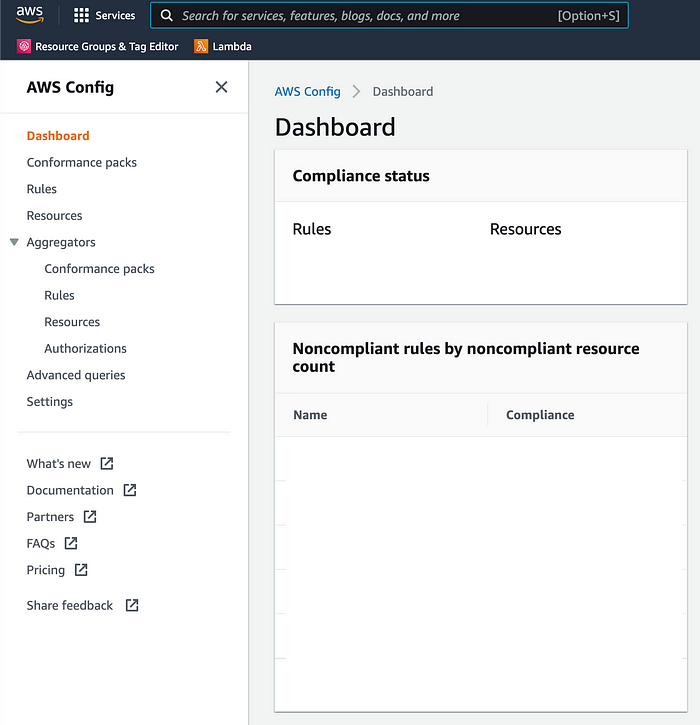
Go to https://console.aws.amazon.com/config/ for the AWS Config dashboard. There, you will find a similar-looking sidebar. Now, go to Advance Query from the sidebar.
You will find something similar to the above page, which might be pre-populated with a few queries through the team-configured conformance pack. Click on the new query and add it to the query editor below.
SELECT
accountId,
resourceName,
resourceId,
resourceCreationTime
WHERE
resourceType = 'AWS::IAM::User'
ORDER BY
accountId
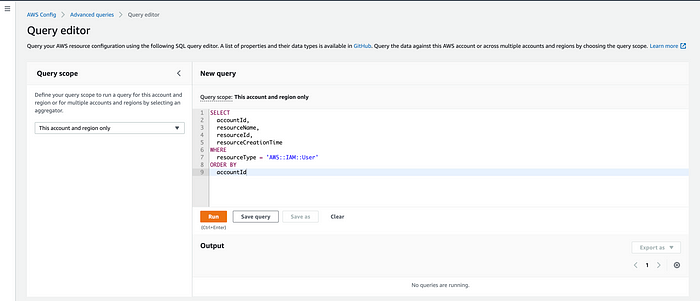
Running this query will show the list of IAM users in the AWS organization, including the other details mentioned in the selected query. Once the team collects the data from their audits, they can contact the creator of those IAM users for their needs and perform the corrections accordingly. One can export the data to any sharable format for frequent updates.
Thank you for reading this article! If you're interested in DevOps, Security, or Leadership for your startup, feel free to reach out at hi@iamkaustav.com or book a slot in my calendar. Don't forget to subscribe to my newsletter for more insights on my security and product development journey. Stay tuned for more posts!
Subscribe to my newsletter
Read articles from Kaustav Chakraborty directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Kaustav Chakraborty
Kaustav Chakraborty
Hey, Thanks for taking the time to read this. I'm a software enthusiast with over 10 years of experience in crafting software and organization. I thrive on taking on new challenges and exploring innovative ideas. When I'm not busy coding, I love to travel the world and have already visited 10 countries with 4 more on my upcoming list. I'm also passionate about discussing music, life, and new ideas. If you need someone to listen to your innovative idea, don't hesitate to buzz me. I'm always open to collaborating and lending an ear. With my passion for creativity and my drive to excel, I'm confident that I can help you take your project to the next level. Let's work together to turn your vision into a reality!