Guide to Learning Ethical Hacking and Penetration Testing
 GnanaAslin 2000
GnanaAslin 2000Ethical hacking and penetration testing have become critical skills in the digital age, where cybersecurity threats are constantly evolving. These practices involve simulating cyberattacks to identify vulnerabilities in systems and networks, ensuring they are secure against potential malicious attacks. For those looking to enhance their skills remotely, Ethical Hacking Online Training offers comprehensive courses that cover these operating systems in depth

Establish a Strong Foundation in Cybersecurity
Embarking on the journey to become an ethical hacker requires a solid understanding of the foundational principles of cybersecurity. The core of this foundation is the Confidentiality, Integrity, and Availability (CIA) Triad, which underscores the importance of protecting data and ensuring its accuracy and availability to authorized users. Confidentiality focuses on restricting access to information to those who are authorized, while integrity ensures that data is accurate and unaltered. Availability guarantees that information is accessible to those who need it when they need it. Understanding various types of cyber threats is also crucial.
Develop Proficiency in Programming and Scripting
Programming and scripting skills are fundamental for any ethical hacker. Python is an excellent starting point due to its simplicity and powerful libraries that are widely used for automating tasks and developing security tools. With Python, you can write scripts to perform a variety of tasks, from web scraping to network scanning.Bash scripting is another critical skill, particularly for automating tasks in Unix/Linux environments. It allows you to write scripts that can manage files, execute programs, and perform other tasks on Unix-based systems. This is particularly useful for managing servers and automating repetitive tasks.
Gain Expertise in Operating Systems
Proficiency in various operating systems is essential for ethical hackers. Linux, particularly distributions like Kali Linux, is favored by security professionals due to its robustness and the extensive array of security tools it offers. Kali Linux is specifically designed for penetration testing and security research, making it an ideal platform for ethical hackers. Learning Linux file systems, command-line operations, and security configurations is crucial for effective system management and exploitation. Equally important is familiarity with Windows internals. Windows is widely used in corporate environments, and understanding its architecture, including Active Directory and common vulnerabilities, is essential.
Acquire Practical, Hands-On Experience
Practical experience is critical for developing proficiency in ethical hacking. Engaging with platforms like Hack The Box, TryHackMe, and VulnHub allows you to practice in safe, controlled environments. These platforms provide various challenges and scenarios that simulate real-world attacks, helping you hone your skills. You can practice techniques such as network scanning, web application testing, and exploiting vulnerabilities in a risk-free environment. For those based in India, Ethical Hacking Training in Hyderabad provides an excellent opportunity to gain practical experience and learn from industry experts. These training programs offer hands-on labs and real-world scenarios that prepare you for actual penetration testing.
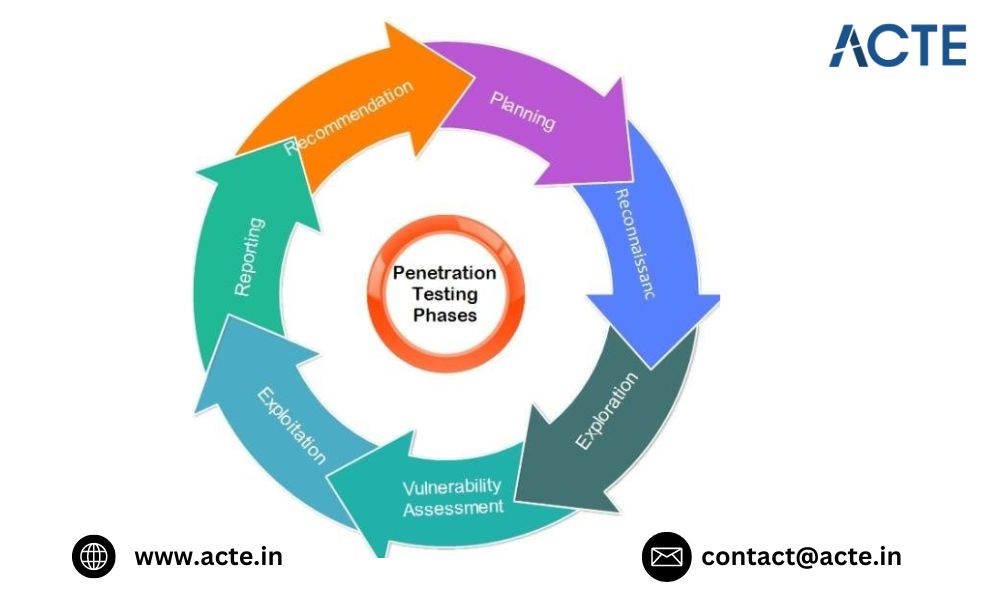
Master Essential Hacking Tools and Advanced Techniques
A variety of tools are essential for penetration testing. Nmap is a fundamental tool for network scanning and discovery, allowing you to identify open ports and services. Understanding how to use Nmap effectively can help you map out a network and identify potential targets for further investigation. Wireshark is crucial for network traffic analysis, helping you understand communication patterns and detect anomalies. With Wireshark, you can capture and analyze network packets to identify suspicious activity and potential vulnerabilities. Metasploit is indispensable for developing and executing exploits. It provides a framework for testing vulnerabilities and includes a vast library of pre-built exploits.
Embrace Continuous Learning and Ethical Practices
Cybersecurity is a rapidly evolving field, necessitating continuous learning. Keeping up with the latest trends, tools, and techniques is crucial for staying effective in this dynamic environment. Reading cybersecurity blogs, forums, and news sites like Krebs on Security, Threatpost, and the SANS Internet Storm Center can help you stay informed about the latest developments. Attending cybersecurity conferences such as DEF CON, Black Hat, and RSA Conference provides opportunities to learn from experts and network with peers. These events often feature talks and workshops on the latest threats, tools, and techniques, providing valuable insights and knowledge.
Conclusion
Learning ethical hacking and penetration testing is a comprehensive and ongoing process that requires a blend of theoretical knowledge, practical skills, and ethical considerations. Starting with a solid foundation in cybersecurity principles, building strong programming and networking skills, and gaining hands-on experience through labs and competitions are crucial steps. Mastering essential tools and advanced techniques ensures you remain effective in this dynamic field. By adhering to legal and ethical guidelines, you can contribute positively to cybersecurity, protecting systems and data from malicious threats. This journey requires dedication, continuous learning, and a commitment to ethical practices, but it is ultimately rewarding as you play a crucial role in safeguarding the digital world.
Subscribe to my newsletter
Read articles from GnanaAslin 2000 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
