Linux Fundamental Part 1
 Anshul Choudhary
Anshul Choudhary
Hackers are doers by nature, craving hands-on interaction and experimentation. We love creating and sometimes breaking things. Few enjoy reading lengthy IT theory before hacking. This chapter provides essential skills for Kali immediately.
A Bit of Background on Linux
Where is Linux Used?
It's fair to say that Linux is a lot more intimidating to approach than Operating System's (OSs) such as Windows. Both variants have their own advantages and disadvantages. For example, Linux is considerably much more lightweight and you'd be surprised to know that there's a good chance you've used Linux in some form or another every day! Linux powers things such as:
Websites that you visit
Car entertainment/control panels
Point of Sale (PoS) systems such as checkout tills and registers in shops
Critical infrastructures such as traffic light controllers or industrial sensors
Flavours of Linux
The name "Linux" is actually an umbrella term for multiple OS's that are based on UNIX (another operating system). Thanks to Linux being open-source, variants of Linux come in all shapes and sizes - suited best for what the system is being used for.
For example, Ubuntu & Debian are some of the more commonplace distributions of Linux because it is so extensible. I.e. you can run Ubuntu as a server (such as websites & web applications) or as a fully-fledged desktop. For this series, we're going to be using Ubuntu.
Ubuntu Server can run on systems with only 512MB of RAM
Introductory Terms and Concepts
Before we delve into the fundamentals of Linux Basics for Hackers, let's clarify a few essential terms that will be frequently referenced throughout this chapter.
Binaries
Binaries are executable files, akin to executables in Windows. These files typically reside in the /usr/bin or /usr/sbin directories. Examples of binaries include utilities such as ps, cat, ls, and cd, which we will explore further in this chapter. Additionally, binaries can include applications like the wireless hacking tool Aircrack-ng and the intrusion detection system (IDS) Snort.
Case Sensitivity
Unlike Windows, Linux is case sensitive. This means that Desktop, desktop, and DeskTop are recognized as distinct entities. Each of these would correspond to a different file or directory. For users transitioning from a Windows environment, this can be a source of frustration. If you encounter the error message “file or directory not found” and are certain the file or directory exists, you likely need to check your capitalization.
Directory
A directory in Linux serves the same function as a folder in Windows. It provides a means to organize files in a hierarchical structure.
Home
Each user in Linux has their own /home directory. By default, this is where any files you create will be saved.
Kali
Kali Linux is a specialized distribution of Linux designed specifically for penetration testing. It comes preloaded with hundreds of tools, saving you the time and effort of downloading and installing them individually. For this book, I'll be using the latest version of Kali available at the time of writing: Kali 2018.2, which was first released in April 2018.
Root
Linux, like most operating systems, has an administrator or superuser account. This account, known as root, is intended for use by a trusted person who has almost unlimited control over the system. This includes tasks such as reconfiguring the system, adding users, and changing passwords. As a hacker or penetration tester, you will often use the root account to gain control over a system. Many hacking tools require root access to function.
Script
A script is a series of commands executed in an interpretive environment, which converts each line into source code. Many hacking tools are essentially scripts. Scripts can be executed with the Bash interpreter or other scripting language interpreters, such as Python, Perl, or Ruby. Currently, Python is the most popular interpreter among hackers.
Shell
A shell in Linux is an environment and interpreter for running commands. The most commonly used shell is Bash, which stands for Bourne Again Shell. Other popular shells include the C shell and Z shell. In this book, we will exclusively use the Bash shell.
Terminal
The terminal provides a command line interface (CLI) for interacting with the Linux operating system.
With these foundational concepts covered, we'll now methodically develop the essential Linux skills you'll need to become a proficient hacker or penetration tester.
The Linux Filesystem
The structure of the Linux filesystem differs significantly from that of Windows. Unlike Windows, which uses physical drives (like the C: drive) as the foundation of its filesystem, Linux employs a logical filesystem structure.
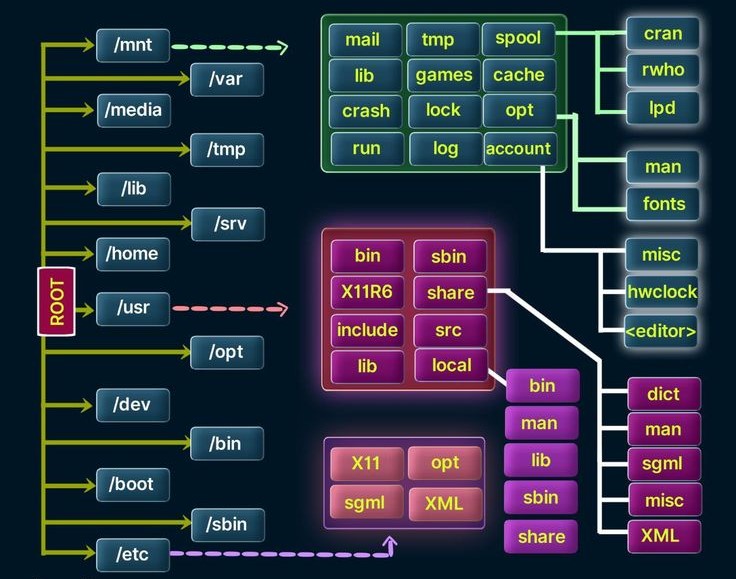
At the very top of the Linux filesystem is the root directory, denoted by /. Think of this as the root of an upside-down tree, from which all other directories and files branch out. It's important to note that this root directory, /, is distinct from the root user account. The similarities in their names might be confusing initially, but with time and practice, you'll find it easier to differentiate between them.
Understanding this structure is crucial as it lays the foundation for navigating and managing files within a Linux system.
Key Directories in the Linux Filesystem
The root (/) of the Linux filesystem sits at the top of the directory tree. Here are some of the most critical subdirectories under the root directory and their purposes:
/root: This is the home directory for therootuser, who has administrative privileges. It’s a private space reserved for system administration tasks./etc: This directory generally holds configuration files for the system and various applications. These files define how the system and software should behave and when and how certain programs should start./home: Each non-root user has a home directory within this directory. For example, if your username isalice, your home directory would be/home/alice. This is where your personal files and settings are stored./mnt: This is used for temporarily mounting filesystems. When you attach another filesystem (like an additional hard drive), it can be accessed through this directory./media: This directory is typically used for mounting removable media like CDs, DVDs, and USB drives. When you insert such devices, they are usually attached to subdirectories under/media./bin: Here you'll find essential application binaries, which are equivalent to executables in Windows. Common utilities such asls,cp, andmvare located here./lib: This directory contains essential libraries, which are shared code files that provide functionality to other programs. These are akin to DLL files in Windows and are crucial for running software and system processes.
Basic Commands in Linux
pwd
Use: Print the current working directory.
Example:
pwd
whoami
Use: Display the current logged-in user.
Example:
whoami
cd
Use: Change directory.
Example:
cd /etc
ls
Use: List directory contents.
Example:
ls
man
Use: Display manual pages for commands.
Example:
man ls
locate
Use: Search for files by name.
Example:
locate aircrack-ng
whereis
Use: Locate binaries, source, and manual pages for a command.
Example:
whereis aircrack-ng
which
Use: Locate a command within the user's PATH.
Example:
which ls
find
Use: Search for files in a directory hierarchy.
Example:
find /etc -type f -name "apache2"
grep
Use: Search for patterns within files.
Example:
ps aux | grep apache2
mkdir
Use: Create a new directory.
Example:
mkdir newdirectory
cp
Use: Copy files and directories.
Example:
cp file1.txt /path/to/destination
mv
Use: Move or rename files and directories.
Example:
mv file1.txt newname.txt
rm
Use: Remove files or directories.
Example:
rm file1.txt
These commands are essential for navigating, manipulating files, and performing administrative tasks in Linux.
Before moving to part 2 try out the skills you learned from this chapter by completing the following exercises:
Exercises
Explore Directory Structure
Use
lscommand from the root (/) directory to explore Linux's directory structure.Move to each directory using
cdcommand and verify your location withpwd.
Verify Logged-In User
- Use
whoamicommand to confirm which user you are logged in as.
- Use
Find Wordlists
- Utilize
locatecommand to find wordlists suitable for password cracking.
- Utilize
Create and Append to a File
- Use
catcommand to create a new file. Remember,>redirects input to a file and>>appends to a file.
- Use
Manipulate Directories and Files
Create a directory named
hackerdirectory.Create a new file
hackedfilewithinhackerdirectory.Copy
hackedfileto the/rootdirectory and rename it tosecretfile.
These exercises will help reinforce your understanding of basic Linux commands and file system navigation.
Subscribe to my newsletter
Read articles from Anshul Choudhary directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
