BRB Bootcamp Session 2
 Siddharth Shukla
Siddharth Shukla
Namaste🙏️ Folks, In this we will be reading about my learning and topics discussed in the 2nd session of BRB Bootcamp.
Overview
Session 2 was started by our previous session mentor Aman Ser. In this blog, we will be discussing the given topics:
Understanding Cryptography & Digital Signatures.
Evolution and Types of Web3 Wallet.
Setting up a Web3 Wallet.
Introduction to Smart Contract Development.
Introduction Smart Contract Security.
Understanding Cryptography & Digital Signatures.
What is Cryptography?
Cryptography is a technique of securing communication by converting plain text into ciphertext.
This technique was also used in older times when kingdoms needed to communicate with their spies in another kingdom where they wrote text on a note in an unreadable text. Then spies convert it into normal text.
This way no one can understand the message even if it is intercepted by enemies.
SOME TERMS:
Plain Text: Text that can be read by humans example "Hello Guys".
Cipher Text: Text that cannot be read by without converting into Plain text. example "ZPV BSF BXTPNF". (Try decrypting it 😉️)
Secret Key: A Secret key that is used to encrypt the plain text into cipher text or vice-versa.
Types of Cryptography
Symmetric
A Cryptographic technique that utilizes a single key for encryption & decryption.
It is the most basic type of technique. Let us see its types which are:
Ceaser Cipher
Playfair Cipher
Hill Cipher
Advanced Encryption Standard (AES)
Data Encryption Standard (DES)
To understand Cryptography basics we look into Ceaser Cipher.
Ceasert Cipher utilizes a single key which represents how many times to shift a character in Message.
For Example, Our Message is "I am Sid" and the Key is 2. With this, we can encrypt our text.
Encrypting: To encrypt it we will shift each character one by one by 2(key) position. So, character 'I' will become 'K', 'a' becomes 'c', and so on.
The cipher Text will be " K CO UKF ".
Decrypting: To decrypt we have to shift characters 2 steps back to obtain the original message.This technique is easy but If the key is compromised then it will be a disaster. Also, it is very easy to crack. Try cracking the above code in the Cipher TEXT section.
Asymmetric
This technique utilizes a pair of keys for encryption and decryption of the text.
Where Keys can be a Public Key and a Private Key.To understand it more let's have a look at Public key Cryptography (PKC).
This method requires the sender & receiver to have its own pair of keys. These can be generated through a key generation algorithm some of them are RSA and ECDSA (used by Ethereum & Bitcoin).
Things to Note
A Public Key can be derived from the private key. But, the Opposite is not possible.
It is important that You keep your private key safe.
If you create your wallet just now no one will be aware of your public Key as it is not involved in any on-chain transaction.
Once a key is generated anyone can take part in the communication process.
Digital Signatures
It is a mathematical scheme for verifying the authenticity of digital messages or documents.
To Utilize the Digital Signature one requires its Private Key.
Generally, speaking One requires a Digital Signature when he/she needs to prove identity on the internet.So How will anyone verify it? via his/her's public key and then compare their Hashes.
What is Hash?
- A Hash is a technique that converts any piece of information into a fixed length of characters. And it is irreversible & close to impossible to obtain the original piece of information.
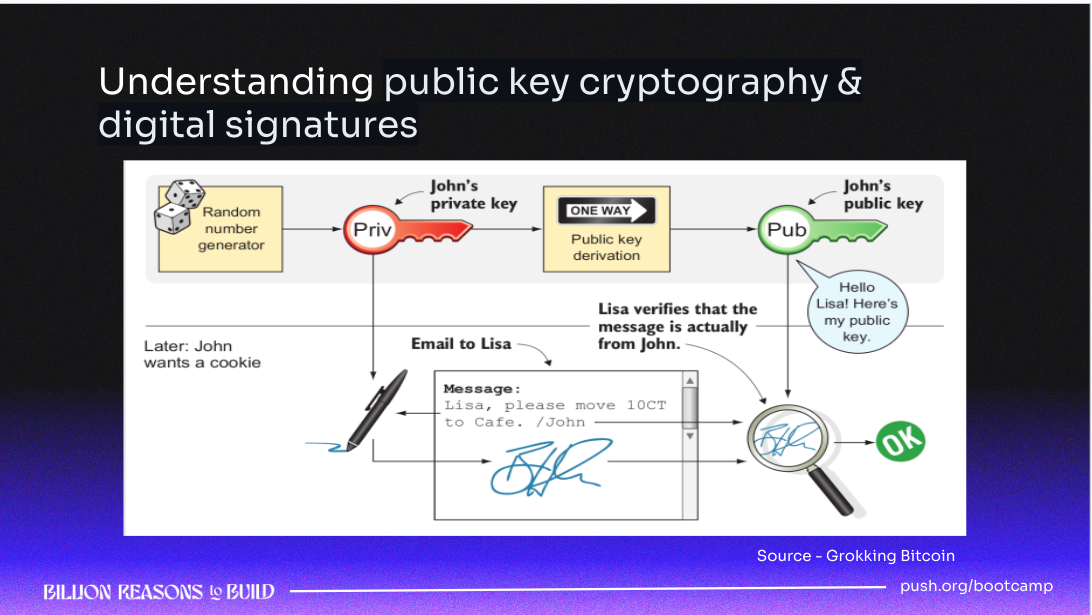
Let's understand all of it better via the above figure.
We have two actors John & Lisa. So Jhon wants to Email something but Lisa does not believe anyone on the internet that you are the intended person.
So John generates his Private key via any algorithm and derives its public key from it. Then, John signs the Email via his private key and sends the email to Lisa. Also, he provides his public to Lisa as well. Then by using a hash function, Lisa compares the hashes of both Email+Private Key and Email+Public Key if it is the same then she believes it.
Web3 Wallets
At a high level, a wallet is a software application that serves as the primary user interface to Ethereum. The wallet controls access to a user’s money, managing keys and addresses, tracking the balance, and creating and signing transactions.
What is Need of Wallets:
Storing private keys securely.
Multi-chain asset management.
Better UX / DevX for interaction with Dapps.
Types Of Wallets
Hot Wallets: These wallets are software-based wallets that are connected to the internet and are more convenient to use for quick trade and exchange of tokens/coins.
Example: Metamask a Browser wallet, Electrum a Desktop Wallet & Trust a Mobile Wallet.
However, these possess a high threat of losing funds if keys are compromised.Cold Wallets: This type of wallet is not connected to the internet as they are a physical piece of hardware like a pen-drive or hard-disk. But these are considered the most secure for storing large investments.
Example: Hardware Wallets & Paper Wallets.Custodial Wallets: A wallet who's private key is managed by a third-party.
Example Account on Binance gives you a virtual wallet which is managed by Binance.Benefits are:
Easy recovery in case the user forgets the password.
* Better UX since no signatures are required from the user again and again
Downsides are:
- Loss/blocking of funds in case of third-party crisis or bankruptcy. Eg - FTX, Vauld.
Non-Custodial Wallets: A Wallets Which is owned by the user itself.
Downsides are:
Recovery is not possible in case private keys/seed phrase is lost.
The user needs to sign in for every on-chain action affecting UX.
Smart Contract Wallets: It is blockchain-based wallets that use smart contracts to manage transactions and can offer more functionality than traditional wallets.
Benefits are:
Enhanced Security: They can require multiple signatures or conditions to execute transactions, reducing the risk of theft.
Programmable: Users can set rules for automatic transactions based on certain conditions.
Interoperability: They can interact with various decentralized applications (DApps) directly from the wallet.
Downsides are:
- Complexity: They can be more complex to use than simple wallets, which might be challenging for beginners.
Multi-Party Computation ( MPC ) Wallets: It is a type of cryptographic wallet where the private key is not held by a single entity but is instead distributed among multiple parties.
Benefits are:
- Reduces Risk: As the keys are divided among a group of people it reduces the risk of fund theft.
Downsides are:
Complex Setup: The initial setup for MPC wallets can be more complex than traditional wallets.
Operational Risk: This relies on the availability and honesty of all parties involved in the computation.
Setting Up a Web3 Wallet
To Enter into the Web3 World explore DeFi, Metaverse or be a part of DAO's we need a Wallet. Let us create it.
Head over to the Metamask website and add its extension to your Chromium based Web-Browsers. You can also use other wallets as well
Then Follow through the steps and don't forget to store your SeedPhrase Somewhere safe and secure. Because whenever you have to use your wallet somewhere else you require this SeedPhrase.
Now, It is important to Add your Favourite Network or Add New Token that you don't see in your wallet.
To Add a New Network:
Navigate to the Top Left Corner and click on the symbol aside to your Account Name.
Then click on "Add Network" at the bottom of the network list.
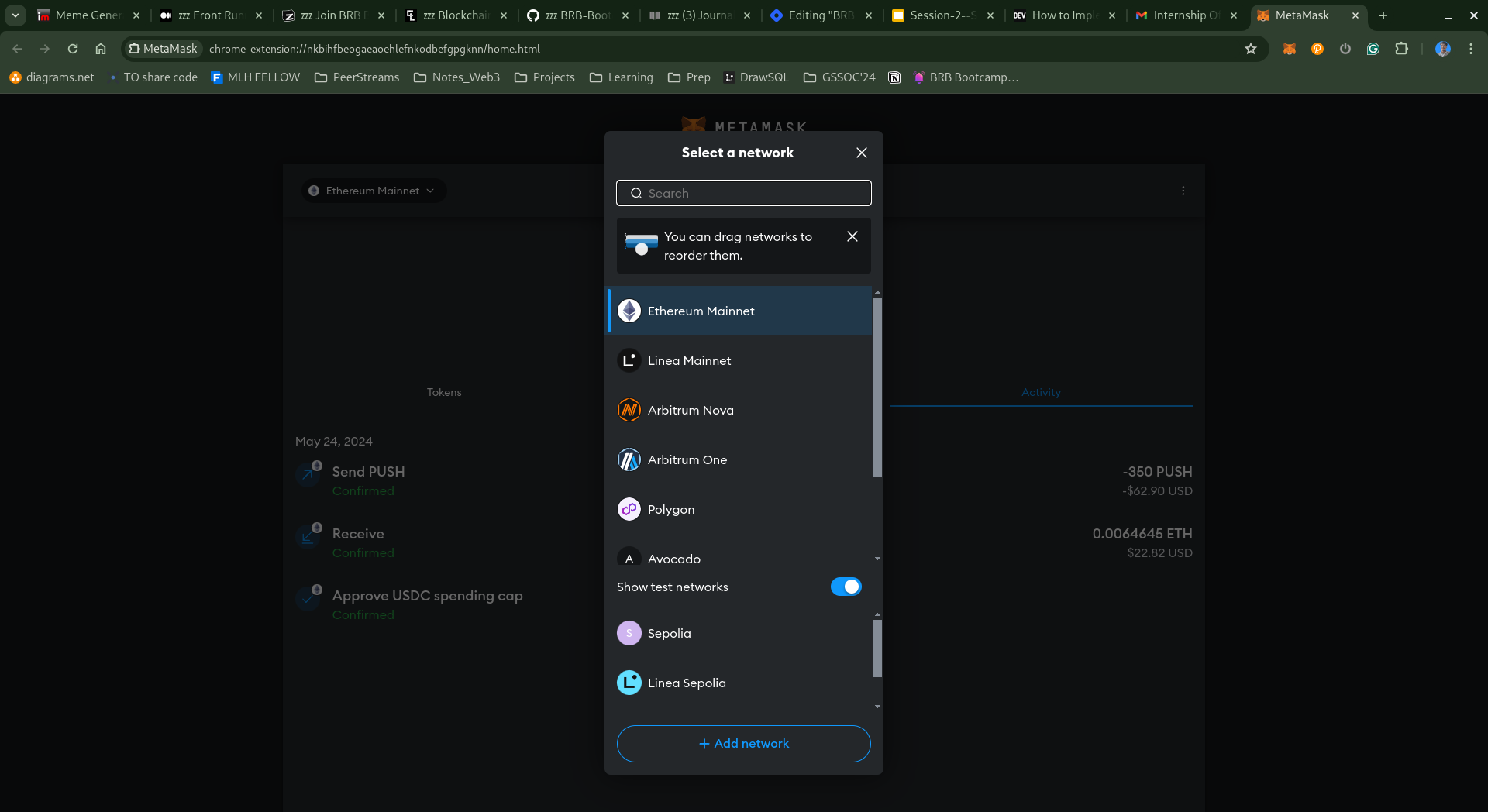
You will see a list of networks if your desired network(which is generally not here if you are a dev) is not listed then click on "Add network manually".
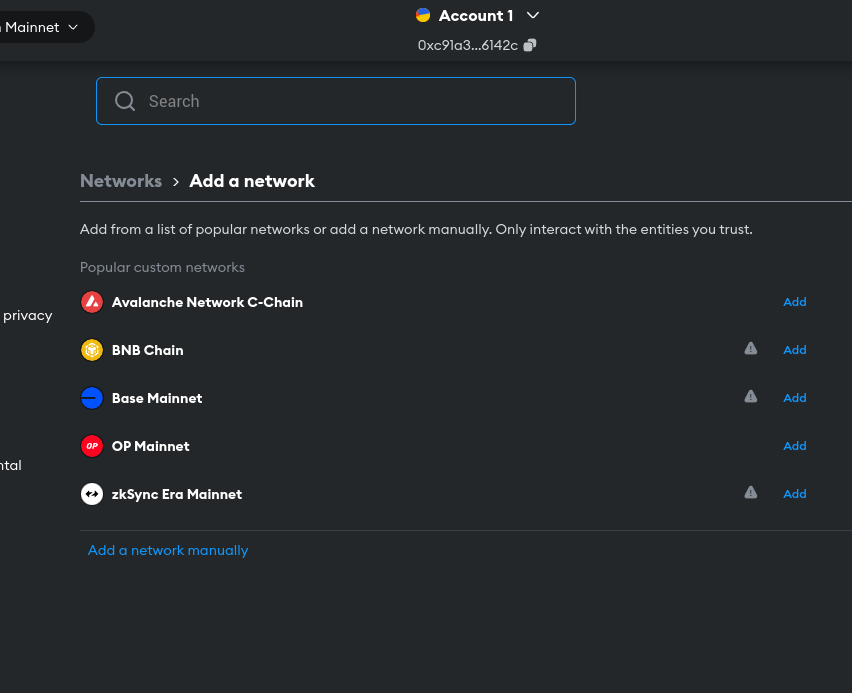
Now a bunch of fields are there but not to panic😵💫️ use the Chainlist website to add any desired network. And you are done👍️.
Add New/Custome Token
Head over to the Tokens Section and at the bottom, you will find an option "Import Token".
Now you can either search for the token if it is popular or you can import using Token Contract Address.
Intro to Smart Contract Dev.
In this section, we were taught about various resources that are required to learn the smart-contract dev. It is always better if you know any low-level language to learn Solidity.
If not then you can still start from solidity itself you can explore these resources for a better learning experience:
Pattrick Collin's Ser Foundry Course here.
Alchemy University here.
For Coding Practice use DApp World here.
For GEEKS use this.
We also discussed which chains to use to build what type of DApps:
Such as for:
Security: Prefer Layer-1 Blockchains
Higher TPs rate: Solana
Faster & Cheaper Transaction: Layer-2 Chains such as Polygon, Optimism, Arbitrum
Oracles: These are third-party services that provide smart contracts with external information.
They serve as bridges between blockchains and the outside world.
Oracles are necessary because the blockchain cannot access data outside of its network
For example knowing the real-time value of INR, USD, or any currency.
Intro. to Smart Contract Security
Smart contracts are self-executing contracts with the terms of the agreement directly written into code. They run on a blockchain, making them immutable and distributed. However, their security is paramount as they often handle valuable transactions and can be targets for attacks.
Here's a List of attacks that happened on smart contacts:
Logical Errors in Code: These occur when the smart contract’s code doesn’t accurately reflect the intended logic or outcomes, leading to unintended behavior.
Reentrancy Attacks: This type of attack happens when a malicious contract calls back into the calling contract before its first execution is complete, potentially draining funds.
Integer Overflow/Underflow Attacks: These happen when arithmetic operations reach the maximum or minimum size of a variable, causing unexpected results like balance errors.
Front Running: This happens when someone takes advantage of knowing a future transaction to make a profit, such as by seeing a pending transaction and quickly submitting their own with a higher gas fee to be executed first.
Oracle Manipulation: Since oracles provide external data to smart contracts, manipulating the data source or the oracle’s response can lead to incorrect contract execution.
What can be done:
Requirements and expectations from the smart contract should be clear before writing the code.
Best coding practices should be followed.
Solidity version should be selected carefully with no known vulnerabilities.
There must be proper unit and integration testing.
Fuzzing can be used to identify edge cases.
Contracts must be audited by reputed organizations / reputed smart contract researchers before deployment to Mainnet.
Thank you for reading this blog. We'll wrap it up here. Stay tuned for the next one.
Subscribe to my newsletter
Read articles from Siddharth Shukla directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
