Understanding Hashing and Its Different Types in Cyber Security 🔐
 Sudhanshu Wani
Sudhanshu Wani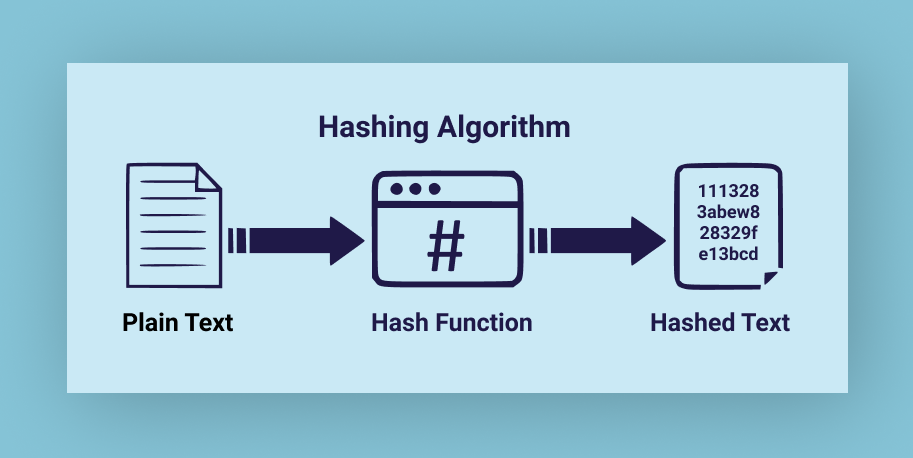
Introduction to Hashing
Hashing is an essential component of data integrity, authentication, and security protocols, making it a critical concept in both computer science and cyber security. It involves converting any size of input data into a fixed-length string of characters, usually a hash value or code. This transformation is performed by a hash function, which guarantees that even a small change in the input results in a significantly different hash value. Hashing is a powerful tool for ensuring security and data integrity thanks to this property.
The Importance of Hashing in Cyber Security
In cyber security, hashing serves multiple purposes:
Data Integrity: Hashing ensures that data has not been altered during transmission. Any tampering can be identified by comparing the hash values of the original and received data.
Authentication: Hash functions are used in password storage. Systems store the hash values of passwords rather than plain text, enhancing security.
Digital Signatures: Hashing is a crucial part of creating digital signatures, ensuring the authenticity and integrity of documents and messages.
Blockchain Technology: Hashing is the foundation of the blockchain structure, ensuring the integrity and security of data across decentralized networks.
Types of Hashing Algorithms
Different hashing algorithms serve various purposes, each with unique characteristics. Here are some common types:
1. MD5 (Message Digest Algorithm 5)
Overview: Developed in 1991, MD5 produces a 128-bit hash value.
Use Cases: Initially used for verifying data integrity and password hashing.
Security: Considered insecure for most cryptographic purposes due to vulnerabilities to collision attacks, where two different inputs produce the same hash value.
2. SHA-1 (Secure Hash Algorithm 1)
Overview: SHA-1 generates a 160-bit hash value and was widely used in cryptographic applications.
Use Cases: Digital certificates and signatures.
Security: Similar to MD5, SHA-1 is no longer considered secure against well-funded attackers due to collision vulnerabilities.
3. SHA-256 (Secure Hash Algorithm 256)
Overview: Part of the SHA-2 family, SHA-256 generates a 256-bit hash value.
Use Cases: SSL/TLS certificates, blockchain technology (e.g., Bitcoin).
Security: Currently considered secure, with no practical collision vulnerabilities known.
4. SHA-3 (Secure Hash Algorithm 3)
Overview: The latest member of the Secure Hash Algorithm family, SHA-3 offers a different structure compared to its predecessors.
Use Cases: Applications requiring high security levels, such as advanced cryptographic protocols.
Security: Provides robust security and resistance to collision and pre-image attacks.
5. BLAKE2
Overview: Designed as a faster and more secure alternative to MD5 and SHA-2, BLAKE2 is highly efficient and offers various configuration options.
Use Cases: General-purpose cryptographic applications, file integrity verification.
Security: Known for its speed and security, BLAKE2 is widely used in modern software.
How Hashing Enhances Cyber Security
Password Security: Hash functions store passwords securely by converting them into hash values. When a user logs in, the entered password is hashed and compared to the stored hash. This method ensures that plain text passwords are not stored, reducing the risk of exposure in case of a data breach.
Data Integrity Checks: Hashing verifies the integrity of files and data. For example, software downloads often come with a hash value that users can compare to the hash of the downloaded file, ensuring it hasn't been tampered with.
Digital Signatures: Hashing ensures the authenticity and integrity of digital documents and messages. The sender hashes the document and encrypts the hash with their private key, creating a digital signature. The receiver can then decrypt the signature and compare the hash to verify the document's integrity and origin.
Blockchain Security: In blockchain technology, each block contains the hash of the previous block, creating a secure chain. This structure ensures that altering any block's data would require recalculating the hashes of all subsequent blocks, making tampering practically impossible.
Conclusion
Hashing is a cornerstone of modern cyber security, providing essential services such as data integrity verification, secure password storage, and digital signature creation. Understanding different types of hashing algorithms and their applications is crucial for developing robust security measures and protecting sensitive information in an increasingly digital world.
By leveraging secure hashing algorithms and staying updated with advancements in cryptographic research, we can ensure that our data remains secure and our systems resilient against emerging cyber threats.
Subscribe to my newsletter
Read articles from Sudhanshu Wani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
